The CNET “Bombshell” and the Four Surveillance Programs
CNET is getting a lot of attention for its report that NSA, “has acknowledged in a new classified briefing that it does not need court authorization to listen to domestic phone calls.”
In general, I’m just going to outsource my analysis of what the exchange means to Julian Sanchez (I hope he doesn’t charge me as much as Mike McConnell’s Booz Allen Hamilton for outsourced analysis).
What seems more likely is that Nadler is saying analysts sifting through metadata have the discretion to determine (on the basis of what they’re seeing in the metadata) that a particular phone number or e-mail account satisfies the conditions of one of the broad authorizations for electronic surveillance under §702 of the FISA Amendments Act.
[snip]
The analyst must believe that one end of the communication is outside the United States, and flag that account or phone line for collection. Note that even if the real target is the domestic phone number, an analyst working from the metadatabase wouldn’t have a name, just a number. That means there’s no “particular, known US person,” which ensures that the §702 ban on “reverse targeting” is, pretty much by definition, not violated.
None of that would be too surprising in principle: That’s the whole point of §702!
That is, what Nadler may have learned that the same analysts who have access to the phone metadata may also have authority to issue directives to companies for phone content collection. If so, it would be entirely feasible for the same analyst to learn, via the metadata database, that a suspect phone number is in contact with the US and for her to submit a request for actual content to the providers, without having to first get a FISA order covering the US person callers directly. Since she was still “targeting” the original overseas phone number, she would be able to get the US person content without a specific order.
 I just want to point to a part of this exchange that everyone is ignoring (but that I pointed out while live tweeting this).
I just want to point to a part of this exchange that everyone is ignoring (but that I pointed out while live tweeting this).
Mueller: I’m not certain it’s the same–I’m not certain it’s an answer to the same question.
Mueller didn’t deny the NSA can get access to US person phone content without a warrant. He just suggested that Nadler might be conflating two different programs or questions.
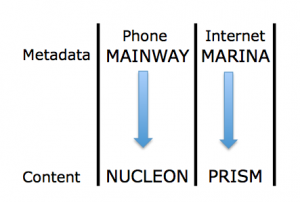
And that’s one of the things to remember about this discussion. Among many other methods of shielding parts of the programs, the government is thus far discussing primarily the two programs identified by the Guardian: the phone metadata collection (which the WaPo reports is called MAINWAY) and the Internet content access (PRISM).
Thus, we are effectively just talking about two programs, and not two that intersect via targeted technology, as MAINWAY would with NUCLEON and MARINA with PRISM. So, while there are a slew of other possibilities for what Mueller might mean by “another question,” one big one is “how may an analyst access NUCLEON information if she had MAINWAY data”?
And, as Sanchez notes in his piece, the way 702 is supposed to work (and indeed, would have to work for the claims made about PRISM’s role in thwarting the Najibullah Zazi attack to be remotely true) is that US person information comes up along with targeted foreign targets. Indeed, as I noted last year during the FISA Amendments Act debate, in an effort to defeat this amendment prohibiting effectively what Sanchez has laid out, Sheldon Whitehouse said that getting US content without a warrant was the entire point.
He referred back to his time using warrants as a US Attorney, and said that requiring a warrant to access the US person communication would “kill this program,” and that to think warrants “fundamentally misapprehends the way in which this program operates.”
The possibility that the government would do this kind of thing has been raised repeatedly since Russ Feingold did so in 2009 during the FISA Amendments Act debates, speaking specifically about the content of calls to people overseas.
It may be that, discussed in isolation, the government can avoid talking about what Feingold and Wyden and others have called a backdoor. Which is probably why they don’t want us to “confuse” (that is, understand the relationship between) the business records and content access.

I just want to flag part of the same issue here as came up in a comment post I made last night:
“Note that even if the real target is the domestic phone number, an analyst working from the metadatabase wouldn’t have a name, just a number.”
