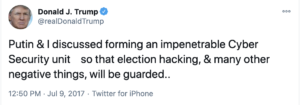
In a Mike Flynn sentencing memo submitted in January delayed twice to secure all necessary approvals, Bill Barr’s DOJ asserted that Flynn’s lies were material because they hid, in part, who directed that he call up the Russian Ambassador and undermine sanctions.
It was material to the FBI’s counterintelligence investigation to know the full extent of the defendant’s communications with the Russian Ambassador, and why he lied to the FBI about those communications.
[snip]
The defendant’s false statements to the FBI were significant. When it interviewed the defendant, the FBI did not know the totality of what had occurred between the defendant and the Russians. Any effort to undermine the recently imposed sanctions, which were enacted to punish the Russian government for interfering in the 2016 election, could have been evidence of links or coordination between the Trump Campaign and Russia. Accordingly, determining the extent of the defendant’s actions, why the defendant took such actions, and at whose direction he took those actions, were critical to the FBI’s counterintelligence investigation.
That makes sense. After all, Don Jr took a meeting in June with envoys for Aras Agalarov and — at a meeting offering dirt on Hillary Clinton — said his father would reconsider Magnitsky sanctions after the election. Both after that meeting and on October 7 — two of three days that stolen emails were released — Aras Agalarov provided elaborate gifts to Trump, the latter one personally couriered from Russia by Ike Kaveladze. When Agalarov didn’t succeed in revisiting his conversations about sanctions directly after the election, Jared Kushner sought out a back channel. Flynn’s conversations with Sergey Kislyak arose directly out of the meeting at which Kushner made that request, and Kushner ordered Flynn to pursue the discussions with Kislyak. Flynn, Kushner, and KT McFarland made efforts to keep those conversations secret, even from other members of the Administration. At the same time, Flynn and McFarland were explicitly talking about sending secret messages between Putin and Trump.
So it would make sense that Flynn’s effort to undermine sanctions might be proof that Trump had entered into a quid pro quo back in June, rewarding Russia’s help for getting elected with sanctions relief.
But the Mueller Report did not find adequate proof that Trump directed this effort to charge it.
Some evidence suggests that the President knew about the existence and content of Flynn’s calls when they occurred, but the evidence is inconclusive and could not be relied upon to establish the President’s knowledge.
[snip]
Our investigation accordingly did not produce evidence that established that the President knew about Flynn’s discussions of sanctions before the Department of Justice notified the White House of those discussions in late January 2017.
The Report relies on some, but not the most damning, of the exchanges back and forth between Flynn, McFarland and others released in an affidavit targeting them in 2017, as well as Flynn and McFarland’s testimony.
Since that time, several other pieces of evidence have become available — thanks to the interventions of former Acting Director of National Intelligence Ric Grenell and Flynn (and recently fired Trump) attorney Sidney Powell, among others — that might tip the balance on this evidentiary question.
Bill Barnett’s interview report claims he pursued a desired outcome in the interviews of Flynn and KT McFarland
One of those things is the testimony of Bill Barnett, one of the key FBI agents who investigated Flynn. Barnett was interviewed by Jeffrey Jensen in the review of Flynn’s prosecution that Sidney Powell demanded in June 2019 and Bill Barr gave Powell in January 2020, just after DOJ filed a sentencing memo calling for prison time.
Barnett’s testimony is, by itself, remarkable for all the ways it materially conflicts with the actions he took in the case. Effectively, he claims to have treated the investigation as a criminal investigation when documents he drafted clearly treat it as a counterintelligence investigation (thereby undermining all the claims that this was just about the Logan Act).
Barnett also claims that, after expressing disinterest in conducting this investigation four different times but ultimately relenting only so he could serve as a counter-weight to other investigators on the team, he single-handedly prevented the Mueller team from concluding that KT McFarland was lying when she told a story about coordinating with Mar-A-Lago that exactly paralleled the lies that Flynn originally told.
Barnett describes that he was the only one who believed that KT McFarland was telling the truth when she said that she did not remember Trump directing Flynn’s efforts to undermine sanctions. Significantly, he describes this question as — in Mueller’s view — “key to everything.”
