The Evolving Media Strategy of Lev Parnas
In advance of revisiting my work on the many ways Bill Barr intervened to protect — and participated in — Trump and Rudy Giuliani’s Ukraine capers, I want to first examine Lev Parnas’ recent media efforts, to include his House testimony and his recent book. After years of insinuating Barr had a role in Rudy’s capers, Parnas’ expanded story situates Barr more centrally in events, so I want to point out some gaps in his story and questions the fuller story raises.
Make of them what you will.
The limits of firsthand experience
First, note that Parnas’ book is not all based on firsthand experience. He has a co-author, Hells Angels chronicler Jerry Langton. That, plus sourcing choices about the book, make it difficult, at times, to understand where Parnas’ first-hand witness ends and where research begins.
One notable example is where Parnas and Langton tell an incomplete story about the Russian investigation. The purpose of the explanation is, at least in part, to explain why Parnas adopted Trump’s claims about the Russian investigation but no longer does; it is one of many attempts to disavow past beliefs.
Here’s one example of the uneven treatment that results.
Once the allegations of Russian interference became part of the national consciousness, Trump began to repeatedly and falsely claim that he had never done business in Russia, despite his many tweets to the contrary and the fact that his 2013 Miss Universe Pageant in Russia had been broadcast worldwide by NBC, Telemundo and Channel One, showing Trump sitting right beside Azerbaijani oligarch Aras Agalarov in the front row of the audience. Trump even told CBS News: “I have nothing to do with Russia. Nothing to do. I never met Putin. I have nothing to do with Russia whatsoever.” His lawyer, Michael Cohen, said that Trump called him right after that claim to check up on the status of Trump Tower Moscow.
Days later, the FBI would begin its own investigation into links between Russia and the Trump campaign.
Trump addressed the accusations again the same day at a news conference, saying: “Russia, if you’re listening, I hope you’re able to find the 30,000 emails that are missing.” Not only did that indicate that he was indeed looking for dirt on Hillary, but he was widely accused of “urging a foreign adversary to conduct cyberespionage” on another American, which is a serious crime.
The passage puts Trump’s Russia “are you listening” quip at the beginning of the Russian investigation, albeit with a focus on Michael Cohen’s comments, with no acknowledgment of whether it relies on Cohen’s public comments, court records, or on personal comments from Cohen, with whom Parnas has developed a personal relationship.
But the construction suggests a temporal tie between the presser and the investigation.
There’s no mention of George Papadopoulos here, and therefore of a Coffee Boy who ran his mouth to a stranger. It hides the genesis of the investigation. One effect of that is that Parnas absolves himself of addressing a lot of the bullshit about the origin of the investigation offered by Republicans, bullshit that he was party to. Parnas focuses more on Barr’s bullshit about the Russian investigation than that of his one-time allies.
This lack of clarity on sourcing leaves the provenance of more interesting descriptions about events to which Parnas was not a witness, but of which he might have inside information, uncertain. For example, is this an obscure public reference, or something Parnas learned from his right wing buddies?
Meanwhile, [Jeff] Sessions had been asking staffers for disparaging information against Comey and told them that he expected to see at least one anti-Comey article in major media every day.
Similarly, in critically describing John Solomon’s false claims about Yuriy Lutsenko, Parnas provides a claim that Lutsenko had grown close to Paul Manafort.
Solomon then portrays Lutsenko as an anti-corruption hero, as he had been instructed. Although along with letting Kilimnik sneak away, Lutsenko had been fired, dismissed, suspended, jailed (he was pardoned, officially for health reasons) and gotten chummy with Manafort.
This is a really important detail I had not known: but where does it come from? Parnas does not say. And it matters.
Everyone’s mob past
One thing Parnas does attribute to firsthand knowledge, however, is familiarity with the mob (in both senses of the word). Indeed, he offers himself up as a native of the same Brooklyn (and Queens) world that Michael Cohen, Felix Sater, Rudy Giuliani, and Donald Trump all arose from and unashamedly suggests growing up in such a place means you have mob ties.