Actually, I think all you can actually say is that an analyst working from the metadatabase wouldn’t have a name *provided by the telco*. If the metadatabase, or another database created from it, has numerous other columns added by NSA’s indexing and parsing algorithms, the computers can probably guess a name for a large number of the records and then tie in all kinds of other public and private files. In this case, it would probably be easy for an analyst to sift for all contacts with 2-3 degrees of a target who probably have an Muslim-sounding name or probably live in an Arab neighborhood.
@Adam Colligan: yes. we know FBI has also been getting phone books. So they’ve got numbers and names via other means, at least for landlines.
Years ago watching the Finance news I could not understand why Poppy Bush’s Carlyle group bought out the Yellow Pages and Comcast.
NOW I know. Again, I’d like for Barbara to talk about welfare queens living off the Government.
@emptywheel: And my suspicion here is that that extra data — the meta-meta-data or whatever they want to call it, is so robust that they can usually do any invasive thing they want just by querying it and never looking at the cells that contain original metadata from the telcos. The robustness is *provided* by the telcos’ metadata dumps because all the associations are generated from that database, but that’s done automatically without any pesky “voyeuristic” humans. Since the humans are only looking at the meta-meta-data, which just contains highly technical, esoteric, nothing-to-see-here information (like people’s real names, addresses, employers, travel history…), it’s as Constitutional American as Betsy Ross eating a McDonald’s apple pie.
As I read CNet, Nadler is disclosing information from a closed hearing. Sanchez is arguing that Nadler’s disclosure is inconsistent with Mueller’s public statements, and hence that Nadler is confused. But Mueller’s a spook; surely one would expect his public position to be at odds with his private one? Why give the puhlic statement credence? Further, Nadler seems to have (for a Democrat) a good record on FISA, Occupy, and Mayor-for-Life Bloomberg. Does Nadler have a record of being more confused than other Democrats, or confused at all? What am I missing here?
NOTE I’m focusing on the “confused” (to put it tendentiously) gambit, since the suggestion from the Jacquith -> Fogler -> Perlstein axis is that Greenwald is ocnfused because he’s presentin evidence of a system architecture that is at odds with the architecture they themselves would have built, were it to have been built. But they offer no evidence that the architecture was built, and the evidence they do offer is at odds with the idea that it has been. So the bloody shirt of “confusion” seems to be being waved rather a lot these days.
@emptywheel: And getting numbers/names of cellphones isn’t all that hard, either. If they’re not classified as business records that they can just get like the metadata, they can certainly afford to buy all the commercial databases that contain this stuff.
@Saul Tannenbaum: Exactly! Like I said above, Comcast, Yellow Pages, etc. Carlyle Group bought them all.
@Peasantparty: Plus, the US Chamber of Commerce was using this outfit to spy on journalists that were giving out information about dirty biz episodes. They did a dragnet type of thing on Glen Greenwald and Brad Freidman. That instance alone went beyond any reasonable personal rights and Constitutional values. Then the govt tried to cover up and give some lame ass reason for why it was necessary for Chamber and Chamber biz partners to do that to people.
In a police state you don’t need no stinking warrants. All of this gubmint BS (kayfabe) is just them trying to make it sound legal.
Here is one of their current pages:
http://www.carlyle.com/news-room/news-release-archive/carlyle-group-and-welsh-carson-anderson-stowe-purchase-qwests-yellow-pages
Then the war profiteers:
http://www.apfn.org/apfn/Carlyle_group.htm
And another Housing Bust about to happen:
http://www.apfn.org/apfn/Carlyle_group.htm
This is where Bain Capital comes in:
http://www.fasken.com/experience/detail.aspx?experience=763
They were the ones that gave Qwest such a hard time and tried to buy them out via hard tactics.
There is a link to where they are trying to buy out Verison wireless but the pages have been removed so we can’t see them.
@par4:
And also quiet down the people who haven’t been following the story all along.
Nadler walks it back.
It IS remarkably to cheap to archive the voice contents of a phone call.
That cost has been declining for quite some time as the cost of computer storage has plummeted and has the percentage of voice traffic vs data traffic relegates voice to a miniscule portion of the traffic being carried on telecom networks.
