Some Perspective on the Politicized Leak Investigation Targeting Adam Schiff
The NYT reported the other day that DOJ obtained phone records of Adam Schiff, Eric Swalwell, and a bunch of House Intelligence Committee staffers in the guise of what it reports is a leak investigation (though given the specific form of Bill Barr’s prevarications about his knowledge, may have been repackaged as something else when the investigation was resuscitated in 2020).
Prosecutors subpoenaed Apple for data from the accounts of at least two Democrats on the House Intelligence Committee, aides and family members. One was a minor.
All told, the records of at least a dozen people tied to the committee were seized in 2017 and early 2018, including those of Representative Adam B. Schiff of California, then the panel’s top Democrat and now its chairman, according to committee officials and two other people briefed on the inquiry. Representative Eric Swalwell of California said in an interview Thursday night that he had also been notified that his data had subpoenaed.
Prosecutors, under the beleaguered attorney general, Jeff Sessions, were hunting for the sources behind news media reports about contacts between Trump associates and Russia. Ultimately, the data and other evidence did not tie the committee to the leaks, and investigators debated whether they had hit a dead end and some even discussed closing the inquiry.
But William P. Barr revived languishing leak investigations after he became attorney general a year later. He moved a trusted prosecutor from New Jersey with little relevant experience to the main Justice Department to work on the Schiff-related case and about a half-dozen others, according to three people with knowledge of his work who did not want to be identified discussing federal investigations.
The initial collection and especially the subsequent treatment were clearly politicized — and more importantly, stupid, from an investigative standpoint. But, especially because this involves Adam Schiff, some exactitude about what went on really is required.
This is not spying
First, this is not “spying.” If the use of informants to investigate members of the Trump campaign and Hillary Clinton’s Foundation during a political campaign is not spying, if the use of a lawful FISA to conduct both physical and electronic surveillance on recently departed campaign volunteer Carter Page is not spying — and Adam Schiff said they were not, and I agree — then neither is the use of a subpoena to collect the phone records of Democrats who had knowledge of information that subsequently leaked in a fully predicated (and very serious) leak investigation.
This is “just” metadata
According to all reports, the government obtained the iPhone metadata records of 73 phone numbers and 36 email addresses. Apple suggests other tech companies probably got subpoenas, too, which means that some of those email addresses probably weren’t Apple emails.
But it was — as Adam Schiff said many times when defending a program that aspired to collect “all” the phone records in the United States — “just” metadata.
I don’t mean to belittle the impact of that. As I and others argued (against Schiff), metadata is actually profoundly revealing.
But if this is a problem (it is!), then people like Adam Schiff should lead a conversation about whether the standard on collection of metadata — currently, it only needs to be “relevant to” an investigation — is what it should be, as well as the rules imposed on future access to the data once collected prevent abuse.
Apple (and other tech companies) wouldn’t have known this was Adam Schiff
Even people who understand surveillance seem to believe that Apple would have known these requests targeted Adam Schiff in a leak investigation and therefore should have done more to fight it, as if the actual subpoena would be accompanied with an affidavit with shiny flags saying “HPSCI Ranking Member.”
They wouldn’t have. They would have gotten a list of selectors (some of which, by its description, it probably did not service), a description of the crime being investigated (a leak), and a gag order. The one thing that should have triggered closer review from Apple was the number of selectors. But apparently it did not, and once Apple complied, the data was swept up into the FBI’s servers where it presumably remains.
The subpoena was overly broad and not tailored to limit damage to Schiff
All that said, there were aspects of the subpoena that suggest it was written without any consideration for limiting the damage to Congressional equities or reasonable investigative targets. Focusing on these details are important because they distinguish what is really problematic about this (and who is to blame). According to reports, the subpoena:
- Obtained information from a minor, who would have had no access to classified information
- Included a series of year-long gags
- Obtained all the toll records from date of creation
- May have focused exclusively on Democratic members and staffers
It’s conceivable that, after years of investigation, DOJ would have reason to believe someone was laundering leaks through a child. But given how broad this subpoena is, it’s virtually impossible the affidavit included that kind of specific knowledge.