Parnas lays all this out in matter-of-fact terms.
Parnas describes the mob ties of his ex-wife.
The girl that I was dating (who I would later marry and have a daughter, Zarina, with) had an uncle named Arkady Seifer. He was a very important man in our community. Seifer had been in prison four times and was connected to the Franchese, the Colombo and the Genovese families — among others. And everybody knew exactly how he made his money — the gas tax.
Seifer and I became quite close very quickly and I found myself referring to the old gangster as my uncle. After I gained his confidence and trust, Seifer let me in on his gas scam.
He describes how he came to call neighborhood boss Butch Montevecchi his uncle.
I translated what he said into English for a neighborhood boss, Ernest “Butch” Montevecchi. At the time, everybody knew Butch. He was strikingly handsome with dark hair and green eyes. He ran Brooklyn’s Sheepshead Bay, and Little Odessa, for the Italians. Later, he’d become so close to me and my family that he served as something of a surrogate father for me, and I started to call him my uncle.
He describes how, during the collapse of the Soviet Union, Parnas used his legally sound US citizenship as a means to ferry stuff into the collapsing Russian empire.
All of the clients were over-the-top excited that I could actually go back to whichever old Soviet republic they had come from. Not only could I import products and perhaps make them rich, but I could also get in touch with friends and relatives they hadn’t heard from in decades.
All of them had gifts for me to give to their loved ones overseas. I limited the haul to two suitcases, not only because I couldn’t carry any more, I didn’t want to arouse too much suspicion. They rapidly filled up with things like jeans, watches and other Western items that would be status symbols over there.
[snip]
Some of the people ultimately became my partners because we saw that it was obvious that our individual skills and contacts could benefit all of us. The people who had entrusted me to visit their contacts came from a variety of places, and an itinerary for me was quickly put together. First, I’d go to Moscow and St. Petersburg (officially Petrograd, but nobody ever called it that). Then it was on to Ukraine, where I’d stop at Odessa (now Odesa) and Kiev (now Kyiv). Finally, I would go to Kazakhstan and Uzbekistan. I was fluent in Russian, so I was confident that I’d be understood in all of those places.
Parnas described how this business venture put him in the service of a number of mobsters and oligarchs, including some he helped enter the US. Buy the book!
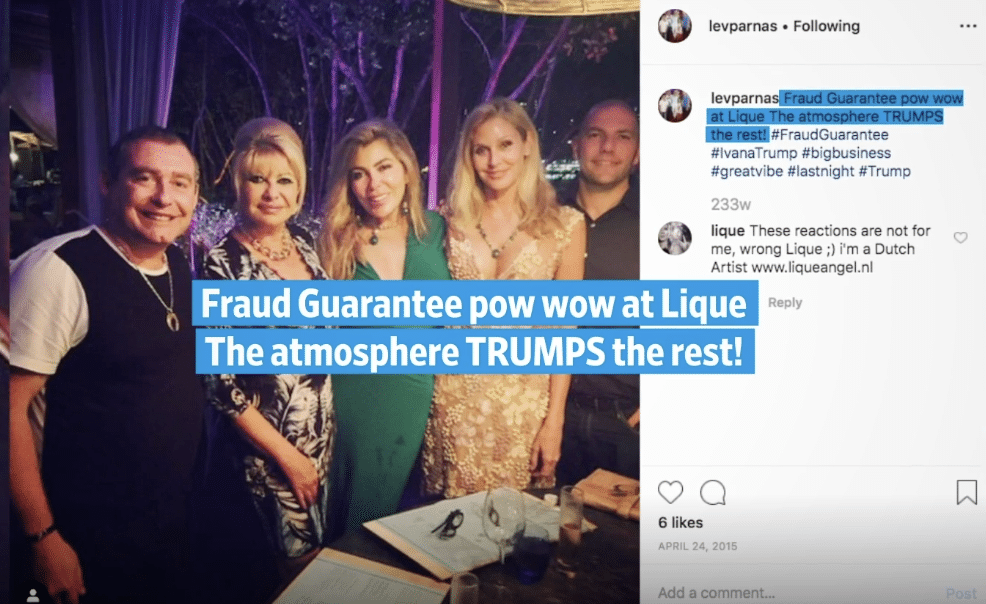
That story continues seamlessly to Parnas’ gradual insinuation in Trump world, in which the owner of Lique had a role.
