The Cultivation of Don Jr: A Framework to Think of the Russian Attack
Months ago, I started laying out a framework to provide background to explain how Trump has trained the GOP to hate rule of law, a key part of how he has brought us close to fascism. My weekend post on Bill Barr’s obfuscation about his role in Ukrainian matters (to which there will be a follow-up) started to fill in another of the remaining bullets.
- Trump’s narcissism makes him easy to trigger
- Trump released documents that past actors assumed would never be released
- The first time Trump “colluded” with Russia was to help Bibi Netanyahu dodge accountability
- Corruption is a process and a tool
- What is WikiLeaks
- Russia’s flipping focus
- My understanding of the Russian attack
- The import of chat rooms
- Rudy Giuliani was never investigated as the possible UNSUB
- John Durham’s studied ignorance
- Seth DuCharme’s information collection
- The GRU propaganda from the US Attorney for Pittsburgh
- Was Bill Barr even more corrupt than we knew? [Barr Time 1]
Today, and in parallel, LOLGOP and I will begin to release some podcasts as we explain the important part: how all this brings us to where we are, with both Aileen Cannon and SCOTUS taking active measures [heh] to help Donald Trump avoid accountability.
So I need to explain how I think of the Russian attack.
Generally, people think of the Russian attack in the same way Robert Mueller set up Volume I of his Report:
- Volume I Section II: [Dead] Yevgeniy Prigozhin’s social media campaign
- Volume I Section III: GRU’s hack and leak campaign
- Volume I Section IV: Russian Government contacts to the Trump campaign
Remember, his report was an explanation of prosecutorial decisions. It was only intended to determine whether things were crimes. It only included the prosecutorial decisions that had been concluded by Mueller. So, for example, the report itself didn’t describe the referrals sent to other districts, such as SDNY’s prosecution of Michael Cohen for financial crimes and hush money payments or EDNY’s prosecution of Tom Barrack on foreign agent crimes, which ended in acquittal; it remains unclear how much of these referrals show up in the referral section. Mentions of ongoing investigations, such as into the suspected $10 million payment to Trump from an Egyptian bank or evidence that Roger Stone conspired with Russian in the hack-and-leak, were relegated to the appendix or a footnote.
The SSCI Report instead considered whether these things posed a counterintelligence risk, rather than a crime. As such, they considered a long list of possible compromises, categorized both by people (like Paul Manafort or Maria Butina — the latter of whom was not included in scope of Mueller Report) and events (like the June 9 meeting). Viewed from that framework, having a guy who spent years implementing influence operations for Russian allies Manafort, work for “free” on the campaign looks quite different, like a grave counterintelligence risk to Donald Trump. Great swaths of that report — such as a section on Andrii Telizhenko’s influence operations, which may even have incorporated Bill Barr — remain redacted.
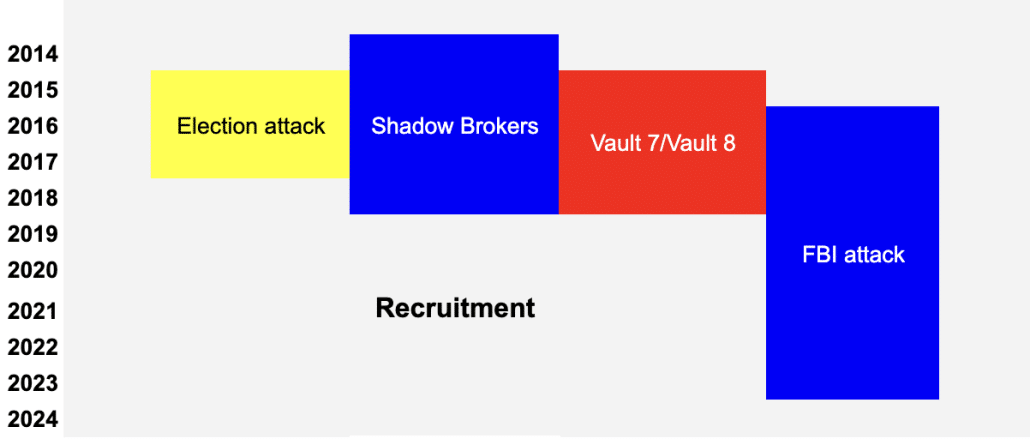
But as this effort to interfere in the US election proceeded, Russia conducted at least two (and, I argue, at least a third) devastating attacks on US intelligence, which had ties to the election year attack itself.
