WaPo Is Suppressing Information that Might Debunk Devlin Barrett’s Latest Spin
Last week, I asked the WaPo if they would release the two reports — one from Johns Hopkins professor Matt Green and the other from InfoSec expert Jake Williams — that were the basis of this report on the “Hunter Biden” “laptop.”
I had asked once before, in May 2022.
But since I had originally asked, a bunch of things had happened to make those reports more newsworthy. Hunter Biden had countersued John Paul Mac Isaac (here’s the WaPo’s report). James Comer has stumbled over and over in his unabashed effort to manufacture a scandal (in which the WaPo has played along, still treating it as a credible investigation). Delaware US Attorney David Weiss’ office released a plea deal to which Hunter Biden is expected to plead guilty next week (here’s the WaPo report). IRS agents claiming to be whistleblowers, Gary Shapley and Whistleblower X, shared notes that raised questions about the FBI treatment of the device (but WaPo didn’t mention that in their report). Abbe Lowell claimed that Shapley misidentified Hunter Biden’s interlocutors in some key WhatsApp messages (something else WaPo didn’t mention even while repeating the substance of the contested WhatsApp texts). Denver Riggleman, who has been working as part of a Hunter Biden team to examine what has been released, has alleged some of the data has been manipulated (something WaPo hasn’t bothered to cover at all).
That all led me to start looking at the publicly released (but unreliable) emails at BidenLaptopEmails dot com, where I’ve discovered that during a period when Hunter Biden was getting Ketamine treatment and bookended by two communications from him that indicated he was not getting outside comms, someone:
- Split Hunter’s Uber account, on which his two iCloud accounts had previously been joined
- Accessed Hunter’s rhb iCloud account from a browser
- Changed the password and related phone numbers to his rhb iCloud account
- Installed and gave full access to his droidhunter gmail account a real app, called Hunter, that can send email on someone else’s behalf
- Signed into that droidhunter account using a new device
- Again changed emails and phone numbers associated with his rhb account
- Asked for a full copy of his rhbdc iCloud account
- Reset the password of that rhbdc iCloud account
- Made droidhunter account the notification email for the rhbdc account
- Downloaded all Hunter’s Apple Store purchases
- Made changes to the Uber (and Waze) account associated with an XS phone that would be included in the “laptop”
- Restored rhb as an alternate address to the account
- Restored contacts from an unidentified prior change
- Obtained — including at the droidhunter email account — a download link of the entire rhbdc iCloud account
- Backed up the XS phone to the laptop
- Gotten a trial app of a photo editor
- Backed up an iPad to the laptop
- Changed the iTunes password
- Added the Dr. Fone account, allowing you to adopt a chosen second phone number for a phone, to a second of Hunter’s accounts
- Signed into the droidhunter account from a burner phone
- Restored the prior trusted phone number
- Added software that could record calls
- Started erasing and then locked a laptop — probably the one that would eventually end up in Mac Isaac’s store
- Got a new Mac phone for the droidhunter account
That series of changes are not the only emails in the MarcoPolo set that should raise questions about whether Hunter Biden’s digital identity may have been compromised.
Two that are important to the topic of this post are, first, that a great many devices logged into Hunter Biden’s iCloud accounts in 2018 and 2019, yet many of them don’t appear to be tied to him getting his own new iPhone or computer, and only rarely are the existing devices shut down or passwords changed afterwards. The sheer number should have raised alarms that people had broken into Hunter Biden’s iCloud accounts when the IRS asked Apple for Hunter Biden’s subscriber information in November 2019, in advance of writing a subpoena for the laptop in custody of John Paul Mac Isaac. Additionally, there were a bunch of attempts to get into Hunter Biden’s Venmo account, and the account added two new Remembered Devices within 12 minutes of each other in August 2018, one in the LA foothills and the other in Las Vegas. That and other details (including texts and emails) might have raised questions about whether sex workers from the very same escort service on which the IRS had predicated this entire investigation took steps to compromise Hunter Biden’s devices.
But the timeline above provides some reason to believe that at the time the “laptop” was packaged up for delivery to John Paul Mac Isaac, Hunter Biden did not have complete — if any — control of his own communications.
I wouldn’t be able to prove whether Hunter Biden was hacked during this key period in 2019. It would require subpoena power and access to reliable data. But as it happens, Whistleblower X had subpoena power — and was already watching Hunter Biden closely — in precisely the period this happened.
For those of us who don’t have subpoena power, though, we have to rely on publicly available evidence, filtered through partisan gatekeepers alleged to have tampered with the device.
The two reports done for the WaPo are the only known assessments of the drive containing the “laptop” primarily using forensic — as opposed to a correlative — methodology. The correlative methodology, which shows all the communications on the drive confirm the others, unsurprisingly concludes that the “laptop” came from one of Hunter Biden’s several iCloud accounts.
The forensic methodology looked for digital verification — not just of email signatures, but also of the drive itself. Both Green and Williams raised questions about the treatment of and missing digital signatures on the drive, questions that seem to match what Riggleman’s team is seeing.
Indeed, the concerns that Green and Williams raised may explain something the FBI itself found. Shapley’s notes recorded that on March 31, 2020, someone wrote an email “about quality and completeness of imaged/recovered information from the hard drive” — an email that was being intentionally withheld from the agents (especially Whistleblower X) who might one day testify at trial.
This sounds like it might reflect the same concerns raised by anyone external examining the drive forensically. If it does, it would suggest that some of the irregularities everyone can see in drives released via Rudy Giuliani and Steve Bannon always existed, including in the one shared with the FBI and in any separate drive shared with Republicans in Congress.