Later on that week, I was talking with my friend, Alex Podolnyy, on his boat. It was moored behind his restaurant, Lique. It was nighttime and I was smoking a joint on deck. Before long, I was approached by two excited-looking, well-dressed men who were Alex’s friends. They introduced themselves as Ted and Robert and joined me on the boat. They seemed friendly and they knew Alex, so I didn’t mind sharing a joint with them.
As I’ve noted, SDNY’s affidavit for Parnas’ Instagram inexplicably excluded a picture of Parnas and Ivana Trump at Lique from the scope of their review.
And from there, Parnas got access through Brian Ballard. Over a long passage, he tells the story of how he pitched former head of Ukrainian’s Fiscal Service, Roman Nasirov (who awaits trial on corruption charges), to Brian Ballard and then got Nasirov and another foreigner into the Inauguration.
Later that day, I set up a meeting for Ballard and Nasirov. The Ukrainians were eager. When Ukrainian President Petro Poroshenko found out that Nasirov had an opening into Trump’s future administration with Ballard through me, he pressed Nasirov to make it happen. At the time, Ukraine had almost no relationship with the U.S. and even that was in danger of being erased as the Ukrainians were seen as being pro-Hillary. I explained the situation to Ballard. I told him that it wasn’t the president who was in favor of Hillary, just some loud members of his administration. Besides, Ukraine was a sovereign nation and they needed to have some relationship with the U.S. If they hire you, I told Ballard, they could get it done.
[snip]
The first person in the new power structure I sought out was prominent lobbyist Brian Ballard. Right after the win, I set up a meeting with Ballard — and his right-hand-man, Lukis. Although we talked on the phone, I preferred face-to-face meetings and would always see Ballard when he was in Florida.
Ballard was no dummy, he wanted to talk with me about what I knew and where I had contacts. Ballard wanted what I had, so it didn’t take much to make a deal. I would put Ballard in touch with the right people for 20 percent of any deals he made with them.
Although there was some thrill associated with making such high-level deals, I was really in it for the money. I had just had my big fallout with Hudson Holdings and had filed the lawsuit, so I needed to get paid. I knew just where to go.
Nasirov was a major player in the Ukrainian government and eager to talk with Ballard in order to improve Ukraine’s relationship with Washington. Because Ukraine’s support of Obama and Clinton had greatly offended the new crop of Republicans, he was almost desperate to get on Trump’s good side.
So I arranged to meet Nasirov at one of Igor’s Kyiv nightclubs, Buddha Bar. I flew there on December 1, 2016 to spend a week in Ukraine. When I arrived at Buddha Bar, Igor told me that the first floor was closed for a private party, so I’d have to meet Nasirov upstairs.
These descriptions make for great color. And I don’t doubt Parnas’ claims that everyone else he was dealing with was wowed if not working with the mob.
But the descriptions are notable for two other reasons. They address some — but not all — of details publicly released from his investigation.
But then the descriptions stop.
For example, Nasirov is mentioned just five more times in the book after this long introduction. Parnas explains how, just after Trump encouraged his efforts to dig up dirt with Rudy, Nasirov gave him the introduction to Viktor Shokin.
It was in that kind of weather that I landed in Kyiv to find Shokin. It wouldn’t take long for him to turn up. Everybody who was anybody in Kyiv knew me or at least knew of me. If I put the word out that I wanted to see Shokin, it would get to him.
It didn’t take long, I got a call from Nasirov. Of course he knew Shokin, he told me, they were old friends. He’d be more than happy to take me to see him. Shokin had a place just outside Kyiv.
