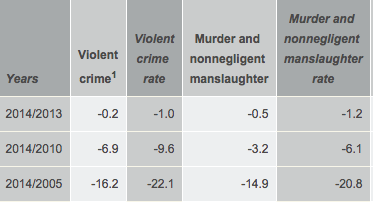
For at least the second time, Jim Comey has presented himself as a Ferguson Effect believer, someone who accepts data that has been cherry picked to suggest a related rise in violent crime in cities across the country (I believe that in Ferguson itself, violent crime dropped last month, but whatever).
I have spoken of 2014 in this speech because something has changed in 2015. Far more people are being killed in America’s cities this year than in many years. And let’s be clear: far more people of color are being killed in America’s cities this year.
And it’s not the cops doing the killing.
We are right to focus on violent encounters between law enforcement and civilians. Those incidents can teach all of us to be better.
But something much bigger is happening.
Most of America’s 50 largest cities have seen an increase in homicides and shootings this year, and many of them have seen a huge increase. These are cities with little in common except being American cities—places like Chicago, Tampa, Minneapolis, Sacramento, Orlando, Cleveland, and Dallas.
In Washington, D.C., we’ve seen an increase in homicides of more than 20 percent in neighborhoods across the city. Baltimore, a city of 600,000 souls, is averaging more than one homicide a day—a rate higher than that of New York City, which has 13 times the people. Milwaukee’s murder rate has nearly doubled over the past year.
Yesterday, Comey flew to Chicago and repeated something its embattled Mayor recently floated (even while Bill Bratton, who is a lot more experienced at policing than Rahm Emanuel, has publicly disputed it): that cops are not doing their job because people have started taking videos of police interactions.
I’ve also heard another explanation, in conversations all over the country. Nobody says it on the record, nobody says it in public, but police and elected officials are quietly saying it to themselves. And they’re saying it to me, and I’m going to say it to you. And it is the one explanation that does explain the calendar and the map and that makes the most sense to me.
Maybe something in policing has changed.
In today’s YouTube world, are officers reluctant to get out of their cars and do the work that controls violent crime? Are officers answering 911 calls but avoiding the informal contact that keeps bad guys from standing around, especially with guns?
I spoke to officers privately in one big city precinct who described being surrounded by young people with mobile phone cameras held high, taunting them the moment they get out of their cars. They told me, “We feel like we’re under siege and we don’t feel much like getting out of our cars.”
I’ve been told about a senior police leader who urged his force to remember that their political leadership has no tolerance for a viral video.
So the suggestion, the question that has been asked of me, is whether these kinds of things are changing police behavior all over the country.
And the answer is, I don’t know. I don’t know whether this explains it entirely, but I do have a strong sense that some part of the explanation is a chill wind blowing through American law enforcement over the last year. And that wind is surely changing behavior.
Let’s, for the moment, assume Comey’s anecdote-driven impression, both of the Ferguson Effect and of the role of cameras, is correct (to his credit, in this speech he called for more data; he would do well to heed his own call on that front). Let’s assume that all these cops (and mayors, given that Comey decided to make this claim in Rahm’s own city) are correct, and cops have stopped doing the job we’re all paying them to do because they’re under rather imperfect but nevertheless increased surveillance.
We’ll take you at your word, Director Comey.
If Comey’s right, what he’s describing is the chilling effect of surveillance, the way in which people change their behavior because they know they will be seen by a camera. That Comey is making such a claim is all the more striking given that the surveillance cops are undergoing is targeted surveillance, not the kind of dragnet surveillance (such as the use of planes to surveil the Baltimore and Ferguson protests, which he acknowledged this week) his agency and the NSA subject Americans to.
Sorry, sir! Judge after judge has ruled such claims to be speculative and therefore invalid in a court of law, most recently when T.S. Ellis threw out the ACLU’s latest challenge to the dragnet yesterday!
I actually do think there’s something to the chilling effect of surveillance (though, again, what’s happening to cops is targeted, not dragnet). But if Comey has a problem with that, he can’t have it both ways, he needs to consider the way in which the surveillance of young Muslim and African-American men leads them to do things they might not otherwise do, the way in which it makes targets of surveillance feel under siege, he needs to consider how the surveillance his Agents undertake actually makes it less likely people will engage in the things they’re supposed to do, like enjoy free speech, a robust criminal defense unrestricted by spying on lawyers, like enjoy privacy.
Comey adheres to a lot of theories, including the Ferguson Effect.
But as of yesterday, he is also on the record as claiming that surveillance has a chilling effect. Maybe he should consider the implications of what he is saying for the surveillance his own agency has us under? If the targeted surveillance of cops is a problem, isn’t the far less targeted surveillance he authorizes a bigger problem?