Because of all the new questions raised about the “laptop,” and because of the centrality that the Republicans want it to have on the upcoming election, I thought it reasonable to ask the WaPo to do what even the Washington Examiner was willing to do: show their work. While the Examiner’s report from Gus Dimitrelos tellingly excludes many of the details I’ve laid out above and hides both some key later device accesses and types of apps — especially spyware — loaded onto Hunter Biden’s iCloud accounts, while the way the Examiner released it exacerbated the privacy violations on Hunter Biden himself, it nevertheless was useful for explaining how two iCloud accounts were loaded up onto one laptop and how the government was able to obtain WhatsApp texts that don’t show up on the unencrypted parts of the laptop.
After I made several requests, WaPo PR manager Savannah Stephens declined to release the reports, calling the two reports, “foundational reporting documents.”
Marcy, thank you for reaching out. We do not release foundational reporting documents. Our coverage at the time was transparent about how the study was conducted, including this report.
Even though it has two reports that could significantly impact fairly pressing debates — debates the WaPo itself treats as important — the WaPo refuses to release more on these expert reports on the laptop.
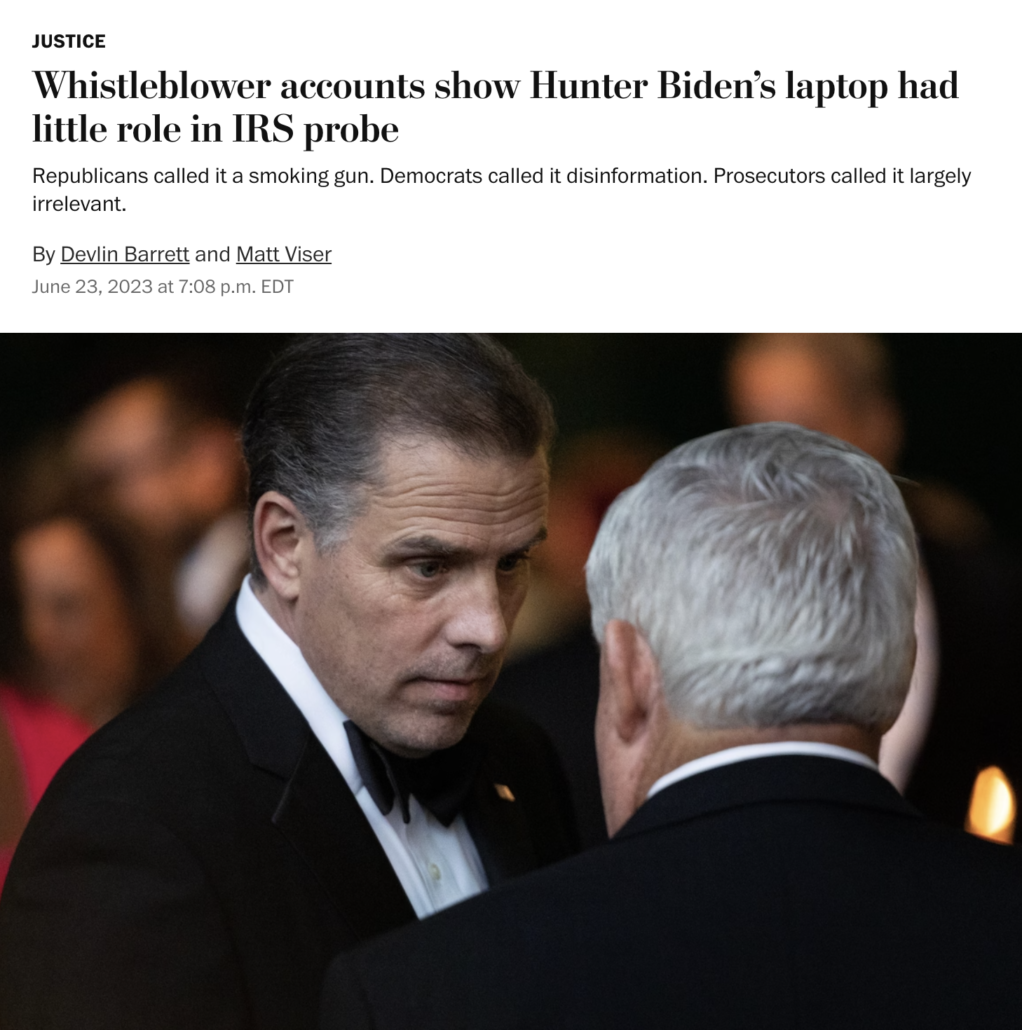
Instead of doing that, the WaPo is instead paying Devlin Barrett to do what he does best — write down as true what right wingers tell him to write, not what the public evidence actually shows.
In a story with Matt Viser (the same guy who repeated the content of contested WhatsApp texts without revealing that Abbe Lowell had contested them), Barrett wrote that the testimony of the men he calls “whistleblowers” “show Hunter Biden’s laptop had little role in the investigation into Hunter Biden.”
Barrett and Viser utterly misrepresent the debate over the laptop — dodging the question, in the lede, at least, of whether the laptop can help get to the truth — something once considered the purview of journalism and something WaPo’s own report on this drive had previously done.
For more than two years, Democrats and Republicans have hotly debated the importance of the “Hunter Biden laptop” — insisting that it was either key evidence of corruption or fool’s gold meant to con 2020 voters into abandoning then-candidate Joe Biden.
Both theories were largely wrong, according to two of the agents closest to the investigation of tax crimes allegedly committed by President Biden’s son.
[snip]
But the agents’ accounts also indicate that the laptop played at best a small role in the criminal investigation into potential tax and gun-purchasing violations. Far from a smoking gun, the laptop appears to have been mostly an afterthought to the reams of text messages, emails and other evidence that agents gathered from Hunter Biden’s cloud data. A lawyer for one of those agents said he nevertheless was frustrated by the Justice Department’s refusal to let them review the laptop’s contents.
