[Get Carter by MGM c. 1971]
[
NB: As always, check the byline before reading. ~Rayne]
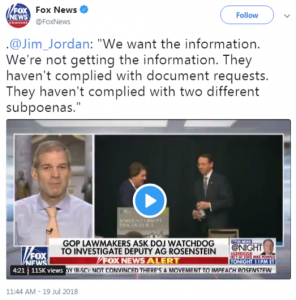
After all the Nunes memo hubbub and the impending Democratic counterpart, erstwhile Trump campaign adviser Carter Page looks sketchier than ever after TIME reported this past Saturday that Page characterized himself as an “informal advisor to the Kremlin” back in 2013.
The FBI warned Page that same year that he was being recruited by spies; Page blew them off. During the following year the FBI obtained a FISA warrant on Page.
Page thought the FBI had retaliated against him — he knew his blow-off was pretty arrogant — but as much as he asked for trouble by saying they should focus on the Boston bombing, then as now, the body of his actions asked for more scrutiny.
Let’s take a step or two back and take a look at the bigger picture surrounding Page; the timeline here is a work in process and will be updated.
2010 — In New York City, Russian spies Igor Sporyshev, Victor Podobnyy, and Evgeny Buryakov began work on several economics-related objectives on behalf of Russia’s SVR ‘Directorate ER’; their efforts started shortly after guilty pleas by members of Russian ‘Illegals’ spy ring and their expulsion.
14 DEC 2012 — Bipartisan Magnitsky Act (Pub.L. 112–208) passed and signed into law.
XX JAN 2013 — Carter Page met Podobnyy in New York City at an Asia Society meeting where the topic was China and Chinese energy development. (specific date TBD).
2013 — Podobnyy and Sporyshev attempted to recruit Page. Special agents with the FBI’s New York Field Office Counterintelligence Division surveilled and investigated spies and Page.
XX JUN 2013 — FBI interviewed Page about his contacts with Russians and cautioned him he was being recruited (specific date TBD).
25 AUG 2013 — In a letter this date sent to an academic press, Page refers to himself as “an informal advisor to the staff of the Kremlin.”
13 APR 2013 — In response to the Magnitsky Act, Russian lawmakers banned 18 Americans from entering Russian Federation, including Preet Bharara, a judge and 12 other DOJ/DEA personnel from the Southern District of New York. Russia also barred adoptions of Russian children by U.S. citizens.
2014 — FBI obtains a FISA warrant to monitor Page‘s communications (specific date TBD).
26 JAN 2015 — Russian spy Buryakov arrested; he had non-official cover as an employee of Vnesheconombank. Igor Sporyshev and Victor Podobnyy had already left the country; both had diplomatic immunity. Case was under U.S. Attorney Preet Bharara’s office for Southern District of New York. Page‘s identity was masked and appeared in the complaint against the spies as “MALE-1.” (See Buryakov, et al complaint (pdf))
DEC 2015 — George Papadopoulos began work for Ben Carson’s presidential campaign as a foreign policy advisor.
Late 2015 — New York’s GOP chair Ed Cox was in contact with Page. It is not clear from Page‘s testimony how this contact occurred; Page uses the word volunteered more than once.
JAN 2016 — Page had at least one meeting with campaign officials based on his contact with Ed Cox; in his HPSCI testimony he said he met Corey Lewandowski. Page was an unpaid adviser. Unclear from testimony if Sam Clovis had Page sign an NDA now or later in the campaign, before the July trip to Moscow.
FEB 2016 — Papadopoulos left Carson’s campaign.
Early MAR 2016 — Sam Clovis recruited Papadopoulos to work for Trump’s campaign as a foreign policy advisor.
06 MAR 2016 — Clovis relayed to Papadopoulos that “a principal foreign policy focus of the campaign was an improved U.S. relationship with Russia,” according to court records related to Papadopoulos’ eventual indictment. Clovis later denied saying this.
