Guccifer 2.0: What about those DCCC and “Clinton Foundation” documents
In this post, I addressed one recent and one not-recent research finding pertaining to Guccifer 2.0 (I had already raised both of them, but I addressed them at more length). I pointed out the conclusions of the research itself (that Guccifer 2.0 put Russian metadata in the first documents he released intentionally, just as he had put the name Felix Dzerzhinsky in one; and that some files released by proxy in September were copied locally) were not that controversial and certainly don’t refute the Intelligence Community conclusion that Russia was behind these hacks.
I also pointed out something that came out of that and related research — the understanding that the documents Guccifer 2.0 first released weren’t the DNC documents released to WikiLeaks at all, and so had absolutely no bearing on the question of whether Guccifer 2.0 provided the DNC documents to WikiLeaks. The NYer’s Raffi Khatchadourian used that same data as part of his argument that Russia was clearly working with WikiLeaks.
Cui bono from DCCC documents
Not only does all this analysis focus on the DNC when it really should focus on Hillary documents, but it almost entirely ignores the later documents Guccifer 2.0. For example, here’s how Adam Carter dismisses the import of the DCCC documents in considering attribution.
The documents he posted online were a mixture of some from the public domain (eg. already been published by OpenSecrets.org in 2009), were manipulated copies of research documents originally created by Lauren Dillon (see attachments) and others or were legitimate, unique documents that were of little significant damage to the DNC. (Such as the DCCC documents)
The DCCC documents didn’t reveal anything particularly damaging. It did include a list of fundraisers/bundlers but that wasn’t likely to cause controversy (the fundraising totals, etc. are likely to end up on sites like OpenSecrets, etc within a year anyway). – It did however trigger 4chan to investigate and a correlation was found between the DNC’s best performing bundlers and ambassadorships. – This revelation though, is to be credited to 4chan. – The leaked financial data wasn’t, in itself, damaging – and some of the key data will be disclosed publicly in future anyway.
Even ignoring that some of these documents provided the DCCC’s views of races and candidates, the notion that data will one day become public in no way minimizes the value of having that data in time for an electoral race, which is what Guccifer 2.0’s release of them did.
Even Khatchadourian simply nods at what, given the timing, are likely the DCCC documents. After laying out what are suggestions of pressure Assange’s source is exerting on WikiLeaks in the early summer, he reveals that in August, Guccifer 2.0 considered leaking documents through Emma Best (who, notably, had just linked the Turkish emails that WikiLeaks would get blamed for at the end of July).
In mid-August, Guccifer 2.0 expressed interest in offering a trove of Democratic e-mails to Emma Best, a journalist and a specialist in archival research, who is known for acquiring and publishing millions of declassified government documents. Assange, I was told, urged Best to decline, intimating that he was in contact with the persona’s handlers, and that the material would have greater impact if he released it first.
Given the mid-August date, those emails are likely the DCCC emails that Guccifer 2.0 first announced on August 12 by publishing the contact information of members and their key staffers (one of the several things over the course of the operation that got suppressed by providers). While Khatchadourian doesn’t dwell on what happened to them instead of release via Best, it is significant: Guccifer 2.0 reached out to local journalists to report on the state-level data. That is, for a limited set of what must have been available at DCCC, a set focused on swing states (which, contrary to what Carter suggests, cannot be bracketed off from the top of the ticket in a presidential year), Guccifer 2.0 worked to magnify these documents too, with mixed success.
It’s hard to imagine why anyone associated with the Democratic party or Crowdstrike — who both have been accused of being the real insiders behind the Wikileaks documents — would release those documents, no matter how uninteresting people outside of politics find them. Likewise, even the most bitter Bernie supporter would have little reason to help Republicans get elected to Congress. Leaking boring but useful documents that benefit just Republicans doesn’t even fit with the hacktivist persona Guccifer 2.0 presented as. That leaves GOPers, as well as the Russians if they were siding with the GOP, with sufficient motive to hack and leak them.
Moreover, given questions about whether Republicans incorporated data made available by Russia in their own data analysis, the release of these documents may have provided a way to do that while maintaining plausible deniability. This stuff could get more interesting now, given that Ron DeSantis, who benefitted from these state level leaks, wants to cut the Mueller investigation short.
What about Guccifer 2.0’s Clinton Foundation headfake?
