“They Were Trying to Boot the Machine:” John Paul Mac Isaac Claims the FBI Really WERE That Incompetent
If you can believe John Paul Mac Isaac, the FBI did some incredibly bone-headed things after they obtained Hunter Biden’s laptop in December 2019. As he describes it in his book (which I read recently while stuck in a hospital awaiting foot surgery), on the very same day the FBI collected the laptop purported to belong to Hunter Biden, on December 9, 2019, someone named “Matt” told Mac Isaac they had tried to boot it up.
“Hi, my name is Matt,” said a voice I didn’t recognize. “I work with Agent DeMeo and Agent Wilson. Do you have a second? I have some questions about accessing the laptop.”
Confused, I responded, “Sure, what’s going on?”
“Did the laptop come with any cables or a charger? How can I connect the drive to a PC? When I plug it in, it wants to format the drive,” Matt said.
“PCs can’t natively read Mac-formatted disks. You will only be able to access the drive from another Mac.”
This is fairly common knowledge among most computer users, and I was surprised that any kind of tech person wouldn’t know it.
“Sadly, Hunter never left the charger or any other cables,” I went on. “I have a charger and everything you need back at the shop. You guys are welcome to it.”
I was feeling really uncomfortable. This Matt guy definitely didn’t seem to have the training or resources to be performing a forensic evaluation of the laptop. Hadn’t the whole reason for taking the laptop been to get it to a lab for proper evaluation and dissemination?
“Tell him we’re OK and we won’t need to go back to his shop,” Agent DeMeo said in the background. “We’ll call you back if we need to,” Matt said before hanging up.
[snip]
“Hi, it’s Matt again. So, we have a power supply and a USB-C cable, but when we boot up, I can’t get the mouse or keyboard to work.”
I couldn’t believe it—they were trying to boot the machine!
“The keyboard and trackpad were disconnected due to liquid damage. If you have a USB-C–to–USB-A adaptor, you should be able to use any USB keyboard or mouse,” I said. He related this to Agent DeMeo and quickly hung up.
Matt called yet again about an hour later.
“So this thing won’t stay on when it’s unplugged. Does the battery work?”
I explained that he needed to plug in the laptop and that once it turned on, the battery would start charging. I could sense his stress and his embarrassment at having to call repeatedly for help. [my emphasis]
To be sure, you can’t believe Mac Isaac.
His own story is riddled with questionable details and important discrepancies.
The most important discrepancy is his description of the laptop he turned over to the FBI, which he describes as a 2016 Mac, not the 2018 Mac identified by serial number.
I moved on to the last Mac, a thirteen-inch 2016 MacBook Pro. The drive was soldered onto the logic board. This one powered on but then would shut down. I suspected that there was a short in the keyboard or trackpad, and if I took it apart, I could at least get it to boot and possibly recover the data.
As I understand it, Mac Isaac’s claims that the hard drive was soldered onto the logic board is also inconsistent with the known details of the laptop shared with the FBI.
But there are important other discrepancies between the story Mac Isaac tells and the one the government tells. In his timeline of his interactions with the FBI, Mac Isaac gets the date for the actual handoff, December 9, correct, but other dates he uses differ from those that show up in Gary Shapley’s timeline. For example:
- Mac Isaac says that Agent Josh Wilson (who is mentioned in Shapley’s notes) reached out to his father on November 1; Shapley’s notes say that happened on November 3
- Mac Isaac says that Wilson called him on November 4; Shapley’s notes say that happened on November 6
- Mac Isaac says that Wilson came to his home on November 19; Shapley’s notes say that happened on November 7
These discrepancies aren’t all that important, legally. But Mac Isaac’s dates seem tailored to the impeachment proceedings going on in the same period, and so to laying a foundation for sharing the laptop with Rudy Giuliani.
A far more important set of discrepancies pertain to Mac Isaac’s description of what happened on December 9, 2019.
The blind computer repairman first describes that the second agent, Agent Mike DeMeo, called him to ask for the device identifiers that morning, before coming to the shop to pick up the device.
Agent DeMeo called around 9:30 a.m. It caught me a little off guard. The only other time we had communicated was shortly after our meeting almost three weeks earlier. He had asked me then to text him the timeline of my interaction with Hunter. I figured that he wanted something in writing showing the chain of custody—or it was an effort to trap me into writing something that could be twisted into a charge of lying to the FBI.
This time, he asked me to text him the model and serial number of the external drive and laptop. I explained that I hadn’t made it to the shop yet. “I need this information before we head over,” he insisted. “It’s important.”
“Give me thirty-five minutes,” I responded, then hung up. I finished getting ready and headed to the shop. After texting the numbers to Agent DeMeo, I waited in the shop with the blinds closed and the lights out, so as not to announce that the store was open. [my emphasis]
Shapley described that the FBI obtained and confirmed the device identifier before they ever met Mac Isaac, on November 6 (though perhaps Mac Isaac only referred to other identifiers needed for the subpoena).
Nevertheless, this discrepancy is important for a number of reasons, not least that if the FBI looked at all closely at the returns on a subscriber subpoena to Apple, it should have raised significant alarm that someone was trying to hack Hunter Biden. But if they didn’t obtain this information until the day they obtained the laptop, then they couldn’t have reviewed the subscriber data very closely in advance. That negligence might, in turn, amount to negligence in missing clear signs that the then former VP’s son was being hacked.
As Mac Isaac describes it, it was not until Agents arrived at his shop that they told him they were going to seize the laptop with a subpoena rather than imaging the laptop there at the shop.
Both agents arrived at my door about a half hour late. “Where’s the tech?” I asked, holding the door open.
“We have a change of plans,” Agent Wilson responded. “Can we go in the back?”
I led the agents to the back, and Agent Wilson placed his bag on the workbench. “
I have a subpoena here to collect the laptop, the drive, and all paperwork associated with the equipment,” he said, pulling out a collection of very formal and important-looking paperwork. “I’ll need you to sign it.”
When Mac Issac asked why they had changed their plan, he claims, lead Agent Josh Wilson deferred to Agent Mike DeMeo, who told him that they were taking the laptop back to a lab to image.
“You guys scared the shit out of me!” I exclaimed. “So why the change of plans? Don’t get me wrong; I’m grateful that you’re taking this stuff out of my shop.”
Agent Wilson looked over at Agent DeMeo, who was buried in his clipboard. “Ah, Mike?” he said. Agent DeMeo paused his writing and said, “We have a lab that takes these things and is better equipped than our field tech.”
Mac Isaac also claims that at that same meeting, DeMeo told him only to contact him, not Wilson.
“Tell them you keep abandoned equipment offsite, like a warehouse location,” Agent DeMeo answered, taking over. “Tell them it will take a day for you to check and they should call back the next day. Then immediately text me at my cell number. From now on, only communicate through my cell number. Not Agent Wilson, just me. We need to avoid communicating through, ah, normal channels. I’m sure you can understand. Text me and we will get the equipment back to you and deal with the situation.”
This communication works the opposite of the way you’d expect. Often, second agents are asked to take the stand, so you’d want them to have a clean digital trail. Here, the lead agent, Agent Wilson, was protecting his communications, whereas the second agent was not.