I’m very interested in the project of this column, because not only is this not what Shapley and Whistleblower X’s testimony said, but it misrepresented and misunderstands how evidence works.
This is a tax investigation. It came from, per Whistleblower X, his examination of what is probably a Russian escort service. But it’s a tax investigation: it relies on financial data that comes directly from banks and other financial institutions, institutions that are — to the extent they aren’t tainted by identity theft or hacking, like people seem to have tried to do to Hunter Biden’s Venmo — inherently reliable.
As for emails and texts, the IRS agents’ testimony (taken in conjunction with the report that the Washington Examiner was ethical enough to release), shows that the IRS didn’t obtain what is probably Hunter Biden’s rhb iCloud account — from which the cited, contested WhatsApp messages were probably obtained a second time — until August 2020, after it got some of the same material on the laptop. That potential taint may be why someone told Barrett to downplay the import of the laptop.
While the laptop may not have played a key role in substantiating a tax case against Hunter Biden, it may well have tainted the evidence in the case. It may well be part of the reason why Hunter Biden is getting to plead to misdemeanor rather than felony tax charges — because as even Whistleblower X explained that he had been told, there are emails that raised concerns about whether this could be charged at all, suggesting this case couldn’t withstand discovery.
Plus, WaPo is being coy here: The laptop may have played little part in a tax investigation reliant on bank records. But it did play a central part in allegations, including WaPo’s own reporting, of foreign influence peddling involving (among others), Burisma, the hack of which became public between the time the IRS started using this laptop as evidence and the time they learned Rudy Giuliani had a role in it.
That part is all pitch, though — yet another instance where Devlin Barrett writes down what right wingers tell him to say and WaPo reports it as if it were true. It’s what WaPo pays him to do.
It’s the claims about the laptop — from an outlet sitting on two reports that raise questions about its reliability — that I find especially curious. Start with this paragraph, which conflates the steps FBI took in November 2019 to authenticate that the laptop was Hunter Biden’s — subscriber information from Apple, a purchase record in Delaware, two but maybe only two phone calls with Mac Isaac, and “other intelligence” — with what the AUSA on the case said about it almost a year later.
After being handed the device by a Wilmington, Del., computer shop owner in 2019, the FBI quickly concluded by examining computer data as well as Hunter Biden’s phone records that the laptop was genuinely his and did not seem to have been tampered with or manipulated.
That last bit — “did not seem to have been tampered with or manipulated” — published by an outlet sitting on two reports that show the laptop was tampered with? It is a paraphrase from a meeting in October 2020, not a description of legal process served in November 2019. And therein lies a big part of the scandal.
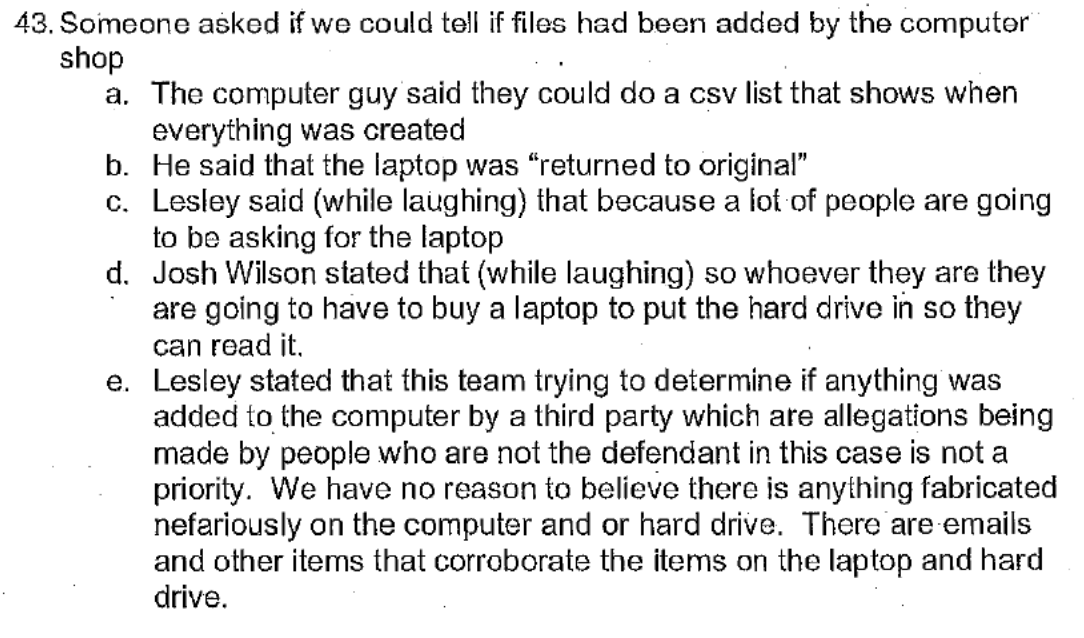
In the actual quote, Wolf — painted as the bad guy here by the IRS agents — was saying that it “is not a priority” for the investigative team to see “if anything was added to the computer by a third party” even after learning that the lawyer for the President, whose demands for this investigation had raised influence problems from the start of the investigation, had some kind of tie to it.
This is as if Peter Strzok, rather than just failing to make sure people writing FISA applications had adverse information about the Steele dossier (which is what frothers think the IG Report showed), had instead said, “fuck it, I don’t care if it is tainted.” These notes show the Hunter Biden investigative team did what right wingers accuse the Crossfire Hurricane team of doing, blowing off the import of the involvement of a campaign in a key piece of evidence.
When the WaPo conflates those two items again later in the piece, they date the quote to May 2020.