Many at the SCO had the opinion that MCFARLAND had knowledge TRUMP was directing [sanction discussions] between FLYNN and the Russian Ambassador. When MCFARLAND did not provide the information sought, it was assumed she was lying. When BARNETT suggested it was very possible MCFARLAND was providing truthful information, one of the SCO attorneys participating in the interview said BARNETT was the only person who believed MCFARLAND was not holding back the information about TRUMP’s knowledge of [the sanction discussions]. MUELLER described MCFARLAND as the “key to everything” because MCFARLAND was the link between TRUMP, who was at Mar-a-Lago with MCFARLAND, and FLYNN, who was in the Dominican Republic on vacation, when [the calls] were made.
Again, it is stunning that Barnett was permitted to give this answer without being asked about the call records, which showed Flynn lied about consulting with Mar-a-Lago, to say nothing about the way that McFarland’s forgetfulness matched Flynn’s and then her unforgetting similarly matched Flynn’s. It’s not a credible answer, but Jeffrey Jensen doesn’t need credible answers.
Then, having made it clear that he believed that Mueller treated McFarland as the “key to everything,” BARNETT described how he single-handedly managed to prevent the entire team from concluding that Trump was in the loop.
BARNETT was told at one point he was being taken off the MCFARLAND proffer interview because SCO attorneys thought would be easier for MCFARLAND to talk without BARNETT there, due to her attitude toward BARNETT during past interviews.
McFarland has complained publicly about being caught in a perjury trap by the FBI agents who first interviewed her (and the 302s show a continuity among the FBI agents), so Fox viewers have actually seen evidence that McFarland had a gripe with Barnett.
BARNETT insisted he be on the interview. When BARNETT was told he would not be allowed on the interview, BARNETT suggested he might take the matter to the Inspectors General or to “11.” BARNETT believed some at SCO were trying to get MCFARLAND to change her story to fit the TRUMP collusion [sic] theory. [Probably Van Grack] later contacted BARNETT and said BARNETT would be part of the MCFARLAND interview.
During the proffer interview with MCFARLAND, the “obstruction team” was leading the interview. BARNETT described the “obstruction team’s” questions as general. They did not ask follow-up or clarifying questions. BARNETT was perplexed by their lack of asking follow-up questions. BARNETT began asking MCFARLAND follow-up questions and direct questions. BARNETT was trying to “cut to the chase” and obtain the facts. BARNETT asked questions such as “Do you know that as a fact or are you speculating?” and “Did you pass information from TRUMP to FLYNN?” Andrew Goldstein (GOLDSTEIN), a SCO Attorney, called “time-out” and cautioned BARNETT by saying, “If you keep asking these questions, we will be here all day.”
It’s unclear whether Barnett’s depiction is correct or not. The 302 of that interview is heavily redacted, but doesn’t show a “time out” in it. What matters for the purposes of this post is that Barnett is claiming he singlehandedly prevented McFarland from implicating the President.
You would never get this kind of admission from an FBI Agent, that he single-handedly undermined the questioning of a witness to get an outcome he believed in, all the while undermining his previously untainted credibility. But Sidney Powell’s demands led to DOJ producing it, nevertheless.
And that’s before any further scrutiny of Barnett’s role and the material inconsistencies here. Such scrutiny might come from the Strzok and Page lawsuits, which would have reason to use his pro-Trump tweets as proof that they were selectively disciplined for expressing political views on FBI-issued devices. Or, particularly given his efforts to blame investigative decisions on Andrew McCabe in ways that conflict with the public record, the McCabe lawsuit might have cause to inquire whether he was the agent who sourced a false story that Sara Carter published, alleging that McCabe said, “First we fuck Flynn, then we fuck Trump,” which ended up leading to the investigation into McCabe itself and ultimately to his firing. Or, DOJ IG might have cause to investigate the Jensen investigation itself, given how it submitted altered documents packaged up for publication, and the circumstances of the Barnett interview in particular, given how DOJ withheld material information from Judge Emmet Sullivan by redacting references to Brandon Van Grack in the interview report.
Interviewing Barnett in such an obviously biased way provides an easy hook for more scrutiny.