And then, as Mac Isaac tells it, that very same day, someone else, “Matt,” called using DeMeo’s phone, asking really embarrassing questions about how to access the laptop.
The claim that someone at the FBI was trying to boot up the laptop is alarming enough — though as I noted in July, there is some corroboration for the claim in Gary Shapley’s notes.
FBI determined in order to do a full forensic review a replacement laptop had to be purchased so the hard drive could be installed, booted and imaged.
[snip]
Josh Wilson stated that (while laughing) so whoever [people wanting to review the laptop] are they are going to have to buy a laptop to put the hard drive so they can read it.
Where Mac Isaac’s claims are totally inconsistent with the FBI claims, in a way that would cause grave legal problems for the FBI, is the date: Mac Isaac claims that the FBI was trying to boot up the laptop that same day, on December 9.
According to Gary Shapley’s notes, the FBI didn’t have approval to even get a warrant on December 9, much less have a signed warrant itself.
The FBI didn’t have a warrant to access the “Hunter Biden” “laptop” until December 13.
And yet, if you can believe Mac Isaac, the FBI was already trying to boot it up, perhaps irreparably altering its contents, three days before they got a warrant.
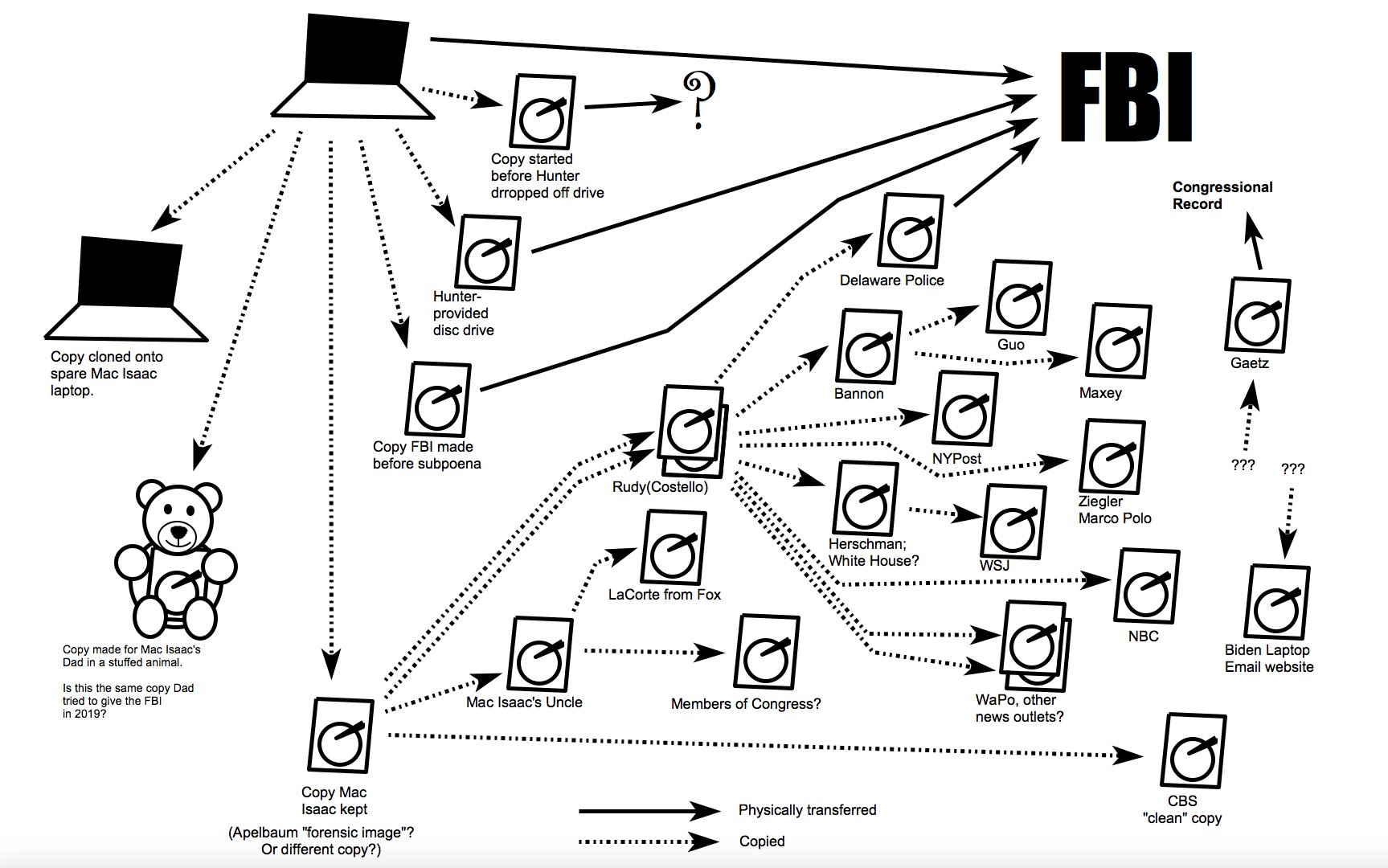
Featured image showing known dissemination of the “Hunter Biden” “laptop” by Thomas Fine.





The story as presented by Mac Isaac reads as if these weren’t real FBI agents but folks from Project Veritas.
That’s what I was thinking. What kind of FBI agent introduces themself so informally as just “Matt?” without having some sort of prior introduction – doesn’t pass the sniff test, but then again, very little about Mac Isaac does.
This entire story has so many things that do not make any sense, but regarding the FBI not having competency with dealing with computers and software, this aligns with personal experience. My company does DoD research and we had a break in on one of our servers a few years back. I called the FBI to report it.
Two agents arrived to investigate. The software developer who discovered the break in was interviewed by the agents. It was obvious that they did not know how to ask relevant questions. While my developer was being interviewed by them in his office, he was working on his computer and within about 15 minutes found the IP address of the computer that the break in was performed from.
The agents were stunned and confused. At first, they asked what an IP address was, and then how it could be discovered. Then they tired to hire my developer to work for the FBI. He laughed and told them that they could not afford his services.
Your observations are absolutely contrary to what I know about the FBI and its handling of assets such as these. I might see this a possibility 20 years ago but not in this period of information warfare. Anecdotal accounts are just those – someone’s recountings.
Isn’t your response anecdotal?
Heh. you’re the naive one if you believe anything an agent is portraying to you, since their “gee whiz” attitude is just as much about determining what you know and if you may have even been involved. They know what they need to know to do what they need to do.
I had a similar experience when I submitted a tip to the FBI regarding some suspicious activity regarding facebook accounts and potential russian espionage activity in a high profile group. I was surprised when I got a call from an agent who debriefed me and asked how I knew or deduced certain things, and she also complimented my investigative and technical skills and asked if I ever considered applying at the bureau.
Unlike mac isaac or your developer, im aware that im not “smarter than the bureau”, and any such appearance is an intentional part of investigative technique. Especially in counter-intel – they are just as curious about what *I’m up to* as what this purported adversary might be up to, and what I might deduce about what they know.