Democrats suggested the data might have been doctored or possibly a Russian-backed disinformation campaign. The information provided by IRS agents to Congress seems to put both the accusations and counter-accusations to rest.
FBI agents were able to determine in early November 2019 that the device they had was registered to Hunter Biden, and phone records showed he had been in contact with the computer shop owner.
“We have no reason to believe there is anything fabricated nefariously on the computer and or hard drive. There are emails and other items that corroborate the items on the laptop,” Shapley wrote in notes that dated that determination to around May 2020.
Dating Lesley Wolf’s comment saying they had no reason to believe anything on the laptop was fabricated to May 2020 is either a deliberate error or a confession that two journalists proclaiming the laptop to lack any taint have no fucking clue what they’re reading.
Wolf said this, at a meeting the investigative team had on October 22, 2020, in the wake of the discovery that Rudy Giuliani had some tie to the laptop, as the team scrambled to memorialize how they had treated a key piece of evidence about which a bunch of questions would now be raised.
A Yes. So there are a couple significant parts of this. One was that, at this time, the laptop was a very big story, so we were just making sure that everything was being handled appropriately.
So we wanted to go through the timeline of what happened with the laptop and devices.
Because the laptop had become a huge story, “we were just making sure that everything was being handled appropriately,” Devlin Barrett’s star “whistleblower” explained.
And Shapley shows Wolf saying that they had no knowledge, in October 2020, of any fabrications on the laptop. But he records her saying that after “computer guy” said “they could do a csv list that shows when everything was created.”
That is, Wolf said this after “computer guy” described something they had not yet done ten months after obtaining the laptop, had not yet done two months after getting warrants relying on the laptop, that they would need to do to make sure the laptop had not been altered by third parties. Wolf said this after “computer guy” described that the FBI had not done very basic things to verify the integrity of the laptop they should have done ten months earlier, before relying on it.
Again, I’m not sure whether WaPo’s journalists are dishonest or just stupid. But this exchange is critical for another reason. Lesley Wolf’s assertion about the integrity of the laptop relied on correlation: by matching emails on the laptop with emails that could be obtained directly from the provider.
There are emails and other items hat corroborate the items on the laptop and hard dive.
This is the method that Washington Examiner’s expert used to proclaim the laptop authentic. It’s the method that a bunch of other right wing journalists have gotten experts to use to validate the laptop.
If you steal someone’s iCloud account, the way to prove that it is authentic is by proving that it is their iCloud account, which is what correlation does.
But “computer guy” was suggesting using a forensic method, ten months after the fact, to test the integrity of the laptop itself. DDOSecrets has done this test on the publicly released emails — and half of them have a last modified date of February 11, 2019, right towards the end of the timeline I show above.
Lesley Wolf made her comment on October 22, 2020. No one in Gary Shapley’s interview asked him what happened after that. Nor does Devlin Barrett seem curious to ask.
If “computer guy” subsequently did this test, there’s good reason to believe he would have found what DDOSecrets did: that while these emails match the ones in Hunter Biden’s accounts, they were all packaged up on February 11, 2019, at a time it’s not clear Hunter Biden had control of his own digital accounts.
If you use a forensic method to validate these files, you’re not going to get the same results as a correlative method. That’s why it would be very useful for the debate about the laptop for WaPo to share the two known expert reports done using forensic methods on the drive itself, rather than correlation.
There’s one more hilarious thing about this Devlin Barrett creation. He, predictably, repeats his “whistleblower’s” complaints about not getting stuff pertaining to the laptop.
Shapley said a federal prosecutor on the case, Lesley Wolf, told him that the IRS agents couldn’t see the laptop. “At some point, they were going to give a redacted version, but we don’t even think we got a full — even a redacted version. We only got piecemeal items,” Shapley told the committee, voicing his frustration that he would have liked to see all the data.
Devlin Barrett — dishonest or stupid? — quotes Shapley’s testimony out of context. The full quotation makes it clear Shapley is referring, again, to a discussion that took place on October 22, 2020. More importantly, Shapley is not referring to the laptop!!
And when it came down to item number 33 on page 2, Special Agent [Whistleblower X] is saying like, well, I haven’t seen this information. And AUSA Lesley Wolf says, well, you haven’t seen it because, for a variety of reasons, they kept it from the agents. And she said that at some point they were going to give a redacted version, but we don’t even think we got a full — even a redacted version. We only got piecemeal items [my emphasis]
That particular quotation, identified clearly as item number 33, is the report about the laptop — which I’ll copy again here to make it so easy even Devlin Barrett might understand it:
To help a right winger allege corruption, Devlin Barrett quotes his complaint that his team was not given the actual forensic report about the laptop. Corruption, in this story, is withholding a forensic report that might tell people what they need to know about the laptop.
And yet that is precisely what WaPo itself refuses to do: release two reports that raise questions about the quality and completeness of the drive.
According to Devlin Barrett’s own standard — at least the standard he applies when he’s parroting right wingers — withholding such a report is a sign of corruption.
Even the plain language of Gary Shapley’s contemporaneous notes show that Devlin’s claim that, “information provided by IRS agents to Congress” “put[s] … the accusations” that “the data might have been doctored or possibly a Russian-backed disinformation campaign” … “to rest” is wildly false (dishonest or stupid?). It does the opposite: It shows that ten months after beginning to rely on the laptop, the FBI still had not done basic forensic checks of the data on it and the AUSA leading the investigation didn’t think doing so was a priority.
That should be the story. That’s the scandal.
And true to form, Devlin Barrett spins the exactly opposite tale.
The WaPo has in its possession some of the only available information that can help to explain what the FBI saw by March 2020, two independent equivalent reports to the one that Shapley implies it is corrupt to withhold.
