In Two So-Called Fact Checks of Facebook, NYT Forgets Everything It Knows about Indictments
In both this Scott Shane article and this “fact check” of Facebook VP Rob Goldman’s recent tweets on Russian trolls’ use of Facebook (which President Trump then picked up), the NYT has twice forgotten everything it knows about indictments, and in the process failed to properly analyze last week’s Internet Research Agency indictment.
In Shane’s article, he attempts to fact check Goldman using the indictment.
Facebook’s vice president for advertising, Rob Goldman, said on Twitter on Friday, “I have seen all of the Russian ads and I can say very definitively that swaying the election was *NOT* the main goal” — a statement that President Trump retweeted.
But Mr. Mueller’s indictment repeatedly states that the Russian operation was designed not just to provoke division among Americans but also to denigrate Hillary Clinton and support her rivals, mainly Mr. Trump. The hashtags the Russian operation used included #Trump2016, #TrumpTrain, #MAGA and #Hillary4Prison, and one Russian operative was reprimanded for “a low number of posts dedicated to criticizing Hillary Clinton,” the indictment says.
On Twitter, Shane even suggested Goldman hadn’t read the indictment.
Wonder if Rob Goldman has read the indictment. Mueller appears to disagree.
Then, Sheera Frenkel extends the purported fact check.
“I have seen all of the Russian ads and I can say very definitively that swaying the election was *NOT* the main goal.” Tweet #2
Not according to the indictment.
The grand jury indictment secured by Mr. Mueller asserts that the goal of Russian operatives was to influence the 2016 election, particularly by criticizing Hillary Clinton and supporting Mr. Trump and Bernie Sanders, Mrs. Clinton’s chief rival for the Democratic nomination.
The Russians “engaged in operations primarily intended to communicate derogatory information about Hillary Clinton, to denigrate other candidates such as Ted Cruz and Marco Rubio, and to support Bernie Sanders and then-candidate Donald Trump,” the indictment said.
Mr. Goldman later wrote in another tweet that “the Russian campaign was certainly in favor of Trump.”
Both Shane and Frenkel don’t consider what I laid out here:
[T]here are hints that Mueller is using this indictment to set up a more important point.
For example, the indictment (perhaps because of Mueller’s mandate) focuses on political activities supporting or opposing one or another 2016 candidate. Even where topics (immigration, Muslim religion, race) are not necessarily tied to the election, they’re presented here as such. Unless Facebook’s public reports are wrong, this is a very different emphasis than what Facebook has said the IRA focused on. Which is to say that Mueller’s team are focusing on a subset of the known IRA trolling, the subset that involves the 2016 contest between Trump and Hillary.
Goldman was addressing all of IRA’s activity on Facebook, which it described this way in September:
- The vast majority of ads run by these accounts didn’t specifically reference the US presidential election, voting or a particular candidate.
- Rather, the ads and accounts appeared to focus on amplifying divisive social and political messages across the ideological spectrum — touching on topics from LGBT matters to race issues to immigration to gun rights.
- About one-quarter of these ads were geographically targeted, and of those, more ran in 2015 than 2016.
- The behavior displayed by these accounts to amplify divisive messages was consistent with the techniques mentioned in the white paper we released in April about information operations.
Nowhere in the indictment does Mueller describe the scope of what IRA activity his team investigated, though it does describe how “over time” the IRA activity came to focus on the 2016 election.
These groups and pages, which addressed divisive U.S. political and social issues, falsely claimed to be controlled by U.S. activists when, in fact, they were controlled by Defendants. Defendants also used the stolen identities of real U.S. persons to post on ORGANIZATION-controlled social media accounts. Over time, these social media accounts became Defendants’ means to reach significant numbers of Americans for purposes of interfering with the U.S. political system, including the presidential election of 2016.