14-21 MAR 2016 — Prof. Joseph Mifsud met twice with Papadopoulos; Mifsud brought to the second meeting “Olga” who posed as Putin’s niece.
XX MAR 2016 — Page had breakfast in “March-ish” timeframe with Sam Clovis in Falls Church, VA to discuss NDA and “general foreign policy topics.”
21 MAR 2016 — Page joined Trump campaign as one of five foreign policy advisors, including George Papadopoulos.
MAR-APR 2016 — Dialog continued between Papadopoulos, Mifsud, Olga Vinogradova (referred to as Olga Poloskaya in some earlier reports). [link, link]
24 MAR 2016 — Papadopoulos sends an email copying campaign foreign policy advisers and Sam Clovis, offering to set up “a meeting between us and the Russian leadership to discuss US-Russia ties under President Trump.”
28 MAR 2016 — Article: Donald Trump Hires Paul Manafort to Lead Delegate Effort
26 APR 2016 — Papadopoulos learned the Russians had “dirt” on Hillary Clinton consisting of “thousands of emails.”
05 MAY 2016 — Trump is the presumptive GOP presidential nominee. Page emailed fellow foreign policy adviser Walid Phares and J.D. Gordon, asking them to contact him via cell phone or iMessage, adding “P.S. I forgot to mention that I also have the Middle East staple of [redacted]* as well. So that’s another global connectivity alternative if you want to get in touch there.” (* Believed to be the name of a regionalized communications system. See testimony transcript (pdf).)
16 MAY 2016 — Page sent an email to Walid Phares and J.D. Gordon, suggesting that Trump visit Russia (see testimony transcript (pdf)).
24 MAY 2016 — Page emailed J.D. Gordon: “FYI: At the Newark Sky Club, Delta has a private room when you can have a confidential conversation, but, unfortunately, no such luck at Third-World LaGuardia. So I’ll mostly be on the receive mode, since there are a significant number of people in the lounge. Rather than saying too much, I’ll just refer to the seven points on my list which I sent last night.” (see testimony transcript (pdf)).
26 MAY 2016 — Page emailed J.D. Gordon and another foreign policy team member, Bernadette Kilroy, letting them know he will be speaking at the New Economic School’s commencement alongside Russia’s Sberbank’s chair and CEO (see testimony transcript (pdf)).
27 MAY 2016 — Page may have met Paul Manafort associate Rick Gates at Trump’s North Dakota speech event (see testimony transcript (pdf)).
Early JUN 2016 — Page called Putin “stronger and more reliable than President Obama” and “touted the positive effect a Trump presidency would have on U.S.-Russia relations” according to attendees of a meeting of campaign foreign policy team members with India’s Prime Minister Modi. Modi’s trip was five days long, beginning June 8.
09 JUN 2016 — Trump Tower meeting between Donald Trump Jr. and Natalia Veselnitskaya et al., ostensibly about Russian adoptions.
XX JUN 2016 — After back-and-forth and an initial refusal with Corey Lewandowski, J.D. Gordon, and Hope Hicks, Page finally obtains approval from Lewandowski to travel to Russia as a campaign team member (specific date TBD). In HPSCI testimony there is an exchange about an email he sent asking for feedback about the speech he was going to give in Moscow; same email mentions Russia’s Minister of Economics and Trade Herman Gref was expected to speak at the same event.
30 JUN 2016 — On the Thursday before his Moscow trip Page attended a dinner meeting at the Capitol Hill Club in DC at which both Sen. Jeff Sessions and George Papadopoulos were present and seated next to each other. Page testified to HPSCI this is the last time he saw Papadopoulos, and that he (Page) wasn’t going to Russia as part of the campaign team.
05 JUL 2016 — Page‘s trip to Russia. (05-09 JUL 2016; in his HPSCI testimony he said he left Sunday night, which would have been July 3.)