- The Shadow Brokers release of NSA’s hacking tools, which (I was told but have not reconfirmed) shared one forensic link and has several human infrastructure links to the election attack
- The Vault 7/Vault 8 release of CIA’s hacking tools, which in implementation continued a pressure campaign by Julian Assange rooted in the election year attack
- A concerted campaign against the FBI, largely focused but not exclusively reliant on the Steele dossier
The Solar Winds attack, discovered in the last year of Trump’s presidency, could be another such attack, one used by Sidney Powell’s team (including Mike Flynn and Patrick Byrne) in their attack on democratic elections, one that stole Chad Wolf’s emails as he helped Trump discredit election integrity efforts, one Trump is using in his attack on rule of law. The attack was first initiated years earlier, possibly as early as 2016. But so little is known about the attack — aside from that it targeted a number of government agencies and court filing systems — that I will bracket that for now.
This sets up a structure something like this:
What Mueller includes in his contacts with Russia section is possible (and in some cases, definite) attempted recruitment. That kind of thing is a constant.
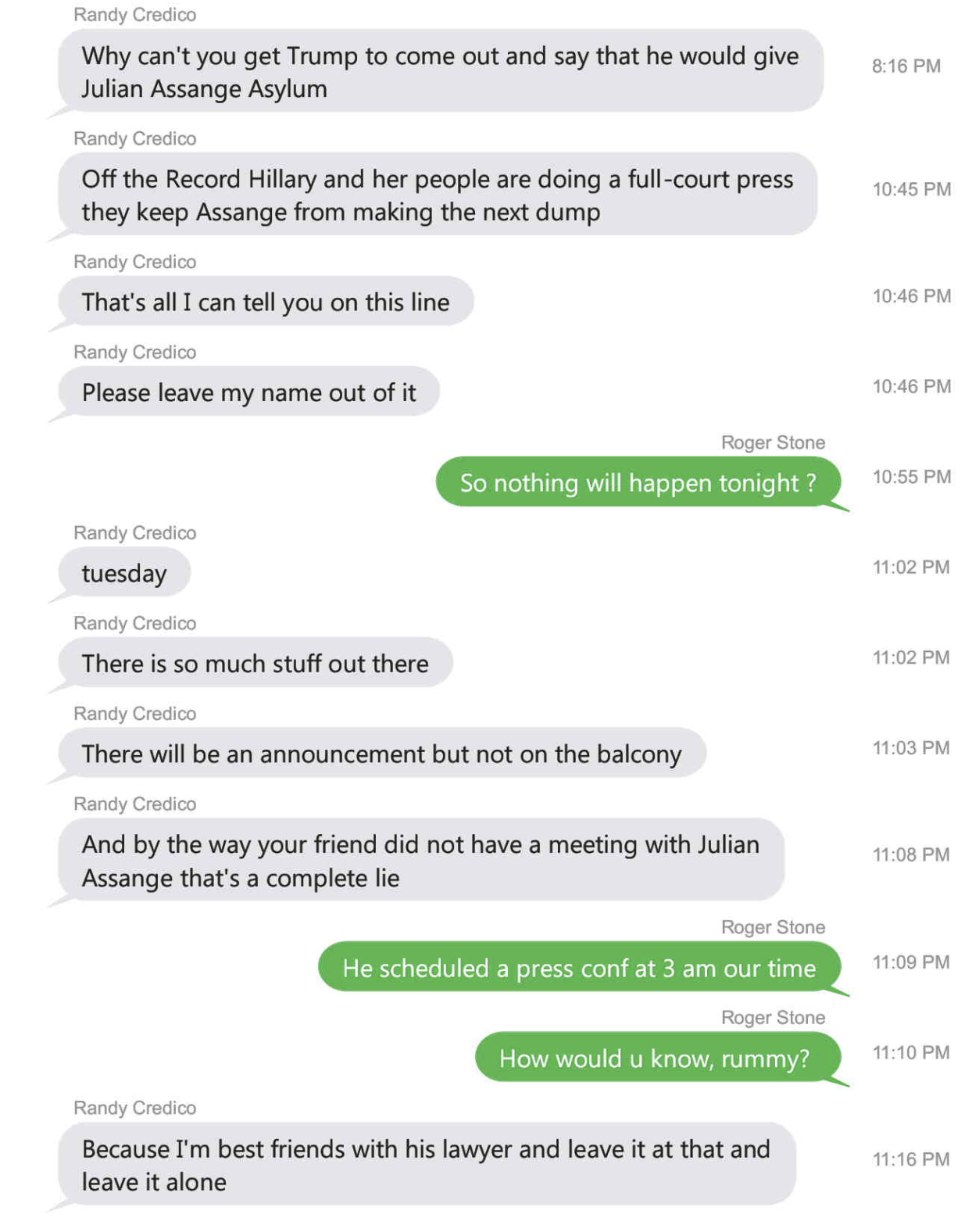
In advance of the Russian attack, however, Russian entities may have been behind a number of efforts focused on Trump and his associates. Deripaska worked a brutal double game that made it more likely to get Manafort’s cooperation, witting or not. Joseph Mifsud brokered ties to Russian officials for George Papadopoulos — leading to an (aborted) plan to set up a meeting with Putin’s team in London. A former GRU officer and two sanctioned banks got involved in Felix Sater’s pitch of a Trump Tower to Cohen, resulting in Dmitry Peskov collecting proof of Trump’s willingness to work with GRU before the Hillary hack was ever revealed. Someone dangled stolen emails before Roger Stone, ultimately giving him an advance peek — in exchange for what, we don’t know — but Stone started pursuing a pardon for Julian Assange no later than November 15 (and probably as early as October 3).