Which brings us to some other still unexplained events from last year: Roger Stone’s promises that WikiLeaks would release the Clinton Foundation emails in early October. A lot gets missed in the public narrative of that period. Stone turned out to repeatedly promise files, only to be wrong, which (on its face, anyway) undermines Democratic accusations he was in cahoots with WikiLeaks. And ultimately, WikiLeaks didn’t publish the Clinton Foundation files; instead, it released the Podesta document that included excerpts of Hillary’s speeches. Though — again, contrary to what the Democrats now complain — those were completely drowned out by the Access Hollywood release. No one mentions, either, that Stone sort of sulked away, uninterested in WikiLeaks emails anymore, moving on to Bill Clinton rape allegations. What happened?
Here’s what I laid out in April.
CNN has a timeline of many of Stone’s Wikileaks related comments, which actually shows that in August, at least, Stone believed Wikileaks would release Clinton Foundation emails (a claim that derived from other known sources, including Bill Binney’s claim that the NSA should have all the Clinton Foundation emails).
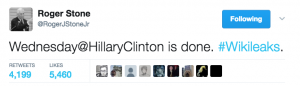
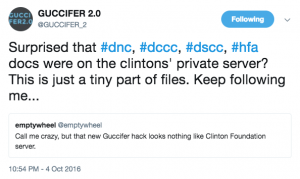
It notes, as many timelines of Stone’s claims do, that on Saturday October 1 (or early morning on October 2 in GMT; the Twitter times in this post have been calculated off the unix time in the source code), Stone said that on Wednesday (October 5), Hillary Clinton is done.
Fewer of these timelines note that Wikileaks didn’t release anything that Wednesday. It did, however, call out Guccifer 2.0’s purported release of Clinton Foundation documents (though the documents were real, they were almost certainly mislabeled Democratic Party documents) on October 5. The fact that Guccifer 2.0 chose to mislabel those documents is worth further consideration, especially given public focus on the Foundation documents rather than other Democratic ones. I’ll come back to that.
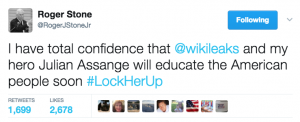
Throughout the week — both before and after the Guccifer 2.0 release — Stone kept tweeting that he trusted the Wikileaks dump was still coming.
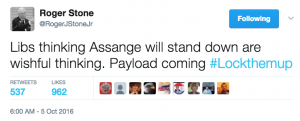
Wednesday, October 5 (though this would have been middle of the night ET):
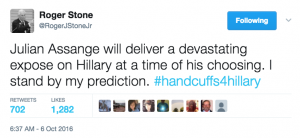
Thursday, October 6 (again, this would have been nighttime ET, after it was clear Wikileaks had not released on Wednesday):
On October 7, at 4:03PM, David Fahrenthold tweeted out the Access Hollywood video.
On October 7, at 4:32 PM, Wikileaks started releasing the Podesta emails.
Stone didn’t really comment on the substance of the Wikileaks release. In fact, even before the Access Hollywood release, he was accusing Bill Clinton of rape, and he continued in that vein after the release of the video, virtually ignoring the Podesta emails.
Two parts of this narrative now look very different, given what we know now. As noted, Kachadourian argues that Guccifer 2.0 served as a pressure point for WikiLeaks, pushing Assange to release things on the persona’s timeline. I’ve long been puzzled (for obvious reasons) by Guccifer 2.0’s response to my tweet, calling out his supposed October 4 release of Clinton Foundation documents as the bullshit it was.
There was no private conversation behind this — Guccifer 2.0 and I never spoke by DM. My guess is he chose to respond to my tweet because Glenn Greenwald immediately responded to me and took my debunking seriously, though Guccifer 2.0’s response was quick — within 45 minutes. And only after that tweet did he follow me. It was a rare unsolicited response to someone, and it was one of maybe three tweets he sent responding to a criticism. (Interesting side note: I realized when reviewing his tweets that a few of Guccifer 2.0’s tweets appear in Twitter’s count but are not visible.) In other words, Guccifer 2.0 apparently wanted to respond to my debunking, perhaps because Greenwald found them credible, thereby sustaining the claim he really had Clinton Foundation emails. But it happened at a time when Stone, too, was pushing WikiLeaks to release Clinton Foundation emails.
Now couple that information with the details of GOP rat-fucker Peter Smith’s attempt to hunt down Clinton Foundation emails. As Matt Tait describes, close to the July 22 release of the the DNC emails, Smith contacted him already having been contacted by someone who claimed to have copies of Hillary’s Clinton Foundation emails.