With journalists, DOJ is supposed to use shorter gags–three months. The series of year-long gags suggests that DOJ was trying to hide the existence of these subpoenas not just to hide an investigation, but to delay the political embarrassment of it.
There’s no reason to believe that Adam Schiff leaked a FISA application targeting Carter Page first obtained in 2016 in 2009 (or whenever the Californian lawmaker first set up his Apple account). It’s a physical impossibility. So it is completely unreasonable to imagine that years-old toll records would be “relevant to” a leak investigation predicated off a leak in 2017. Mind you, obtaining all records since the inception of the account is totally normal! It’s what DOJ did, for example, with Antionne Brodnax, a January 6 defendant who got notice of subpoenas served on him, but whose attempt to limit the subpoena failed because those whose records are subpoenaed have no authority to do that. There are two appropriate responses to the unreasonable breadth of this request: both a focus on the failure to use special caution with Congressional targets, but also some discussion about how such broad requests are unreasonable regardless of the target.
Given the number of these selectors, it seems unlikely DOJ did more than ID the people who had access to the leaked information in question. Except if they only obtained selectors for Democrats, it would suggest investigators went into the investigation with the assumption that the leak was political, and that such a political leak would necessarily be partisan. That’s simply not backed by exhibited reality, and if that’s what happened, it should force some scrutiny on who made those assumptions. That’s all the more true given hints that Republicans like Paul Ryan may have tipped Page off that he had been targeted.
These kinds of limiting factors are where the most good can come out of this shit-show, because they would have a real impact and if applied broadly would help not just Schiff.
Barr continued to appoint unqualified prosecutors to do his political dirty work
I think it would be useful to separate the initial records request — after all, the leak of a FISA intercept and the target of a FISA order are virtually unprecedented — from the continued use of the records in 2020, under Billy Barr.
The NYT explains that the initial investigators believed that charges were unlikely, but Barr redoubled efforts in 2020.
As the years wore on, some officials argued in meetings that charges were becoming less realistic, former Justice Department officials said: They lacked strong evidence, and a jury might not care about information reported years earlier.
[snip]
Mr. Barr directed prosecutors to continue investigating, contending that the Justice Department’s National Security Division had allowed the cases to languish, according to three people briefed on the cases. Some cases had nothing to do with leaks about Mr. Trump and involved sensitive national security information, one of the people said. But Mr. Barr’s overall view of leaks led some people in the department to eventually see the inquiries as politically motivated.
[snip]
After the records provided no proof of leaks, prosecutors in the U.S. attorney’s office in Washington discussed ending that piece of their investigation. But Mr. Barr’s decision to bring in an outside prosecutor helped keep the case alive.
[snip]
In February 2020, Mr. Barr placed the prosecutor from New Jersey, Osmar Benvenuto, into the National Security Division. His background was in gang and health care fraud prosecutions.
Barr used this ploy — finding AUSAs who were unqualified to work on a case that others had found no merit to — on at least three different occasions. Every document John Durham’s team submitted in conjunction with the Kevin Clinesmith prosecution, for example, betrayed that investigators running it didn’t understand the scope of the Crossfire Hurricane investigation (and thereby also strongly suggested investigators had no business scrutinizing a counterintelligence investigation at all). The questions that Jeffrey Jensen’s team, appointed by Barr to review the DOJ IG investigation and the John Durham investigation to find conclusions they didn’t draw, asked Bill Barnett betrayed that the gun crimes prosecutors running it didn’t know fuckall about what they were doing (why Barnett answered as he did is another thing, one that DOJ IG should investigate). And now here, he appointed a health care fraud prosecutor to conduct a leak investigation after unbelievably aggressive leak investigators found nothing.
DOJ IG should include all of those investigations in its investigation, because they all reflect Barr’s efforts to force prosecutors to come to conclusions that the evidence did not merit (and because the Jensen investigation, at least, appears to have altered records intentionally).
