Russian Hack-Related Excerpts from President Obama’s Press Conference
Just to have all this in one place, I’ve pulled all the comments from President Obama’s December 16 press conference.
Josh Lederman, of AP.
Q Thank you, Mr. President. There’s a perception that you’re letting President Putin get away with interfering in the U.S. election, and that a response that nobody knows about or a lookback review just won’t cut it. Are you prepared to call out President Putin by name for ordering this hacking? And do you agree with what Hillary Clinton now says, that the hacking was actually partly responsible for her loss? And is your administration’s open quarreling with Trump and his team on this issue tarnishing the smooth transition of power that you have promised?
THE PRESIDENT: Well, first of all, with respect to the transition, I think they would be the first to acknowledge that we have done everything we can to make sure that they are successful as I promised. And that will continue. And it’s just been a few days since I last talked to the President-elect about a whole range of transition issues. That cooperation is going to continue.
There hasn’t been a lot of squabbling. What we’ve simply said is the facts, which are that, based on uniform intelligence assessments, the Russians were responsible for hacking the DNC, and that, as a consequence, it is important for us to review all elements of that and make sure that we are preventing that kind of interference through cyberattacks in the future.
That should be a bipartisan issue; that shouldn’t be a partisan issue. And my hope is that the President-elect is going to similarly be concerned with making sure that we don’t have potential foreign influence in our election process. I don’t think any American wants that. And that shouldn’t be a source of an argument.
I think that part of the challenge is that it gets caught up in the carryover from election season. And I think it is very important for us to distinguish between the politics of the election and the need for us, as a country, both from a national security perspective but also in terms of the integrity of our election system and our democracy, to make sure that we don’t create a political football here.
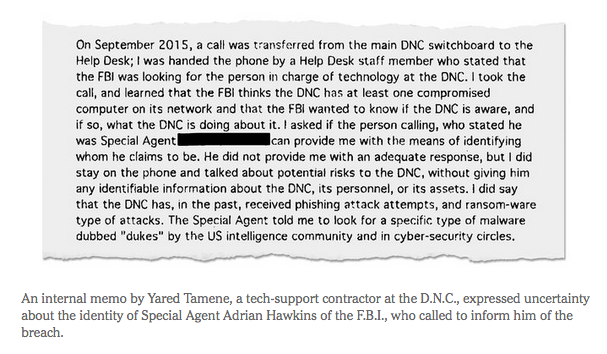
Now, with respect to how this thing unfolded last year, let’s just go through the facts pretty quickly. At the beginning of the summer, we’re alerted to the possibility that the DNC has been hacked, and I immediately order law enforcement as well as our intelligence teams to find out everything about it, investigate it thoroughly, to brief the potential victims of this hacking, to brief on a bipartisan basis the leaders of both the House and the Senate and the relevant intelligence committees. And once we had clarity and certainty around what, in fact, had happened, we publicly announced that, in fact, Russia had hacked into the DNC.
And at that time, we did not attribute motives or any interpretations of why they had done so. We didn’t discuss what the effects of it might be. We simply let people know — the public know, just as we had let members of Congress know — that this had happened.
And as a consequence, all of you wrote a lot of stories about both what had happened, and then you interpreted why that might have happened and what effect it was going to have on the election outcomes. We did not. And the reason we did not was because in this hyper-partisan atmosphere, at a time when my primary concern was making sure that the integrity of the election process was not in any way damaged, at a time when anything that was said by me or anybody in the White House would immediately be seen through a partisan lens, I wanted to make sure that everybody understood we were playing this thing straight — that we weren’t trying to advantage one side or another, but what we were trying to do was let people know that this had taken place, and so if you started seeing effects on the election, if you were trying to measure why this was happening and how you should consume the information that was being leaked, that you might want to take this into account.
And that’s exactly how we should have handled it. Imagine if we had done the opposite. It would have become immediately just one more political scrum. And part of the goal here was to make sure that we did not do the work of the leakers for them by raising more and more questions about the integrity of the election right before the election was taking place — at a time, by the way, when the President-elect himself was raising questions about the integrity of the election.
And, finally, I think it’s worth pointing out that the information was already out. It was in the hands of WikiLeaks, so that was going to come out no matter what. What I was concerned about, in particular, was making sure that that wasn’t compounded by potential hacking that could hamper vote counting, affect the actual election process itself.
And so in early September, when I saw President Putin in China, I felt that the most effective way to ensure that that didn’t happen was to talk to him directly and tell him to cut it out, and there were going to be some serious consequences if he didn’t. And, in fact, we did not see further tampering of the election process. But the leaks through WikiLeaks had already occurred.
