When we left the mainstream Trump press corps on Friday afternoon, they were all focused on the decision by Beryl Howell to rule that some of Evan Corcoran’s testimony in the stolen document case was crime-fraud excepted. Sure, there were journalists using wildly exaggerated descriptions for the uniqueness or surprise of the development. But, on Friday, reporters covering Trump’s legal woes were providing factual descriptions of actual newsworthy developments.
At the time, there was a general awareness that an indictment from Alvin Bragg may come next week, but the focus was the stolen documents investigation, in part because some journalists appear to believe that the crime-fraud ruling was some new sign that Jack Smith believed a crime had been committed.
Then, on Saturday morning, on his failing social media platform, the former President tweeted out incitement that included the following, in all caps:
- An unsubstantiated claim about illegal leaks probably based on Fox News reporting about efforts to prepare for potential violence as a response to a Trump indictment next week
- An attack on Alvin Bragg’s record on crime
- A claim Bragg is funded by George Soros, the kind of coded antisemitism Trump is including in virtually all his communications these days
- An assertion that he would be charged on something that “numerous other prosecutors!” had debunked as a fairy tale
- An overstatement of the degree to which he is leading in polls and an admission that he is the “former” President
- A day, Tuesday, when he would be “arrested”
- A call to “protest,” invoking one of the same cries used to incite a coup attempt on January 6, “take our country back”
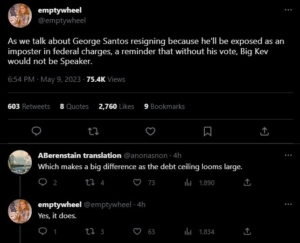
The response was almost instantaneous, with one after another journalist screen-capping the tweet in its entirety, some like Kyle Cheney adding no other commentary other than, “🚨 Trumps says he expects to be arrested Tuesday,” with the siren adding to its inflammatory nature. Jonathan Lemire repeated select newsworthy bits — while still including the full screen cap — without mentioning the coded slur on Soros or labeling the entire tweet as obvious incitement; Lemire parroted Trump’s all caps for the purported timing and quoted the incendiary line also associated with January 6.
NEW: Trump is suggesting that he will be ARRESTED ON TUESDAY due to Manhattan DA probe
This is historic: he would be the first former president to be indicted
He urges his supporters to “Protest, take our nation back!”
The absolutely most hysterical tweet magnifying Trump’s words unfiltered came from Jared Holt, a supposed expert on radicalization online, who introduced Trump’s full tweet onto Twitter (where Trump has not tweeted under his own ID since being permitted back on) with the following:
It will be hard to think of a bigger tech moderation failure than if Trump uses the platforms he’s been allowed back onto (FB, YouTube, Twitter) to incite protests again.
As of this morning, Holt’s tweet, along with the screen cap of Trump’s tweet unfiltered, had garnered 230,000 views on Twitter, over 300 RTs and almost 1,700 likes. Lemire’s had garnered 300 quote tweets, almost 600 RTs, over 2,000 likes, and 1.3M views. Cheney’s had garnered 770 quote tweets, 1,200 RTs, 7,400 likes, and 2.6M views.
By publishing such an inflammatory tweet on Truth Social, Trump was rightly calculating that even people like Holt would help to make his unfiltered words go viral on Twitter, as Trump has consistently done during the period when he still remained banned on Twitter.
It’s like Pavlov’s dogs, pure reflexive behavior at this point: The more incendiary Trump’s tweets, the more quickly journalists rush to disseminate them unfiltered on Twitter.
Remarkably, neither Lemire nor Cheney noted the import of the fact that a habitual liar like Trump was only claiming that he expected to be arrested Tuesday, not that he knew he would be.
In its report on the tweet, NYT noted, even in the subhead, that the timing was unclear, but given that at least one more witness is expected to testify on Monday, a Tuesday arrest is unlikely. It further described that Trump’s team was already in discussions about how to minimize the kind of showy arrest Trump was promising on Truth Social. NYT went on to report how Trump’s team simply guessed the date of his arrest.
His indictment by a Manhattan grand jury is expected, but its timing is unclear.
[snip]
Two hours later, a spokesman issued a statement saying that Mr. Trump had not written his post with direct knowledge of the timing of any arrest,
[snip]
Prosecutors working for Mr. Bragg have signaled that an indictment of Mr. Trump could be imminent. But they have not told Mr. Trump’s lawyers when the charges — expected to stem from a 2016 hush money payment to a porn star — would be sought or an arrest made, people with knowledge of the matter said. At least one more witness is expected to testify in front of the grand jury, which could delay an indictment, the people said.
One of the people said that even if the grand jury were to vote to indict the former president on Monday, a Tuesday surrender was unlikely, given the need to arrange timing, travel and other logistics.
The statement from Mr. Trump’s spokesman did not explain how he had landed on Tuesday as an arrest date. One person with knowledge of the matter said that Mr. Trump’s advisers had guessed that it could happen around then, and that someone might have relayed that to the former president.
A lawyer for Mr. Trump, Susan R. Necheles, said that his post had been based on news reports,
CNN, including Kaitlan Collins, who was among the first to help disseminate this incendiary tweet, later reported on the legal discussions going on inside Trump’s camp.
Trump’s defense team is expected to be notified following any possible indictment and then they would engage in negotiations for surrender and an initial appearance.
Another witness is expected to testify Monday before the grand jury investigating the hush money payments, according to a source familiar with the investigation. It is not clear whether this would be the final witness before it votes on a possible indictment.
Trump’s team has said repeatedly that he will not accept an invitation to testify before the grand jury. But multiple sources familiar with his legal team’s thinking says that if there is an indictment, he would negotiate an agreed upon surrender date with the district attorney’s office.