Watch “Reality” about Reality Winner.
[Welcome to emptywheel. Please choose and use a unique username with a minimum of 8 letters. We are moving to a new minimum standard to support community security. Thanks. /~Rayne]
Thanks to Joni Mitchell and late great Jaco Pastorious and Michael Brecker for The Dry Cleaner from Des Moines live performance
https://youtu.be/ZbPorrmjWHM?si=D5dXzwD8E9w1iJcK
The Dry Cleaner who Purloined
I’m about to commit a crime
I’m stalking the scam that’s not
I keep hearing lies all around me
Pinging me but finding Jack squat
They keep you tantalized
They keep you reaching for your wallet
Griftin fools paradise
Blind dude fixes MACs for some coin
He said he can’t identify
A cat who dropped of some MACs
Well, he must have had a genie in a lamp
Cause the New York Post and Rudy Giuliani
Started ringing bells
Nothing to it!
They got the emails
The Dick Picks
The I Cloud
The texts
But they lost their search for proof
Then got the “lawyer” to do it
Costello co-defendant in the suit
You’re bad luck
Is you suck
When you’re the Donald’s lackey you end up never making money
Love it! Great song too.
To the tune of Mack the Knife:
Mac the Naif
I had never seen that clip, thank you for that.
And your lyrics are wonderful.
About as wonderful as a cold dish, of pistachio ice cream or a suit from Tish, going to summary judgement.
SunZoomSpark nailed it, but in passing I would also draw folks’ attention to Joni’s brilliant lyrics set to Mingus’ music. Worth a click (not going to copy/paste the whole thing).
Another fine example is her poignant rendition of Goodbye Pork Pie Hat. , Mingus’ homage to tenor sax icon Lester “Prez” Young.
Yes to that, punaise. Joni’s love and understanding for jazz shine in that one. I heard it in Hissing of Summer Lawns, still my favorite of her albums, which came out when I was teaching myself alto sax (with no previous wind instrument experience. I wanted to be Charlie Parker.) I played along with it relentlessly with a t-shirt stuffed down my horn to absorb as much of my unmodulated noise as possible. Neighbors did not love it.
That’s a great story. I’ve never attempted any wind instruments – must be hard!
Personal favorite, in my pantheon of desert island albums: Hejira.
And only Joni could write this gem (from Talk to Me on the album Don Juan’s Reckless Daughter):
Hejira & Hissing of Summer Lawns are my favorite Joni albums. I practically wore through the vinyl on both of them.
Hejira was my fave until Hissing displaced it.
I’ll never forget something Joni wrote in the liner notes of one of her first albums. She thanked her high school English teacher because “He taught me to love words.”
punaise, that verse you quoted made me think of it. She loves words and her genius is the interface between language and music.
Guess I should revisit Hissing. For me it was a gateway drug, a quick stopover on the way to the beautifully melancholic Hejira.
Love that the estimable Joni Mitchell saw fit to “cover” Yeats’s poem with “Slouching Toward Bethlehem.” Ever more relevant to now.
Hearts and flowers! That was awesome!
The live version of Shadows & Light is the bomb. Grea
Marcy, does Mac Isaac say in the book why he contacted the FBI about the laptop? I have read some NY Post articles where he claims to have observed evidence of possible financial crimes and that is why he got his father involved to reach out to the FBI. That strikes me odd. Much more so than if he was just reporting some kind of porn or drug use.
It would be valuable to know if Mac Isaac, and the responding agents, were using Burisma and the China accusations from Schweizer’s book as their predicate to grab the laptop.
Because I have yet to see any email evidence of influence peddling, money laundering, bribery, or FARA violations from the contents of the laptop. I’d like to know what Mac Isaac considered tip worthy. It looks like innocent business communication unless some far-fetched innuendo is added.
It was this email, conveniently marked with a purple dot. And his focus was exclusively Ukraine, which is not at all suspicious given the efforts to frame Hunter w/Burisma.
“ All that money and this asshole couldn’t spring for a backup drive!,”
Why would Hunter need a backup drive when he was already paying Apple a lot of money a year for the extra iCloud space for backups?
That’s the other thing that bugs me about this whole story. Why would Hunter pay this guy for data recovery that already exists on Apple hardware?
Ding ding ding
We have a winner!
It is impossible that Hunter Biden’s devices could provide any proof of Schweizer’s fictional stories which were published in March 2018.
Just speculation on my part, but Dr Wheer’s analysis seems to point at FBI agents who are “Friends of Rudy” doing some freelancing and pretending that they obtained the “laptop” by legal or official means.
Steve Bannon collaborated with Schweizer on the “Secret Empires” book, and he is one of the people who got his copy of the hard drive from Rudy, and Rudy shopped all of Schweizer’s stories to Russian intelligence.
Once the real story is exposed (and it will be)
We have fraud and computer crimes for everyone!
Except Schweizer. He is just a professional liar who needs to suffer the consequences of that for the rest of his life. As in “oh look, there’s the liar who can’t be trusted in any way”
[Moderator’s note: Please allow time for moderation of your comments as they may have been held up by auto-moderation by keywords or other security triggers. Your duplicate comment has been deleted. /~Rayne]
Gonna go back and read your whole post. Hope you didn’t have a Lisfranc injury as I did a 16 months ago. Any foot surgery tho has a long recovery. Wishing your foot well.
Yes, best wishes EW. I have a more modest problem: clomping around in a boot due to a torn plantar fascia. Good times!
Hobbled goblins!
“It’s just a flesh wound. I can still fight!”
Aye.
Ouch! Hope you feel better soon!
Thanks, harpie. Had to cancel a camping (OK, glamping) trip with some best buds. I was reassured, though, as my best defense strategy for avoiding critter attacks was moot: :”You don’t have to run faster than the mountain lion, just faster than the slowest person in your group”.
Ohhh….that is fine advice.
Great decision! Live to glamp another day!
When glamping, couldn’t you just lock the door so the critter can’t get in?
Glamping-light, I guess: 4 wheel drive access into National Forest land in the Sierra, tents get slept in, good day hikes, a full camp kitchen, hammocks, live amplified music and surround sound playlists, a variety of consumables… Our campsite needs are rather specific (to avoid bothering others).
Adding my wishes for a speedy recovery, Marcy!
It is, indeed, lis franc. Also my first experience with Irish healthcare.
I go to the urgent clinic. The Cuban doctor says, “lis franc, go to University of Limerick Hospital Emergency Department, they’ll do a CT scan, and admit you for surgery right away.” Instead, I decided to try a hospital in Galway (I was already headed there), since UL is notorious for the worst ED wait times in Ireland. Galway sent me back to UL, They do another x-ray, say it’s not lis franc, and send me home with an appointment 10 days later.
I come to the appointment and THAT doctor, right away, says it’s lis franc. He tries to admit me to the hospital right away, so I can get a CT more quickly. But there are no beds so I have to go wait in ED for hours and hours, where I eventually get a CT, which shows — sure enough — lis franc.
To be fair, they did this to make sure I got in the surgery line for the one doctor who does lis franc surgery, so I got the surgery the next day. But, yeah, it’s gonna be a while.