With the exception of the Manafort pitch (which leveraged his financial desperation), none of those pitches from Russia — whether they were backed by Russian spooks or not — would have required anything more than recklessness and venality from the Trump side. For example, in January, when Cohen called Dmitry Peskov to ask for Putin’s help finalizing the Trump Tower deal, Trump probably doubted he was going to win and there was no reason to be particularly alarmed by the GRU tie; but after the revelation that GRU hacked the DNC, after Trump got the nomination, the existence of the January call became potentially devastating. The Coffee Boy bragged to diplomats from three different countries that Russia was going to attack Hillary, which looked dramatically different when WikiLeaks released the stolen DNC emails (which is when the Australians shared their knowledge of it).
If I’m right that Russia deliberately used some of the same infrastructure in the hack-and-leak and the Shadow Broker operation, it would serve as a stick unveiled at precisely the moment Roger Stone bit on the carrot of advanced access to John Podesta emails, basically tying Stone’s outreach to an attack on the NSA.
Similarly, the unveiling of the Vault 7 release, which WikiLeaks (or an intermediary between Josh Schulte and WikiLeaks) sat on from May 2016 until March 2017, made Stone’s sustained commitment to winning a pardon for Assange all the more damaging. It is unknown whether Russia got an advanced look at those files (which would have provided a way to identify CIA’s assets in Russia), but Assange used a Deripaska-linked attorney to try to negotiate immunity in advance of releasing the files, tying its release to Russia.
Along with Stone, this entire operation came to a focus on Don Jr.
Obviously, there’s the June 9 meeting pitch, which again requires nothing more than recklessness from Don Jr, but which resulted in him receiving a pitch for sanctions relief in exchange for dirt on Hillary. “If it’s what you say I love it especially later in the summer.” Maria Butina similarly tried to pitch Trump’s son.