FBI never deletes evidence
In an attempt to disclaim responsibility for yet more political abuse, Billy Barr issued a very interestingly worded disavowal.
Barr said that while he was attorney general, he was “not aware of any congressman’s records being sought in a leak case.” He added that Trump never encouraged him to zero in on the Democratic lawmakers who reportedly became targets of the former president’s push to unmask leakers of classified information.
There are two parts to this: One, that “while he was attorney general,” Congresspersons’ records were not sought, and two, sought in a leak case. The original subpoena for these records was in February 2018, so not during Barr’s tenure as Attorney General. He doesn’t deny asking for those previously-sought records to be reviewed anew while Attorney General.
But he also limits his disavowal to leak cases. Under Barr’s fervent imagination, however, these investigations may well have morphed into something else, what he may have imagined were political abuse or spying violation cases. DOJ can and often does obtain new legal process for already obtained records (which would be unnecessary anyway for toll records), so it is not outside the realm of possibility that Barr directed his unqualified prosecutor to use those already-seized records to snoop into some other question.
It’s a pity for Adam Schiff that no one in charge of surveillance in Congress imposed better trackability requirements on FBI’s access of its investigative collections.
Both an IG investigation and a Special Counsel are inadequate to this investigation
Lisa Monaco asked Michael Horowitz to investigate this investigation. And that’s fine: he can access the records of the investigation, and the affidavits. He can interview the line prosecutors who were tasked with this investigation.
But he can’t require Barr or Jeff Sessions or any of the other Trump appointees who ordered up this investigation to sit for an interview (he could move quickly and ask John Demers to sit for an interview).
Because of that, a lot of people are asking for a Special Counsel to be appointed. That would be nice, except thus far, there’s no evidence that a crime was committed, so there is no regulatory basis to appoint a Special Counsel. The standard for accessing records is very low, any special treatment accorded journalists or members of Congress are not written into law, and prosecutorial discretion at DOJ is nearly sacrosanct. The scandal is that this may all be entirely legal.
Mind you, there’s good reason to believe there was a crime committed in the Jeffrey Jensen investigation, the same crime (altering documents) that Barr used to predicate the Durham Special Counsel appointment. So maybe people should revisit that?
Luckily, Swalwell and Schiff know some members of Congress who can limit such abuses
If I learned that DOJ engaged in unreasonable surveillance on me [wink], I’d have no recourse, largely because of laws that Adam Schiff has championed for years.
But as it happens, Schiff and Swalwell both know some members of Congress who could pass some laws limiting the ability to do some of the things used against them that affect thousands of Americans investigated by the FBI.
Now that Adam Schiff has discovered, years after we tried to reason with him on this point, that “it’s just metadata” doesn’t fly in this day and age, maybe we can talk about how the FBI should be using metadata given how powerful it has become?
