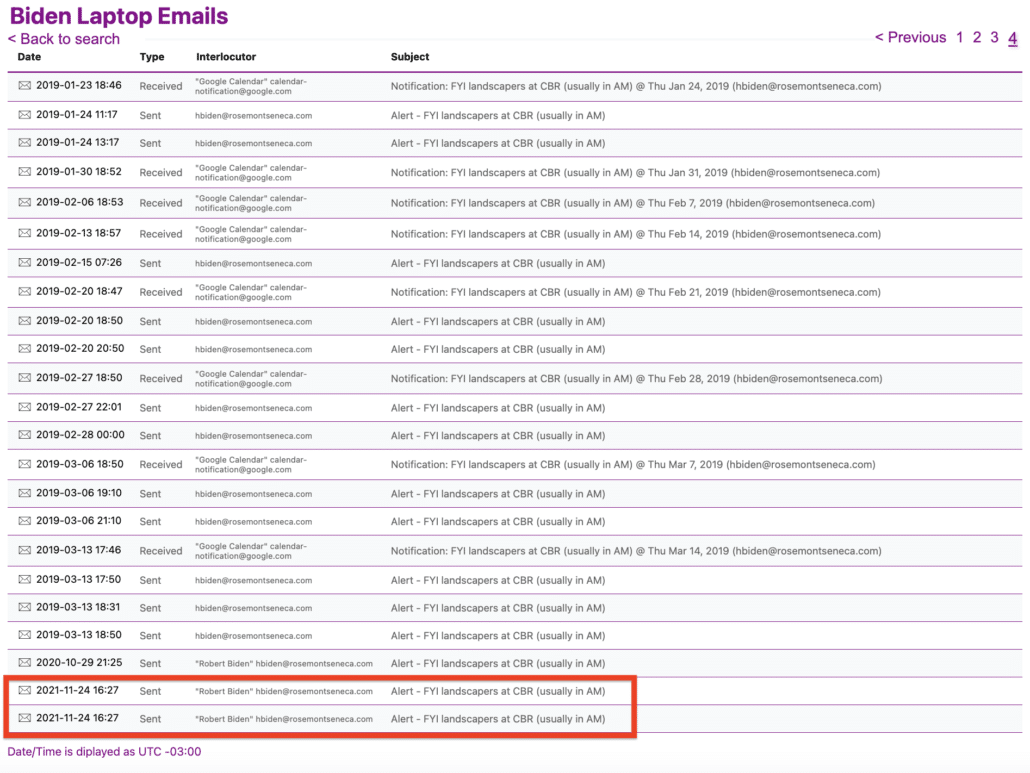
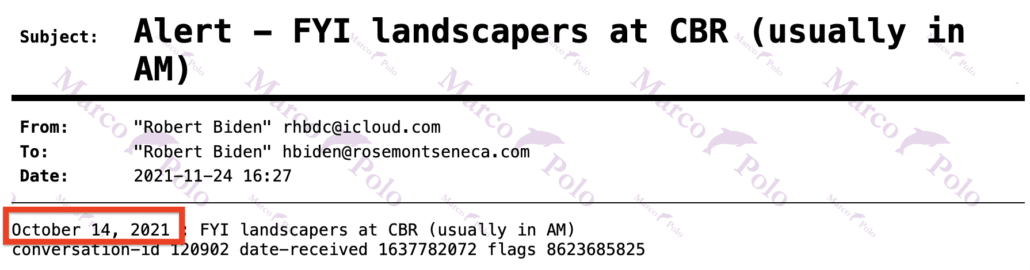
White Man’s Burden: Trump Is Failing Six of Ten Metrics on His Own Open Book Test
One reason I laid out what Stephen Miller and Trump’s other sad little advisors think they’re doing in their National Security Strategy is because once you do that, it makes it even more clear that their overestimation of their own competence is dooming the United States.
Fully seven pages of the short (33 pages as compared to Trump’s 68-page 2017 NSS and Sleepy Joe Biden’s 48-page 2022 one) document blather about what it is trying to accomplish: two pages announcing the adoption of utilitarianism over values, two laying out what the US should want, another laying out what Trump thinks the US wants from the world, and two more laying out what means the US has to get there.
This is the work of a bunch of men who imagine they are competent telling everyone who came before them that they were doing things wrong.
Yet by laying all that out — by writing down what they imagine competence would deliver — they make it clear how badly they’re screwing up.
Effectively, Donald Trump has already done significant, if not grave, damage to six of the ten things that Trump claims America wants:
- Continued survival of US sovereignty
- Protect the country from human trafficking, foreign influence, propaganda, and espionage
- “A resilient national infrastructure that can withstand natural disasters, resist and thwart foreign threat”
- The most dynamic economy
- A robust industrial base
- Unrivaled soft power that “believe[s] in our country’s inherent greatness and decency”)
Start with the obvious ones.
Donald Trump and Marco Rubio and Elon Musk spent the first six months of this Administration trashing America’s soft power. These boys seem to imagine they can replace it with something that “believe[s] in our country’s inherent greatness and decency.” Except no one else will believe in American decency after it suddenly withdrew funding that resulted in the deaths of 600,000 people, two thirds of them children. People won’t trust you after you renege on paying the bills.