For the first time in history we can compare NSLs to warrants obtained
Then there’s another unprecedented thing that Powell’s demands produced: A report of (some of) the NSL’s that DOJ used against Flynn in early 2017. In an effort — almost certainly deliberately misleading — to suggest that McCabe and Strzok inappropriately got NSLs targeting Flynn in 2017 that they chose not to get in 2016 (there’s reason to believe they did get NSLs, only financial rather than communication ones), the government summarized what NSLs FBI obtained in February and March 2017. Those were:
One NSL, authorized on February 2, 2017, sought subscriber and toll billing records for a telephone number associated with Michael T. Flynn for the period from July 1, 2015 to the present.
A second and third NSL, authorized on February 7, 2017, sought “electronic transactional records” for an email address associated with Michael T. Flynn for the period from July 15, 2015 to the present and subscriber information for a telephone number associated with Michael T. Flynn for the period from August 1, 2016 to the present.”
A fourth, fifth, and sixth NSL, all authorized on February 23, 2017, sought toll records for three telephone numbers, for the period of January 1, 2016 to the present, and an email address, for the period of inception to the present, all associated with Michael T. Flynn.
A seventh NSL, issued on March 7, 2017, sought subscriber and transactional information for a telephone number associated with Michael T. Flynn from December 21, 2016, to January 15, 2017.
The government has only recently permitted NSL recipients to inform targets, but just targets, and only after a significant delay. Here, however, you have the government listing out the seven different communication records publicly, in a case where there was already a pending request and precedent to release the warrant applications publicly.
That not only allows us (again, for the first time I know of) to see how the FBI launders information learned in an NSL for use in a potential criminal prosecution, but it also tells us something about the communications devices the government had reason to find relevant when it did obtain warrants.
Warrant applications for Flynn’s iPhone 6 and a computer (first filed on July 7, 2017, then refiled on July 27, 2017) rely on toll records obtained in June 2017 and “other materials in the government’s possession” (which surely include those NSLs) to determine that Flynn had used the same phone from March 2015 until at least June 8, 2017. That said, Flynn changed the number three times, including after he learned he was under criminal investigation in January 2017. After Flynn refused to turn the phone over in response to a subpoena, the government obtained a warrant that would have permitted it to search Covington & Burling, where Flynn was storing it, if they didn’t otherwise produce the phone.
The warrant application and a parallel one targeting Flynn’s son* were focused on FIG, but written in a way such that any communications with foreign officials like Kislyak would still be responsive, and could be used in a False Statements or Foreign Agent prosecution.
By the time of the July 27 warrant that presumably successfully obtained Flynn’s phone, the government already had his Flynn Intelligence Group emails (there are two EDVA warrants that have not yet been unsealed, and some of those emails were turned over pursuant to a subpoena).
Also by that time, the government had confirmed that Flynn’s FIG email was provided by Google. This was the period prior to the time when DOJ agreed to let enterprise clients know when warrants were served on their facilities, meaning the government could have independently obtained FIG emails from Google, as they obtained Michael Cohen’s Trump Org emails from Microsoft in the same period.
On August 25, 2017 — the same day that Mueller asked GSA to turn over related devices and email accounts — Mueller obtained a warrant for Mike Flynn, KT McFarland, and Flynn assistant Daniel Gelbinovich’s devices and emails. GSA had provided Flynn one email account, three phones, and three computers, which would be consistent with devices hardened to three levels of classification — unclassified, Secret, and Top Secret (Flynn had renewed his clearance earlier in 2016). The government had already used a d-order to obtain the header information for the email accounts and obtained toll records by undisclosed means (of which there would be several possible, but the NSLs would have provided that information as well). In addition to sender and recipient information, the header information would have shown what IP any emails were sent from, using what devices (this would have built on information obtained via NSL), which can help to identify the location of someone. The August 25 affidavit referenced FIG emails obtained via subpoena to demonstrate that the Russians contacted Flynn at his Transition account (as well as via Gelbinovich and, apparently, Flynn’s son); though because the Russian side of the conversation would have already been targeted under FISA, the FBI also would have had their side of the communication, which the Russians surely knew.