Then there’s acknowledgment that Nasirov ran against Zelenskyy (and Poroshenko) in 2019. And that’s it. He’s the guy who hooked Parnas — and through him, Rudy — up with Shokin, but Parnas never returns to that relationship. That’s important because, as a letter that Parnas’ attorney failed to properly redact revealed, Nasirov was identified as a subject of the investigation into Parnas.
One person who is never mentioned is Alexander Levin who, like Nasirov, shows up in the warrants targeting Parnas, whose name was exposed in that same Joseph Bondy letter after Rudy phones were seized. As Savage Librarian first noted, a person of the same name and roughly the same vintage was charged in 2021 and will soon stand trial for money laundering in association with a series of safe deposit thefts across Europe; this motion in limine provides a glimpse into his background.
And the mobsters? Most of them are replaced in the story by Rudy Giuliani, as if never the twain shall meet.
Parnas never describes when his association with a bunch of sketchy types ended, if they did. That’s especially notable given Parnas’ description of the men he met at Otisville (the same prison at which Michael Cohen did time).
Once I was introduced into the camp’s general population, I was surprised at how many of the guys I already knew. There were friends of friends, old acquaintances and guys I did business with. There were even some people from the old neighborhood — Jews, Italians and Russians. In fact, they had been watching the news and knew I was coming, so they put together a welcome-to-prison gift package to make my life a little easier. They bought me the things that they had found essential behind bars — toothpaste, slippers, a comfortable sweat suit and other useful items they had bought from the commissary.
Suffice it to say Parnas never makes it clear if — and if so when — he broke from the mobbed up old neighborhood or whether they had a role in his work for Donald Trump’s lawyer.
Igor
Which brings us to Parnas’ treatment of his co-defendant Igor Fruman, who is not from Brooklyn, but instead from South Florida, where all this went down.
As Parnas describes it, they were mutual acquaintances through Jewish charities until Igor reached out because of Parnas’ access to Trump.
I knew Igor Fruman through common friends. Born in Belarus, his family emigrated to Detroit when the USSR was shedding even more Jews, Igor was six years older than me and had moved to South Florida, where the Russian, Ukrainian and Belorussian communities were tight. Still, he spent most of his time in Ukraine where he made his money.
I knew about Igor from various Jewish charities we were both involved in and mutual friends, but we weren’t really friends at the time. Igor became interested in me because of the pictures I was posting of myself with Trump on social media and because I was hosting events for Russians for Trump. Igor wanted to get deals done in the petroleum industry and thought I could help.
He owned two popular nightclubs in Kyiv, Mafia Rave and the more upscale Buddha Bar. Both places were very popular with well-heeled men from both the West and East. They mingled at Buddha Bar, got to know each other and made deals, often huge deals.
Parnas claims that Igor’s famous recordings of a few meetings with Trump — including a later one where Parnas offered up, in 2018, that Marie Yovanovitch was disloyal to Trump — were a surprise to him as well.
When I first started going to these events, I was all eyes and ears. All I wanted to do was learn. And to make contacts. My brain was recording everything so that I could sift through it all for what was valuable. I remember it all vividly, but I don’t have to — it was all recorded.
Although we weren’t officially allowed to take pictures or video, Igor surreptitiously caught it all on his phone without anyone realizing it. Even me.
All he had to do was keep the phone out of sight. Because of that, all his videos contain long shots of things like the backs of chairs, ceilings and water glasses. It was far more important to him to record what was said and who was there rather than it was to make it look any good. Back in Ukraine, he’d play the videos to important people in his bars. To the people there, Igor was just a nightclub owner. So, when he said that he was spending time with Donald Trump and Rudy Giuliani, nobody believed him. But with the videos, he could prove that he had access to the very top. It made for good business.
[snip]
So, I was very excited to head to dinner at the Trump International.
Again, Igor managed to catch it all for posterity despite the usual warnings about using cameras or recording devices.
Playing to the audience, I mention that a lot of European countries are back-stabbing us. I knew he’d love that. The crowd falls silent and seems to be very interested in what I have to say. I discreetly mumble something about the U.S. taking over, then tell Trump that the biggest problem I saw for Ukrainian-American relations is the ambassador.