This site is so informative. I now know all I ever intended about the anatomy of the foot. I’m gonna buy better shoes.
https://orthoinfo.aaos.org/en/diseases–conditions/lisfranc-midfoot-injury/
Thank you for that link, GlennDexter. It really is superb, and the pictures should scare anyone with feet.
I hope you recover smoothly, EW.
I learn new things here all the time, but did not expect today’s new thing to be a foot injury! Descending from a long line of hobbled women (bunions on both sides, plantar fasciitis, etc.), I thought I’d heard them all. Obviously not.
And how appropriate for a comparative literature major to get the one named lis franc.
I was looking for a foot comment . . . Hope you heal quickly. Thanks for keeping on top of all the phuckery. They are trying awfully hard to come up with something to get at Joe. Shame they are using his son. The “party” of Reagan is done.
This whole thing where the idea is that the F.B.I. accepts hardware and raw data from a visually disabled computer repairman, who just took them from his customer after 30 (?) days, & then gets a search warrant because a tax evasion case is underway is to my ears bizarre. What was the stated basis of this search warrant I wonder? Wouldn’t there have had to have been some predicated investigation that would allow such an intrusion?
Does the FBI not know computer forensics? The drive should have come out and mirrored at the bit level and anything should be done to only the copy. Booting the original drive changes it and compromises any value it had as evidence. That’s just nuts.
[Welcome back to emptywheel. Please choose and use a unique username with a minimum of 8 letters. We are moving to a new minimum standard to support community security. Thanks. /~Rayne]
I have no idea what that means. And thinking about it, I don’t think Isaac knew either: it just makes no sense. The only thing that could be done forensically would have to be done with the original drive in the machine. The closest one can get is doing a bit-wise (literally 1 bit at a time) low level copy, but even that does not guarantee getting recoverable over-writes from the original.
That Isaac says Hunter’s machine was a 2016 seems bizarre at this point, given all the attention given to it have been reported as a 2018 model. This suggests really sloppy incompetence, even before trying to address all the nefarious activities.
Or really horrible editing of the book manuscript. Amazon lists the publisher as “Liberatio Protocol.” *eyeroll*
The dating of MacBook Pro 13inch laptops is not totally intuitive. I have a MBPro 13 that is considered a mid-2012 model. It was manufactured in 2016. A site called mactracker.ca has good information on this subject.
Thanks, I didn’t know that. I looked there, did not see explanation for what you describe. I never encountered anything like that in years I used MB 13’s in my business.
The more important thing IMO was not years of HB’s Macs: it is apparent that there was (at least) 2 HB Macbooks floating around. Can’t help wondering if one of those was used for hacks, then propagate changes to HB’s other devices.
As others have pointed out, whoever the hackers were and whoever else in FBI was directing handling of these machines, it was a very wobbly, unprofessional effort. Given what we know, there was never an effort to even acknowledge the hacks much less track them down.
Something(s) are wrong. I suspect Lowell’s legal actions will start poking some holes in this thing.
In order to see all the mactracker.ca information you will need to download the Mactracker app on either a Mac or an iPhone. The Mac app is available on mactracker.ca, and also through the Mac App Store, where the app gets 4.9 out of 5 stars.
ahhh, thanks.
The Mac Isaac 💻, is a 2017 model with a removable hard drive, per the serial number on the subpoena.
Mac Isaac claims it’s a 2016 model with a soldered in hard drive.
That detail throws Mac Isaac’s story apart. His whole claim is that because the hard drive was soldered, a repair he isn’t skilled to deal with, that he was forced to drag and 💧 to another drive, open files and *accidentally* noticed the evidence of Hunter’s misdeeds. if he removes the hard drive for the data recovery this story never g the time off the ground.
Is it possible that Mac Isaac and others are following a script and someone messed up their line, blundered the op by going to a Mac store and thinking all Macs are the same what the hell and bought the wrong one to plant hacked data?
Please avoid emojis. They’re not searchable let alone viewable by all readers’ devices.
Gotcha. I’m on a phone, autocorrect keeps putting in the emojis
LOL it’s not your phone, it’s your habit. I never use emojis in comments as replacement for words, only sparingly as emotional punctuation at the end of text messages. My phone won’t offer emojis for words because of this practice.
Oh brother, lol. a habit huh? I type emojis all the time to replace text, huh? How many of my past comments have emojis?
I’d ask what made you think you could do that *now* but I don’t care. Just knock it the fuck off. You should have stopped as soon as the first emoji popped up. Look around here, nobody else is doing that regardless of device they’re using.
NOBODY.
It’s really interesting the claims made in 2020 versus 2022. It’s like they got reckless by 2022, and never bothered to check their story.
The fact that the average FBI field agent doesn’t know anything about computers isn’t all that surprising. The wildly varying capabilities of their “cyber” units (see various previous posts that Marcy has done over the last [checks notes] 15 or so years ago) concerns me greatly.
On the other hand, handling seized property in accordance with constitutional, legal, and regulatory requirements is a core competency for any FBI agent. This seems like something Hunter Biden’s legal team might consider worth following up on.
Exactly this. I don’t expect a single random FBI agent to exhibit any more talent with navigating damaged Apple hardware any more than I expect a single random FBI agent to be familiar with replacing the radiator on a Hyundai.
I do expect multiple FBI agents working on concert to correctly address chain of custody and other law enforcement procedures at a much higher level, to where if one agent involved in the process makes or is about to make a mistake, co-workers are going to catch and correct (and certainly not sustain) the errors.
Conversely, I absolutely do not expect Mac Isaac to have perfect recall such that he can reconstruct the dialog of a conversation that happened years prior… and while it is sometimes the business of historians and documentarians to dramatize events and conversations for which they were not themselves present, it’s kinda squirrely to pass off a personal dramatization of your own reconstructed memories as a verbatim account.
While it is certainly within the range of expected behavior for some corner shop PC nerd to flex his technical superiority by embarrassing government officials in his book, it does beg the question about whether his account is engineered to shift any personal culpability of how he handled the devices.
And… getting electronic equipment needing forensic investigation to a lab actually capable of doing just that.
Exactly. The average special agent has a short list of competencies they are required to have down pat. Forensic computing is not among them. But FBI HQ in Quantico should have those skills in abundance.
Oh, and I haven’t even shared the BEST story.
C’mon, why would you do that?
What, they couldn’t get a Genius Bar appointment?
This illegal confiscation sounds like a rogue operation, to my unlawyerly mind. And probably a pattern for the political retribution tfg is promising, following his reinstatement by a compromised Supreme Court.
Also – the point about a “filter protocol” – that might make sense for the purposes of a tax evasion case. That means using certain search terms and maybe other metadata restrictions like doc type or extension to drill down to only what is most relevant. That filter should therefore isolate what is at issue for the case and anything outside of it is quite plainly ***not***. And that might also be the situation for the acquisition of iCloud data by search warrant as well if a similar process was followed and again IMO it should have been.
To me this reads like Agents Wilson and DeMeo were doing some ‘off the books’ forensic research on this laptop and had no fucking clue what they were doing. Whoever Matt is, he’s most definitely not a digital forensic examiner for the FBI.