The renewed focus on Schiff’s metadata would have come after Schiff disclosed Nunes’ ties to Rudy Giuliani’s grift
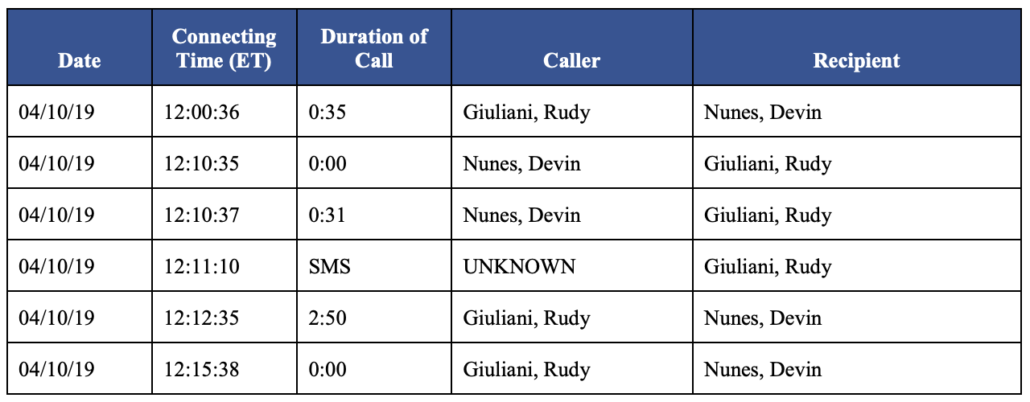
Another factor of timing hasn’t gotten enough attention. In late December, Schiff released the Democrats’ impeachment report. Because Schiff obtained subpoenas (almost certainly targeting Lev Parnas and Rudy Giuliani), he included call records of calls implicating Devin Nunes and his staffer Derek
Over the course of the four days following the April 7 article, phone records show contacts between Mr. Giuliani, Mr. Parnas, Representative Devin Nunes, and Mr. Solomon. Specifically, Mr. Giuliani and Mr. Parnas were in contact with one another, as well as with Mr. Solomon.76 Phone records also show contacts on April 10 between Mr. Giuliani and Rep. Nunes, consisting of three short calls in rapid succession, followed by a text message, and ending with a nearly three minute call.77 Later that same day, Mr. Parnas and Mr. Solomon had a four minute, 39 second call.78
[snip]
On the morning of May 8, Mr. Giuliani called the White House Switchboard and connected for six minutes and 26 seconds with someone at the White House.158 That same day, Mr. Giuliani also connected with Mr. Solomon for almost six minutes, with Mr. Parnas, and with Derek Harvey, a member of Representative Nunes’ staff on the Intelligence Committee.159
69 AT&T Document Production, Bates ATTHPSCI _20190930_00848-ATTHPSCI_20190930_00884. Mr. Parnas also had an aborted call that lasted 5 seconds on April 5, 2019 with an aide to Rep. Devin Nunes on the Intelligence Committee, Derek Harvey. AT&T Document Production, Bates ATTHPSCI_20190930_00876. Call records obtained by the Committees show that Mr. Parnas and Mr. Harvey had connected previously, including a four minute 42 second call on February 1, 2019, a one minute 7 second call on February 4, and a one minute 37 second call on February 7, 2019. AT&T Document Production, Bates ATTHPSCI_20190930_00617, ATTHPSCI_20190930_00630, ATTHPSCI_20190930_00641. As explained later in this Chapter, Rep. Nunes would connect separately by phone on April 10, 11, and 12 with Mr. Parnas and Mr. Giuliani. AT&T Document Production, Bates ATTHPSCI_20190930_00913- ATTHPSCI_20190930_00914; ATTHPSCI_20190930-02125.
76 Specifically, between April 8 and April 11, phone records show the following phone contacts:
- six calls between Mr. Giuliani and Mr. Parnas (longest duration approximately five minutes), AT&T Document Production, Bates ATTHPSCI_20190930-02115-ATTHPSCI_20190930-02131;
- four calls between Mr. Giuliani and Mr. Solomon (all on April 8, longest duration approximately one minute, 30 seconds) AT&T Document Production, Bates ATTHPSCI_20190930-02114- ATTHPSCI_20190930-02115;
- nine calls between Mr. Parnas and Mr. Solomon (longest duration four minutes, 39 seconds) AT&T Document Production, Bates ATTHPSCI_20190930-00885- ATTHPSCI_20190930- 00906; and
- three calls between Mr. Parnas and Ms. Toensing (longest duration approximately six minutes), AT&T Document Production, Bates ATTHPSCI_20190930-00885- ATTHPSCI_20190930- 00905.
77 AT&T Document Production, Bates ATTHPSCI_20190930-02125, ATTHPSCI_20190930-03236.
78 AT&T Document Production, Bates ATTHPSCI_20190930-00902.
[snip]
158 AT&T Document Production, Bates ATTHPSCI_20190930_02313.
159 AT&T Document Production, Bates ATTHPSCI_20190930_02314; ATTHPSCI_20190930_02316; ATTHPSCI_20190930_02318; ATTHPSCI 20190930 01000.