Trump’s team has been huddled all week planning for various scenarios, including Trump traveling to New York as well as having a remote hearing where he stays at Mar-a-Lago, according to sources familiar with the meetings.
Some members of his legal team are advising Trump to ask for a remote appearance for security reasons should an indictment occur but it is unclear if he would agree to that as he has also discussed with his team wanting to give a statement at the courthouse, sources said.
But before it got to those details, CNN described that the tweet was just a political ploy based off a guess about timing.
The former president has been agitating for his team to get his base riled up and believes that an indictment would help him politically, multiple people briefed on the matter told CNN.
[snip]
Joe Tacopina, an attorney for Trump, later said the former president had based his claims on press reports.
“No one tells us anything which is very frustrating. President Trump is basing his response on press reports,” Tacopina said in a statement to CNN.
In other words, the most newsworthy detail in Trump’s tweet (beyond the incitement) — the day he would be charged — was just made up, a guess based off the same information all the rest of us have. It was nevertheless treated as newsworthy by a slew of journalists needing an excuse to disseminate unfiltered incendiary speech on Twitter. And no one has since gone back to amend their original tweets to note that Trump’s claims to know the date of his arrest were a lie.
Trump’s team simply guessed what day he’ll be charged so as to make a call to fight newsworthy enough for kneejerk journalists to help it go viral for him.
It worked.
It works every single fucking time Trump does this.
Every. Single. Time.
And it’s not just the fact that a bunch of journalists served as willing data mules for Trump’s incendiary tweet, bringing it onto Twitter for him and helping it to go viral in unfiltered form.
It’s the other effect the tweet had on reporting about Trump.
First, everyone completely dropped the significant development in a case that even a number of diehard Republicans think has real gravity, Trump’s refusal to return all the classified documents he stole. That story — a burning story late into Friday — utterly disappeared by Saturday morning. Trump is so good at playing the media that he can effectively just dictate what even CNN and MSNBC will cover. And his tweet managed to make that more damaging investigation — an investigation led by a white man rather than a Black one, and so harder to use to mobilize Trump’s most racist followers — completely disappear from coverage. Journalists who had broken key details about the crime-fraud ruling Friday were instead asked to cover Trump’s tweet on the cable shows on Saturday.
And it wasn’t just cable coverage that Trump’s incendiary tweet managed to dictate. One after another politician — Kevin McCarthy, Mike Pence, Elise Stefanik (who released then deleted multiple drafts before hers was sufficiently dripping in obsequious propaganda) — was forced to comment on the made up news that Trump has a date when he’ll be indicted. Even poor Asa Hutchinson, who was trying hard to launch a Presidential run that didn’t define itself entirely in terms of Trump, was forced to answer multiple questions about Trump’s tweet.
In other words, by releasing the tweet, Trump not only made it the sole focus of cable programming, but made it the leading political question of the day. He made the presidential race about him again, exclusively about him. And in the case of McCarthy and Stefanik — both of whom cling to power by ceaselessly performing their obeisance to Trump — made it a matter of loyalty, a political litmus test that Trump supporters and opponents alike would be required to publicly adhere to.
Finally, all this was done without any mention of the actual facts of the case. All this was done in a way guaranteed to short-circuit rational thought — that’s the point.
To be clear, I don’t know all that many people who are sure this is going to be a substantive indictment, and there are real questions about how it is not time-barred. Perhaps Bragg will surprise us, but even many lefties are skeptical about the legal soundness and wisdom of this indictment.
But the substance of it stems from Trump fucking a sex worker.
He fucked a sex worker then paid her to cover it up. And then, in his efforts to cover that up, Trump engaged in some dodgy corporate accounting. There may be other exacerbating factors, like witness intimidation. But this is about trying to cover up the fact that he fucked a sex worker so it wouldn’t harm his chances of becoming President.
This case involves a crime for which, under Jeff Sessions, SDNY prosecuted Trump’s personal lawyer, Michael Cohen. One reason Trump wasn’t prosecuted as a result is that Bill Barr interfered; Barr even tried to force SDNY to reverse Cohen’s prosecution. And when Cohen went to jail because he refused to cover up Trump’s efforts to cover up fucking a sex worker, Trump cut him off, making him a pariah. Trump’s tweet falsely claimed that multiple prosecutors had deemed this case bullshit when instead he means his own Attorney General engaged in breathtaking corruption to protect him from it.
We don’t know what the indictment includes. But we know it involves fucking a sex worker. And all the journalists repeating Kevin McCarthy’s bullshit comments about investigating this investigation, or Mike Pence’s comments about how measly an indictment this would be, are not making them go on the record about whether they think voters should know if someone is spending significant money — several times what most Trump supporters make in a year — to cover up that they fucked a sex worker. Does Mike Pence, that god-fearing Christian, think a man who paid six figures then engaged in financial fraud to cover up that he fucked a sex worker should be President? Let’s ask him.
That’s not happening, in significant part because Trump has gotten journalists to shed all rationality when reporting on this story. The point is to make this about emotion, not facts, and journalists’ immediate instincts accommodated that.
Because Trump went on offensive, the substance of the indictment — however flimsy or not — has been largely absent from any reporting on the case.
Trump has these journalists trained to act reactively, without taking the time first to figure out whether he was again making shit up (as he was in this tweet). He has these journalists trained to mindlessly help him disseminate antisemitic incitement on platforms he’s not a part of, usually without commentary identifying that’s what he’s doing. Trump is so good at exploiting journalists who know better that he has made them participants in his incitement.
And it could well get people killed.
Updated: Added the circulation numbers for the three tweets disseminating Trump’s incitement.





![[Photo: Emily Morter via Unsplash]](https://www.emptywheel.net/wp-content/uploads/2017/08/Question_EmilyMorter-Unsplash.jpg)