And unlike the Washington Examiner, they won’t release it.




Marcy, your research is priceless. Some day, probably after we are all dead and buried, it will be part of an historical review of the laptop story along with Teapot Dome, Watergate, other examples of corruption in our Great Experiment. The extent of the data diddling and the use of it by a once-admired news org is gobsmacking.
Agree! And I do hope some arrangement has been made to permanently archive all the contents of this site (less identifying information on the commenters).
I’m pretty sure that was in hand on day one, more than a decade ago, and equally sure we’ll never hear about it. Not all interested parties are benign.
Now THIS is yet another example of top shelf investigative journalism. Full Stop.
Even the feeble minded should (would) be hard pressed to believe that Hunter Biden was ever capable of, much less under the influence of ketamine, pulling off any part of the bulleted list of tech tasks listed. I hope this somehow ends up in a court trial.
We appear to know what was done to the devices and when, but by whom? A modern day technical game of Clue.
Pete
Agree completely, and everything in here makes sense from a tech perspective. It seriously bothers me that newspapers and TV channels with reporters who SPECIALIZE in tech and information security and who could call on any experts they want couldn’t take the time to get the facts straight and dig into the tech, the timeline and the strong likelihood that the laptop was compromised.
[Welcome to emptywheel. Please choose and use a unique username with a minimum of 8 letters. We are moving to a new minimum standard to support community security. Because your username is far too common (many Steves already here in the community) it will be temporarily changed to match the date/time of your first known comment until you have a new compliant username. Thanks. /~Rayne]
I should not be the one trying to figure out what each account change in quick succession in 2019 might have done to Hunter’s account. It makes me wildly despondent about the status of journalism that I had to try it .
I think Barr combined the two investigations because he knew there were no grounds to seize the laptop based on evidence of financial crimes. He needed the laptop’s porn pictures and videos to link the laptop to the “sportsman” investigation of the amateur pornography ring. Once Barr was able to conflate the two investigations as one, the porn case apparently dried up.
Excellent exposé.
“Devlin Barrett — dishonest or stupid?”
I think the most likely correct answer is “dishonest AND stupid.”
Apologies for what’s probably a dumb and/or already answered question but Wray and others have declined to answer certain questions citing an “ongoing investigation.” Rather than an ongoing investigation of either Hunter or his dad, might that investigation be focused on the malfeasance of others? More akin to matters relating to Ashely’s diary?
One of the WaPo experts didn’t accept any payment for the work. Would he be willing to release his report publicly, or is there a contractual reason that he can’t?
My question too. I’m guessing WaPo owns the work product in some way; that in itself would be worth investigating, as yet more reinforcement for EW’s argument about how a supposedly truth-telling media in fact colludes with corrupt political entities.
I wonder if EW tried asking them?
I did, last year. It was generally treated as work product by both.
IANAL. That said, there has to be “consideration” from one party to the other party for a contract to be legally binding. If Green and/or Williams received no “in-kind” compensation, then they would be free to disclose their work product, assuming they wished to do so. Example: Stephanie Winston Wolkoff was never paid by Melania Trump despite a non disclosure agreement (per trump White House). Legally, there was no contract and Winston Wolkoff could publish her book about Melania without any legal interference from Melania.
It’s probably rare for the WaPo or NYT to run stories about which it did not own the work product.
“Autocracy Thrives in Darkness.”
“Democracy Dies in Dumbness” as well.
Fine reporting and even better detective work.
Matt and Jake are excellent and highly credible. It’s a shame the Post won’t release their analyses, because I would trust their methods implicitly.
[NB: I changed my username to meet the length requirement.]
O/T but…!!!!!
https://nitter.net/kyledcheney/status/1681294065759920129#m
Jul 18, 2023 · 1:25 PM UTC
Not to detract from this [yet AGAIN] amazing post, here’s the most recent kind-of on topic post for further discussion if anyone’s interested:
https://www.emptywheel.net/2023/07/13/poof-how-jack-smith-made-800000-pages-into-4500/
BETTER recent on-topic post:
https://www.emptywheel.net/2023/07/14/maggie-and-mike-back-together-again-this-time-on-or-with-corrupt-purpose/
BEST: a NEW post [Marcy never ceases to amaze me!]:
Jack Smith Gives Trump Until Thursday to Explain Himself to the January 6 Grand Jury https://www.emptywheel.net/2023/07/18/jack-smith-gives-trump-until-thursday-to-explain-himself-to-the-january-6-grand-jury/
Re: “The WaPo has in its possession some of the only available information that can help to explain what the FBI saw by March 2020,” maybe I’m missing something, but I don’t see how Green’s and Williams’ analyses can explain what the FBI saw, because they’re not analyses of the same hard drives, and we don’t know to what extent the contents differ. In subsequent reporting, it might be helpful to name the various hard drives (e.g., Mac-Issac-Giuliani-Maxey-laptop, Mac-Issac-FBI-Western-Digital) to more explicitly track which hard drive one is talking about and whose hands it passed through / whose hands might have altered it. That said, having access to Green’s and William’s reports would still be useful.
If I had the power to bestow the “I. F. Stone Lifetime Achievement Award” on Marcy Wheeler, I sure as hell would do it this morning. Thank you, Ms Wheeler. It is a privilege to read you.
Dimmsdale – Totally agree. Well said!
Dr. Wheeler, I have a question for you about how us folks without IT brains or your amazing sluething skills might help in this matter.
I’m not on social media anymore but I do subscribe to the Post and I know a few other folks who frequent here do as well, so my question is this- Is this important enough to start a campaign of public pressure on the Post to release the two forensic reports the Post’s refusing to release?