06 JUL 2016 — In his HPSCI testimony Page admits to meeting Rosneft’s Directer of Investor Relations Andrey Baranov at a Morgan Stanley-hosted Europa football event as well as [redacted] Nagovitsyn* of Gazprom; he also admitted to having a 10-second exchange with Russia’s Deputy Prime Minister Arkady Dvorkovich as well as meeting members of the Duma. (* This may be Oleg Nagovitsyn who in 2014 had been CEO of Gazprom Investproekt, a subsidiary entity; Nagovitsyn has been elevated to General Director of Gazprom if this is the same Oleg.)
07 JUL 2016 — Page gave a speech at New Economic School; his speech is critical of U.S. foreign policy. He testified that the school paid for his expenses. (video)
08 JUL 2016 — Page attended and gave commencement speech at New Economic School graduation. (video) Page avoided answering journalists’ questions both days regarding officials Page may have/will meet with in Russia. Page emailed campaign advisers Tera Dahl and J.D. Gordon, telling them he would send them “a readout soon regarding some incredible insights and outreach I’ve received from a few Russian legislators and senior members of the Presidential administration here.”
14 JUL 2016 — Page praises fellow foreign policy advisers and campaign team members J.D. Gordon, Walid Phares, Joseph Schmitz, Bert Mizusawa, Chuck Kubic, and Tera Dahl for their work changing the GOP platform on Ukraine.
18-21 JUL 2016 — Page spoke with Russian Ambassador Sergey Kisylak during the Global Partners in Diplomacy event associated with the RNC Convention in Cleveland (specific date TBD).
19 JUL 2016 — Former MI6 intelligence officer Christopher Steele wrote a memo about Page‘s July trip to Moscow. Steele’s intelligence said Page met with Rosneft’s Igor Sechin and Russian Internal Affairs minister Igor Diveykin.
U.S. received intelligence that Page met with Igor Sechin, Putin associate, former Russian deputy prime minister, and executive chairman of Rosneft, but it isn’t clear whether this intelligence is based on Steele’s dossier alone and/or if disinformation involved.
After 22 JUL 2016 — Australia’s Ambassador to the U.S. Joe Hockey disclosed to the FBI that diplomat Alexander Downer learned from George Papadopoulos the Trump campaign had “dirt” on HRC in the form of emails.
XX JUL 2016 — Page had dinner alone with Sam Clovis some time after the July trip to Moscow.
05 AUG 2016 — Article: Trump adviser’s public comments, ties to Moscow stir unease in both parties; includes a profile of Page. Hope Hicks characterized Page as “informal policy adviser.”
19 AUG 2016 — Paul Manafort resigns from the campaign two days after Trump’s first security briefing. Steve Bannon assumes Manafort’s role for the campaign.
26 AUG 2016 — Sen. Harry Reid sent a letter to FBI Director James Comey asking for the investigation of Russian hacking and influence on the 2016 election with publication of findings. Reid cited the example of an unnamed Trump adviser “who has been highly critical of U.S. and European economic sanctions on Russia, and who has conflicts of interest due to investments in Russian energy conglomerate Gazprom, met with high-ranking sanctioned individuals while in Moscow in July 2016…” (link)
XX AUG 2016 — Page said he sold his ADR shares in Gazprom this month, approximately five months after joining the campaign; it’s not clear whether this sale happened before or after Sen. Reid’s letter (see written testimony (pdf)).
XX AUG 2016 — Page traveled to Hungary and met with the ambassador to the US; the ambassador had already met Page at the RNC convention. They discussed U.S.-Russia policy as it affected Hungary — “in general,” according to Page‘s testimony.
23 SEP 2016 — Article: U.S. intel officials probe ties between Trump adviser and Kremlin.
25 SEP 2016 — Page wrote to Comey and asked him to end the investigation into his trip to Russia (see written testimony).
26 SEP 2016 — Page left Trump campaign.
Mid to Late SEP 2016 — After discussing the matter with Fusion GPS’ Glenn Simpson, Christopher Steele metwith the FBI in Rome to share what he had learned about the Trump campaign and related Russian efforts. Steele was concerned there was a crime in progress; some of his research shared included information about Page‘s interactions with key Russians during his July trip.
