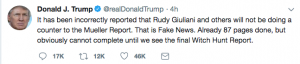
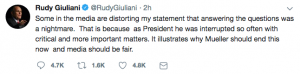
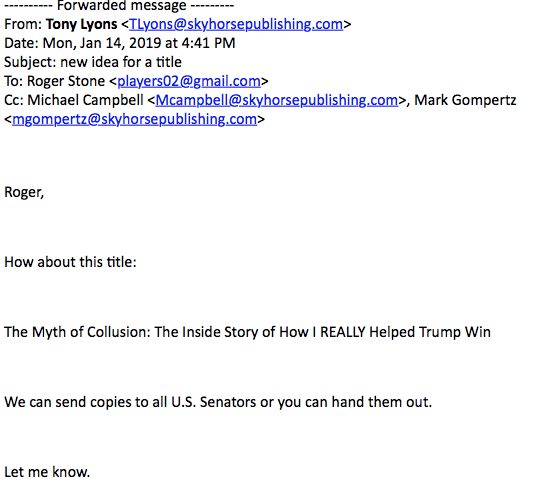
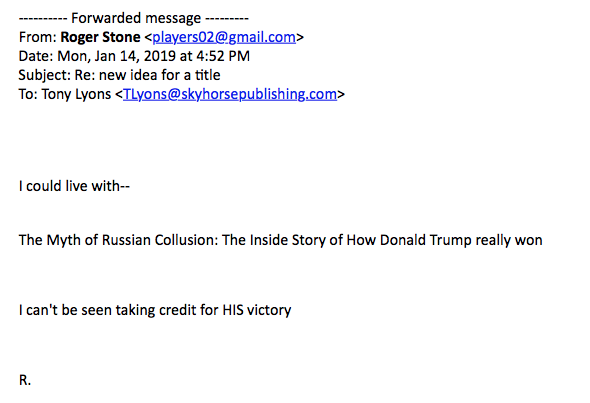
Towards the end of the day on January 14, amid a three day stint writing the 3,000 word introduction that would justify reissuing his 2016 book, Making of the President, Roger Stone rejected the title suggested by his publisher, Skyhorse Publishing, “The Myth of Collusion; The Inside Story of How I REALLY Helped Trump Win.” He suggests instead, “The Myth of Collusion; The Inside Story of How Donald Trump really won,” noting, “I really can’t be seen taking credit for HIS victory.”
That’s the title the book now bears.
That exchange — and a number of other ones revealed in the correspondence Stone’s lawyers submitted in an attempt to persuade Judge Amy Berman Jackson they weren’t just trying to get publicity for the book when asking for a “clarification” regarding the book on March 1 — raises interesting questions about why he reissued the book how and when he did.
On one level, the explanation is easy: his publishers expected the original book, Making of the President, would be a big seller. They made 100,000 copies when it first came out in January 2017. The book flopped.
So in November 2018, Stone’s rising notoriety — and more importantly, the increased polarization surrounding the Mueller probe — provided an opportunity to recoup some of the losses on the hardcover. At that level, the reissue needs no explanation other than the obvious formula publishers use to make money: Exacerbate and profit off of controversy.
But that doesn’t explain why the project started on November 15, 2018 rather than any time in the year and a half earlier, when Skyhorse would have all those same goals. Nor does it explain how Stone went from expressing no interest in the project to rushing it through quickly in mid-December.
Given the timeline of events and a few stray comments in the correspondence (as I laid out here, Stone has probably withheld at least eight exchanges with his publisher from the court submission, after letting the publisher review what correspondence was there), I think he’s got several other purposes.
As noted below, Skyhorse first approached Stone on November 15, in the wake of the Democrats winning the House in midterm elections. On January 14, Skyhorse president Tony Lyons suggests that “We can send copies [of the book] to all U.S. Senators.” Those two details suggest that Skyhorse intended the book, on top of the obvious financial incentives, to capitalize on the general right wing campaign to discredit the Mueller investigation in an effort to stave off impeachment.
