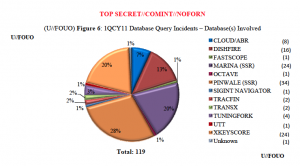
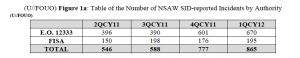
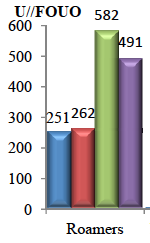
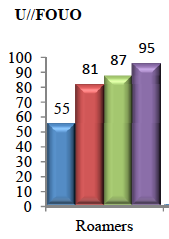
Have There Been Significant Phone Dragnet Violations Since 2009?
As I laid out in more obscure fashion here, there are slight — but interesting — differences between how the 2009 Congressional notice, the 2011 Congressional notice, and the 2013 White Paper on the PATRIOT Act dragnet(s) describe the compliance problems. I’ve laid out all three below.
I’ll have more to say about the differences in a follow-up. But for the moment, note that the White Paper released 11 days ago doesn’t date the compliance issues.
Since the telephony metadata collection program under Section 215 was initiated, there have been a number of significant compliance and implementation issues that were discovered as a result of DOJ and ODNI reviews and internal NSA oversight.
The 2009 one doesn’t either — though it does reveal that the government was only just briefing the FISC that September on its compliance fixes when Silvestre Reyes first asked for this notice (they stalled almost 3 months in responding to him), at least suggesting the recentness of the discovery. The 2011 notice limits the compliance issues to 2009, though.
In 2009, a number of technical compliance problems and human implementation errors in these two bulk collection programs were discovered
Note, too, the different descriptions of the FISC response. Both the 2009 and 2011 assure Congress that the FISC, along with the Executive, found no evidence of bad-faith or intentional violations.
However, neither the Department, NSA nor the FISA Court has found any intentional or bad-faith violations.
The 2011 also reveals that the FISC imposed restrictions on the program — restrictions that surely were in place in March 2009, when Dianne Feinstein and Kit Bond tried to start the PATRIOT Reauthorization program and may still have been in place in September 2009 (there were notices to Congress about the program on February 25, April 10, May 7, June 29, September 3, and September 10, 2009, and briefing materials sent to FISC on the program on September 1, September 18, and sometime in October).
Nice of DOJ to tell Congress that two years after the fact.
The White Paper, however, describes the FISC response — at times — quite differently. It makes no claim about whether FISC found intentional violations. And it reveals the FISC has, on occasion, “been critical” of both the compliance problems and the government’s court filings.
The FISC has on occasion been critical of the Executive Branch’s compliance problems as well as the Government’s court filings. However, the NSA and DOJ have corrected the problems identified to the Court, and the Court has continued to authorize the program with appropriate remedial measures.
Not only is there no claim that the FISC found no bad-faith problems, but it now reveals that “on occasion” the FISC has been critical — critical about both the problems and the the government’s claims about the problems.
There are several possible explanations for the difference in language.
Perhaps, for example, the government revealed FISC’s critical stance because it knew the FISC would read this White Paper, along with the rest of us, whereas the Congressional notifications would originally have never been seen by the FISC. Thus, the Administration would have reason to be far more frank about the FISC’s response than it did in the past.
But in conjunction with the silence about the date of these compliance problems, I do wonder whether FISC has grown more critical since 2011. After all, if there have been violations since this apparently extended effort in 2009 to fix compliance issues, wouldn’t it make the Court crankier?
One more thing to keep in mind. Read more →