Because Nunes doesn’t understand how phone records work, he — and most other Republicans in Congress — accused Schiff of subpoenaing the record of his colleagues. That’s not what happened. Instead, Nunes and a key staffer got involved in with Rudy’s efforts to solicit dirt from Russian assets and as a result they showed up in Rudy’s phone records.
But it’s the kind of thing that might lead Barr to intensify his focus on Schiff.
The last section of this was an update.





Reminds me of Sen. Dianne Feinstein (D-Calif.) (who never met a surveillance program that she didn’t like) becoming outraged in 2014 when she learned that the CIA had been spying on Senate Intelligence Committee Computers (including hers) and removing documents.
Seems like our hooty-tooty love to spy on the little people, but suddenly become outraged when the state’s survilence machines are pointed at them.
[Welcome back to emptywheel. Please use the same username each time you comment so that community members get to know you. This is your second user name. Thanks. /~Rayne]
Latin Lessons
For four years, Trump operated “in flagrante delicto” and we are still seeking the “corpus delecti”
The IG report should take another four years to complete…. (sigh)
Thank you Dr. Marcy.
Remember this exchange – Kamala Harris grills AG Barr during Senate hearing
https://www.youtube.com/watch?v=M1CjMtRs59g
Where does Rod Rosenstein fit into this equation? He was there with Sessions and Barr.
Where was Rod Rosenstein?
The man who, as acting attorney general offered to ‘wear a wire’ for the Feds and while assistant attorney general, said he would ‘land the plane’?
What are the odds Rosenstein would not tell Barr about this if it didn’t land on his desk from Barr’s?
Given the historical level of “leaks” regardless of the origination, from either the Democratic-oriented or Republican-oriented “appointees”, I find that my political relapse of today, remains the same. Thusly, I advocated that during the presidential campaign, that the next president, should establish a Saturday Morning Bloggers Conference. And as such, each Cabinet Secretary and the assorted “appointees” appear before these bloggers to advocate their public policies as well defend their respective daily activity. Consequently, each 13-week cycle, would become the increasing focus relative to the governmental employees on the receiving end of our taxpayer dollars.
Now, much can be said for and against our credentialed Journalism schematic and yet such political oriented “magnets” such as Apple and Facebook, should be required to immediately disclose their being subjected to any “demand” made by federal government operatives, including the “intelligence” gathering efforts that are charged with investigating the “leaks” that seem to become a daily reality. And yet we in the public sector are intentionally denied such behavior and even to include the actions taken or not taken.
In closing, our public discourse is hampered due to the political shenanigans that manifest on a daily basis and only “bloggers” of political access, remains the only vehicle, readily available to encourage this more seminal discourse.
I smell toast.
Now, does Emptywheel.net, Writ Large, support a Biden-enhanced Bloggers’ Conference?
That is an asinine position and question.
You’re derailing conversation about the topic of this post. Every unrelated comment causes community members on mobile devices to scroll more to get to relevant discussion. Knock it off; post this kind of question at your own site.
There is a key bit left unspoken, as alluded to in the subhed “Luckily, Swalwell and Schiff know some members of Congress who can limit such abuses.”
The fact that DOJ acted with such impunity shows how much congressional leadership has acquiesed in the destruction of its own authority over the years.
A stronger Congress would have meant DOJ would have feared such a move, both with regard to retribution on an institutional level in terms of funding and inquiries, and on a personal level in terms of career advancement for people involved.
There is a sickness that has infected the leadership of Congress, first the GOP and now the Democrats, that sees incidents like this and, more importantly the 1/6 attack, and feels preserving a leisurely schedule is more important than throwing down a gauntlet on day one of an institutional outrage.
They have handed away their ability to fight in terms of staffing, expertise, and funding, and when the inevitable outrage arises, they have no recourse but plead impotence.
Agreed completely. The whole “Democrats look forwards not backwards” position is what got us where we are today.