Over the course of a long phone call, he mentioned that he had been contacted by someone on the “Dark Web” who claimed to have a copy of emails from Secretary Clinton’s private server, and this was why he had contacted me; he wanted me to help validate whether or not the emails were genuine.
The WSJ explained that Smith could never authenticate any of the emails he got pitched, which is why they weren’t ever published, and recommended they be dealt to WikiLeaks.
So what if someone actually did deal those emails to WikiLeaks, authentic or not? What if Guccifer 2.0 somehow knew that? It would explain Stone’s certainty they’d come out, Guccifer 2.0’s attempt to claim he had them, and the back-and-forth in early October.
Incidentally, the latest stink in the right wing noise machine is that a guy trying to obtain more Hillary related emails via FOIA got denied because the public interest doesn’t outweigh Hillary’s privacy interests. [Deleted: this was one of the fake Assange accounts–thanks to Arbed for heads up.] Assange claim he has duplicates.
To be clear, I don’t believe those are Clinton Foundation emails. But I find the possibility that Assange may still be getting and releasing materials damning to Hillary.
Guccifer 2.0’s other propaganda
Finally, it’s worth noting that these reassessments of Guccifer 2.0 largely look at the documents he released, out of context of the things he said.
I think that’s particularly problematic given this last two posts, which align with activities alleged to have ties to Russia. His second-to-last post was typically nonsensical (the FEC’s networks have nothing to do with vote counting). But it attributed any tampering with software to Democrats.
INFO FROM INSIDE THE FEC: THE DEMOCRATS MAY RIG THE ELECTIONS
I’d like to warn you that the Democrats may rig the elections on November 8. This may be possible because of the software installed in the FEC networks by the large IT companies.
As I’ve already said, their software is of poor quality, with many holes and vulnerabilities.
I have registered in the FEC electronic system as an independent election observer; so I will monitor that the elections are held honestly.
I also call on other hackers to join me, monitor the elections from inside and inform the U.S. society about the facts of electoral fraud.
We’ve since learned (most recently in this NYT piece) that there was more risk of tampering with the vote count than initially revealed. And no matter whether or not you believe the Russians did it, there is no credible reason why Democrats would target turnout that they needed to win the election. This message, Guccifer 2.0’s last before the election, could only serve to give pre-emptive cover for any tampering that did get discovered.
Finally, there’s Guccifer 2.0’s last post, bizarrely posted months after he seemed to be done, capitalizing on legitimate complaints about the first Joint Analysis Report released on December 29 to suggest the evidence implicating him as Russian is fake.
The technical evidence contained in the reports doesn’t stand up to scrutiny. This is a crude fake.
Any IT professional can see that a malware sample mentioned in the Joint Analysis Report was taken from the web and was commonly available. A lot of hackers use it. I think it was inserted in the report to make it look a bit more plausible.
But several things are interesting about this post (in addition to the way it coincided with what Shadow Brokers claimed was going to be his last post). In spite of using the singular “this” to refer to the “reports,” Guccifer 2.0 claims that several reports tie him to Russia.
The U.S. intelligence agencies have published several reports of late claiming I have ties with Russia.
But the JAR actually doesn’t mention him at all. What does mention him is the Intelligence Community Assessment.
We assess with high confidence that the GRU used the Guccifer 2.0 persona, DCLeaks.com, and WikiLeaks to release US victim data obtained in cyber operations publicly and in exclusives to media outlets.
Guccifer 2.0, who claimed to be an independent Romanian hacker, made multiple contradictory statements and false claims about his likely Russian identity throughout the election. Press reporting suggests more than one person claiming to be Guccifer 2.0 interacted with journalists.
Guccifer 2.0’s silence about the ICA is all the more interesting given that the post — dated January 12 and so immediately after the leak of the Steele dossier — doesn’t mention that, but says the Obama Administration would release more fake information in the coming week.
Certainly, those who believe Guccifer 2.0 is not Russian even while noting his many false claims will take this post as gospel. But it’s worth noting that it doesn’t actually refute the substance of the claims made about Guccifer 2.0, rather than Russia.