21 OCT 2016 — FISA warrant on Page obtained.
24-OCT-2016 — Page did an interview with Russian media outlet RT on its Going Underground program. Program host and Page characterized Page‘s status as “on leave” from the campaign. Page‘s written testimony shared that Wikileaks and leaked emails “tangentially came up.” (video, uploaded to YouTube on 29-OCT-2016.)
08 NOV 2016 — Election Day.
08 DEC 2016 — Page took another trip to Russia; Arkady Dvorkovich stopped by a dinner Page attended and said hello according to Page‘s testimony (specific date TBD). Page also met Shlomo Weber again; he had lunch with Andrey Baranov, a bank analyst with Bank of America/Merrill Lynch, and a third person whose names were redacted at Page‘s request. He had a laptop with him at the lunch which he said he used to share his speech and slides for another academic presentation. The Kremlin’s spokesperson, Dmitri Peskov, said there were no plans to contact Page yet managed to see Page just before a television interview.
XX DEC 2016 — On the return leg to the U.S., Page stopped in London to attend an energy conference. While in London he met with a Russian national, Sergey Yatsenko, in London on return from Moscow; they talked about opportunities in Kazahkstan related to the country’s privatization process and the sovereign wealth fund, Samruk Kazyna. They were joined by the Kazahk ambassador to the U.K. and an aide.
10 JAN 2017 — BuzzFeed published 35 pages of the dossier Steele prepared for Orbis under contract to Fusion GPS.
Mid JAN 2017 — Jones Day LLP, White House counsel Don McGahn’s former law firm, communicated with Page, instructing him not to depict himself as a representative of the campaign. Steve Bannon conveyed a similar message by text to Page.
XX JAN 2017 — In an interview with ABC News, Page said he didn’t meet with any Russian officials on behalf of Trump campaign or with Igor Sechin (specific date not clear in ABC’s report).
18 JAN 2017 — Deadline, FISA renewal required (before inauguration).
19 JAN 2017 — Article: Intercepted Russian Communications Part of Inquiry Into Trump Associates; Page along with Paul Manafort and Roger Stone have become subjects of an investigation.
20 JAN 2017 — Inauguration Day.
31 JAN 2017 — Trump nominated Maryland’s U.S. Attorney Rod Rosenstein as Deputy Attorney General.
31 JAN 2017 — Page told ABC News’ Brian Ross he never talked to anyone in the Kremlin about the campaign during his July trip, “not one word.”
15 FEB 2017 — Interview: Former Trump adviser says he had no Russian meetings in the last year
JUDY WOODRUFF:
Did you have any meetings — I will ask again — did you have any meetings last year with Russian officials in Russia, outside Russia, anywhere?
CARTER PAGE:
I had no meetings, no meetings.
I might have said hello to a few people as they were walking by me at my graduation — the graduation speech that I gave in July, but no meetings.
02 MAR 2017 — Interview: Page: ‘I don’t deny’ meeting with Russian amb.; Page admitted meeting Russia’s Ambassador Kislyak during the campaign.
04 MAR 2017 — Corey Lewandowski told Fox News, “I never met Carter Page.”
11 MAR 2017 — Preet Bharara fired by USAG Jeff Sessions.
11 MAR 2017 — Page sent a letter to the HPSCI asking to be interviewed in a public hearing. His letter coincided with letters from Paul Manafort and Roger Stone who both volunteered to be interviewed.
03 APR 2017 — ABC News and BuzzFeed contacted Page about his role as MALE-1 in Buryakov et al spy ring case ((see written testimony (pdf))
13 APR 2017 — Page told ABC News’ George Stephanopoulos that he “said hello briefly to one individual, who was aboard member of the New Economic School where I gave my speech” during his July 2016 to Moscow. He also hedged as to whether he had any discussion of sanctions while in Russia.
05 APR 2017 — Evgeny Buryakov was released from prison on March 31 and expelled from the U.S. days later; he had been credited with time served while in custody against his 2.5 year sentence. His deportation shortened his sentence by a couple of months.