Then on September 27, 2017, Mueller obtained a warrant targeting the email accounts and devices of Keith Kellogg, McFarland assistant Sarah Flaherty, Sean Spicer, Reince Priebus, and Jared Kushner. These two posts show how damning the content relayed in this warrant is. For the purposes of this post, however, the affidavit is useful because it identifies whether the emails Flynn and McFarland were using to communicate with the others were Transition accounts or not. While it appears Kellogg always used his Transition account, Flaherty, Spicer, and Priebus occasionally did, most of the rest did not, except in cases where they were writing cover emails. But her emails! (Numerous communications from Tom Bossert are included in this batch, as well, but that must come from an interview and subpoena he complied with.)
In addition, the affidavit explains that regarding the sanctions coordination, McFarland was consistently calling Flynn on his personal cell phone (the implication may be that earlier calls were on one of his GSA devices). He was responding to her and calling Kislyak from the hotel phone where he was staying in the Dominican Republic (the latter calls and their content, the FBI would know from FISA intercepts). The December 31 follow-up from Kislyak was placed to Flynn’s personal cell. The affidavit does not, however, describe which phones Flynn used for other calls.
There are many details about these records that are interesting. Among the most interesting, however, is that the FBI would have known before they obtained the first warrants on Flynn’s devices and emails that almost none of the key calls with Russia, nor even the key calls coordinating the Russian sanctions call with McFarland and others, involved Flynn’s GSA devices. Additionally, there appear to be extra phones, not identified by the known warrants. These might be the possible targets of the NSLs:
One NSL, authorized on February 2, 2017, sought subscriber and toll billing records for a telephone number associated with Michael T. Flynn for the period from July 1, 2015 to the present. [Flynn personal phone]
A second and third NSL, authorized on February 7, 2017, sought “electronic transactional records” for an email address associated with Michael T. Flynn for the period from July 15, 2015 to the present and subscriber information for a telephone number associated with Michael T. Flynn for the period from August 1, 2016 to the present.” [Flynn Intelligence Group email and another phone (possibly his son’s?)]
A fourth, fifth, and sixth NSL, all authorized on February 23, 2017, sought toll records for three telephone numbers, for the period of January 1, 2016 to the present, and an email address, for the period of inception to the present, all associated with Michael T. Flynn. [GSA accounts]
A seventh NSL, issued on March 7, 2017, sought subscriber and transactional information for a telephone number associated with Michael T. Flynn from December 21, 2016, to January 15, 2017. [unidentified account]
At a minimum, the NSL report suggests that even though none of the calls identified in the warrants were to Flynn’s presumably more secure phones (indeed, only Spicer appears to have had a second phone at that point, probably in part because, of the others, only Kellogg and Flaherty had clearance), the government chose to obtain those phones as well. The government knew, when it obtained the August 2017 warrant, that there was something interesting on those second and third GSA lines Flynn was using.
If it weren’t for Sidney Powell’s attempts to frame Andy McCabe, these details would be totally classified. But because she demanded the “review,” it shows that there are parallel phone communications via which Flynn could have kept Trump in the loop on his calls to Russia (remember, translators believed the key December 29 one, which Flynn made from his hotel phone, sounded like he was using a speaker phone).
Ric Grenell releases really damning transcripts but withholds the potentially most damning one
Finally, in yet another unprecedented release, while he was Acting Director of National Intelligence, Twitter troll Ric Grenell prepared the release of the actual transcripts of the calls between Flynn and Kislyak, purportedly to show there was nothing untoward about the calls. (Current DNI John Ratcliffe approved the actual release as one of his first acts on the job.)
Even by itself, the transcripts were far more damning than the gaslighters suggested. Of particular note, on the December 31 call that Kislyak placed to tell Flynn that Putin had held off on retaliating because of his request, Flynn told the Russian Ambassador that Trump was aware of one thing — a proposed Syrian “peace” conference — that Kislyak had raised just two days before.
FLYNN: and, you know, we are not going to agree on everything, you know that, but, but I think that we have a lot of things in common. A lot. And we have to figure out how, how to achieve those things, you know and, and be smart about it and, uh, uh, keep the temperature down globally, as well as not just, you know, here, here in the United States and also over in, in Russia.
KISLYAK: yeah.
FLYNN: But globally l want to keep the temperature down and we can do this ifwe are smart about it.
KISLYAK: You’re absolutely right.