When it comes to the alleged incompetence of the real or imagined Matt, Wilson, and DeMeo, Woody Allen on discussing the lack of brainpower of his lead character in Take the Money and Run who played the cello in a marching band – “He had no conception of the instrument. He was blowing into it.”
“… it is generally assumed the cello is a phallic symbol, I mean with the grasp and the lowest structural forms certainly a feminine, if anything motherly. In fact, the utilization of the bow I would imagine is the sublimation of the stroking the torso. So between the grasping, the phallus and the stroking of the torso, would create, I would imagine great conflict”
Again, I don’t think Mac Isaac is reliable, so I don’t make too much of this.
But if there’s a rogue operation–possible if you consider the Attorney General was personally interested–then it would exclude Wilson. Thus the contact through DeMeo’s phone, and Wilson’s deferral to why they weren’t just imaging the device (without yet obtaining a warrant, AFAWK) in the shop.
This… makes sense.
OT: Cannon finally just scheduled Garcia hearings.
https://www.msn.com/en-us/news/politics/mar-a-lago-judge-blasted-for-late-trial-date-cannon-is-slow-walking-this-case-to-benefit-trump/ar-AA1hiJa8
DOJ brought the atty conflict issue up in their motion for Garcia ~2.5 months ago. “Slow walking” doesn’t quite do it justice, when characterizing Cannon’s de-facto defense work.
Lol, 2.5 months is not slow at all on a federal case.
For a Garcia hearing specifically? I keep hearing, from normally pretty reliable sources, that it is, but it can be difficult for us non-lawyers to filter out the bullshit.
No, not specifically. Federal judges are like Forest Gump’s box of chocolates, you just never know. Granted it was a civil case, but I once waited a year and a half for a decision after oral argument. Even on criminal cases, they often take 60-90 days. Or they can move quickly. You just never know.
Does Cannon get scheduling priority in her courthouse for this NatSec-disaster mitigation case? And what kind of caseload is she carrying over and above that one?
Has she had any colloquy with Pryor about this, I wonder?
A Garcia inquest isn’t something that requires massive precedent inquiries, or any but the basic fact finding and remand-setup argument about how putting blindfolds on witless pawns will take care of everything.
This is about defendants’ protection of rights to counsel (In Real Time), something that should elevate the process above all others.
No. Federal judges make their own schedules. But criminal is a higher priority than civil.
How much advantage is there to Trump in having this trial slow-walked, now that others have apparently “jumped ahead” of it?
Back when this was the first case going to trial, and others were gonna be in line behind it, slow-walking gave him the chance to put them all off until after the 2024 election. But now that the DC case is scheduled for March, does he gain much by having the Florida case come dragging slowly behind?
And actually, if Cannon is slow-walking it, won’t having the other cases zip ahead put a spotlight on her? (e.g. hypothetically: “The DC trial already came to a verdict, how come Cannon is still futzing around with discovery??”)
Uh…it’s harder to run for President from a prison cell?
So, now we know what you meant when you said you had a vacation of sorts. Hope you are well on the mend. I guess you might be thinking about a different kind of boot, too. Best wishes on your recovery.
Thanks for sharing the Thomas Fine diagram, too.
OT but amazing. The judge in the NY case brought by Laetitia James has just ordered the dissolution of the Trump Organization, putting it into receivership and stripping it of it’s business licenses.
https://www.thedailybeast.com/trump-basically-just-lost-the-new-york-bank-fraud-case-before-it-even-started?utm_source=web_push
“Even before the trial officially starts, the ruling handed New York Attorney General Letitia James a near total victory, meaning that next week’s trial will mostly focus on damages that could pulverize whatever is left of Trump’s many business entities and bank accounts.
In his 35-page opinion, Justice Arthur F. Engoron tore apart what he called the Trump family’s “bogus arguments” and obstreperous conduct. And he summed up the entire defense as “a fantasy world, not the real world.” “
I think we are about to find out how resilient TrumpOrg is. If they cannot conduct business in NY State, what will be the collateral effects on the worldwide business between the properties used for backstop loans and loss of reputation? I think it is substantial and might just be a tipping point if we’re lucky.
The whole schtick for Defendant-1 is the ability to buy off anything he wanted, but this ruling will blow a hole in that plan even before the damages are tacked on.
Perhaps DJTJ needs to marry Kim G before his money runs out.
He’s counting on the press to treat it as a nothingburger the way they’ve memoryholed a judge and jury deciding he sexually assaulted someone.
Something something diner patron in Iowa.
He literally threatened to take down NBC, but the NY Times and Washington Post published nothing, as if they aren’t just as exposed and lacking in leverage if he wins. Their editors and execs are broken, and Trump knows it.
Marcy:
https://nitter.net/emptywheel/status/1706793076159643863#m []
Sep 26, 2023 · 10:09 PM UTC
I think this is what she’s referring to:
Just after a footnote citing Chico Marx, which I’m guessing is not typical for judges in any jurisdiction.
Hi harpie, good to see you.
Hi, Molly! Good to see you, too! :-)
It is indeed. Working on a post on the Fraud ruling.
Stunning the degree to which the press is uninterested that the GOP candidate is a fraud.
And here it is:
https://www.emptywheel.net/2023/09/27/donald-trumps-fantasy-self-worth/
harpie! I’ve missed you! It’s great to see you back here doing what you do so well, and nobody else does at all. Thank you.
“In his decision on Tuesday, Engoron also decided to impose sanctions on the Trumps’ lawyers over the AG’s accusations that they have acted unprofessionally by raising ridiculous arguments and delaying the case this long. AG investigators have been digging into the Trumps’ finances for more than three years and have been slowed down at every turn by a company that has refused to turn over documents and Trump family members who wouldn’t show up for official interviews. The family’s procrastination and obstruction efforts forced the judge to intervene several times, at one point ordering the former president himself to pay $110,000 in fines.”
…
“He ordered the entire Trump legal team—Michael Madaio, Clifford S. Robert, Michael Farina, Christopher Kise, and Armen Morian—to each pay $7,500, a punishment that will also serve as a blemish on their professional records.”
OT, but having just read Judge Engoron’s ruling in the Laetitia James case I can’t recall reading a more brutal benchslap.
This is no “brutal benchslap”; this is “manos de piedras”
Have a cite for the text of that ruling? Thanks.
Screen cap of the conclusion / order section here.
https://www.dailykos.com/stories/2023/9/26/2195644/-RIP-Trump-Organization
ew retweeted southpaw: https://twitter.com/nycsouthpaw/status/1706782301047214170
(it’s an image extracted from the decision: the former guy trying to justify inflated values claimed in the past as being fine because current values are higher.)
Also has link to decision: https://www.documentcloud.org/documents/23991885-452564_2022_people_of_the_state_of_v_people_of_the_state_of_decision___order_on_1531
Judge cites former 2016 Trump ruling in his Parens Patriae section. His own history of judicial slapdowns gets two entries in that page (4) of the ruling. The “sophistry” slapdown is the footnote at the bottom of that page.