~19 APR 2017 — Deadline, FISA renewal required (specific date TBD).
25 APR 2017 — Rod Rosenstein confirmed by Senate as Deputy Attorney General.
28 APR 2017 — Senate Intelligence Committee sent a letter to Page along with Mike Flynn, Paul Manafort, and Roger Stone asking for records related to the campaign, including a “list of all meetings between you and any Russian official or representative of Russian business interests which took place between June 16, 2015, and Jan. 20, 2017.”
05 MAY 2017 — Senate Intelligence Committee chair and vice chair sent a joint statement to Page to insist on his cooperation with their investigation.
09 MAY 2017 — FBI Director James Comey fired.
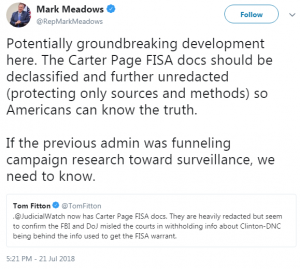
21 MAY 2017—Page requested appealed to the DOJ, FBI, NSA for disclosure of “information, applications and other materials related to my illegitimate FISA warrant” (see written testimony (pdf)).
~18 JUL 2017 — Deadline, FISA renewal required (specific date TBD).
04 OCT 2017 — HPSCI issued a subpoena to Page.
10 OCT 2017 — Page informed the Senate Intelligence Committee he would plead the Fifth Amendment and not testify in front of the SIC.
30 OCT 2017 — Excerpt from interview with MSNBC’s Chris Hayes suggests Page expected House Speaker Paul Ryan to release the FISA warrant documentation (video, about 06:57):
HAYES: Did you bring an attorney to you when you spent five hours before the Senate?
PAGE: Nope. Nope. I’m very, very open and happy to give all the information I can. In the interest of really getting the truth out there, because I think when the truth comes out, when Speaker Paul Ryan says the FISA warrant or the details about the dodgy dossier and what happened and all this documents around that is going to be released, that’s what I’m really excited about. And I think the truth will set a lot of people free.
02 NOV 2017 — In testimony submitted to the House Permanent Select Committee on Intelligence, Page said he briefly met Russian Deputy Prime Minister Arkady Dvorkovich during his July trip. Page pleaded the Fifth Amendment on some of the materials responsive to the HPSCI’s subpoena.
14 NOV 2017 — Jeff Sessions testified before the House Judiciary Committee; he said he did not remember seeing Page at the June 30, 2016 dinner with campaign team members, nor did he recall any communications about Page‘s trip to Moscow.
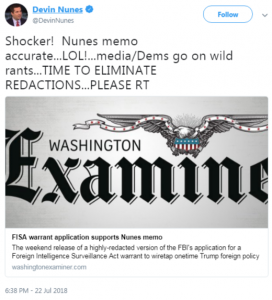
Again, this is not a complete timeline of Trump-Russia events, let alone a complete timeline of everything Carter Page. It captures some key points from just before the FBI became aware of Carter Page through the release of the Nunes’ memo Friday last week.
From a comprehensive meta level, the push operation to release the Nunes memo — driven in part with help from Russian bots promoting #ReleaseTheMemo, complementing Page’s request for the FISA warrant documentation — looks less like an effort to remove Robert Mueller as special counsel or Rod Rosenstein as U.S. Deputy AG.
As others have suggested, Page looks like an expendable mule and/or a decoy — a perfect fit for a perfect useful idiot.
The entire picture reflects a more comprehensive effort to attack the USDOJ apart from Jeff Sessions, and to undermine or obscure the opposition research process which included the Steele dossier.
And it looks more like Devin Nunes aided Putin’s continued attack against the U.S.’ Magnitsky Act, attempting to undermine law enforcement charged with executing this public law.
For all the concern that Page and other campaign team members might have talked about the sanctions with Russia, the Magnitsky Act is lost in the media buzz.