And because I’m worked up, I’ll just reiterate that when congressional leadership refuse to fight for a level of funding and staffing commeasurate with the executive branch and private entities, “looking forward and not backwards” is the only option left.
It’s not clear to me why Congresscritters deserve less invasion of privacy than the rest of us.
They do not.
They absolutely do not, and I think this piece does a good job of getting the balance right — this is an outrage, and it’s a predictable one.
I think it’s important to add that it’s critical to not let the second facet overwrite the first. There’s a temptation (I’m sure Bmaz doesn’t fall for the tempation) to say let’s let this stand as a lesson to the gatekeepers. That’s nuts.
As Bmaz has pointed out, the fact that huge numbers of regular people suffer from rights abuses doesn’t justify those same abuses against the powerful. Violating due process against someone arrested for pot posession doesn’t make a hypothetical illegal search against some Trump flunky OK. It’s certainly fair game for some schadenfreude, but that’s it.
Which is what also launches my unhappiness with the term “congresscritters” which is even dumber than the way some people use names like “Cheetolini” to refer to Trump. Schiff has faults, some of them major. But he’s also a serious, important player and lumping him together under the diminutive “congresscritter” as if he was someone like Gohmert is a genuine problem.
We need a strong Congress as a counterbalance to presidents and the courts. Succumbing to cheesy stereotyping makes things worse.
BobCon, I certainly agree with Bmaz’s statement that “they do not” deserve greater privacy than you or I. My statement was akin to a modest proposal. Regarding Congresscritters; its a term used frequently here as you are no doubt aware. I use it to indicate a mild disrepsect that is richly deservered by many, if not most, Congressciritters (and also to avoid the sexist term Congressmen or the, ugly to my ear, term Congressperson). Regarding cheesy stereotypes I would refer you to some lyrics from “Avenue Q”. I have enjoyed many of your comments, but not particularly this one. Be well.
I was ruminating on this same idea of criminal exposure to the law and Constitutional rights, although the flavors were mostly generated by OLC’s unchallenged cud that a President cannot be indicted.
I’m highly doubtful that this post supports your position. If it does, the sea change would have tsunamis rolling inland for hundreds of miles along every coast.
The suggestions offered are made to reduce the level of unwarranted investigations into ALL Americans, not just those who hold political office.
The Speech or Debate Clause is an example of why higher protections are required for Congress vs. the general public. See this article by the Congressional Research Service
“The Constitution’s Speech or Debate Clause(Clause)represents a key pillar in the American separation of powers.The Clause, which derives its form from the language of the English Bill of Rights and has deep roots in the historic struggles between King and Parliament,serves chiefly to protect the independence, integrity, and effectiveness of the legislative branch by barring executive or judicial intrusions into the protected sphere of the legislative process.
…
While there appears to be much about the Clause that is unclear, it is well established that the Clause seeks to secure the independence of legislators by providing Members with immunity from criminal prosecutions or civil suits that stem from acts taken within the legislative sphere.https://fas.org/sgp/crs/misc/R45043.pdf”
There has to be a wide berth given to Congress for it to operate. For example, if a congressman discussed information with a reporter with the understanding that the reporter would help unearth other information that could reveal official wrongdoing, is that within Speech or Debate? I don’t know, but I certainly hope so.
We, or at least I, still don’t know a lot about the leak investigation. However, I think there are clear indications that it was based on inadequate evidence, that the conduct it intended to investigate was not of sufficient severity to warrant an investigation as intrusive as this one, and that the early findings were so weak that only a partisan as determined as Bill Barr would continue it. I also think that the fact that the former president seemed to be directing the DoJ to conduct investigations is impeachable. Whether laws were broken in the process, I don’t know. But these sorts of activities are wrongdoing in the larger sense, and I would hope that the laws protect Congress as they try to expose it, even if the laws do not protect us.
Wait a minute. Maybe stuff has changed since I left the telecom industry. I’m trying to understand.