So when I look back in terms of how we handled it, I think we handled it the way it should have been handled. We allowed law enforcement and the intelligence community to do its job without political influence. We briefed all relevant parties involved in terms of what was taking place. When we had a consensus around what had happened, we announced it — not through the White House, not through me, but rather through the intelligence communities that had actually carried out these investigations. And then we allowed you and the American public to make an assessment as to how to weigh that going into the election.
And the truth is, is that there was nobody here who didn’t have some sense of what kind of effect it might have. I’m finding it a little curious that everybody is suddenly acting surprised that this looked like it was disadvantaging Hillary Clinton because you guys wrote about it every day. Every single leak. About every little juicy tidbit of political gossip — including John Podesta’s risotto recipe. This was an obsession that dominated the news coverage.
So I do think it’s worth us reflecting how it is that a presidential election of such importance, of such moment, with so many big issues at stake and such a contrast between the candidates, came to be dominated by a bunch of these leaks. What is it about our political system that made us vulnerable to these kinds of potential manipulations — which, as I’ve said publicly before, were not particularly sophisticated.
This was not some elaborate, complicated espionage scheme. They hacked into some Democratic Party emails that contained pretty routine stuff, some of it embarrassing or uncomfortable, because I suspect that if any of us got our emails hacked into, there might be some things that we wouldn’t want suddenly appearing on the front page of a newspaper or a telecast, even if there wasn’t anything particularly illegal or controversial about it. And then it just took off.
And that concerns me. And it should concern all of us. But the truth of the matter is, is that everybody had the information. It was out there. And we handled it the way we should have.
Now, moving forward, I think there are a couple of issues that this raises. Number one is just the constant challenge that we are going to have with cybersecurity throughout our economy and throughout our society. We are a digitalized culture, and there is hacking going on every single day. There’s not a company, there’s not a major organization, there’s not a financial institution, there’s not a branch of our government where somebody is not going to be phishing for something or trying to penetrate, or put in a virus or malware. And this is why for the last eight years, I’ve been obsessed with how do we continually upgrade our cybersecurity systems.
And this particular concern around Russian hacking is part of a broader set of concerns about how do we deal with cyber issues being used in ways that can affect our infrastructure, affect the stability of our financial systems, and affect the integrity of our institutions, like our election process.
I just received a couple weeks back — it wasn’t widely reported on — a report from our cybersecurity commission that outlines a whole range of strategies to do a better job on this. But it’s difficult, because it’s not all housed — the target of cyberattacks is not one entity but it’s widely dispersed, and a lot of it is private, like the DNC. It’s not a branch of government. We can’t tell people what to do. What we can do is inform them, get best practices.
What we can also do is to, on a bilateral basis, warn other countries against these kinds of attacks. And we’ve done that in the past. So just as I told Russia to stop it, and indicated there will be consequences when they do it, the Chinese have, in the past, engaged in cyberattacks directed at our companies to steal trade secrets and proprietary technology. And I had to have the same conversation with Prime Minister — or with President Xi, and what we’ve seen is some evidence that they have reduced — but not completely eliminated — these activities, partly because they can use cutouts.
One of the problems with the Internet and cyber issues is that there’s not always a return address, and by the time you catch up to it, attributing what happened to a particular government can be difficult, not always provable in court even though our intelligence communities can make an assessment.
What we’ve also tried to do is to start creating some international norms about this to prevent some sort of cyber arms race, because we obviously have offensive capabilities as well as defensive capabilities. And my approach is not a situation in which everybody is worse off because folks are constantly attacking each other back and forth, but putting some guardrails around the behavior of nation-states, including our adversaries, just so that they understand that whatever they do to us we can potentially do to them.
We do have some special challenges, because oftentimes our economy is more digitalized, it is more vulnerable, partly because we’re a wealthier nation and we’re more wired than some of these other countries. And we have a more open society, and engage in less control and censorship over what happens over the Internet, which is also part of what makes us special.
Last point — and the reason I’m going on here is because I know that you guys have a lot of questions about this, and I haven’t addressed all of you directly about it. With respect to response, my principal goal leading up to the election was making sure that the election itself went off without a hitch, that it was not tarnished, and that it did not feed any sense in the public that somehow tampering had taken place with the actual process of voting. And we accomplished that.
That does not mean that we are not going to respond. It simply meant that we had a set of priorities leading up to the election that were of the utmost importance. Our goal continues to be to send a clear message to Russia or others not to do this to us, because we can do stuff to you.
But it is also important for us to do that in a thoughtful, methodical way. Some of it we do publicly. Some of it we will do in a way that they know, but not everybody will. And I know that there have been folks out there who suggest somehow that if we went out there and made big announcements, and thumped our chests about a bunch of stuff, that somehow that would potentially spook the Russians. But keep in mind that we already have enormous numbers of sanctions against the Russians. The relationship between us and Russia has deteriorated, sadly, significantly over the last several years. And so how we approach an appropriate response that increases costs for them for behavior like this in the future, but does not create problems for us, is something that’s worth taking the time to think through and figure out. And that’s exactly what we’ve done.
