What Roger Stone’s Latest Lies Tell Us about Mueller’s Investigation into Him
As I disclosed last month, I provided information to the FBI on issues related to the Mueller investigation, so I’m going to include disclosure statements on Mueller investigation posts from here on out. I will include the disclosure whether or not the stuff I shared with the FBI pertains to the subject of the post.
After a puff piece in the NYT over the weekend, Roger Stone took to the Daily Caller to attack Mueller’s case against him. As bad as the Daily Caller is, it actually ends up being far more informative than the NYT because Stone is so bad at telling lies they’re informative for what they mirror.
So assuming, for the moment, that Stone’s piece reflects some kind of half-accurate reflection of what witnesses have said they were questioned about him, here’s what we learn.
Mueller is examining conduct that goes back 10 years
Obviously, statutes of limitation have probably tolled on any crimes Stone committed more than five years ago, but this suggests witnesses are being asked about conduct that goes back further, ten years.
Mueller is running a criminally abusive, constitutionally -unaccountable, professionally and politically incestuous conspiracy of ethically conflicted cronies colluding to violate my Fourth, Fifth and Sixth Amendment rights and those of almost everyone who had any sort of political or personal association with me in the last 10 years.
Given the involvement of Peter Jensen and Kristin Davis in Stone’s recent rat-fucking, perhaps as an explanation of more recent rat-fucking we’ll finally get an accounting of Stone’s role in taking out Eliot Spitzer ten years ago. (h/t Andrew Prokop for Jensen tie to Spitzer op)
Mueller is considering charging Stone with ConFraudUs
I assume this reference to ConFraudUs comes from a friendly witness passing on what a subpoena described were the crimes being investigated.
Mueller and his hit-men seek to frame some ludicrous charge of “defrauding the United States.”
This is, of course, based on a false and unproven assumption that Assange is a Russian agent and Wikileaks is a Russian front — neither of which has been proven in a court of law. Interestingly Assange himself has said, “Roger Stone has never said or tweeted anything we at Wikileaks had not already said publicly.”
As described, it looks like how I envisioned Stone might be charged with ConFraudUs back in June.
As Mueller’s team has itself pointed out, for heavily regulated areas like elections, ConFraudUs indictments don’t need to prove intent for the underlying crimes. They just need to prove,
(1) two or more persons formed an agreement to defraud the United States;
(2) [each] defendant knowingly participated in the conspiracy with the intent to defraud the United States; and
(3) at least one overt act was committed in furtherance of the common scheme.
Let’s see how evidence Mueller has recently shown might apply in the case of Roger Stone, Trump’s lifelong political advisor.
[snip]
Stone repeatedly entertained offers from foreigners illegally offering dirt that would benefit the Trump campaign — Greenberg, Guccifer 2.0, possibly Peter Smith’s Dark Web hackers. He may even have exhibited a belief that Australian Julian Assange had and could release the latter dirt, possibly with the knowledge they came from Russians.
So we’ve got Stone meeting with other people, repeatedly agreeing to bypass US election law to obtain a benefit for Trump, evidence (notwithstanding Stone’s post-hoc attempts to deny a Russian connection with Guccifer 2.0 and Wikileaks) that Stone had the intent of obtaining that benefit, and tons of overt acts committed in furtherance of the scheme.
Stone appears to address just one conspiracy with a foreigner — Julian Assange — to obtain something of value, by insisting (though less strongly than he has in the past!) that Assange is not a Russian asset. Except, foreign is foreign, whether Australian or Russian, so making a weak case that Assange is not Russian won’t get you off on ConFraudUs.
Moreover, now that I’ve reviewed some dodginess about Stone’s PACs, I suspect there may be two levels of ConFraudUs, one pertaining to depriving the US government from excluding foreign influence on the election, and the other pertaining to depriving the US government of the ability to track how political activities are being funded.
That is, Mueller’s reported focus on Stone’s finances may well pertain to a second ConFraudUs prong, one based on campaign finance violations.
Stone thinks Mueller wants him to flip, rather than to punish him for the case in chief
In spite of the abundant evidence that Stone is a key target of this investigation, Stone appears to believe that Mueller only wants to charge him to get him to flip on Trump.
Mueller’s hit team is poking into every aspect of my personal, private, family, social, business and political life — presumably to conjure up some bogus charge or charges to use to pressure me to plead guilty to their Wikileaks fantasy and testify against Donald Trump who I have known intimately for almost 40 years.
Side note: I appreciate the way Stone — an unabashed swinger — worked that word “intimately” into his description of his relationship with Trump.
