The 2009 Draft NSA IG Report Makes No Mention of One Illegal Practice
The 2009 Draft NSA IG Report released by the Guardian last week — and related reporting from Barton Gellman — seem to clarify and confirm what I’ve long maintained (12/19/05; 7/29/07; 7/30/07): that one part of the illegal wiretap program that Jack Goldsmith and Jim Comey found “illegal” in 2004 was data-mining of Americans.
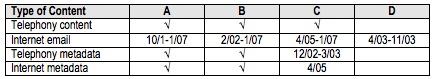
Eight days later on 19 March 2004, the President rescinded the authority to collect bulk Internet metadata and gave NSA one week to stop collection and block access to previously collected bulk Internet metadata. NSA did so on 26 March 2004. To close the resulting collection gap, DoJ and NSA immediately began efforts to recreate this authority in what became the PR/TT order.
Mind you, this bulk collection resumed after Colleen Kollar-Kotelly signed an order permitting NSA to collect the same data under a Pen Register/Trap & Trace order on July 14, 2004.
The FISC signed the first PR/TT order on 14 July 2004. ALthough NSA lost access to the bulk metadata from 26 March 2004 until the order was signed, the order essentially gave NSA the same authority to collect bulk Internet metadata that it had under the PSP, except that it specified the datalinks from which NSA could collect, and it limited the number of people that could access the data.
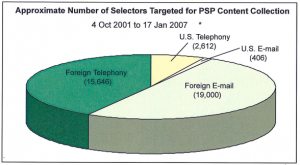
Indeed, we know the program was expanded again in 2007, to get 2 degrees of separation deep into US person Internet data. The Obama Administration claims it ended this in 2011, though there are also indications it simply got moved under a new shell.
Mystery solved, Scoob!
Not so fast.
It appears the bulk Internet metadata collection and mining is just one of two practices that Goldsmith and Comey forced Bush to at least temporarily halt in 2004. But the second one is not mentioned at all in the NSA IG Report.
I first noted that Bush made two modifications to the program in this post, where I noted that 6 pages (11-17) of Jack Goldsmith’s May 6, 2004 OLC opinion on the program described plural modifications made in March and one other month in 2004 (I correctly surmised that they had actually shifted parts of the program under parts of the PATRIOT Act, and that they had narrowed the scope somewhat, though over-optimistically didn’t realize that still included warrantless collection of known domestic content).
But there’s actually a far better authority than Goldsmith’s heavily redacted opinion that confirms Bush made two modifications to the program in this period.
Dick Cheney.
When his office disclosed to Patrick Leahy in 2007 what documents it had regarding authorizations for the illegal wiretap program, it listed two modifications to the program: the one on March 19 described in detail in the NSA IG Report, plus one on April 2.
[Cheney Counsel Shannen] Coffin’s letter indicates that Bush signed memos amending the program on March 19 and April 2 of that year.
But there’s no hint of a second modification in the NSA IG Report.
That could mean several things. It could mean the April 2 modification didn’t involve the NSA at all (and so might appear in a one of the other Agency IG Reports at the time — say, DNI — or might have been completed by an Agency, like some other part of DOD, that didn’t complete an IG Report). It could mean that part of the program was eliminated entirely on April 2, 2004. Or it could mean that in an effort to downplay illegality of the program, the IG simply didn’t want to talk about the worst prior practice eliminated in the wake of the hospital confrontation.
Goldsmith’s opinion does seem to indicate, however, that the modification pertained to an issue similar to the bulk metadata collection. He introduces that section, describing both modifications, by saying “it is necessary to understand some background concerning how the NSA accomplishes the collection activity authorized under” the program.
That may still pertain to the kind of data mining they were doing with the Internet metadata. After all, the fix of moving Internet metadata collection under the PR/TT order only eliminated the legal problem that the telecoms were basically permitting the government to steal Microsoft and Yahoo Internet content from their equipment. There still may have been a legal problem with the kind of data mining they were doing (perhaps arising out of Congress’ efforts in that year’s NDAA to prohibit funding for Total Information Awareness).
Whatever it is, one thing is clear. Even with the release of the unredacted Draft NSA IG Report, we still aren’t seeing all the details on what made the program so legally problematic.
Maybe it’s something the Senate Judiciary Committee might ask Jim Comey during his FBI Director confirmation hearing?

![[NSA presentation, PRISM collection dates, via Washington Post]](http://www.emptywheel.net/wp-content/uploads/2013/06/WaPo_Prism-Slide5_06JUN2013_300pxw.jpg)