As Parnas describes it, the tie to Nasirov went through Igor’s mobbed up Ukrainian clubs.
I knew someone who might want to become an investor. It was Ukrainian politician Roman Nasirov, who I knew from Igor’s nightclubs. He was then Chairman of the State Fiscal Service of Ukraine (something like Secretary of the Treasury), and was considered the third-most powerful man in the Ukrainian government.
The tie Yuriy Lutsenko, who just happened to show up in New York after they reached out to Shokin for dirt on the Bidens, went through Igor.
And that’s when a gift dropped right into our laps. At the end of January 2019, about a week or so after we spoke with Shokin, I learned from Igor that one of his friends — Gyunduz Mamedov, the Prosecutor General of Crimea — was in New York on personal business with the current top prosecutor in Ukraine, Yuriy Lutsenko, and Glib Zagoriy, a member of the Ukrainian parliament and a pharmaceutical tycoon.
Igor was also friends with Andrii Artemenko, who in turn set them up with Andrii Derkach and Andrii Telizhenko.
In September, I got a call from Andrii Artemenko, who was a friend of Igor’s. He told me that he had some guys with real, hard evidence that would prove all of our theories once and for all. Naturally, I was intrigued. But once he told me that the guys were Derkach and Telizhenko, I told him that we were cool, I’d pass. Not long after, Giuliani text me and asked: “Who’s this Artemenko?” He had, of course, known Artemenko, but had a habit of forgetting names, especially Eastern European ones.
I told him not to deal with Artemenko, he was peddling Russian disinformation. In fact, I gave him other names of guys who were doing the same thing. Of course, I later learned that he was enthusiastically dealing with Artemenko, as well as Derkach and Telizhenko.
Parnas tells two stories about how they got set up with Dmitry Firtash, one in Paris, seemingly arranged by Firtash because of his legal plight.
He probably first called Manafort, but he was already out of the picture. By the time Firtash needed him, he was already serving time. So Firtash had instead retained American lawyers Lanny Davis and Dan Webb.
On a trip to Paris, Rudy and I had a meeting with a Ukrainian we knew from one of the bars my business partner Igor Fruman owned in Kyiv. Igor considered him a close friend, but he hadn’t seen him in a long time. Unbeknownst to us, he was Firtash’s right-hand man.
He introduced us to Firtash. We wanted to talk to Firtash because we knew that he was connected to Mykola Zlochevsky, owner of Burisma Holdings, Ukraine’s biggest oil and gas company. He told us that he had heard things about Hunter Biden, Joe Biden’s son, bad things. Things we might be interested in. He recommended that we talk to Firtash about it. He wasn’t the first person we talked to, but we believed that he had a great deal of pull with the Ukrainian government. We believed that he could get us what we wanted — a Ukrainian investigation of the Bidens.
He describes the second one to have taken place in Madrid (this may be wrong; it may be the same meeting), where they went after Paris (though they met Kholodnytskyi in Paris first).
After our meeting with Kholodnytskyi, we happened to run into another friend of Igor’s at our hotel in Madrid. Everyone knew him as Little Dimitri because he worked for Firtash and we didn’t want to confuse the two. We spoke about why we were there and how important it was for us to get any compromising information on Joe Biden. He told us that the guy we wanted to talk to was Firtash and that he could introduce us. He didn’t need to explain to us who Firtash was.
Parnas was definitely the one trying to network his way through Trump’s world, but at least as Parnas depicts it, the key Ukrainian relationships — first Nasirov, then Shokin, then Lutsenko, then Firtash, and through Artemenko, Derkach and Telizhenko — all went through Igor. Parnas’ explanation of the foreign donations from Andrey Muraviev also blames Igor for intermixing those funds with other funds.
If SDNY learned that (there’s no hint they did, or if they did, that they believed Parnas), you’d think they would have focused more closely on Fruman than on Parnas.
Instead, the investigation treated Parnas as the brainchild of all the crime.
A continued unpersuasive explanation for his Marie Yovanovitch attacks
Against this backdrop, Parnas’ explanations for taking out Yovanovitch are wildly unpersuasive.