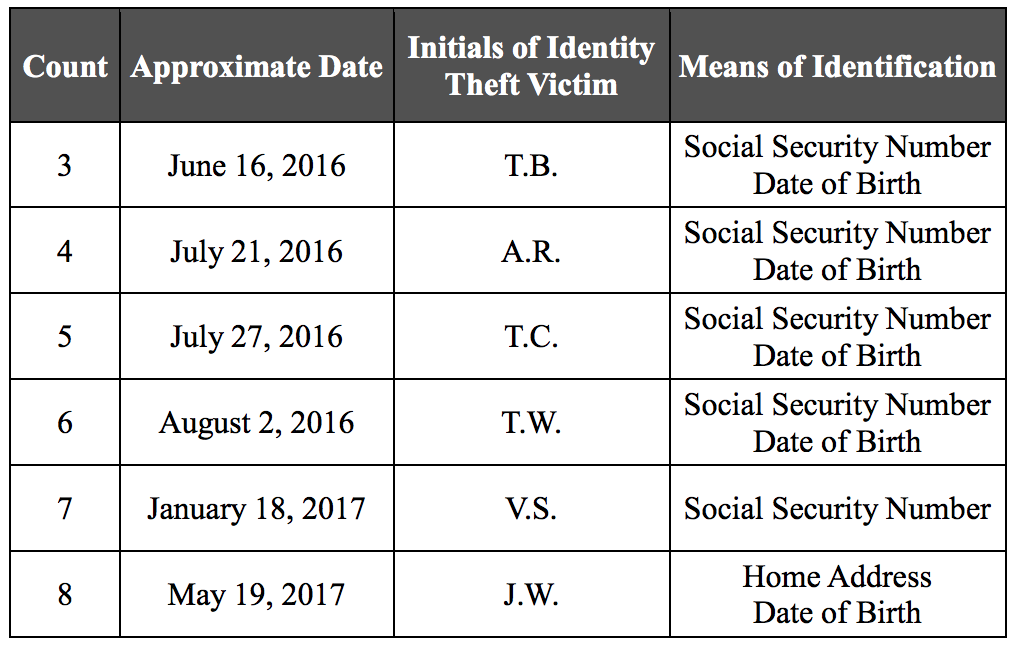
Indeed, the indictment makes it clear that the universe of IRA activity is larger than the election-related activity, in part by tying two counts of identity theft to crimes that happened after the election, as recent as May 2017.
Eight of the usages of fake credentials described in ¶92 also postdate the election. That’s presumably part of what Goldman was pointing to when he tweeted,
The majority of the Russian ad spend happened AFTER the election. We shared that fact, but very few outlets have covered it because it doesn’t align with the main media narrative of Tump and the election.
Even as they, a mainstream media outlet, ignored how Goldman’s invocation of this spending detail and the inclusion of 2017 activities in the indictment is proof that not all of the IRA activities Mueller investigated did pertain to the election, NYT deemed that claim lacking in context.
According to figures published by Facebook last October, 44 percent of the Russian-bought ads were displayed before the 2016 election, while 56 percent were shown afterward. Mr. Goldman asserted that those figures were not published by the “mainstream media” — however, many mainstream news outlets did print those numbers, including CNN, Reuters and The Wall Street Journal.
The point is that there are two universes of IRA Facebook activities: the entire universe, for which Goldman’s claims are generally true, and the activities that Mueller has chosen to focus on, which Shane and Frenkel mistake as the entire universe, and in the process blow their fact checks.
This disjunct continues to the citation of real life events planned using Facebook. Goldman pointed to two May 21, 2016 Houston events, where an Islamophobic event was planned on the same day as a United Muslims event, as the quintessential example of how Russia was trying to pit Americans against each other.
The single best demonstration of Russia’s true motives is the Houston anti-islamic protest. Americans were literally puppeted into the streets by trolls who organized both the sides of protest.
Frenkel doesn’t even get Goldman’s reference correct, in spite of his link to a story on it, and instead apparently takes the citation to be a reference to this passage from the indictment.
By in or around early November 2016, Defendants and their co-conspirators used the ORGANIZATION-controlled “United Muslims of America” social media accounts to post anti-vote messages such as: “American Muslims [are] boycotting elections today, most of the American Muslim voters refuse to vote for Hillary Clinton because she wants to continue the war on Muslims in the middle east and voted yes for invading Iraq.”