Don Jr, who joined some of the most rabid Trumpsters in validating the Prigozhin’s trolls, likewise would have represented an overlap between those trolling operations and the ones run by right wing extremists.
At least as interesting is the way Assange repeatedly incorporated Don Jr into his pitch. On September 20, WikiLeaks alerted Don Jr to an anti-Trump campaign and provided a password.
59. On or about September 20, 2016, at approximately 11 :59PM, Target Account 1 sent a private message to a high level individual associated with the Campaign (the “high-level · Campaign individual”). 4 The message stated: “A PAC run anti-Trump site ‘ ‘ is about to launch. The PAC is a recycled pro-Iraq war·PAC. We have guessed the password. It is ‘. See ‘About’ for who is behind it. Any comments?”
Jr passed it onto the campaign, making it clear he had accessed the site. This was the basis of the (totally appropriate) prosecution declination for Jr. only disclosed after years of FOIA challenge by Jason Leopold.
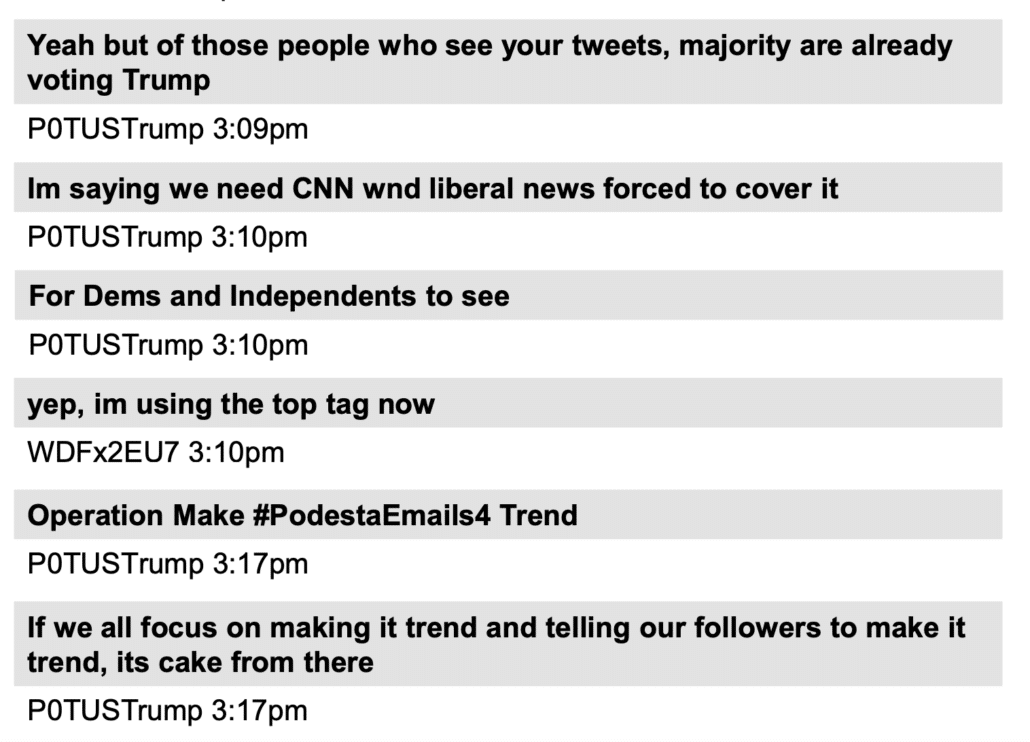
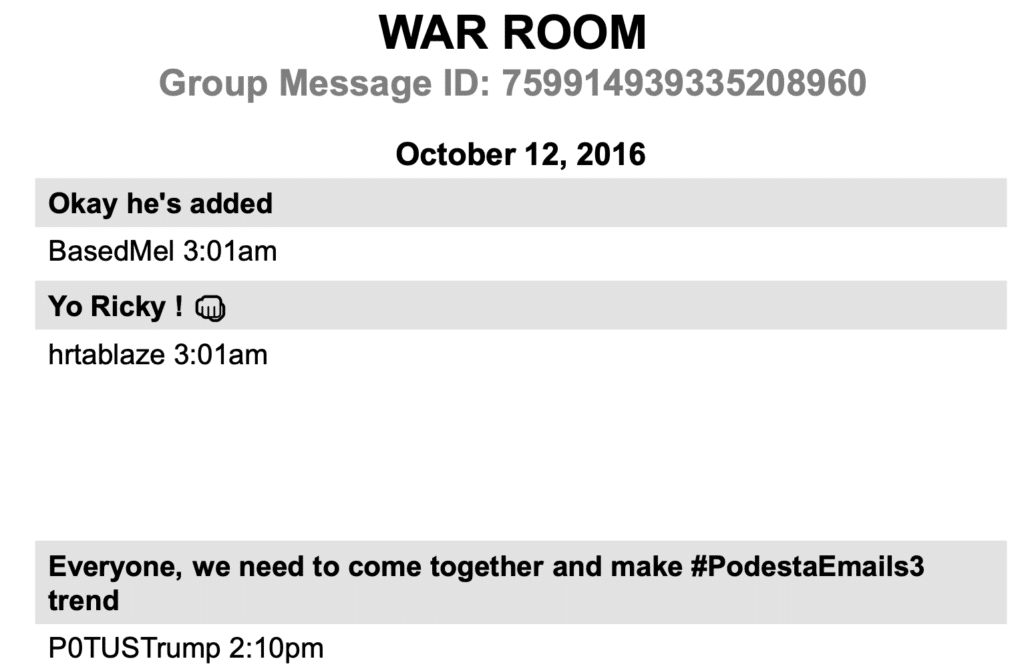
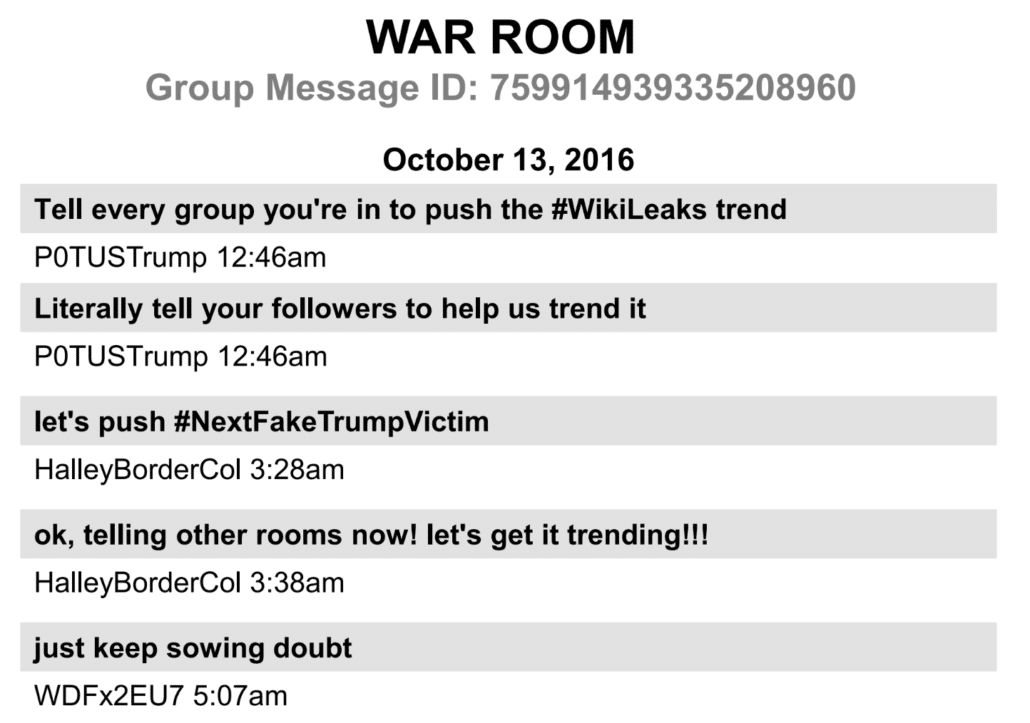
In October, at a time when WikiLeaks was rebuffing Stone’s outreach, WikiLeaks repeatedly suggested Don Jr push out links (and recommend his father do so too). A figure in the Douglass Mackey DM threads by the name of P0TUSTrump kept pushing those links as if in response.