It is very unlikely that the telecoms themselves store this content as the government will to wish to post-process the data – transcribe it, translation it, analyze for keywords and index it for future use.
Much as the government archived signals intercepts in the past, even encrypts that they could not decode at the time, they realized that there would a time when they could make use of the that data.
The same will is now true for all voice communications and if not already true for data, it will be. Certainly WRT archival of data traffic however making use of it to the fullest extent will take quite some it.
The collection of the raw voice and data traffic has been well known for years given Mark Klein’s reporting of the NSA’s activities in splicing into the telcos networks.
The fly in the ointment from the NSA’s perspective is that they need to associate the content they’ve already collected with the network management information that the telcos have but can’t provide on a real time basis without compromising the functioning of their networks.
Hence the need to provide regular dumps of the metadata to the government.
Related keywords would be SS7, out of band signaling, command and control networks, network provisioning and network configuration.
@Saul Tannenbaum
Is it a coincedence that Facebook wants your phone # “for security purposes?” I think not. And too many are glad to hand it over.
@Lambert Strether: Not Nadler walking it back. Denying something he didn’t say.
He said he was briefed they can get content from a call, based on a record of a call that would then be historical. That’s different than listening in on calls on the US end going forward.
http://www.ft.com/cms/s/2/a096d1d0-d2ec-11e2-aac2-00144feab7de.html#axzz2WRVRqGtc
Because you need to know.
@emptywheel: Actually, I take that back, in his question, he does say listen in.
@emptywheel: And that is the crux of all of this. Briefings!
The first briefings after 9-11 were held in Cheney’s office with only a couple of Dept and Committee heads. They were told ONLY what Mr. Secret wanted them to hear and nothing more!
@Citizen92:
And hotmail – which caused me to permanently abandon hotmail.
They probably directly capture, analyze, and archive everything. But, in order to present the information to a court they need a series of snappily titled ‘legal’ methods of data collection.
From an NPR interview of the NSA’s former Inspector General Joel Brenner (http://www.npr.org/templates/story/story.php?storyId=192277276&sc=tw&cc=share):
“BRENNER: The rules have to be understood. We have people who want to do us harm who are inside our borders. If you find someone overseas who’s really a bad actor out to do us harm, and you find out that somebody in Yemen is having a conversation with somebody in Newark, you need to know that. Now, some people have said, well, why then do you have to collect all the other information about what the rest of us are saying?
The answer to that is you want to know who the guy in Newark was talking to yesterday. And that’s the reason why we’ve needed to collect this stuff and why we have to have really strong rules about when NSA or the FBI can look at it. But that’s why they need it.”
@Adam Colligan: “At least for landlines”
So, ummm, anyone else here ever signed onto a web-based e-mail provider like Google or Yahoo or Outlook and gotten system prompt after system prompt urging you to enter your cell number to protect access to your e-mail account if you forget your password? Anyone else assume the e-mail providers are busy building directories of cell users? Anyone else assume that what happens at Google (et al.) doesn’t stay at Google? Ayuh.
From page 5 of the transcript of today’s CBS Face the Nation and Bob Schieffer’s interview of HPSCI Chair Mike Rogers, R-Mich (http://www.cbsnews.com/8301-3460_162-57589523/face-the-nation-transcripts-june-16-2013-mcdonough-and-rogers-on-nsa-surveillance/):
“SCHIEFFER: And welcome back to Face the Nation. We want to go back to the house intelligence committee chairman Mike Rogers. We were talking about this big story about has the National Security Agency over-reached? What is your take, Mr. Chairman? Do you think the government’s done anything wrong here at this point?
ROGERS: Well, it depends again what you’re talking about when you’re talking about the IRS scandal or Benghazi, I think there were certainly government misdeeds and maybe even criminal behavior. When you’re talking about this NSA issue, the sheer volume of oversight — and we’ve gone back and reviewed every bit of it, the fact that the court ordered it, the court reviews it every 10 days, especially on the phone records. It has to reapply for the court order every 90 days, review there.”