In his congressional testimony, Parnas claimed that he was “smeared” by a plot to get rid of Marie Yovanovitch.
When I was arrested, I was initially accused of being involved in a plot to remove Marie Yovanovitch, the U.S. Ambassador to Ukraine whom Trump had fired in April 2019. I was smeared by this false information, and also untrue claims that I was fleeing the country.
As my case continued, the Department of Justice decided they had no interest in Ukraine, sanitizing their marquee claims about Ambassador Yovanovich from my indictment. Instead, I was prosecuted for federal campaign finance and unrelated fraud charges.
In his book, Parnas would call what were primarily FARA charges “espionage” charges and vastly exaggerate the sentencing exposure either FARA or 18 USC 951 would bring.
By my read, this is a misstatement of what happened (one potentially necessitated by Parnas’ claim that SDNY was part of Bill Barr’s attempt to silence him and Igor or at least neutralize the threat the posed to Trump and Barr personally). By my read, the inclusion and then exclusion of the FARA charges had everything to do with the attempts to include Rudy in those charges and Barr’s tampering in that effort. There are probably a number of reasons why SDNY ultimately couldn’t pursue those charges: the corruption of Rudy’s phones, the provable role Trump had in this process, lasting damage Barr did, and Victoria Toensing’s attorney-client privilege with Dmitry Firtash.
But SDNY’s declination in no way debunks the claim that Parnas was involved in a plot to oust Yovanovitch. In his book he explicitly calls his attacks on Yovanovitch “slander.”
Nobody at the embassy knew what the game was. Yovanovitch was too professional to have said disrespectful things about the President, certainly not that he was going to be impeached. But I had been the source of a constant flow of slander against her. It was a big playground game. We’d go visit important people in Ukraine and tell them how bad Yovanovitch was. That would be followed by a visit by someone from the State Department who would tell the same people that we were lying. I would then double back and talk to the same people again, assuring them that Yovanovitch was anti-Trump and could be dangerous for Ukraine. Then the embassy staff would visit those same people again, telling them that we were nobodies who didn’t know what we were talking about. I had more time, so I usually got in the last word.
Parnas’ attempts to deny that there was a plot are important because, in Parnas’ telling, why he came to oppose Yovanovitch is inconsistent. As he describes telling Anderson Cooper in 2020, as he tried to avenge his arrest by cooperating in impeachment, he was reflecting the views of Republicans.
We discussed the Yovanovitch situation. He asked me if I had a problem with her. I told him I didn’t know her personally, but since the Trump people hated her so virulently, I came to the opinion that she had to go.
That’s, of course, nonsense. When Parnas targeted her in 2018, almost no Republicans would have heard of her.
He attributes the animus he expressed in 2018, which likely led Republicans to start examining Yovanovitch more closely, to the opinion of “Ukraine’s wealthy and those who planned to be,” people Parnas implicitly describes to be aiming to cozy up to “power brokers in Russia.”
She was unpopular with Ukraine’s wealthy and those who planned to be.
They were well aware that any serious investigations would easily expose them and their alignment, if not outright fealty, to the power brokers in Russia, not their own country (including more than a few elected politicians). With my many connections in various fields, there was a consensus about Yovanovitch — she had to go. And, when they found out I was American, they couldn’t wait to tell me about how bad Yovanovitch was for Ukraine, without giving too many specifics, of course.
She was unpopular with Ukraine’s wealthy and those who planned to be. They were well aware that any serious investigations would easily expose them and their alignment, if not outright fealty, to the power brokers in Russia, not their own country (including more than a few elected politicians). With my many connections in various fields, there was a consensus about Yovanovitch — she had to go. And, when they found out I was American, they couldn’t wait to tell me about how bad Yovanovitch was for Ukraine, without giving too many specifics, of course.
The rest of the book describes a progression: Shokin blamed Yovanovitch for denying him a US visa whence he could plot against the Bidens, which led Rudy to blame Yovanovitch, which led Trump and his failson and John Solomon and everyone else to pile on.