One of the right’s strengths is its ability to galvanize its’s followers in a wide spectrum of campaigns from contacting Congressional leaders, making FOIA requests, trolling, you name it. This is an opportunity in which not just politically left of center folks but a variety of stakeholders could be motivated on social media and in the comments section of WAPO to contact the editor you mentioned above and provide boilerplate language for use to request those reports be made public for the common good.
This may not be something you’re interested in, but if you are, I’m pretty sure you have your own small army who can act as force multipliers of pressure to release the reports. And I think it would have the side benefit of empowering those on the left who often feel manipulated and outmaneuvered by the outrage right and their tactics.
What say you? I understand it might not be good politics for this, but if you’re interested I have plenty of time to write an email and work the comments section of WAPO for the next few days.
When the political leanings of management get in the way of actual reporting, part number….
I encourage others here to write to WaPo editors: [email protected]
“Today, I am taking a financial step away from my next payment of a subscription to your paper my go-to alternative news reference to NYT. I am sending 50% of my upcoming renewal to https://www.emptywheel.net/. The tethering scaffolding that Devlin Barret writes from while covering the Hunter Biden mess is similar to the one constructed by NYT’s M. Habberman’s to sanitize coverage of former President Trump’s indictable acts. It is too obvious to me and it does not serve my most basic “referencing” need. I am one of your readers with the patience to seriously consider the details of the political stories whose surface you lightly brush. I am amazed that a blogger without your resources and Amazonian wealth can illuminate the truths better for me, Please realize you are betraying the “foundational” journalistic legacy you purchased/acquired from the Graham family”
Yes. I wrote & sent an email to WaPo in much the same vein as yours.
I’m nodding along and probably understanding 30 percent of the technical details being detailed here.
What I’m getting though is a comparison to the Feds’ investigation (or lack thereof) of the Alfa Bank episode. Most people assumed something weird was going on but didn’t have any concrete evidence to make educated guesses.
Then MW used testimony from people that Durham and Comey put out there in each case. And those testimonies show a lack of curiosity or technical acumen that leaves both Alfa and HB open to more questions about the methods or expertise being used to “solve” these issues.
Is it the subject that causes these seemingly skipped steps or do feds just not have the expertise to appropriately solve them? It almost makes me question the USSS’ vaunted reputation for computer analysis and retrieving deleted data. If we looked at their investigation logs, would experts see the same sort of dismissibe derision and missed opportunities?
Apologies if I’m making leaps of logic here. Just seems like a second thing I’ve read here where important details are left on the cutting floor at the outset by the “experts”. Then by the time someone like Wheeler starts diligently poking at it, it’s that much more difficult to unwind.
I for one, think you make a very good point.
Marcy clearly outlined how cursory the FBI investigation into the Alfa Bank anomalies were.
It would seem like initially at least, the same level of expertise was applied here.
Worrying to see.
Interesting point. You summed up- here. Thank you.
I think it is important who gets assigned to investigate these technical issues at FBI.
The investigators are assigning which technical guys to use and what to look for.
If there are no technical FBI experts assigned and no probing questions to assure they get to the bottom of inconsistencies, then the results are garbage. You cannot make assumptions you operate on good data unless the data is verified, authenticated, and data integrity is confirmed.
Like they say, garbage in, garbage out.
The FBI probably has tools that make it easy to debug the laptop but somebody that knows what they are doing would need to know to look closely at these details.
The FBI agents, I assume, just rely on the FBI technical team expertise.
I am wondering if the FBI started to realize some of the problems with the laptop after Hunter defense team pointed some obvious issues.
This reminds me of the story I read about Mike Lindell challenge, worth $5M, about the voter fraud data ML was claiming he had. A conservative network forensics Trump supporter got invited to the ML challenge conference (only GOP/conservatives/MAGA could attend). He won the challenge, meaning he was able to relatively prove easily the data is bogus, the network traffic that supposedly showed voter fraud was dated after the election actually took place so it could not be traffic from the actual voting machines. It was huge amounts of network captures that were created with the hope that nobody will actually dig thru the vast amount of data.
Once you knew what to look for, it was easy to prove all packets were bogus.
Despite Bob Zeidman winning the challenge, he’s still waiting for Lindell to pay up. And Lindell is busy liquidating pillow-making machinery now that he’s up beyond his lying eyes in legal debt.
https://www.politico.com/news/magazine/2023/05/26/my-pillow-mike-lindell-investigation-00097903
Great story. I missed it. Thanks.
“ It almost makes me question the USSS’ vaunted reputation for computer analysis and retrieving deleted data. If we looked at their investigation logs, would experts see the same sort of dismissibe derision and missed opportunities?”
It’s not just technical analysis. The fundamental rules and procedures weren’t even followed. In this country, the burden of proof is on the accuser, that standard is even higher in criminal cases. Yet they made no attempt to simply investigate what proof they had could withstand even a cursory inspection by a court. Everyone involved needs a refresher in proper evidence gathering with an emphasis on what would be court ready should it even reach that stage. It’s almost like they weren’t intending to bring a case.
This is a really good analysis and I hope they make the 2 forensic reports available to the public. It’s newsworthy, and democracy dies in darkness right?
Also I re-read the Dimitrelos report and your article with the iCloud timeline. Does Dimitrelos imply on page 13 that Hunter only has 1 Apple ID and that it is the one with the iCloud . com email address?
from the final report:
55. It should be noted that ‘Robert’s MacBook Pro’ laptop listed above was authenticated and
connected with the icloud.com account 1 day after the user account ‘roberthunter’
was created on the MacBook Pro on October 21, 2018.
56. RHB sent and received thousands of emails using the macOS Apple mail application, his icloud.com account and other personal and business email accounts.