There are quite a few oddities about Page which should cause the average Joe to take pause. Why did Page join the campaign in March 2016 when Trump wasn’t the presumptive nominee until the first week of May after the Indiana primary? Did he just show up at the campaign’s doorstep via Ed Cox on his own or was he recruited/encouraged? Why wasn’t Page vetted more thoroughly by the campaign?
And why when he joined the campaign was he not expected to have already eliminated any conflicts of interest like his Gazprom ADRs? The financial conflict made Page an easily compromised mark even though both campaign and administration didn’t and don’t give a fig about ethics. It’s not clear how Page earns his keep; he testified he was living off his savings. Did he sell his ADRs only because he was low on cash? In other words, was he at risk for financial compromise?
(An aside: with Page’s relationships to Russian oil and gas community members, did Page buy or sell his ADRs on what might have been insider information? He didn’t do well if he sold in August 2016 but it’s not clear when and at what price he bought the ADRs to begin with.)
How did a guy with such thin credentials — he was awarded his doctorate in 2012 after his thesis was twice rejected — end up speaking not just once at the New Economic School but twice, giving the commencement speech? Not to mention his flaky personal style spies Podobnyy and Sporyshev noted years earlier. What was in his speeches that students, faculty, and distinguished guests alike needed to hear? Did someone at the New Economic School ‘review’ an electronic or hardcopy version of the speeches in advance? This is a question the HPSCI attempted to ask but didn’t receive a clear answer. Did a member of Russia’s government ‘review’ the speeches?
Why was there such a lag between Page’s trip to Russia and the FISA warrant given Page’s history?
Some pieces in this puzzle hint at other possible connections. Recall that Rosenstein — who has been involved in the FISA warrants since Comey was fired — was the US Attorney for Maryland. Pioneer Point, one of Russia’s compounds confiscated December 29, 2016 under sanctions related to hacking the DNC, is located on the water in Maryland.
Maryland was also home to a Manafort-related business SCG raided on May 11 last year. Has Rosenstein been kept preoccupied so that he would not be involved in anything related to either Pioneer Point or SCG? Who (if anyone) was nominated to replace Rosenstein in Maryland? Has the pressure on Rosenstein been two-fold — not just to discourage another extension of the FISA warrant on Page, but to keep him from looking too closely in what was once his backyard?
Key events from George Papadopoulos’ tenure with the campaign were included in the timeline for comparison between two foreign policy advisers working for the same campaign. What marching orders did these two receive from Clovis or other senior campaign team members? They’re off doing their own things but both generating trouble at the same time. Page’s open activities drew media attention; Papadopoulos’ efforts were not as visible to the public. Was this intentional? Why did the campaign need not one but two foreign policy advisers with fossil fuel-based energy backgrounds mingling with Russians? Were they both proof-of-concepts establishing back channel communications, testing approaches to see which would be more successful? Were there any other attempts at back channels via campaign team members?
And while we’ve been focused on these two advisers, at least three others continued their work for the campaign and possibly into the transition. What were they doing?
It’s worth reading the HPSCI transcript of Page’s oral and written testimony. He’s a lousy writer; his work borders on irrational. His oral responses during the HPSCI hearing are as bad if not worse. Of particular concern is his repetitive use of certain arguments and phrases which have been use at times by online provocateurs.
Other persons and issues aside, consider this particular excerpt in a report published about a month before the FBI obtained a FISA warrant on Page:
Page came to the attention of officials at the U.S. Embassy in Moscow several years ago when he showed up in the Russian capital during several business trips and made provocative public comments critical of U.S. policy and sympathetic to Putin. “He was pretty much a brazen apologist for anything Moscow did,” said one U.S. official who served in Russia at the time.
How could the FBI not have requested a FISA warrant given what we the public already knew about Carter Page once he left for Moscow last July?

![[Photo: Emily Morter via Unsplash]](https://www.emptywheel.net/wp-content/uploads/2017/08/Question_EmilyMorter-Unsplash.jpg)