The delay between the time — on November 15 — when Skyhorse first pitched the reissue and the time — mid-December — when Stone and his lawyer, Grant Smith, start engaging in earnest suggests two other factors may be in play.
First, while Stone had been saying that Mueller would indict him for months, the aftermath of the Corsi “cooperation” starting on November 26 made Stone’s jeopardy more immediate. Yes, Corsi’s attempt to make his own cooperation useless may have delayed Stone’s indictment, but the details Corsi described to be in his own forthcoming Mueller-smearing book made it clear the Special Counsel believed Stone had successfully affected the timing of the release of the John Podesta emails on October 7, 2016, in a successful attempt to dampen some of the impact of the Access Hollywood video.
That’s why the specific content of the new introduction Stone finished on January 13, 2019, which he notes is more substantive than Skyhorse initially planned, is of interest. In the introduction, Stone:
- Describes learning he was under investigation on January 20, 2017
- Discounts his May 2016 interactions with “Henry Greenberg” — a Russian offering dirt on Hillary Clinton — by claiming Greenberg was acting as an FBI informant
- Attributes any foreknowledge of WikiLeaks’ release to Randy Credico and not Jerome Corsi or their yet unidentified far more damning source while disclaiming any real foreknowledge
- Gives Manafort pollster, Tony Fabrizio, credit for the decision to focus on Michigan, Wisconsin, and Pennsylvania in the last days of the election
- Mentions Alex Jones’ foreboding mood on election night
- Accuses Trump of selling out to mainstream party interests, choosing Reince Preebus over Steve Bannon
- Blames Jeff Sessions for recusing from the Russian investigation
- Harps on the Steele dossier
- Dubiously claims that in January 2017, he didn’t know how central Mueller’s focus would be on him
- Suggests any charges would be illegitimate
- Complains about his financial plight
- Falsely claims the many stories about his associates’ testimony comes from Mueller and not he himself
- Repeats his Randy Credico cover story and discounts his lies to HPSCI by claiming his lawyers only found his texts to Credico after the fact
- Suggests Hillary had ties to Russia
- Notes that Trump became a subject of the investigation after he fired Jim Comey
Some of this is fairly breathtaking, given that Corsi’s theatrics had long ago proven Stone’s Credico cover story to be false. But of course, by the time Stone wrote this, he knew that he was at risk at a minimum for false statements charges, so he was stuck repeating the long-discredited HPSCI cover story. Which may be why his attorney, Grant Smith, provided some edits of the introduction on January 15 (something Smith should have but did not disclose in the filing to Amy Berman Jackson). Stone will now be stuck with this cover story, just as Corsi is stuck with the equally implausible cover story in his book.
But to some degree, that’s clearly one purpose this introduction serves: to “retake the narrative” (as Skyhorse’s editor Mike Campbell described it when pitching Stone on the project) and try to sell at least frothy right wingers on his cover story.
Another is to make money. Stone’s first response — over three weeks after Skyhorse first floated the paperback project — was to complain that because the publisher printed way too many copies of the hard cover, which was done as part of a joint venture, he made no money off the deal (a claim that Skyhorse corrects, slightly, in the follow-up). That’s why Skyhorse ended the joint venture: to mitigate the risk to Stone and by doing so to convince him to participate in the project.
More interesting — given the January stories suggesting that Jerome Corsi may have gotten a six month severance deal as part of a bid to have him sustain Stone’s cover story — is that Stone seemingly reversed his opinion about doing the project between December 9, when he said he was uninterested, and Monday, December 17, when Smith said they were ready to move forward, because Stone urgently needed money by the next day to pay off his collaborators in the book project.

From the public record, I’m actually fairly confused about who these collaborators are. A number of them would be the witnesses interviewed by Mueller’s grand jury.
But the book itself — because it retains the Acknowledgements section from the original — thanks Corsi third, after only Richard Nixon and Juanita Broaddrick, and lauds what Stone calls Corsi’s “investigative report[ing].”