But the actual people behind that original animus are never named, possibly because tying that animus to the mobsters and oligarchs with whom Parnas networked would substantiate a plot, just a different plot, than the one SDNY laid out.
Relatedly, Parnas suggests that Pete Sessions was already working on replacing Yovanovitch when Parnas repeated this story to him and donated that money that, Parnas claims, Igor had mixed in with their other funds. Parnas was just the mule for a letter to Trump.
In short, the campaign against Yovanovitch is presented as always-already in progress, even though there’s no evidence that it started in the US before that Parnas comment in 2018.
A different approach to Dmitry Firtash’s equities
This post is meant to set up one on Barr. We get there via Dmitry Firtash.
Parnas manages to focus more closely on Bill Barr’s role in all of this by expanding, from earlier instances, on how he describes the Firtash relationship.
When he wrote James Comer last year, he probed for a subpoena that would provide a way to breach any privilege claim.
Thereafter, as I became an interpreter between Firtash’s new legal team and Firtash, most of the conversations in which I participated were potentially privileged; however, I believe this information may be made available to the House Oversight Committee through a Congressional subpoena.
He didn’t get that subpoena.
When invited to testify without subpoena, Parnas made no mention of Firtash in his prepared congressional testimony. But in the hearing, Ro Khanna cued Parnas to describe his second-hand understanding that Barr was willing to trade campaign help for lenience from DOJ.
Ro Khanna: Did Bill Barr know that you were involved in getting this dirt?
Parnas: Absolutely. Bill, Bill Barr was informed of our investigation from the day he took office.
Khanna: Did you ever have a conversation with Bill Barr being lenient towards Dmitry, in Bill Barr’s role as Attorney General?
Parnas: I personally did not but I was witness to Victoria Toensing and Joe DiGenova, having a conversation with Bill Barr about Dmitry Firtash.
Khanna: What did they say to Bill Barr?
Parnas: Basically, they were telling him that the charges were false, and that he needs to drop the charges and, basically, end the case.
Khanna: And why did they tell him to drop the charges on this Russian [sic] oligarch?
Parnas: Because Dmitry Firtash was going to help us getting dirt on the Bidens, or whatever else the Trump campaign needed.
Khanna: So my understanding is you have the Trump campaign telling you to talk to a Russian [sic] oligarch to get dirt, on the President of the United States for political reasons, and then someone from the Trump campaign is talking to the Attorney General to drop the charges because this foreign national is helping get dirt on a political candidate?
Parnas: Absolutely.
Khanna: Did Bill Barr indicate any willingness to drop the charges?
Parnas: After the meeting that Victoria Toensing and Joe DiGenova had with DOJ, they came back and informed me that “we’re going to Vienna” because, to tell Dmitry Firtash everything is going to be okay.
While Parnas’ focus on Firtash at the hearing had the appearance of accident, Firtash is a central focus of Parnas’ book. The first pages of Parnas’ book describe meeting — alone, apparently — with Firtash, in what would be the penultimate visit to finalize a quid pro quo.
As my car approached its destination, I watched as a black — no doubt armored — Mercedes SUV with opaque black windows blocked the one-way street behind me. Closer to the massive iron gates in front of the property, another big black SUV blocked the road ahead.
It didn’t unsettle me at all, I’d been through the same routine on the previous trips I had made to this house and others like it. I also knew that the guys protecting Dmytro Firtash seriously outgunned anyone who might want to hurt him. And he was on our side.
As we turned down the only open lane toward the main building, we drove past a legion of security guards in black with dark sunglasses and AK-47s. Nothing out of the ordinary.
The chapter then maps out how, at a hush hush meeting at John Dowd’s in Chatham, MA, as news of the Perfect Phone Call started to break, Trump’s team promised to protect Parnas.
A black SUV with security took me to Chatham, Massachusetts, on the “elbow” of Cape Cod. Firtash paid for all of it. There was a conference call set up by Trump’s legal team at Dowd’s beach house. Dowd told me that the reason we met on Cape Cod was to keep the media away from me.