Reassessing the Role of Guccifer 2.0 Should Not Terrify Analysts
I’m glad folks are still poking around the Guccifer 2.0 documents, and applaud the openness of the researchers to respond to criticism. Frankly, it’s a model those who made initial claims about Guccifer 2.0 — most egregiously, that Cyrillic metadata in a document adopting the name of Felix Dzerzhinsky would not be every bit as intentional as that graffiti — should adopt. There were errors in the early analysis of the Guccifer 2.0 persona (such as the assumption he was publishing DNC documents), that, with hindsight, are more clear. One particularly annoying one is the logic that because Guccifer 2.0 got caught pretending to be Romanian — a claim he backed off of in his FAQ a week later in any case — he had to be Russian. The unwillingness to revise early analysis only feeds the distrust of the Russian attribution.
That said, in my opinion nothing about the new analysis undermines the claim of Russian attribution, and the majority of the known evidence does support it (and has since been backed — for example — by Facebook, which has its own set of global data to draw from).
Update: I thought Stone was involved in the Smith effort. This article describes him as chatting to Guccifer 2.0 at the direction of Smith.
“The magnitude of what he was trying to do was kind of impressive,” Johnson said. “He had people running around Europe, had people talking to Guccifer.” (U.S. intelligence agencies have linked the materials provided by “Guccifer 2.0”—an alias that has taken credit for hacking the Democratic National Committee and communicated with Republican operatives, including Trump confidant Roger Stone—to Russian government hackers.)



Maybe OT: An interesting take over at TPM yesterday, in that the “dirt on HRC” idea behind Jr’s June 9 meeting was really about “Dirt on the DNC”. The DNC and HRC could easily be conflated, especially in the eyes of the BernieBros. The key point here is that Natalia was peddling non-public info, which might have come from the hacks here.
http://talkingpointsmemo.com/edblog/my-theory-on-manaforts-notes
But she also said they were not proof.
If they were really from any hacking, one would think there would exist some kind of ‘smoking gun’ that was solid evidence for their pitch.
But she said not proof. Not solid.
Maybe Trump smelled it out.
Russia wants the sanctions lifted.
“May rig the elections on November 8. ”
Sounds like pre-emptive cover to buy cred if HRC did win. And then another avenue of attack post-election.
Sounds like Gucifer2.0 really thought HRC would win.
He may actually be Russian, but he very well may be working for some group in US.
If he is not in US, he would not be involved in FEC, right? Unless his statement is pure BS, pure distraction.
I am not sure that is a valid assumption.
bmaz,
An excellent observation applicable to all of the assumptions (assumed to be information and informative) blathered by all parties weighing in on this sop-orific soup -erficial brew-up of Breathless-News subject…
If Guccifer 2.0 was intended as a distraction after Assange’s announcement on 12th June that WikiLeaks had upcoming publications related to the US election, could the fact that none of Guccifer 2’s early documents are DNC documents be because, IIRC, Assange’s ITV interviewer specifically asked him about “unpublished emails from Hillary Clinton’s private server… not yet public” (Assange was fairly evasive/non-committal in reply: “we have emails related to Hillary Clinton that are pending publication, that is correct”) so therefore the people behind Guccifer 2 did not know exactly which set of documents they needed to distract from? Could this explain why the first G2 documents come from a variety of places? Virtually everyone seems to have ASSUMED the upcoming WikiLeaks publications would be either Clinton Foundation or Clinton private server – Roger Stone, Peter Smith, Matt Tait, maybe Guccifer 2 himself – but could it be they all took their cue from Robert Peston’s QUESTION to Assange on 12th June? It’s really worth watching the original footage to see what I mean. At any rate, it does look as if the only people who knew what WikiLeaks was going to publish are Craig Murray (two separate DC insider leaks – both with “legal access” to the materials – always thought that “legal access” remark was significant but no one’s pursued it) and Assange.
As for the New Yorker info about Guccifer 2’s prediction on July 5th that Wikileaks had DNC documents, is it possible that by then Crowdstrike had actually traced the source of the leak and knew its contents? What date was Seth Rich offered a job on Hillary’s campaign? I know it was a few days before his death on July 10th.
Lastly, I’m surprised to see you using a tweet by the parody account @RealAssange and misattributing the quote to Julian Assange. No wonder your estimation of him has gone down if that reflects the quality of your research on Wikileaks matters.
Thanks for the heads up on Assange–I’ve deleted. That’s one of the better fakes.
I’m not sure how your explanation of the not-DNC documents helps at all? G2 would still have had a range of documents to release. What he did release was more apparently a response to the DNC-driven WaPo report than Assange, down to the oppo report on Trump. It also would have (as it apparently did) freaked Dems out even more given that they would know they had been targeted further than their public claims on June 14.