The day of the election, WikiLeaks pushed Don Jr to convince his dad not to concede.
Hi Don; if your father ‘loses’ we think it is much more interesting if he DOES NOT conceed [sic] and spends time CHALLENGING the media and other types of rigging that occurred–as he has implied that he might do. He is also much more likely to keep his base alive and energised this way and if he is going to start a new network, showing how corrupt the old ones are is helpful. The discussion about the rigging can be transformative as it exposes media corruption, primary corruption, PAC corruption etc. We don’t like corruption ither [sic] and our publications are effective at proving that this and other forms of corruption exists.
On December 16, 2016, WikiLeaks pushed Jr to convince his dad to give Assange an Ambassadorship (which would amount to immunity).
Hi Don. Hope you’re doing well! In relation to Mr. Assange: Obama/Clinton placed pressure on Sweden, UK and Australia (his home country) to illicitly go after Mr. Assange. It would be real easy and helpful for your dad to suggest that Australia appoint Assange ambassador to DC “That’s a really smart tough guy and the most famous australian you have! ” or something similar. They won’t do it, but it will send the right signals to Australia, UK + Sweden to start following the law and stop bending it to ingratiate themselves with the Clintons. Background: justice4assange.com
As news of the June 9 meeting broke, WikiLeaks advised Jr to release his emails via WikiLeaks and also advised he reach out to Margaret Kunstler.
When these DMs were released on November 14, 2017, Assange tweeted out a follow-up to the December 2016 one, adding a threat by hashtagging, Vault8, the source code to the CIA files, a single example of which WikiLeaks had just released on November 9, 2017.
I read this as a concerted effort to shift from Stone to Don Jr. Whether Don Jr was actively soliciting this help or not, WikiLeaks made sure to tie Trump’s son to their plight, both publicly and privately.
Whatever else may have gone on between WikiLeaks and the failson, around the time that Mueller’s questions would have alerted Trump that he knew of the pardon pitches, at a time when WikiLeaks’ ties with Russia were under far greater scrutiny, Jr’s buddy Arthur Schwartz went after Cassandra Fairbanks, disabusing her of any hopes Trump would pardon Assange. She ultimately flew off to London to tell him.
None of this says that Don Jr conspired with Russia on the 2016 attack. What is says is that Russian assets systematically viewed him as an idiot that could be and was often useful. And Jr ended up connecting all the through-strands: he bridged the hack-and-leak and social media campaigns with the right wing lists, he reliably got his dad to act on his instructions, and then — as the cost of all this went up — Assange repeatedly targeted Jr as he increased the cost of the hack of the CIA, effectively extorting Jr as he started releasing CIA source code.
Even before I turn to the dossier, viewed this way, the Russian operation in 2016 isn’t so much about getting Trump elected. Rather, it’s about sowing irreparable polarization in the US that deliberately tied Trump’s people to the twin attacks on the Deep State — Shadow Brokers and Vault 7/8.
With little involvement beyond predictable recklessness and venality (and Don Jr’s stupidity), then, Russian assets implicated Trump’s people in attacks on the Deep State that raised the cost of their openness to Russian help in 2016, but which would have made any admissions by Trump all the more costly.
Russia didn’t need cooperation from Trump’s people (though they got it from at least Manafort and Stone and a certain idiot who proved useful). They just needed to make any already improbable conciliation impossible, impossible politically and impossible for a Narcissist like Trump to do. That would practically guarantee that Trump would attack the country to defend himself, his son, his ego.
That, in turn, would make the aftermath of the 2016 attack far more fertile for recruitment, because it would prioritize allegiance to Trump over allegiance to country.