Or consider that 2nd bullet, which reads this way:
We want to protect this country, its people, its territory, its economy, and its way of life from military attack and hostile foreign influence, whether espionage, predatory trade practices, drug and human trafficking, destructive propaganda and influence operations, cultural subversion, or any other threat to our nation.
Of course, Trump claims to combat drug trafficking with his murderboat killings, even while he lets increasingly major drug criminals out of prison.
As for the rest? On her first day in office, the Attorney General stopped policing foreign influence, destructive propaganda, and influence operations; then Kristi Noem piled on by shutting down other programs combatting foreign influence and propaganda.
And, as an endless stream of stories reveal, both Pam Bondi and Noem have reassigned those who would hunt spies and human traffickers to go hunt undocumented grannies and day laborers instead.
Worse, the priority on weaponization has resulted in the loss of those people. Just the firing of a bunch of people who took a knee during the George Floyd protests to deescalate resulted in the firing of a counterintelligence Deputy Assistant Director and a supervisor.
a. In late March 2025, Plaintiff Jane Doe 5 was informed that she was being removed at the direction of Defendant Patel from her position at FBI Headquarters as a Deputy Assistant Director for the FBI overseeing counterintelligence at the direction of Defendant Patel because she kneeled on June 4, 2020. Plaintiff Jane Doe 5 had been specifically identified in then-Representative Gaetz’s letter. Plaintiff Jane Doe 5 retained her SES status but was demoted to a Section Chief position.
b. In April 2025, Plaintiff Jane Doe 6 was serving as the Legal Attache for the FBI based overseas along with her family. In that capacity, Plaintiff Jane Doe 6 had previously provided briefings to Defendant Patel with which he said he was very impressed. Nevertheless, on April 3, 2025, an FBI senior leader informed her that she was being removed from her term position in the Senior Executive Service to a non-Senior Executive Service position, abruptly uprooting her entire family and resulting in a significant pay decrease. The FBI senior leader informed Plaintiff Jane Doe 6 that Defendant Patel had indicated that his mind was made up and could not be changed.
c. In April 2025, Plaintiff Jane Doe 9 was demoted from her position as a supervisor overseeing all FBI ransomware and malware investigations. An FBI senior leader informed her that the demotion came straight from top level FBI leadership.
d. In April 2025, Defendant Patel directed the removal of Plaintiff Jane Doe 8 from her position supervising a counterintelligence squad.
There were even greater losses in DHS’ purges.
That’s part of the problem with bullet 3: The NSS’ grand plan to make America’s infrastructure more resilient. Along with gutting those who protect against foreign influence, Noem has gutted those who protect against hacking and natural disasters.
As for bullets 4 and 5? Trump’s trade war has had the opposite effect than he claimed it would, with historic layoffs and struggling manufacturing and small businesses.
Again, Trump did affirmative damage rather than achieving his goals.
Then there’s the question of sovereignty.
For all its yapping about America First, the NSS doesn’t deal with the way that Trump has been trading away America’s advantages to any rich foreigner with millions in cryptocurrency. Just yesterday, for example, Trump approved the sale of one of Nvidia’s most complex chips to China on the same day Houston’s US Attorney rolled out showy prosecutions for Chinese men accused of illegally exporting those very same chips.
“The United States has long emphasized the importance of innovation and is responsible for an incredible amount of cutting-edge technology, such as the advanced computer chips that make modern AI possible,” said Assistant Attorney General for National Security John A. Eisenberg. “This advantage isn’t free but rather the result of our engineers’ and scientists’ hard work and sacrifice. The National Security Division, along with our partners, will vigorously enforce our export-control laws and protect this edge.”
Alan Hao Hsu aka Haochun Hsu, 43, Missouri City, and his company, Hao Global LLC, both pleaded guilty to smuggling and unlawful export activities Oct. 10.
According to now unsealed court documents, between October 2024 and May 2025, Hsu and others knowingly exported and attempted to export at least $160 million worth of export-controlled Nvidia H100 and H200 Tensor Core graphic processing units (GPUs).
Trump already authorized the export of even more complex chips to Saudi Arabia and Abu Dhabi, the same sovereigns backing Paramount’s hostile bid to take over a big chunk of the US entertainment industry (that’s after China’s Tencent was dropped).
And these are just the areas where Trump has most obviously failed his own standards.
He built in a gimme in those standards he actually accomplished by claiming to want nuclear deterrent but then stating, falsely, that the Golden Dome would deliver such a deterrent.
We want the world’s most robust, credible, and modern nuclear deterrent, plus next-generation missile defenses—including a Golden Dome for the American homeland—to protect the American people, American assets overseas, and American allies.
Mark Kelly explained how unrealistic this effort was months ago.
And as for the hope that the rest of the world will use American technology, one of the things Trump wants from the rest of the world?
We want to ensure that U.S. technology and U.S. standards—particularly in AI, biotech, and quantum computing—drive the world forward.
As for those chips Trump cleared for sale, China is limiting their use.
As for American biotech, the rest of the world is instead importing America’s scientists who’ve been defunded as part of Trump’s anti-intellectual purges.
There’s plenty else in this NSS (such as other references to America’s technical superiority) where the boys aspire to have skills they affirmatively destroyed.
As such, the NSS isn’t so much a strategy (a word they scare quote when they define it): it’s a confession that these self-declared competent people are failing to meet their own standards.