The FISA court reviews it every 10 days? What exactly is “it”? And why would the FISA court have to review anything every 10 days?
When DOJ uses confidential informants to get around ‘entrapment’ and coerces a perp motivated by an offer to reduce sentence by setting-up an associate, technically the government does not entrap.
Similarly, if NSA sends a contractor in for the data…….no problem. Amirite?
@Citizen92: Computer security is always based on one or more of the following:
– what you know, for example, a password
– what you are, as in, biometrics like a retinal scan or fingerprints
– what you posess, for example, a card you swipe or now, a cell phone
That’s why Facebook (and Google and whole bunch of other folks) legitimately want your cellphone number: for two factor authentication. That is, they want to be able to rely both on something you know and something you have. And if you haven’t given them your cellphone number and turned on two factor authentication, you’re putting your accounts at risk.
@Saul Tannenbaum:
They never mention that at all. It’s always presented as ‘in case you lose your password’. (I have my password memorized. I couldn’t tell you my cellphone number without looking it up: I never call it.)
@Snoopdido:
What a lot of BS he threw out there: he knows damned well that the Benghazi and IRS scandals only exist for political purposes, but that the NSA/FBI surveillance thing is very real and could cost a lot of elected officials their well-paid jobs.
@Netmaker: How much OOB, or OS enabled, hacking do you think NSA is doing? There’s no reason (other than the 4th amendment) not to compromise individual computers too. They’ve got the capability.
“Mueller didn’t deny the NSA can get access to US person phone content without a warrant.”
Or rather: ‘without a FURTHER warrant’ — since, as you acknowledge in passing, you don’t KNOW what the government put before the FISA in the first instance (which plan therefore COULD HAVE plainly included a plan to access content to certain classes of communications … including, say, the other end of communications with targets and target numbers, or both ends of communications “linked to” targets or target numbers).
I tried to make this point in an earlier thread: Plans in domestic police tapping schemes designed to work that way have been held — repeatedly — NOT to offend the 4th amendment.
I just didn’t see the level of anxiety, in either Nadler or Mueller, that would suggest that Nadler was particularly concerned with what he was told in the classified briefing, other than he believed he was being told things that didn’t accord with that sort of ‘plan’ and a ‘linked to’ process. The way I hear it, there’s a concern that the particular briefing was wrong, or useless; I actually got the impression that what Nadler was doing was providing a justification for skipping such briefings, for which Merkley has (in my view wrongly) received criticism in opinion media.
On a non-tecnical note, the guardian has another embarrassing (for at least some american officials) nsa story.
What interests me is that there does not appear to have been any concerted effort by the administration to squelch the guardian’s nsa reporting, or for that matter, to squelch the entire u.s. edition of the guardian.
And this with a g-20 meeting impending.
Maybe the plan now is that the principles at that meeting will get together in a non-nsa-tapped pub with only a beer tap, and talk things out over a pint or two – obama style.
@Saul Tannenbaum: There are other much less intrusive means of implementing two factor authentication without providing somebody your phone number.
In particular dedicated one time password devices (OTP – RSA, VASCO, Yubico…) have been widely used for quite some time across multiple industries.
@lefty665: Vacuuming up huge amounts of network traffic can be done on fairly efficient basis.
Given the NSA’s historic activities and methods this would be a natural extension what they have been doing for decades.
Granted, on a scale they’ve not ever been to do before until the huge advancements that have been make in the computer/telecoms/materials manufacturing industries.
Hacking computers on the scale that the telecoms networks are being hacked is not yet practical. Hacking of a specific individual’s computer is trivial absent extraordinary means to protect it.
Certainly there large numbers of computers being hacking on a regular basis by governmental, corporation and criminal entities but the effort to do so requires there a strong motive for doing so.
Two current trends will greatly accelerate the ability of the government/corporations to monitor and control your computer in the future – Walled/curated apps stores and storage of your data/apps in the “The Cloud”.