I just read that. Holy cow, Trump should just plead guilty before he’s slapped down even more.
This is via nycsouthpaw:
https://www.documentcloud.org/documents/23991885-452564_2022_people_of_the_state_of_v_people_of_the_state_of_decision___order_on_1531
Thanks.
Isn’t it great to have Harpie back!
Aw, gee…thanks, bmaz! :-) <3
One of my faves! She always has interesting takes and provides links for us to learn more!
Agree 100%!!
dang, beat me to it…but I stopped to look at it.
That was pure coincidence…just happened to be checking in on nycsouthpaw shortly after this came out.
Sorry, slow to respond.
https://iapps.courts.state.ny.us/fbem/DocumentDisplayServlet?documentId=SW20FJCsispWwDnx1ms5Dw==&system=prod
My personal favourites:
“In flagrant disregard of prior orders of this Court and (in italics) the First Department…”
“the Court decliined to impose sanctions believing it had “made its point”. Apparently, the point was not received. One would not know from reading defendants’ papers that this Court has already twice (in italics) ruled against these arguments, called them frivolous, and twice (in italics) been affirmed by the First Department.”
“Defendants conduct in reiterating these frivolous arguments is egregious. We are way beyond the point of “sophisticated counsel should have known better”; we are at the point of intentional and blatant disregard of controlling authority and law of the case. […] Defendants’ repetition of them is indefensible.”
“That is a fantasy world, not the real world.”
“As this Court has noted ad nauseum (in italics)”
“The defenses Donald Trump attempts to articulate in his sworn deposition are wholly without basis in law or fact.”
“He [Trump] also seems to imply that the numbers cannot be inflated because he could find “a buyer from Saudi Arabia” to pay any price he suggests”
“defendants absurdly suggest that “the calculation of square footage is a subjective process that could lead to differing results or opinions…””
Thank you for posting the link. It really is pretty Lol-worthy.
Thanks for the highlights list, LOL!
Shorter Judge Engeron, regarding Trump’s defenses: “pure sophistry.”
I hope there will be a post about the NY case result soon.
Why? It is a civil case that will not be permanently resolved in Trump’s lifetime.
Sorry—not the full resolution of the case, including appeals—I meant a post on the ruling we’re discussing, which as I understand it, leaves only the financial penalty to be determined by Judge Engoron.
It is an existential threat to Trump’s mythology, persona and wealth. He will appeal at the state level. Trump will try to take it to the Sup. Ct., but I doubt they’ll take it.
A quick note on names, as NY state courts are peculiar. The trial level is, oddly, called the Supreme Court. First level appeals are tried at the Supreme Court, Appellate Division. The top state court is called the Court of Appeals.
Thx, saved me some head scratching.
NY is indeed bizarre in the naming of courts.
Mazars’ infamous disclaimers on the Don’s many financial statements were of no use: “In sum, the Mazars disclaimers put the onus for accuracy squarely on defendants’ shoulders.”
On disgorgement – being forced to return profits made owing to the fraud – Trump’s lawyers argued that it is not available where the money paid was not from the public. Sadly for the Don and his lawyers, NY’s highest court overruled the case they relied on for that argument in 2016, something first-year law students would have learned to check before citing it in court.
“[T]he Court [earlier] declined to impose sanctions, believing it had ‘made its point.’…Apparently the point was not received.”
“One would not know from reading Defendants’ papers,” that the Court – in this case – had twice ruled against Defendants’ arguments, and twice been affirmed on appeal. That’s a plea for the court to impose sanctions.
Two points of perhaps pickiness. First, I’d call it “The Court’s ruling”, not “the Judge’s ruling. It’s not one person’s opinion or decision, it is the ruling of a legally constituted court of law. Let’s give it the weight it deserves.
Second, I’d call it “the New York State case”, not “the Laetitia James” case. It’s not one person’s case, and it’s not even an Attorney General’s case, it’s a case brought by a State and its People. (The case caption starts, “People of the State of New York”.) Let Trump complain about his home state turning on him, not some individual.
But it’s great!
Colloquial usage is fine, as long as it identifies the right people and things. It’s also a frequently useful shorthand.
Fair points.
If and when the receiver starts compiling, valuing and disposing of the assets of Trump’s legal entities, things will get interesting. As bmaz says, it could take years to sort out.
But the receiver’s priority is not running a business. It’s to liquidate a business. S/he would use reasonable efforts to obtain the best possible price for assets, typically for cash in hand, based on current fair market values. They would be obligated to pay all legitimate creditors the full amount they’re owed, or whatever part of that the assets will pay for. The owners of those entities would receive the balance, if any. That’s not how Trump ran his businesses. He deferred everything, except his own satisfaction.
Considerations that might have consumed Trump – tax treatment high among them – would be secondary or irrelevant. Tax consequences are commonly delayed, for example, until a “taxable event” occurs, typically, a sale or disposition. So a lot of long-delayed tax costs and benefits might cascade into one or two tax years, substantially increasing the tax bill. Trump will litigate that unto death.
If the Don is correct, that he can find a Saudi who will pay whatever he wants for whatever he has, we might soon find out.
Thanks for all your help in understanding this, Earl!
Aw, shucks.
We are so so lucky that there are such knowledgable people here! Thanks Earl, blooper, bmaz! and peterr, and of course ew.
and harpie!
There’s been some discussion in the media about Trump’s foreign assets, of which there are reportedly many, and whether they are within reach of this ruling (assuming it is affirmed on appeal).
The short answer is it depends on how they are owned. If a NY entity for which a receiver is appointed is the ultimate owner, then under standard corporate law, it has authority to dispose of its assets, wherever located.
With respect to one such asset — the golf course in Aberdeen Scotland — the opinion says that it is owned by the Trump Organization. It also says that the Trump lawyers “wholly fail to address Aberdeen [ed: the factual misstatements and overstatement of value] in any of their three memos of law, in their response to OAG’s statement of material facts . . .”
Either they realized that they had no defense here, or they simply hoped the judge wouldn’t notice that they didn’t address Aberdeen. Of course, both could be true, and in this case, probably are.
It’s a point I was trying to reach in my question from yesterday. Most businesses have a core / fulcrum / citadel which is the foundation of all their investments. I suspect that for TrumpOrg, the citadel is the New York piece.
Even if a business is licensed in NYC, for example, many jurisdictions would also require a local licensing presence (my DE chartered company has CA and city licenses) to aid in local law enforcement (i.e. labor laws). The EU is notorious for demanding compliance to their business laws, and I would not be surprised that the UK does as well, even post-Brexit.
I would speculate that the NY citadel licensing was used to leverage the overseas ones and it may become a situation where those regulators will take action as well. In addition to the backstop of money and assets under control, there is also now a specific ruling of overall corporate malfeasance so bad that TrumpOrg was fired, so to speak. Even the most corrupt civil servant may look to be somewhere else when the ordure hits the rotating air mover.
It does not augur well for Defendant-1 that both civil trials so far have summarily ruled against him on liability for damages, saying there was nothing to argue about in terms of the facts. With the higher bar for criminal cases it’s not directly analogous but the fact both judges were so clear cut about it can’t be good for the defense.
