20 Questions: Mike Rogers’ Vaunted Section 215 Briefings
Comment — Russ Feingold said that Section 215 authorities have been abused. How does the FBI respond to that accusation?
A — To the FBI’s knowledge, those authorities have not been abused.
That exchange is, according to DOJ’s Congressional Affairs Office, the level of detail offered up at a May 13, 2011 briefing of the House Republican Caucus regarding the PATRIOT Act provisions the House would vote to reauthorize less than two weeks later.
The questioner — who is not identified — may have been talking about comments Russ Feingold made way back on October 1, 2009, as part of the previous reauthorization of the PATRIOT Act (remember, by this point, Feingold was no longer in the Senate). Here are the things Feingold said about Section 215 in that Senate Judiciary Committee markup.
I remain concerned that critical information about the implementation of the Patriot Act remains classified. Information that I believe, would have a significant impact on the debate….. There is also information about the use of Section 215 orders that I believe Congress and the American People deserve to know. It is unfortunate that we cannot discuss this information today.
…
Mr Chairman, I am also a member of the intelligence Committee. I recall during the debate in 2005 that proponents of Section 215 argued that these authorities had never been misused. They cannot make that statement now. They have been misused. I cannot elaborate here. But I recommend that my colleagues seek more information in a classified setting.
…I want to specifically disagree with Senator Kyle’s [sic] statement that just the fact that there haven’t been abuses of the other provisions which are Sunsetted. That is not my view of Section 215. I believe section 215 has been misused as well.
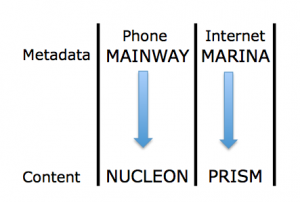
Given the context, it is unclear whether Feingold referred to use of Section 215 for things they shouldn’t have, use of it to authorize bulk collection generally, or in the compliance issues identified in 2009 on which the Administration had recently briefed the Intelligence Committee. But his suggestion that the Senate Judiciary Committee was getting less detailed briefings than the Senate Intelligence Committee at that point is consistent with DOJ’s 2009 notice to Congress on the dragnet, which said, “The [compliance] incidents, and the Court’s responses, were also reported to the Intelligence Committees in great detail,” with no mention of similarly detailed briefings to SJC (the 2011 letter indicates that by that point SJC was getting detailed briefings as well). This, in turn, suggests he was referring to dragnet-related violations.
Regardless of what Feingold meant, though, he tied misuse very closely to the secret use of Section 215 to conduct dragnet collection of all Americans’ phone records. Feingold’s other public statements about Section 215 focus even more closely on the secret dragnet application of it.
In other words, this appears to have been a question attempting to get at the secret application of the PATRIOT Act that Feingold, along with Ron Wyden and people like Jerry Nadler, had been warning about. This appears to have been an attempt to learn about a topic that — in 2009, at least — DOJ had “agree[d] that it is important that all Members of Congress have access to information about this program” (DOJ didn’t include such blather in its 2011 notice).
Exactly 100 days before the briefing at which this question was asked, DOJ had sent House Intelligence Chair Mike Rogers (who appears to have convened this briefing) a letter noting, “In 2009, a number of technical compliance problems and human implementation errors in these two bulk collection programs were discovered as a result of Department of Justice (DOJ) reviews and internal NSA oversight.”
Yet in response to a query clearly designed to elicit both the existence of the dragnet program and details on problems associated with it, FBI Director Robert Mueller and then-General Counsel Valerie Caproni (and/or whatever staffers were with them) said, to the Bureau’s knowledge, there had been no abuses. Perhaps, then, as now, they’re relying on the claim that none of these compliance issues were willful — the letter said they weren’t intentional or bad-faith — to avoid telling members of Congress about problems with the program.
Remember, this is one of the (and may have been the only) briefings that Mike Rogers now claims provided adequate substitute for letting House members know about the letter describing the dragnet and the compliance problems associated with it. Rogers’ House Intelligence spokesperson, Susan Phalen, has claimed those briefings “not only covered all of the material in the letter but also provided much more detail.” (As far as I’ve been able to tell from the FOIA production to the ACLU, there was no similar briefing for the Democratic caucus, though FOIA production tends to be incomplete; one Democratic Congressman, Hansen Clarke, attended the Republican briefing.)
And DOJ’s own records of the briefing make it clear that when someone tried, however inartfully, to learn about the program, Mueller and Caproni obfuscated about the compliance issues and possibly the existence of the dragnet itself.
This is a concrete example of what both Justin Amash and Ron Wyden have described as a game of 20 questions briefers play in these briefings. The questioner raised one of the few public hints about the dragnet program to ask the FBI about it, and the FBI responded in a manner very similar to the way James Clapper did in March, when he lied to the SSCI.
Now, we don’t know what remains behind the redactions in the briefing, but there is one other piece of evidence that this briefing, at least, didn’t even touch on the dragnet. If you look at all 5 closed briefings turned over in production to ACLU, two — a February 28, 2011 briefing for SJC and a March 17, 2011 briefing for the House Intelligence Committee — were deemed classified “per OGA letter dated 4/26/2012.” The acronym “Other Government Agency” is usually used to refer to CIA, but in this context, where we now know NSA played a central role but revealing that role last year would have disclosed significant new details about the secret application of Section 215, it may well refer to NSA. Those briefings also redacted the identities of some briefers which, again, may be classified to hide the NSA’s role in this program.
If all this speculation is correct, then it means there was no mention of the NSA in the briefing for the Republican caucus. If there was no mention of NSA, then they really couldn’t have explained the program (both the 2009 and 2011 notices make extensive reference to the NSA).
In any case, what remains unredacted is quite clear. Someone at that briefing — the briefing that Mike Rogers’ staffer claims offered more information than had been provided in the DOJ letter — tried to learn about problems with the secret program. And they got stonewalled in response.
Was the person who asked this question and got an incomplete answer one of the 65 people who would go on to reauthorize the PATRIOT Act having had no way of learning about the program and its compliance problems?