From which she concludes,
The protests in Houston in November 2017 were among many rallies organized by Russian operatives through Facebook. While the Houston protest was anti-Islamic, as Mr. Goldman said, he failed to note that the goal in promoting the demonstration was to link Mrs. Clinton’s campaign with a pro-Islamic message.
Again, the indictment is focusing on a particular subset of the IRA activity, whereas Goldman is commenting on the larger universe, arguably to say the indictment understates the threat.
With NYT’s mad, repeated rush to fact check Facebook using an indictment that never claims to be addressing the same universe of IRA activity Goldman was commenting on, they commit some pretty significant analytical errors, errors that extend to their ability to understand what Mueller is doing with the indictment.
I can’t say for certain why Mueller focused on certain kinds of IRA activity, but I can think of three likely possibilities:
- Since his mandate is to investigate Russian tampering in the 2016 election, he is focusing on that subset of the IRA activity
- Because it is tied to election law, the conspiracy to defraud the US charge in the indictment depends on activity that violates election law, and much of the IRA Facebook trolling does not
- The events on which Mueller does focus — notably, twin events at key times in NYC and activities in FL that involve three identified Trump campaign officials — may hint at further crimes or more sophisticated cooperation between the campaign and Russian agents
The last possibility is (as I noted in my earlier post) one of the most intriguing parts of the indictment. But the NYT won’t see it because they’re so busy fact checking claims made about different sets of data.
I get the urge to beat up Facebook. They’ve got a lot to pay for in permitting Russia to abuse their platform. But (I suspect entirely because Trump used Goldman’s tweet to try to exonerate himself) in doing so, NYT has missed Goldman’s larger point, which isn’t an apology at all. Indeed, Goldman was saying that the problem is far bigger than what Mueller lays out in the indictment, and that our continued divisions are a vulnerability Russia continues to exploit.
As Mueller moves forward, we’re likely to see similar kinds of confusion between the specific crimes he addresses in indictments and pleas and the larger toxins that hurt our democracy. So long as we confuse Mueller’s investigation for the larger, still vulnerable whole, we’re never going to do the things as a society we need to prevent this from happening again.
Update: My apologies to Frenkel for misspelling her name originally in this.
Update: On the limits of what is and is not illegal for foreigners to engage in see this Rick Hasen post.
Update: I had an exchange on Twitter with Frenkel about this, and the so-called article has what purports to be a correction.
Because of an editing error, an earlier version of this article misstated the month when protests organized by Russian operatives were held in Houston. It was March 2016, not November 2017.
Except that as corrected (by me, though I got no attribution), the piece compounds its error.
The protests in Houston in May 2016 were among many rallies organized by Russian operatives through Facebook. While the Houston protest was anti-Islamic, as Mr. Goldman said, he failed to note that the goal in promoting the demonstration was to link Mrs. Clinton’s campaign with a pro-Islamic message.
According to the indictment secured by Mr. Mueller, there were many other examples of Russian operatives using Facebook and Instagram to organize pro-Trump rallies. At one protest, the Russian operatives paid for a cage to be built, in which an actress dressed as Mrs. Clinton posed in a prison uniform.
None of the materials or contemporary coverage associated with the anti-Islamic side of the protest associated it with Clinton’s campaign. On the contrary. the protest was about a local Islamic center.
A group calling themselves Heart of Texas called for the rally to protest what they consider “Islamization” of Texas – sparked in part by the recent opening of a privately funded library inside the downtown center. The group had also encouraged followers to bring legal firearms.
Although the Heart of Texas group never showed, about 10 people bearing flags of the United States, Texas and the Confederacy were there. “This is America. We have the right to speak out and protest,” said Ken Reed, who wore a T-shirt emblazoned with the phrase “White Lives Matter.” “We feel Texas, our great state and the United States is being threatened by the influx of Islam.”
Again, I agree that Facebook is a shitty company. But a newspaper doubling down on its errors to attack Facebook’s errors is … doing what it is complaining about.







![[Photo: Annie Spratt via Unsplash]](https://www.emptywheel.net/wp-content/uploads/2017/08/Books_AnnieSpratt-Unsplash_mod1.jpg)