On the damages side, the defense has been trying to argue no one was hurt, ignoring the fact that the phony valuations at the very least ripped off the state and cities of New York on tax revenue otherwise owed. That’s before considering those cheated by the inflated pricing and the admission in court papers that Defendant-1 was for sale in a tactical riposte leading to a strategic blunder.
AG James will now be able to conduct discovery (in CA it’s the Order of Examination) to see what TrumpOrg really has and that might be what finishes off the whole rotten empire. It’s about being seen as wealthy and successful and what the OEX might just show is that Forbes was right long ago when the alter ego called to demand the magazine upgrade his ranking.
I don’t have a copy handy of the NYS case but I have the Statement of Facts for the Manhattan false biz records case at hand. The SOF says in Background (pg. 2):
Sadly, doesn’t spell out where the organization is incorporated. I doubt The Donald wanted incorporation in Delaware for the same reasons Elon Musk pulled Xitter out of DE for NV. Asset seizure by NYS-AG could hurt deeply if Trump Org remained incorporated in NYS.
Yes, every state requires a foreign entity doing business instate to register with state tax authorities and to appoint an agent for service of process. Companies typically use a registered branch or subsidiary for that purpose. Its purpose is to manage liability as well as comply with local requirements.
Failure to comply with those “doing business” requirements generates problems. One of them is that the foreign corporation is itself deemed to be doing business in state, which can generate substantial tax and other liabilities.
International licensing is vulnerable to substantial tax abuse, when it occurs among related entities, notwithstanding the IRS’s arms’ length rule.
Revenue is often booked by a controlled entity in a no/low tax jurisdiction. Associated costs tend to be taken in a high-tax jurisdiction. The cash itself is pooled, if possible, with other revenue and kept in a low-tax jurisdiction, until needed elsewhere to cover operating expenses. Service agreements among related entities create the nominal framework for moving it around.
True, and all that is down the road once all the motions are ruled on and all appeals exhausted. There is no “receiver” at present, but there is an independent monitor. Judge Jones (ret) is that independent monitor, who is “to ensure that there is no further fraud or illegality that violates section 63(12) pending final disposition of this action.”
Even the presence of that monitor has to tick Trump off, as he has to get someone else to sign off on everything as not being a further violation of this law. This is *not* something that Trump likes at all.
Well, we’ll see whether Trump wins a stay on the appointment of receivers, pending the resolution of his likely several appeals.
My guess is that the Appellate Division will rule quickly, the Court of Appeals is likely to take longer. (My guess is that the Sup. Ct. would refuse cert., should he ask for it.)
Fortunately, Gov. Kathy Hochul lost in her bid to appoint a radical conservative Republican as chief justice of the CA, which would also have given the court a Republican majority. So many New Yorkers found that move appalling by a Democratic governor that the often moribund legislature successfully stopped the appointment.
Dumb question, but why are the items in the spreadsheet in chronological order? Or reverse chronological order?
Because that’s how you develop a narrative, even a false one.
BTW, the date at the top of the spreadsheet is the date of it’s assembly by Shapley; he doesn’t give a date for the laptop being dropped off.
Sorry. My original comment wasn’t clear. Why are the items on the GOVERNMENT’s list NOT in chronological or reverse chronological order?
Once someone boots up the laptop, outside of a lab environment and presumably without proper chain of custody (most likely, considering the basic questions this guy was asking), there is legitimate cause to at least question the validity of any of the forensic evidence obtained from it.
The act of booting up the laptop alone changes the evidence. The proper way to approach this would be to clone the drive in the presence of another witness, in a closed environment (not connected to a network), using a sterile machine to connect to it (which then becomes part of the evidence chain) and working off of the cloned drive. Folks who can’t figure out how to boot the machine to begin with, or understand even basic details about file systems, have no business doing a forensic investigation.
I am just an unfrozen caveman IT tech who has rebuilt PCs and Macs for over a decade. (I hand ‘em out because it makes me feel like Rockefeller passing out dimes to urchins.)
There is so much about this story that doesn’t pass the smell test.
Occam’s Razor leads me to suspect that a MAGA hacker got Hunter Biden’s iCloud backups, restored them to a used MacBook. That Mac Book went to Giuliani’s team, who dropped it off / Fed Ex’d it at Isaac’s shop.
Isaac then used Apple’s Time Machine software to back the MacBook up, and restored that backup to the second MacBook. Insert Russian techs and a can of Diet Coke. Sprinkle in a couple of rogue agents from Team Rudy.
You can see that I have spent way too much time watching TV.
[Thanks for updating your username to meet the 8 letter minimum. At least I assume that’s what you’ve done here by added the number 9 to your username. /~Rayne]
Your Rudy Colludie season one pilot is perfect, except I’m not sure Rudy is smart enough to plan anything in advance other than a round of Dewars. All we need now is the deaf piano tuner recalling the conversation Hunter had with Burisma.
Rudy’s smart enough, or he used to be. I just don’t think he’s been sober enough for the past five or a dozen years.
That would fly in the face of Hunter’s lawsuit against Costello and Giuliani for “hacking” his laptop.
https://www.cbsnews.com/news/hunter-biden-sues-rudy-giuliani-attorney-robert-costello-for-hacking-laptop-data/
My reading is that Hunter is admitting that his laptop was tampered with, not that his iCloud data was transported to another laptop. Rudy’s lawyer even commented yesterday that the suit has Hunter finally admitting that the laptop is his.
That being the case, I’m wondering why Hunter never claimed it was stolen, as well as hacked, and filed a police report to that effect. I must be missing something.
I used to work in a large laboratory that did mouse genetics research. We went through a lot of laptops, and the old ones (that were broken or just replaced when we updated our hardware) went into a locked drawer in a file cabinet. There was literally a large stack of them in there. We also had a “cable drawer” for old cables for both our desktops and laptops. It was easier to just keep things than it was to go through the process of getting rid of them. If you walked out with two or three of them in your backpack, I doubt anyone would have even noticed that they were gone.
Rudy’s full of shit. For starters, pleadings are bare outlines of the facts, not the full spec sheet. Are Rudy and HB even talking about the same laptop or hard drive?
Wow, boom goes the dynamite. This lawsuit, Hunter’s other lawsuits, Menendez indictment, things are heating up. Can’t wait to dig in and read these articles and new lawsuit.
The agents got a list of Hunter’s devices from Apple and when they found Mac Isaac’s was one of them, then the hardware as well as the contents had a new status, though the suggestion that they might just have imaged it instead of seizing it is odd.
I share your incredulity at the clueless FBI techie. Is it possible “Matt” and the rest taking part were a special team, picked for reasons or is Mac Isaac just a big liar, doing his bit to discredit the FBI?
Mac Isaac said Hunter brought a laptop for data recovery but hardly mentions the other two eg to his April 2019 $85 quote [1] “Attempt data recovery on 3 MacBook pros … contact customer when complete.”
The laptop the FBI took (along with the external drive) identified from the serial number in the subpoena [1] is a 2017 MacBook Pro [2] which has removable flash storage.