FLYNN: I haven’t gotten, I haven’t gotten a, uh, confirmation on the, on the, uh, secure VTC yet, but the, but the boss is aware and so please convey that. [my emphasis]
This evidence would have been inadmissible without Grenell’s intervention. There would have literally no way in hell Mueller would have been permitted to rely on it, a raw transcript of a FISA intercept targeting a foreign power. With it, however, you have Flynn saying in real time that Trump was aware of these conversations with Russia, well before they were made public. That’s precisely what Mueller concluded they couldn’t prove.
The transcripts make evidence obtained using criminal process still more damning, too.
For example, the transcripts and the affidavits make it clear that Flynn, McFarland, and the Russians were explicitly messaging back and forth. First Flynn explicitly told Kislyak that if Russia did not escalate in response to Obama’s sanctions, “we,” which would have to include Trump, would recognize that as a message.
Flynn: And please make sure that its uh — the idea is, be — if you, if you have to do something, do something on a reciprocal basis, meaning you know, on a sort of even basis. Then that, then that is a good message and we’ll understand that message. And, and then, we know that we’re not going to escalate this thing, where we, where because if we put out — if we send out 30 guys and you send out 60, you know, or you shut down every Embassy, I mean we have to get this to a — let’s, let’s keep this at a level that us is, even-keeled, okay? Is even-keeled. And then what we can do is, when we come in, we can then have a better conversation about where, where we’re gonna go, uh, regarding uh, regarding our relationship. [my emphasis]
When Putin announced he would not retaliate, KT McFarland sent two emails explicitly labeling the move as a signal.
My take is Russians are taking the most restrained retaliation possible — it’s his Signal to trump that he wants to improve relations once obama leaves. Although [Obama] didn’t mean to he has given [Trump] new leverage over Putin.
[snip]
Putin response to NOT match obama tit for tat are signals they want a new relationship starting jan 20. They are sending us a signal.
But then Trump thanked Putin for the move, suggesting he was in on the signaling.
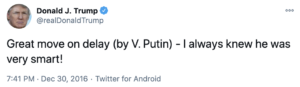
After he did so, McFarland sent Flynn, Kellogg, Flaherty, Priebus, Kushner, and Bannon — the latter of whom almost never used their official accounts but did here — and laid out a cover story, describing Flynn’s call without mentioning that he had raised sanctions. She offered,
a summary of FLYNN’s conversation the day before with the Russian “AMBO,” which I believe to be shorthand for “Ambassador.” McFarland appears to recite a summary of information she received from FLYNN in this email; she provides a summary of FLYNN’s conversation with the Russian Ambassador, but does not indicate that they discussed the sanctions imposed against Russia that had been announced earlier that day.
Flynn would admit to Mueller’s team that he, and therefore McFarland, who knew the truth, deliberately hid his discussions of sanctions with Kislyak.
Shortly thereafter, Flynn sent a text message to McFarland summarizing his call with Kislyak from the day before, which she emailed to Kushner, Bannon, Priebus, and other Transition Team members. 1265 The text message and email did not include sanctions as one of the topics discussed with Kislyak. 1266 Flynn told the Office that he did not document his discussion of sanctions because it could be perceived as getting in the way of the Obama Administration’s foreign policy.1267
But the Russians — who may have monitored some of the traffic that went on between these unsecure personal accounts — made damn well sure that the US intelligence community had a record that all this signaling was intentional. Kislyak called Flynn on his unsecure personal cell phone and told him he had a message, too. The message was that Flynn’s request was the reason Putin had not acted. The message was also that Russia recognized (or claimed to, to play to the Americans’ paranoia) to be pitted against the same hostile entities together.
Kislyak: Uh, you know I have a small message to pass to you from Moscow and uh, probably you have heard about the decision taken by Moscow about action and counter-action.
Flynn: yeah, yeah well I appreciate it, you know, on our phone call the other day, you know, I, I, appreciate the steps that uh your president has taken. I think that it was wise.
Kislyak: I, I just wanted to tell you that our conversation was also taken into account in Moscow and…
Flynn: Good
Kislyak: Your proposal that we need to act with cold heads, uh, is exactly what is uh, invested in the decision.
Flynn: Good
Kislyak: And I just wanted to tell you that we found that these actions have targeted not only against Russia, but also against the president elect.