So at a point in time where we’ve taken certain actions that we can divulge publically, we will do so. There are times where the message will go — will be directly received by the Russians and not publicized. And I should point out, by the way, part of why the Russians have been effective on this is because they don’t go around announcing what they’re doing. It’s not like Putin is going around the world publically saying, look what we did, wasn’t that clever? He denies it. So the idea that somehow public shaming is going to be effective I think doesn’t read the thought process in Russia very well.
Okay?
Q Did Clinton lose because of the hacking?
THE PRESIDENT: I’m going to let all the political pundits in this town have a long discussion about what happened in the election. It was a fascinating election, so I’m sure there are going to be a lot of books written about it.
Peter Alexander.
Q Mr. President, thank you very much. Can you, given all the intelligence that we have now heard, assure the public that this was, once and for all, a free and fair election? And specifically on Russia, do you feel any obligation now, as they’ve been insisting that this isn’t the case, to show the proof, as it were — they say put your money where your mouth is and declassify some of the intelligence, some of the evidence that exists? And more broadly, as it relates to Donald Trump on this very topic, are you concerned about his relationship with Vladimir Putin, especially given some of the recent Cabinet picks, including his selection for Secretary of State, Rex Tillerson, who toasted Putin with champagne over oil deals together? Thank you.
THE PRESIDENT: I may be getting older, because these multipart questions, I start losing track. (Laughter.)
I can assure the public that there was not the kind of tampering with the voting process that was of concern and will continue to be of concern going forward; that the votes that were cast were counted, they were counted appropriately. We have not seen evidence of machines being tampered with. So that assurance I can provide.
That doesn’t mean that we find every single potential probe of every single voting machine all across the country, but we paid a lot of attention to it. We worked with state officials, et cetera, and we feel confident that that didn’t occur and that the votes were cast and they were counted.
So that’s on that point. What was the second one?
Q The second one was about declassification.
THE PRESIDENT: Declassification. Look, we will provide evidence that we can safely provide that does not compromise sources and methods. But I’ll be honest with you, when you’re talking about cybersecurity, a lot of it is classified. And we’re not going to provide it because the way we catch folks is by knowing certain things about them that they may not want us to know, and if we’re going to monitor this stuff effectively going forward, we don’t want them to know that we know.
So this is one of those situations where unless the American people genuinely think that the professionals in the CIA, the FBI, our entire intelligence infrastructure — many of whom, by the way, served in previous administrations and who are Republicans — are less trustworthy than the Russians, then people should pay attention to what our intelligence agencies have to say.
This is part of what I meant when I said that we’ve got to think about what’s happening to our political culture here. The Russians can’t change us or significantly weaken us. They are a smaller country. They are a weaker country. Their economy doesn’t produce anything that anybody wants to buy, except oil and gas and arms. They don’t innovate.
But they can impact us if we lose track of who we are. They can impact us if we abandon our values. Mr. Putin can weaken us, just like he’s trying to weaken Europe, if we start buying into notions that it’s okay to intimidate the press, or lock up dissidents, or discriminate against people because of their faith or what they look like.
And what I worry about more than anything is the degree to which, because of the fierceness of the partisan battle, you start to see certain folks in the Republican Party and Republican voters suddenly finding a government and individuals who stand contrary to everything that we stand for as being okay because that’s how much we dislike Democrats.
I mean, think about it. Some of the people who historically have been very critical of me for engaging with the Russians and having conversations with them also endorsed the President-elect, even as he was saying that we should stop sanctioning Russia and being tough on them, and work together with them against our common enemies. He was very complimentary of Mr. Putin personally.
That wasn’t news. The President-elect during the campaign said so. And some folks who had made a career out of being anti-Russian didn’t say anything about it. And then after the election, suddenly they’re asking, well, why didn’t you tell us that maybe the Russians were trying to help our candidate? Well, come on. There was a survey, some of you saw, where — now, this is just one poll, but a pretty credible source — 37 percent of Republican voters approve of Putin. Over a third of Republican voters approve of Vladimir Putin, the former head of the KGB. Ronald Reagan would roll over in his grave.
And how did that happen? It happened in part because, for too long, everything that happens in this town, everything that’s said is seen through the lens of “does this help or hurt us relative to Democrats, or relative to President Obama?” And unless that changes, we’re going to continue to be vulnerable to foreign influence, because we’ve lost track of what it is that we’re about and what we stand for.
Martha Raddatz.