And if you’re going to assume, as you have, that this is Crowdstrike, then you should answer the substance of this post, which is why Crowdstrike would hurt Dems by leaking DCCC docs? Or why CS would feed a November narrative that could never help the Dems?
Crowdstrike is Atlantic Council, the modern day Trilateral commission.
Yup. And as I’ve noticed the FBI rather pointedly hasn’t agreed with everything they said.
Also, can you point to where Murray indicates he knew what WL was going to publish? I don’t think I’ve seen that and he has vacillated on whether he even got the docs themselves or something else. Given the two-dates issue I pointed to in my last point I think that’s significant.
Craig Murray clarifies the Daily Mail’s misreporting of his meeting with one of Wikileaks’ sources (presumably the Podesta one, given he was in the US on September 24th) here:
https://www.craigmurray.org.uk/archives/2016/12/russian-bear-uses-keyboard/comment-page-1/#comment-643236
https://www.craigmurray.org.uk/archives/2016/12/russian-bear-uses-keyboard/comment-page-1/#comment-643257
I’ve often wondered why Craig was initially denied a visa to visit Washington earlier in that month – quite extraordinary that would happen to an ex-ambassador for the first time ever. Only overturned after an outcry.
http://www.truthdig.com/report/item/us_denies_entry_to_former_british_ambassador_craig_murray_20160906
Given the amount of surveillance of the Ecuador embassy by NSA’s partners GCHQ, I wonder what they knew…?
Oh, by the way, you also mentioned Scott Ritter’s analysis of the VIPS/Adam Carter/Forensicator articles. Did you know Scott Ritter’s analysis of Reality Winner’s document claims that it shows the GCHQ Muscular program (apparently, the Winner doc markings show this is where the NSA analyst sourced his info) did not detect any hack of the DNC?
https://www.truthdig.com/articles/leaked-nsa-report-short-on-facts-proves-little-in-russiagate-case/
Yes, I agree. Guccifer 2’s release of the Trump Oppo report that had been specifically mentioned by Crowdstrike in the Washington Post the previous day was the main way he was able to ‘authenticate’ himself to so many journalists that he set about contacting willy-nilly over the following days.
I’m a bit confused. I asked you to point to where Murray said he knew what WL was going to publish. You linked to comments that back what I’ve said: that he didn’t know enough about who he talked to to rule out the Russians:
But nothing there says anything about his knowledge of publication. Do you have a source for that?
For what it’s worth, I was not working off that Daily Mail piece, which is part of why I have noted the timing disparity.
Ah, does Craig not say in the article above that he knows “for certain” that it was not the Russians because he has met one of the people involved in the leak? He is adamant that the leaker is a “DC insider with legal access”. Ok, that could be an American double agent working within the DC community on behalf of the Russians – bit far-fetched but feasible I suppose – but I assume that when Craig Murray spoke to someone – either the actual leaker or a proxy for them, he’s not sure – in America he’d recognise if the person he was talking to was American or Russian? I’d also hazard a guess they spoke about the content of whatever Craig was passed by that person on September 24th. As WikiLeaks did not publish the Podesta emails until October 7th, I’d call that “in advance”, wouldn’t you?
I absolutely agree that Murray would recognize if he were speaking to a Russian. Given that the Steele dossier says there were Democratic moles involved in this operation, I don’t see why having an American double agent is far-fetched (actually, it’d only have to be single agent–Murray didn’t speak to the NatSec person, but a cut-out).
Even in that passage Murray says he didn’t carry the email back. Elsewhere he said “I didn’t receive the emails full stop.” So not only are you now “hazard[ing] a guess” but it’s based off the faulty understanding that Murray actually carried the emails back, which he pointedly and repeatedly denies.
Yes, it’s intriguing, isn’t it? I think Murray backed away because he got slapped down by Assange, who said in interview that Murray was “not authorised” to speak on Wikileaks’ behalf.
I wonder what “small role” Murray did play? Fetched the password to an encrypted dropbox, perhaps, as the Sy Hersh audiotape intimated? And what part did Gavin MacFadyen play in all this? I can’t wait to see what Assange comes up with on this promised “100% proof that it wasn’t the Russians”.
Murray’s answers are consistent with those he gave elsewhere, for example to Scott Horton, before the Assange slapdown. I’ve thought about a password, but that’s inconsistent with having the emails in August.