[snip]
In Dowd’s home office, he set up a conference call with Giuliani, Jay Sekulow (another of Trump’s attorneys), Toensing and diGenova. There might have been other lawyers, but I didn’t hear any. Dowd laid out the plan, and it was simple: stonewall. He instructed us all not to say anything to Congress and not to worry about subpoenas because we’d only get letters requesting our appearance, which we could ignore. Trump, he said, would tell them to go fuck themselves and everybody else was to follow suit. [my emphasis]
So, even as Congress was investigating, Parnas continued to pursue the quid pro quo with Firtash. Parnas went from this meeting back to DC to tie up loose ends for the big Fox News reveal.
On October 6 (two days before the beginning of Yom Kippur), I flew to Washington to discuss the trip to Vienna with Giuliani and Toensing.
Giuliani told me that he wanted to meet Shokin and that it might also be a great idea to bring Fox News personality and ardent Trump supporter Sean Hannity to interview him.
That was a key part of the plan. Team Trump had not been very successful at getting our message into what Trump called “fake news” and the “lame stream media,” so we depended on Fox News and like-minded outlets for any publicity. Not only would millions of Americans see the interview, but it being on Fox News would lend us an air of credibility among many people.
Just before we left for Vienna, I received a phone call from Firtash warning me that Shokin had become anxious about the interview, and was threatening to back out.
I called Shokin. He answered, but he was tense, even panicky. He told me that he was sure “they” were going to kill him. He was absolutely convinced that he would be poisoned, just like Viktor Yushchenko, who had angered Putin while running for the Ukrainian presidency. There was no way, he said, that he would get on a plane no matter what.
Firtash told me not to worry. He’d see to it personally that Shokin was flown to Vienna safely and would be present for a live interview with Fox’s Hannity.
Part of the deal was that we’d also get Shokin’s sealed testimony to the Viennese court and the hard drive from the laptop Hunter Biden used when he was working in Ukraine. It was supposed to have come from Alexander Gorbunenko, who was CFO of Burisma when Hunter worked there. If there was any evidence of him doing anything illegal in Ukraine, we were sure we’d find it there.
This is the Lev Parnas post, not the Bill Barr post. We can discuss the potential significance of this — the inconsistency between John Paul Mac Isaac’s timeline and the FBI’s, Will Levi writing Barr that a laptop was on its way to him immediately after IRS got a warrant for the laptop ascribed to Hunter, the reported closure of the Mykola Zlochevsky investigation and the use of it to elicit Alexander Smirnov’s false bribery allegation, the limitations imposed on SDNY’s ongoing investigation into Rudy’s influence campaign, the Brady side channel, including Brady’s inquiries into investigations in Chicago, where the Firtash investigation was — in the Bill Barr post.
I’ve got cautions about Parnas’ credibility, and SDNY repeatedly said he was lying about all this (and Parnas sustains some of what SDNY surely treated as lies — for example about Yovanovitch — in this book). But Barr’s a liar too, he affirmatively prevented SDNY from learning some of this, and his own actions are consistent with what Parnas claims.
It’s about motive.
Parnas’ motive has always been transparent. For all his claims to be cured of membership in the Trump cult, that would never have happened if Rudy and Trump and John Dowd hadn’t reneged on their promise to protect him.
I was led into a room where Dowd was sitting behind a table and Downing was standing beside him. Immediately, I started asking questions. I wanted to know why I was still behind bars while Igor was free. I wanted to know what Trump was going to do for me.
Suddenly, Dowd slammed his fist down on the table and shouted at me: “Who do you think you fucking are? Trump is President and he will do whatever he damn well wants to do!”
But in a book that engages in a lot of casual mob-talk, I want to know about the evolving treatment of Firtash.
Firtash had a real attorney-client relationship with Victoria Toensing, however corrupt (Lanny Davis is no better). And for years, Parnas respected that (in part, presumably, because it kept SDNY away from this material, though the statute of limitations on these activities have not quite expired).
I’m all in favor of hearing this story. But what does Firtash feel about it?