Call Detail Records (metadata) are created by the originating Telecom exchange (where you made the call) — and in the case of cell phones in the US, by the terminating exchange because you have to be billed for the minutes even receiving a call (this is not normal in the rest of the world). If your call goes entirely over IP using some app, you get billed by your telecom provider for your data consumption unless you’re on free WiFi. This is info kept by your Telecom provider, not Apple (or Samsung or whoever).
Telecom providers have NO reason to keep this stuff beyond the billing period and the period required by regulators for you to challenge your bill, which used to be about 90 days. If they’re keeping it for several years for law enforcement purposes, what law requires them to do this? If they’re dumping it to the NSA, what law requires this?
Your call record is recorded on your iPhone and the iCloud but not indefinitely and only if you set it up; I regularly wipe my call record so the iCloud could deliver nothing to the FBI. The same would apply to an IP-only app, unless the app provider is keeping call records for the NSA (what law?)
Telcos keep text messages for a few days to ensure delivery, then dump them. iCloud keeps my text messages if I set it up but I can wipe them.
If I were a White House staffer leaking information to the press, I would be careful to wipe the call and text records.
So how is the FBI able to get years-old or even months-old call records??????? Or did I misunderstand and this was a real-time data collection operation?
https://en.wikipedia.org/wiki/Data_retention#:~:text=It%20will%20require%20telecommunication%20providers%20and%20ISPs%20to,are%20allowed%20to%20access%20metadata%2C%20including%20private%20agencies.
Scroll down to the section about the United States. Some opine that this is just the part we know about.
Thanks! This means they don’t have to subpoena AT&T because the NSA already has the CDRs.
About the famous Room 641A: what 2003? I’d heard about that stuff in the 1970s, inside AT&T, when we’d digitized most of the trunks. What I heard is that the NSA “listened” on the international trunks at the NY gateway and was able to filter certain words in conversations, and then record (intercept) he conversations.
We’re likely going to learn that this was something like a Community of Interest subpoena for the subscriber ID and toll records of the contacts of the ultimate suspect, on whose phone records FBI probably did get a CDRs.
Ha, worked on one of those machines that had Universal Voice recognition circa 1979. They kept that function under wraps for another decade. Wasn’t into the guts, but was told flat-out what it did. (Techies weren’t very good about classified technology secrets back then.)
Technically, Apple IDs are often the email addresses of Apple iPhone and email users from other service provider, often the ISP a users has been with for sometime. Another popular Apple ID will be a gmail account as well. What I mean is that if one’s email account is:
[email protected]
or
[email protected]
Then the Apple ID account itself will be that same email address, as the account text string, from either google or ATT, for example. Ugh. And, yep, this Apple ID ‘scheme’ creates plenty of user confusion that IT types have to straighten out when a user gets some email (real or fake) that tells them that they need to reset their password and then they become confused as to whether they’re supposed to do it for their Apple ID account of the original email account elsewhere. In fact, I have many dollars from helping confused users figure out what the F is going on when they start trying to change a password and end up having their email account (elsewhere) and their Apple ID account (at Apple) both locked down because of so many failed attempts to access the respective accounts.
But, to the point, Apple will often have all sorts of metadata about at least one other company (and often several) as to email addresses and accounts at other companies. For instance, one can register several such accounts to receive Apple email through Apple’s Mail app on their phone. This registration does not happen in the app but through the OS itself via system preference panels… sooo, yep, Apple will >know for sure< that when they turn over certain info that has a clear AppleID account name on it that the government will instantly know that there is another email account at a different company that the target of the data collection has. The reverse is also true—Apple could be asked to look for AppleID account information, by the AppleID account string, that matches a different organization or domains email address.
So I’m locked out of my Apple email, because Apple doesn’t recognize the ID I just reset.
Where should I go for help now–Apple or DOJ? (Since it sounds like the latter must know.)
Why does Apple have it’s users phone call metadata? I understand why your phone company would have it but I can’t think of any legitimate reason for Apple to have it. If you aren’t using Apples email servers they shouldn’t have you email metadata ether. While Congress is looking at this and the anti-trust issues maybe they should ask?