57. An Apple ID is the account you use to sign in to all Apple services. Since 2011, RHB’s Apple ID has been consistently and has been authenticated using his below devices and associated connection dates in ascending order.
And then there follows a table with the device s/n, name, and “Associated Date”. Many of the devices are listed twice. Some listed only once.
Device Named by Owner/User s/n Associated Date
Bobby’s MacBook Pro C02830506M3JH4T17 2018-09-01T17:35:54Z
Bobby’s MacBook Pro C02830506M3JH4T17 2018-09-02T11:26:37Z
Roberts MacBook Pro FVFXC2MMHV29 2018-11-15T10:43:18Z
But your article has the following line:
10/21/18: Your Apple ID ([email protected]) was used to sign in to iCloud on a MacBook Pro 13″. Date and Time: October 21, 2018, 5:50 AM PDT
Questions:
1. Hunter has 2 Apple ID’s right? rhb@ rspdc . com, and rhbdc@ icloud . com, right? right? [Part of my confusion is due to me not being familiar with Apple IDs and how they work]
1a) Dimitrelos provides an Apple ID number in the table, which is redacted so it doesn’t show if all of the numbers are identical or 2 separate numbers. If 1 person has 2 Apple IDs, are they merged together to 1 Apple ID number, or remain separate numbers?
2. Is Dimitrelos implying that there is only 1 Apple ID? and that the only Apple ID is the one with the iCloud . com domain? Would he have to go out of his way to be deceptive about the Apple IDs? or am I just ignorant how Apple ID’s work?
3. Why do some of the devices have 2 “associated dates”? 1 for each Apple ID? Can a device unassociate from the laptop and then associate again to the same Apple ID?
4. Why does he give the Mac Isaac laptop Robert’s MacBook Pro an associated date of 11/15/18, but you provide an email from 10/21/18? And why doesn’t it have 2 dates listed in the report like the other devices?
Okay, not a Mac person but I’ll see if I can explain. It doesn’t help I’m going off memory when I wasn’t paying attention.
1. Way back, long ago, Apple used to allow customers to register with a unique ID (these had no extensions, and I think only one word, an Apple/Mac user would know better), then when some of their services became widely available to non Mac users (like iTunes) they allowed non Mac users to register using their email address as the Apple ID. Then when iCloud rolled out they did the same thing, but encouraged existing customers to use their existing Apple/iTunes accounts instead of creating a new ID.
1a. Those aren’t Apple ID’s, but instead are device ID’s, I think those are processor serial numbers, or it could be a combination to create a unique ID including processor SN, hard disk, memory capacity, etc. I remember iTunes had a 5 device limit for linking a new device to an account, even when only one change was made to that device, it was considered new. There was a way to reset the count but it was a PIA as I recall. One other thing. Family Sharing, I remember when they first rolled it out, there was no sharing available, didn’t take long for them to allow parents to share their iCloud accounts with enough controls, so that their kids couldn’t run up big CC bills.
2. Have no idea what he’s thinking.
3. Yes, see 1a.
4. Unsure, could be a typo.
Thanks, that’s helpful.
1a) in the Dimitrelos report, there’s actually a column labeled “Apple ID Number”. All of the entries are redacted. Different from device ID.
4) could be a typo? Wow. Imagine a cyber forensics guy putting out a report like this with a typo that consequential, and the whole word draws conclusions based off that typo?
1a) The only Apple ID’s are the email address used to create an iTunes account, fathered in Apple IDs and newer created iCloud accounts. Unless he’s talking about Apple’s internal tracking. I have no idea where that info could be obtained without a warrant. As I stated elsewhere, Apple knows every device that connects with its servers. and everything those devices do while access is granted.
4) It happens unfortunately. At least it’s not as bad as Ramsland’s report on voting irregularities in the Michigan 2020 Election, where he listed the troubled towns (over voting) that match towns in Minnesota, and the totals he gave didn’t match any totals from any other state. Don’t know if it would be serious enough to get it tossed in a court case, unlike the Ramsland report, hopefully they would clean that up before it was submitted.
Remember, all these reports legally mean nothing until they get submitted as evidence in a court.
As I noted in this post, basically 133 pages into Gus’ report, he notes that the rhb one is “another” iCloud account.
https://www.emptywheel.net/2023/07/12/hunter-bidens-matryoshka-cell-phone/
Before that he suggested the iPad (working from memory) actually was tied to another one.
Hallie’s account is tied up here, but I’m not sure how yet — several times, “family share” was set up on Hunter’s account, so linked accounts would be shared.
I don’t understand how the interlinking works. What I’ve come to think of, for working purposes, is that the rhb one was work (so had rosemontseneca tied to it), the rhbdc was personal (so had droidhunter tied to it). My guess is the Uber got linked to ensure he’d get both personal and work Ubers.
Thanks. I’m able to follow along in that article better now than the first read.
As of 6/25/18, droidhunter is linked to rhb, and rosemontseneca linked to rhbdc
As of 9/2/18, droidhunter is linked to rhb, and rosemontseneca linked to rhbdc
On 11/20/18, password changed for droidhunter and it becomes linked to rhbdc
Another outstanding article from EW. I’m left wondering how, if at all, this relates to Trump’s call with Zelinski later that year.
There is a lot of suspicious information appeared that you point out that indicate someone besides Hunter is access his data.
But on this one point, having looked through the data, I have reason to believe that it was Hunter himself.