Here Mac Isaac describes “the last Mac” a 2016 MacBook Pro with its non-removable, non-upgradable, soldered-on SSD.
I assume he gave the other two back some time before he called the feds but at least there’s something wrong with the chronology here.
[1] https://nypost.com/2020/10/14/email-reveals-how-hunter-biden-introduced-ukrainian-biz-man-to-dad/
[2] https://nitter.net/michaeldweiss/status/1316515800942080000
So, in head-to-head competition, which experience was worse? The foot surgery or the book?
Oh, the dead time was sufficiently dead that the book was easy pickings.
Ha! You beat me to it. That was going to be my question too. I mean, at least you can sleep through the actual surgery–unless they do it differently in UK.
Ireland!
Sorry! I know EW lives in Ireland, but I got off track during the medical narrative when the Cuban doctor showed up. I thought she was visiting UK.
Were she in the UK, using the NHS, she’d still be waiting for surgery, and probably still waiting for months more.
So, was the anesthesia Jameson’s or Red Breast?
Maybe someone in the comments can answer this. I thought Macbooks could be put in a mode where the hard drive can be accessed externally. For example, attaching another computer to the laptop then booting the laptop into that mode where the drive can be accessed by the other computer. If I’m correct, did Mac Isaac or the FBI describe why they didn’t do that?
The laptop mentioned in the document is apparently a 2017 MacBook Pro with function keys. (EMC 3164) Ifixit.com shows this machine to have a removable (not soldered) SSD.
https://www.ifixit.com/Parts/MacBook_Pro_13%22_Function_Keys_2017/Storage
SSD are somewhat resistant to liquids. An idiot can pull this SSD and stick it in a cheap external case in less than 30 minutes. At which point it can be imaged. That SSD can also be used as an external boot drive – which might modify it – or can be accessed by another computer (yes, even by Windows!)
“Target Mode” is what you have in mind, but a machine that will not boot can not go into that mode.
In conclusion: someone is lying. Occam’s Magic 8-Ball says it’s not Hunter Biden.
My experience with macs is about 20 years old, so pretty out of date, so this applies to hard drives in general:
The short version is: As long as you can connect the correct cable from the hard drive to any computer, it can then be accessed.
How much use you can get from the access is something entirely different, mainly dependant on two factors: If the drive is encrypted (which many of the newer drives are by default) you will need the necessary key to gain access. That key is usually entrusted to a secure module on the computer/laptop which is designed to be hard to copy out.
If the disk is unencrypted (or decrypted using the key) the accessing computer still needs to understand the file format used. Windows is notoriously bad at understanding any other formats than it’s own, while most Linux variants can read just about any obscure format.
Lastly, there is a way to access the drive in the computer it’s hosted, without booting from it: There are several portable live systems that can boot from a CD/DVD or USB drive, with Knoppix possibly being the most famous. You wouldn’t do this for a proper forensic dump due to the possibility of hardware triggers, but a computer repair tech would definitely try this method to get data out of a “dead” computer.
EuroTark is quite right. I don’t want to derail our thread because the point is that the whole Isaac story is b.s. and poorly formed.
There are probably several crimes occurring here, and none of them attributable to Hunter Biden. Unfortunately, A. G. Garland can’t prosecute them without feeding the weaponization frenzy.
But I look forward to Hunter Biden’s civil suit, and to hearing the judge slam down his gavel and declare “FAFO!”
PS. I love the Thomas A Fine diagram, but I think spaghetti would explain more than just straight lines.
Very interesting breakdown of these timeline discrepancies btw Mac Isaac and Shapley, and there are even more.
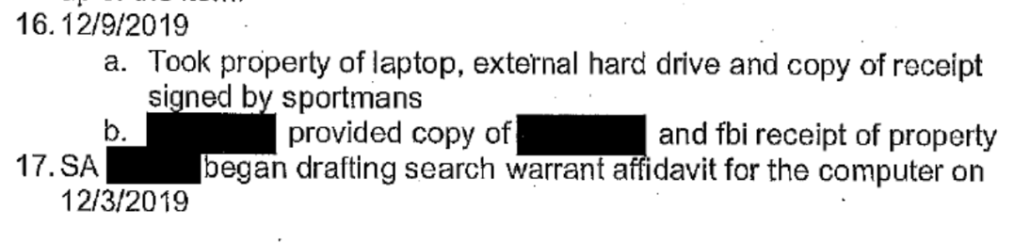
I have been really curious about that 11/6/2019 date from Shapley’s timeline. Here is the full text
First, as you pointed out previously, its weird being on first name basis there. But questions I have are:
* in bullet point a, it doesn’t mention a warrant, so is there another method that the FBI can tie the “device identifier” to the “Apple ID account”? Such as from the original escort service tax investigation or whatever it was started in November 2018?
* in the event of obtaining a warrant, or otherwise, is it possible that they only access 1 of Hunter’s Apple ID’s but not the other?
* in bullet point b, there is a hyphen followed by blank space, like starting a thought but not being able to finish it. Does that mean that they did not actually verify the device and put it on a to-do list?
They would have served Apple with a subscriber request–it’s a subpoena and does not require probable cause. That should have listed all his device identifiers, unless they asked in a really weird way. That’s why I’ve always said, from that moment forward, the IRS/FBI likely had abundant reason to worry that someone was hacking Hunter, probably in ongoing fashion. Even what we see in the emails, there are simply too many new device accesses, without the related password change (and even in the depths of his addiction, he was changing passwords at key times). There are some, even in the emails alone, that are CLEARLY attempted compromises. And if any single one of those were successful (much less a series of them), it would be child’s play to take over his digital identity. All the more so given what we see about changing device identifier information, meaning he wouldn’t get notice if someone was trying to access his computer.
There’s an instance, early on, where (IIRC) Archer or Schwerin accesses his account and Hunter immediately asks if it’s him. You would expect him to respond similarly to the other instances, but he doesn’t.
The subscriber information IRS should have referred to also would include IP addresses, which would make testing whether there was a hack even easier. They don’t appear to have done it.
Interesting, thanks for the response.
About the subpoena that would have served Apple with a subscriber request, would that subpoena achieve results the same day? Or some time as it bounces around the Apple legal department? The way Shapley records it, that is occurring the same day that “Josh Wilson called John Paul”. Would there be some pre existing list of device identifiers matching that they determine the match immediately?
Or am I completely misunderstanding something?
This is pure speculation on my part, but I would be surprised if subpoenas for subscriber info was handled manually. Most likely they’ve set up a law enforcement gateway where authorized users can pull the information they need and leave the documentation for it.
A question I haven’t seen addressed, about the purple email:
“It was begging to be clicked open. So I did.”
Please tell me he’s not admitting to a crime right there. I understand the Mac became his property after a certain period had elapsed (had it?) but does that give him the authority to read private contents, or is wiping surrendered equipment just a courtesy routinely followed by more reputable outfits?
Mac Isaacs is claiming it was his after 30 (or was it 90?) days, but It’s been mentioned that Delaware law says it’s a year for unclaimed property. And we still don’t know who actually left it there, since there’s no receipt with identification.
But none of the drive contents were ever his, certainly nothing password protected.