Flynn: yeah, yeah
Kislyak: and and with all our rights to responds we have decided not to act now because, its because people are dissatisfied with the lost of elections and, and its very deplorable. So, so I just wanted to let you know that our conversation was taken with weight.
This messaging all ended up with Russia and the incoming President aligned on the same side, against the US government.
Still, that’s not direct proof that Trump was involved in real time (though I suspect the government obtained that from its NSLs).
But that may be why Mueller charged Flynn’s lies about the UN vote. In that case (in part because McFarland wasn’t hiding her actions as much), it’s clear that Jared Kushner ordered the effort (and the Americans initiated the calls).
According to records obtained during the course of the investigation, at approximately 8:46 a.m. on December 22, 2016, FLYNN had a four-minute conversation with Jared Kushner. After that conversation concluded, at approximately 8:53 a.m., FLYNN called the Russian Ambassador to the U.S. FLYNN then called a representative of the Egyptian government and had a four-minute conversation with him. At approximately 8:59 a.m., FLYNN had a three-minute conversation with the Russian Ambassador. Over the next few hours, FLYNN had several additional phone calls with the representative of the Egyptian government.
When the Trump crowd succeeded in delaying a vote, McFarland made it clear that Flynn was at Mar-a-Lago working directly with Trump on this effort.
At approximately 8:26 p.m. on December 22, 2016, K.T. McFarland emailed FLYNN and Sarah Flaherty and stated that FLYNN had “worked it all day with trump from mara lago.”
And in spite of the fact that he himself initiated the effort, Kushner sought to release a public cover story, to hide that he and his father-in-law initiated the effort.
Kushner replied all to that email [including Spicer, Bannon, Priebus, Kellogg, McFarland, Kushner, and one other person whose name is redacted] and wrote: “Can we make it clear that Al Sisi reached out to DJT so it doesn’t look like we reached out to intercede? This happens to be the true fact pattern and better for this to be out there.”
This was a lie — a lie designed to cover up that he and Trump and Flynn had worked with Egypt (which had allegedly bribed Trump to get him through the election) and Russia (which had conducted an elaborate operation to help him) to thwart the vote and with it the official US policy not to protect Israel’s illegal settlements.
As it turns out, the transcript from Flynn’s call to Russia that day isn’t among those Grenell released because they were so helpful to Trump. Even the one-line summary of the call, released for all other substantive calls, remains redacted.

But there, too, Kislyak may have been performing for the FBI intercepts he knew would catch these calls.
First, on the December 23 call — the one after the call for which the transcript hasn’t been released — Kislyak assures Flynn that whatever happened on it was considered by Putin.
Kislyak: Uh, I just wanted as a follow up to share with you several points. One, that, uh, your previous, uh, uh, telephone call, I reported to Moscow and it was considered at the highest level in Russia.
Then on the December 29 call, when Flynn asks Kislyak that Russia not box in the new Administration, Kislyak says that message has already been conveyed.
FLYNN: do not, do not uh, allow this administration to box us in, right now, okay? Um —
KISLYAK: We have conveyed it.
That request wasn’t in the December 23 call, so it must have been in one of the communications that preceded it, possibly even the face-to-face with Kushner in Trump Tower.
In his December 22 call — the one the content of which Grenell hid — Flynn made an ask of Russia, an ask that went beyond a vote at the UN. That was a call made from Mar-a-Lago, possibly even made with Trump on the call. That was a call that McFarland bragged Trump was involved with personally.
The Mueller Report, relying on evidence that would be admissible in court, said it was unclear how involved Trump was in any of this. But thanks to Ric Grenell, we now have solid evidence he was personally involved, if not on the phone for the call.
And even Bill Barr’s DOJ says that kind of personal involvement from Trump might amount to the kind of coordination that Bill Barr claimed didn’t exist.
When Mueller closed up shop, his team decided that they couldn’t make this case in court. Now, thanks to Sidney Powell and Ric Grenell, the Biden Administration may have a much easier time making that case.
*We know this warrant targeted Michael G. Flynn because it was sent to Barry Coburn, who represented the failson, because the warrant always refers to Flynn père as Michael T. Flynn (as an affidavit referencing both would necessitate), and the target of the third warrant tried to invoke the Fifth Amendment for questions about Flynn Sr.