“Installed and gave full access to his droidhunter gmail account a real app, called Hunter, that can send email on someone else’s behalf”
I haven’t looked closely at the the 1/16/19 instance when this Hunter app email occurs, but for the 2/9/19 instance there is other data. For example, within the same 4 hour window as the gmail changing passwords and Apple ID via a browser, there is a sign up for Hunter app, then a “test” email to a woman who is likely in the room with him as they record a movie together, as they did the previous day. There is also a test email sent to his own gmail from his gmail, minutes before the record. So, if it were someone else using the Hunter app to access his emails, they would have done so know who was in the room with him, and that they were about to record, and sent them an email.
So, I suspect that was him and not somebody else, but then again, who knows.
What’s the chances Hunter did it under the influence of ketamine?
1/30/19: date likely taken ketamine, selfies at the clinic, I don’t know how many times he took ketamine, if it’s daily or not
2/4/19: has definitely left Ablow’s Cottage, heading south on I 95 to DE
2/9/19: date referenced above
How frequently is ketamine taken? How long does it stay in the system? Any evidence he took it outside of Ablow’s treatment? I have no clue.
Also after the activities on 2/9/19 from my previous comment, as EW has pointed out previously, there are several changes to Apple ID around 8:30pm to 10:30pm. New email added, the 96 phone number added, new sign in to a MacBook, new sign in to iPhone 6s. Add the rspdc . me email as recovery.
This stuff definitely looks suspicious. EW has also suggested mentioned one of the phone devices was kept and not traded in to Apple, so potentially there is another phone that could accept calls from Mac Isaac and pretend to be Hunter.
Is that phone the iPhone 6s? Is it the phone ending in 96, which was the one printed on the receipt from Mac Isaac?
Also, very, very suspicious, a few hours later, at 1:19am, there is a document created which is a copy of a Burisma contract which was signed on 9/3/18. (Dimitrelos p 7)
45. Unlike the previous signed contract located as a stored file on the ‘roberthunter’ desktop, the below signed contract is stored internally in the Gmail.mbox as an email attachment located under 12 nested olders. Unlike the default macOS user folders such as Desktop, Document and Downloads, this nested Scan 1.jpeg file is stored by the Mail application in a nested folder not accessed by the computer user ‘roberthunter’.
What to make of that? Did someone else access Hunter’s account on an older iPhone 6 and then sought out a Burisma doc? Or did Hunter login in to a device he hasn’t used in months and some sort of save process continued that had been paused?
Also, should not, Hunter purportedly has just left behind a laptop at Ablow’s office, so he would be short 1 device, increase chances of needing to login to an old device.
Ketamine?
Who’s going to play Keith Ablow in the movie?
How about the Russian honey-pot?
You’re describing people testing whether they fully owned his account. You are literally describing the opposite of what you think you are.
So one test email was sent to a woman was presently in the room with H 1 minute after Hunter app gets access to droidhunter email. The test “jk” email from droidhunter to itself is 2 minutes before they start to record.
Doesn’t it seem like whoever sent the test emails and set Hunter app to the email would have to be aware of the situation? Aware who is in the room physically w H? Do you think woman was in on a data theft if that is what did happen at that time?
Btw, there is a charge for The District Hotel in DC for 2/6/9, 12 min walk from K street, night of the Lyft collision (which I still haven’t come across, only what is in your article)
For WaPo, those reports are property that are more valuable if not disclosed. They want to be the sole source regarding forensic analysis, and do not care about a mission to provide disclosure in the public interest. It’s similar to a journalist sitting on hot quotes to be used later for a book. There is more profit in the book than in prompt public disclosure.
A likely explanation for the Venmo account being used in LA and Las Vegas minutes apart 8/6/18 in the afternoon.
Hunter was in Vegas, and per MPR page 425, texted is based drug connection, who hooked up H w a drug source in Vegas. The prior night/morning, they were trying to coordinate payments via apps. Is it possible that H gave the LA dealer his account info to send pmt to his buddy in Vegas? 12 minutes after that, a device in Vegas becomes a trusted Venmo device. Would that be Hunter retaking control of his Venmo after letting someone else take temp control? With Venmo, is there only 1 trusted device at a time?
Or some sort of coordination between 2 different people stealing Hunter’s venmo?
This was also 2 days after a Russian drug dealer allegedly stole his laptop night of Aug 4/morning Aug 6 and he may be short a device and trying to make pmts flow to drug sources.
The DDOS link has forbidden access, as do some of the archives on wayback.
Here is an archived link
https://web.archive.org/web/20220522173852/https://ddosecrets.com/wiki/Hunter_Biden_emails
Yup. Sorry. That’s fairly new.
Marcy’s live-tweeting the Comer Circus.
https://nitter.net/emptywheel/status/1681765416329261058#m
Jul 19, 2023 · 8:38 PM UTC
That ddosecrets link doesn’t work—”bad gateway” error.
GREAT WORK MARCY!! (as always)
Want to let you know that it was a WaPo commenter that posted a link (https://www.washingtonpost.com/politics/2023/07/19/marjorie-taylor-greene-hunter-biden-photos/?commentID=904b0117-559f-40b3-ad79-859d90ff1ecb) to this new piece, and that’s how I ended up here. Maybe ask people to do that to put the pressure on?
Thom Hartmann just went through the gist of this story in the opening segment of his third hour of today’s radio show, immediately following the 2pm so-called news on the SiriusXM broadcast.
He described the account transfers and password changes that occurred while Hunter was laid up with ketamine treatment, basically summarizing Marcy’s bullet list in just a few sentences sans the details. But he framed it as “they have found”, not mentioning Marcy or any journalist that did the finding. He also added another element, “they” suspect Russian hackers as having set up the whole thing, doing the hacking and then downloading the content onto the laptop that passed to Mac Isaac and then to Rudy – thus fingering the Russian hackers as possible key players in this imbroglio.
With a quick search I’m not finding other news outlets reporting this. Did Thom hijack Marcy’s good work without attribution?