I think Assange will focus on the 10 email box thing. But by the time he does it may be too late for that to be sustainable either, which maybe why he’s asking for a pardon first, before he reveals the info.
Also confused. That Ritter piece (it has been removed from the link you provided at Truthdig, but you can find it here, where you can review what it actually says)
He makes several errors in it. 1) He focuses on the DNC server, not Hillary’s. As I’ve laid out here, that’s irrelevant to the question at hand. 2) He claims this info had to have come from Muscular. That’s nonsense. It came from FISA, Muscular is 12333. Google servers are subject to 702, as anyone who knows the most basic stuff about NSA spying could tell you. 3) He treats two documents as one. While his observations about certainty are interesting, that’s a document with its own pagination.
That I find Ritter’s take more balanced than the VIPS letter (you’ll note Ritter joined this rebuttal, making many of the same points I have), that doesn’t mean I agree with it. It’s just representative of where I think skeptics can fairly take the evidence, as compared to the VIPS letter that takes it well beyond what is dictated.
Ok, thanks. You are the expert on 702 and 12333 so I’ll take your word for it that Ritter has got things wrong. This was the part of what he said I was persuaded by:
The classification markings on the NSA document leaked by Winner likewise provide clues as to the dearth of forensic data available to the U.S. intelligence community when it comes to attributing the GRU-APT 28 to cyberattacks on the American electoral process. The information clearly is derived from the interception of internet activity—the body of the report focuses on the use of Google by the cyberoperators as the vector for their spear-phishing efforts.
According to documents leaked by Edward Snowden, the sole source of collection against Google Cloud connectivity between Europe (i.e., “neutral space”) and the United States (i.e., “target space”) is through a program known as “Muscular,” which taps into four T16 communication cables at a London-based commercial facility referred to as DS-200B. Muscular is run by the British equivalent of the NSA, known as the Government Communications Headquarters, or GCHQ.
The classification markings on the NSA document leaked by Winner indicate that it is “originator controlled” (i.e., a foreign source) that has been released to the United States via protocols that comply with the requirements of the Foreign Intelligence Surveillance Act, or FISA. The only source for collection against European-based Google Cloud data is the GCHQ-run Muscular operation.
However, in order for this data to be released to the NSA for subsequent analysis using a separate U.S.-based system, known as “Turmoil,” it would have to confirm the requirements of FISA Act 702, governing the collection of communications intelligence from foreign sources. The presence of the FISA marking indicates that, with regard to the data collected in the NSA document, this is the case.
The contents of the NSA document, together with its security markings, strongly suggest that this represents the first significant independent analysis by an American intelligence agency of data linked to activity attributed by to APT 28-GRU. Neither the CrowdStrike data covering the March-April 2016 DNC cyberattack nor the hacking of Podesta’s email server was covered as a collection requirement by either the FBI or NSA. Muscular apparently did not detect the 2016 DNC attack, and the Podesta event simply involved hacked emails.
Yeah. And that’s sheer nonsense. Here’s the original report on Muscular, which not only makes it clear it operates under 12333, not FISA, but notes that the entire reason you’d use Muscular instead of FISA is to get around FISA’s more stringent requirements. You’ll note, too, that DiFi responded to that report by 1) admitting they don’t review 12333 as closely and 2) saying they would. Subsequently, they did pass more restrictions on 12333 precisely because Muscular was an abuse of 12333 that implicates USPs.
As I’ve noted, NSA’s 702 authority clearly covers cloud servers (this is clear from Yahoo filings in 2008). So the claim this would involve Muscular at all is nonsense.
Finally, as I’ll shortly post, Winner makes it clear that the main document she pointed to was not Google based.
I did post an answer to your questions, Marcy, but I think it got stuck in moderation. It had about four links in it, which I guess gums up the works a bit. Sorry.
Liberated. It in no way answers my questions. They’re nice links and all but off point to most of my questions and actually support my point wrt the Murray one.
Do you have links that actually support your argument? I’m happy to read them.
here is an august, 2016 Threatconnect’s post on parts of the grand russian voter (not election, voter) manipulation sceme:
https://www.threatconnect.com/blog/does-a-bear-leak-in-the-woods/
note the passionate comment on the lasting effects of effective propaganda at the end of the post. if that comment stirs your cynacism or disbelief once again, you need to have a long talk with yourself about how democracy succeeds – or fails – and what your priorities are.