Which is one of the reasons I’m so interested in how he describes hiring a new lawyer, a nationally known one who used to work for Trump.
I have been ably served by two fine lawyers Grant Smith and Rob Buschel who won dismissal of a harassment lawsuit based on the same Wikileaks/Russian conspiracy theory by an Obama directed legal foundation in D.C. last month. No evidence to support this false narrative was produced in court other than a slew of fake news clippings from lefty media sites.
I have recently reached agreement to retain a highly respected and nationally known attorney who has represented Donald Trump to join my legal team and lead my defense.
Possibly this is just a hint that some operative like Victoria Toensing or Joseph DiGenova is going to take on Stone’s propaganda case. Possibly it reflects a recognition from Trump that Stone now presents as big a risk to him as Manafort does. Whichever it is, I look forward to learning how serious a lawyer Stone has and whether — Stone claims reports that he has $20 million are false, but if he has been engaging in epic campaign finance violations, who knows? — Trump is paying for his defense going forward.
Stone doesn’t understand how stored communications work
As I pointed out the last time Stone claimed he was targeted by a FISA order, what likely happened instead is Mueller obtained the contents of his phone along with four or nine others in a probable cause warrant on March 9. But that doesn’t stop Stone from claiming he was targeted under FISA again, explaining that his emails, text messages, and (this is less credible) phone calls have been seized going back to 2016.
Even more chilling is the fact that I have learned that — in this effort to destroy me — the government began reading my e-mails and text messages and monitoring my phone calls as early as 2016.
I believe that I, like Carter Page and Paul Manafort, was subject to an illegal FISA warrant in 2016, as the New York Times reported on January 20, 2017. The New York Times published this claim in a page-one story on the same day as President Trump’s inauguration ceremony.
A whistleblower has told my lawyers where my name and the fact that application had been made for a FISA warrant on me was redacted from the stunning Carter Page FISA warrant application released by the FBI last week with 300 of 400 pages blacked out.
What Stone’s dumbass “whistleblower” was pointing to instead was a passage describing the other people being investigated in October 2016, when Page was first targeted. But being investigated is not the same as being targeted under FISA, and what Stone is really trying to obscure here is that Mueller (probably) already showed a judge, back in March, he had probable cause that Rog committed some crimes back in 2016.
Another witness Stone would like to discredit by calling an informant
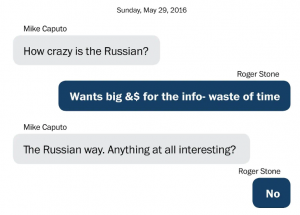
Back in June, Stone tried to spin the fact that he willingly accepted a meeting with yet another Russian offering dirt on Hillary by noting (correctly, it appears) that the Russian had served as a source for the FBI on Russian organized crime before — just like Felix Sater, whom the Trump folks are all still peachy with. In spite of the fact that it was so obviously bunk the last time, he’s trying again, hinting at a second informant working against him.
We also now know that at least one FBI informant in the United States on an informant’s visa approached me in May 2016 in an effort to entrap me and compromise Donald Trump. I declined his proposal to “buy dirt on Hillary.” There is now substantial evidence that a second FBI informant may have infiltrated my political operations in 2016. Stand by.
Who knows whether this is another person — like the Russian dealing dirt on Hillary, “Henry Greenberg,” is just someone who has worked his way out of legal trouble by serving as an informant — or whether there’s some other reason Stone is calling him or her an informant. Most likely, Stone is trying to suggest a perfectly ordinary witness cooperating with the government against him is an informant, to inflame his people. Possibly, this is prepping a claim that Randy Credico set up Roger.
Jeannie Rhee is leading the questioning of Stone witnesses
In tandem with Trump’s attacks on Mueller prosecutors with Hillary ties, Stone states that Jeannie Rhee led the questioning of his witnesses, and claims it’s a conflict.
Incredibly, leading the questioning of witnesses before the Grand Jury about me is Jeannie Rhee, who in private practice represented the Clinton foundation in the Hillary e-mail scandal that is front and center in the special prosecutor’s investigation of me! Can you say conflict of interest?
Of course, he gets the attack wrong: Rhee represented the Foundation, not Hillary’s email defense, and she did so against a nutbag Republican challenge, not with DOJ.
But in telling us that Rhee is leading this inquiry, Stone is (helpfully) telling us that a person who has led the Russian side of the inquiry is leading the inquiry into … oh my! Roger Stone!
Even with all his prevarications, it turns out, a Stone column might be more informative than a NYT puff piece!


 CC BY 2.0
CC BY 2.0