Q Mr. President, I want to talk about Vladimir Putin again. Just to be clear, do you believe Vladimir Putin himself authorized the hack? And do you believe he authorized that to help Donald Trump? And on the intelligence, one of the things Donald Trump cites is Saddam Hussein and the weapons of mass destruction, and that they were never found. Can you say, unequivocally, that this was not China, that this was not a 400-pound guy sitting on his bed, as Donald Trump says? And do these types of tweets and kinds of statements from Donald Trump embolden the Russians?
THE PRESIDENT: When the report comes out, before I leave office, that will have drawn together all the threads. And so I don’t want to step on their work ahead of time.
What I can tell you is that the intelligence that I have seen gives me great confidence in their assessment that the Russians carried out this hack.
Q Which hack?
THE PRESIDENT: The hack of the DNC and the hack of John Podesta.
Now, the — but again, I think this is exactly why I want the report out, so that everybody can review it. And this has been briefed, and the evidence in closed session has been provided on a bipartisan basis — not just to me, it’s been provided to the leaders of the House and the Senate, and the chairman and ranking members of the relevant committees. And I think that what you’ve already seen is, at least some of the folks who have seen the evidence don’t dispute, I think, the basic assessment that the Russians carried this out.
Q But specifically, can you not say that —
THE PRESIDENT: Well, Martha, I think what I want to make sure of is that I give the intelligence community the chance to gather all the information. But I’d make a larger point, which is, not much happens in Russia without Vladimir Putin. This is a pretty hierarchical operation. Last I checked, there’s not a lot of debate and democratic deliberation, particularly when it comes to policies directed at the United States.
We have said, and I will confirm, that this happened at the highest levels of the Russian government. And I will let you make that determination as to whether there are high-level Russian officials who go off rogue and decide to tamper with the U.S. election process without Vladimir Putin knowing about it.
Q So I wouldn’t be wrong in saying the President thinks Vladimir Putin authorized the hack?
THE PRESIDENT: Martha, I’ve given you what I’m going to give you.
What was your second question?
Q Do the tweets and do the statements by Donald Trump embolden Russia?
THE PRESIDENT: As I said before, I think that the President-elect is still in transition mode from campaign to governance. I think he hasn’t gotten his whole team together yet. He still has campaign spokespersons sort of filling in and appearing on cable shows. And there’s just a whole different attitude and vibe when you’re not in power as when you’re in power.
So rather than me sort of characterize the appropriateness or inappropriateness of what he’s doing at the moment, I think what we have to see is how will the President-elect operate, and how will his team operate, when they’ve been fully briefed on all these issues, they have their hands on all the levers of government, and they’ve got to start making decisions.
One way I do believe that the President-elect can approach this that would be unifying is to say that we welcome a bipartisan, independent process that gives the American people an assurance not only that votes are counted properly, that the elections are fair and free, but that we have learned lessons about how Internet propaganda from foreign countries can be released into the political bloodstream and that we’ve got strategies to deal with it for the future.
The more this can be nonpartisan, the better served the American people are going to be, which is why I made the point earlier — and I’m going to keep on repeating this point: Our vulnerability to Russia or any other foreign power is directly related to how divided, partisan, dysfunctional our political process is. That’s the thing that makes us vulnerable.
If fake news that’s being released by some foreign government is almost identical to reports that are being issued through partisan news venues, then it’s not surprising that that foreign propaganda will have a greater effect, because it doesn’t seem that far-fetched compared to some of the other stuff that folks are hearing from domestic propagandists.
To the extent that our political dialogue is such where everything is under suspicion, everybody is corrupt and everybody is doing things for partisan reasons, and all of our institutions are full of malevolent actors — if that’s the storyline that’s being put out there by whatever party is out of power, then when a foreign government introduces that same argument with facts that are made up, voters who have been listening to that stuff for years, who have been getting that stuff every day from talk radio or other venues, they’re going to believe it.
So if we want to really reduce foreign influence on our elections, then we better think about how to make sure that our political process, our political dialogue is stronger than it’s been.
Isaac Dovere of Politico.
[snip]
Q Well, what do you say to the electors who are going to meet on Monday and are thinking of changing their votes? Do you think that they should be given an intelligence briefing about the Russian activity? Or should they bear in mind everything you’ve said and is out already? Should they — should votes be bound by the state votes as they’ve gone? And long term, do you think that there is a need for Electoral College reform that would tie it to the popular vote?
[snip]
So with respect to the electors, I’m not going to wade into that issue because, again, it’s the American people’s job, and now the electors’ job to decide my successor. It is not my job to decide my successor. And I have provided people with a lot of information about what happened during the course of the election. But more importantly, the candidates themselves, I think, talked about their beliefs and their vision for America. The President-elect, I think, has been very explicit about what he cares about and what he believes in. So it’s not in my hands now; it’s up to them.