ICREACH and FBI’s PRTT Program
I’ll have a more substantive post about what we learn about NSA’s broader dragnet from the Intercept’s ICREACH story.
But for the moment I want to reiterate a point I made the other day. ICREACH is important not just because it makes NSA data available to CIA and FBI. But also because it makes CIA and FBI data available for the metadata analysis the NSA conducts.
The documents describe that to include things like clandestine intelligence and flight information.
But there’s one other program that ought to be of particular concern with regards to NSA’s programs. As I laid out here, FBI had a Pen Register/Trap and Trace “program” that shared information with the NSA at least until February 2012, several months after NSA had ended its PRTT Internet dragnet program.
The secrecy behind the FBI’s PRTT orders on behalf of NSA
Finally, there’s a series of entries on the classification guide for FISA programs leaked by Edward Snowden.
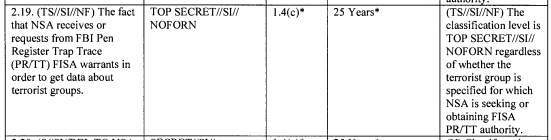
These entries show that FBI obtained counterterrorism information using PRTTs for NSA — which was considered Secret.
But that the FBI PR/TT program – which seems different than these individual orders — was considered TS/SI/NOFORN.
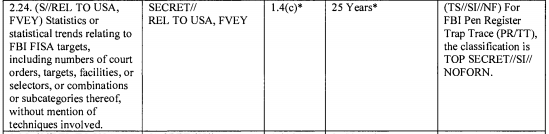
If you compare these entries with the rest of the classification guide, you see that this information — the fact that NSA gets PRTT information from FBI (in addition to information from Pen Registers, which seems to be treated differently at the Secret level) – is treated with the same degree of secrecy as the actual targeting information or raw collected data on all other programs.
This is considered one of the most sensitive secrets in the whole FISA package.
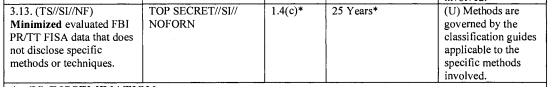
Even minimized PRTT data is considered TS/SCI.
Now, it is true that this establishes an exact parallel with the BR FISA program (which the classification guide makes clear NSA obtained directly). So it may be attributable to the fact that the existence of the programs themselves was considered a highly sensitive secret.
So maybe that’s it. Maybe this just reflects paranoia about the way NSA was secretly relying on the PATRIOT Act to conduct massive dragnet programs.
Except there’s the date.
This classification guide was updated on February 7, 2012 — over a month after NSA shut down the PRTT program. Also, over a month after — according to Theresa Shea — the NSA destroyed all the data it had obtained under PRTT. (Note, her language seems to make clear that this was the NSA’s program, not the FBI’s.)
That is, over a month after the NSA ended its PRTT program and destroyed the data from it (at least according to sworn declarations before a court), the NSA’s classification guide referred to an FBI PRTT program that it considered one of its most sensitive secrets. And seemed to consider active.
I have no idea what this program entailed — and no one else has even picked up on this detail. It’s possible NSA’s Internet dragnet just moved under the FBI’s control. It’s possible (this is my current operative wildarseguess) that FBI’s PRTT program collects location data; the Bureau uses PRTT orders to get individualized location data, after all.
Whatever it is, though, the existence of ICREACH would make that data available to NSA in a form it could use to include it in contact chaining of metadata (which may be why it figures so prominently in NSA’s classification guide). And note: FBI’s minimization procedures are far more lenient than NSA’s, so whatever this data is, NSA may be able to do more with it given that FBI collected it.
And as with a number of other things, even the Pat Leahy version of USA Freedom would weaken protections for PRTT data.