@emptywheel: “That is, what Nadler may have learned that the same analysts who have access to the phone metadata maby also have authority to issue directives to companies for phone content collection. ”
And that is where we find the difference between the statements from Google et al, and from the leaks. Google may well respond to specific requests even manually but they are assuming the requests come from some form of FISA search when they can come from the analysts and be “narrowly targeted” because they are merely using it to index the stream which they already have.
If so, it would be entirely feasible for the same analyst to learn, via the metadata database, that a suspect phone number is in contact with the US and for her to submit a request for actual content to the providers, without having to first get a FISA order covering the US person callers directly. Since she was still “targeting” the original overseas phone number, she would be able to get the US person content without a specific order.
Oops the last paragraph in my prior quote shouldn’t be there. My bad.
@Netmaker: Thanks, I appreciate your response. This is the essence of my cognitive dissonance:
“Hacking computers on the scale that the telecoms networks are being hacked is not yet practical. Hacking of a specific individual’s computer is trivial absent extraordinary means to protect it.”
NSA has stayed 2-3 generations ahead of the rest of us roughly forever. That is their stock in trade. Except in retrospect it is hard for us on the outside to infer what their capabilities are. Intent is a different question.
For example, NSA’s close cooperation with Microsoft at least since early XP days makes it highly likely that their OS’s are thoroughly exploited. Same with OOB and Intel hardware.
Where is the crossover from a special tool used when needed to a generalized proposition? How trivial does a process have to be to be automated, widely applied, and the output added to the database? The answer I suppose is “it varies”, both by exploit and over time.
You have any sense of how long “yet” is in this case?
@Netmaker: Certainly there are other methods involving dedicated devices and/or apps on phones. But you can’t expect Google or Facebook to be handing out fobs to everybody using their services. And, for the average person, the extra security of two factor authentication outweighs the added risk of giving Google your phone number.
And when the nsa gets the first quantum computers?
They will be able to guess with reasonable accuracy what you are going to say or write before you do so. :))
@Saul Tannenbaum:
It is well within the means of Google/Facebook/Microsoft… to provide a hardware based OTP authenticator cheaply and to drive its market adoption.
Blizzard, has already proven that it can be done for large numbers of customers. For years, they have provided Vasco’s Digipass OTP authenticator for $6.50.
Over time, your routinely handing over your phone number will make it as much as of a unique identifier as your social security number. Without even the weak legal protections that the SSN has.
@lefty665:
While Microsoft has provided access to Window’s source code since at least 2003,
http://news.cnet.com/Governments-to-see-Windows-code/2100-1006_3-980666.html
the different computer environments/ecosystems can greatly impede anybody trying to compromise large numbers of computers. For example, what version Windows, what patches have been applied, what anti-virus/anti-malware is running, what browser, internal firewalls, how much bandwidth is available… And this is hardly an exhaustive list and why considerable effort is required to compromise any significant numbers of computers.
I am confused by your use of the term OOB. It the telecoms world, OOB (out of band) refers to the practice of sending control and management information on a separate path than that used by the content. What does it mean to you?
I don’t see any single threshold that would enable widespread compromising of our computers but more of a mad rush to solve problems in isolation not realizing that in the aggregate we’ve created what we’ve been trying to avoid. For instance a strong single-on standard.
One of the biggest things that people have overlooked, that came out of Snowden’s online chat yesterday, is that FISA, FISA court, FISA judges are ALL BULLSHIT, a show designed to fool general public. Just like the Federal Reserve, FISA appears to be a license for a bunch of crooks and gangsters to do their crimes without being questioned. Even the Congress does not know what FISA people do because it is supposed to be secret. Congress should ask to see all video taped proceedings of FISA court to find out how warrant requests were debated and approved. My guess is none exists because the intelligence community makes its own warrants.
This is what Edward SNOWDEN said:
“Even in the event of “warranted” intercept, it’s important to understand the intelligence community doesn’t always deal with what you would consider a “real” warrant like a Police department would have to, the “warrant” is more of a templated form they fill out and send to a reliable judge with a rubber stamp.”
http://www.guardian.co.uk/world/2013/jun/17/edward-snowden-nsa-files-whistleblower