Remember: A key product of that “investigative reporting” was the report Stone asked Corsi to write on August 30, 2016, to invent a cover for why he was discussing John Podesta and Joule Holdings in mid-August 2016. Things had already gone to hell by the time this book was released in e-book form on February 18 and they (appear to) have continued to disintegrate since then.
But I am very interested in who Stone paid off with that urgently wired payment in December. And because it happened before Stone was raided on January 25, Mueller likely knows the answer, if he didn’t already.
Which brings me to the last likely purpose of this paperback, one that goes to the core of whether Stone was trying to publicize its release with his little stunt about “clarifying” whether or not it would violate his gag.
Stone’s decision to do this paperback came not long after Stone repeated a formula other Trump associates bidding for a pardon have engaged in: promise publicly you won’t testify against Trump, then deny you’re asking for a pardon.
[T]here’s no circumstance under which I would testify against the president because I’d have to bear false witness against him. I’d have to make things up and I’m not going to do that. I’ve had no discussion regarding a pardon.
The next day, Trump let Stone and all the world know he had gotten the message.

Every person who is bidding for a Trump pardon is doing whatever they can — from reinforcing the conspiracy theories about the genesis of the investigation, to declaring ABJ found “no collusion” minutes after she warned lawyers not to make such claims, to sustaining embarrassingly thin cover stories explaining away evidence of a conspiracy — to hew to Trump’s strategy for beating this rap. Indeed, the Michael Cohen lawsuit claiming Trump stopped paying promised legal fees as soon as Cohen decided to cooperate with prosecutors suggests Trump’s co-conspirators may be doing this not just in hopes of a pardon, but also to get their legal fees reimbursed.
Which brings me back to Stone’s concern that the title, “The Myth of Collusion; The Inside Story of How I REALLY Helped Trump Win” would suggest he was taking credit for Trump’s win.
There are two reasons why such an appearance might undermine Stone’s goals for the book.
Stone has loudly claimed credit for his role in Trump’s victory, particularly as compared Steve Bannon. And evidence that will come out in his eventual trial will show him claiming credit, specifically, for successfully working with WikiLeaks.
Of course, Trump is a narcissist. And the surest way to piss him off — and in doing so, ruin any chance for a pardon — is to do anything to suggest he doesn’t get full credit for all the success he has in life.
But there may, in fact, be another reason Stone was quick to object to getting credit for all the things he did to get Trump elected.
At least according to Jerome Corsi, Stone, on indirect orders from Trump, took the lead in trying to learn about and with that knowledge, optimize the release of the materials Russia stole from Hillary’s campaign. If non-public details about what Stone did — or even the public claim that Stone managed the timing of the Podesta email release — had a bigger impact on the election outcome than we currently know, then Stone would have all the more reason to want to downplay his contribution.
That is, if Stone’s efforts to maximize the value of Russia’s active measures campaign really were key, then the last thing he’d want to do is release a paperback crowing about that.
Of course, because of the boneheaded efforts of his lawyers, his concerns about doing so are now public.
Update: I’ve corrected my characterization of Skyhorse. They’re not ideological. But they do feed off of controversy.
October 30, 2018: ABC reports that Stone hired Bruce Rogow in September, a First Amendment specialist who has done extensive work with Trump Organization.
October 31, 2018: Date Corsi stops making any pretense of cooperating with Mueller inquiry.
November 6, 2018: Democrats win the House in mid-term elections.
November 7, 2018: Trump fires Jeff Sessions, appoints Big Dick Toilet Salesman Matt Whitaker Acting Attorney General.
November 8, 2018: Prosecutors first tell Manafort they’ll find he breached plea deal.
November 12, 2018: Date Corsi starts blowing up his “cooperation” publicly.
November 14, 2018: Date of plea deal offered by Mueller to Corsi.
November 15, 2018: Mike Campbell pitches Stone on a paperback — in part to ‘retake the narrative — including a draft of the new introduction.
November 18, 2018: Jerome Corsi writes up his cover story for how he figured out John Podesta’s emails would be released.
November 20, 2018: After much equivocation, Trump finally turns in his written responses to Mueller.
November 21, 2018: Dean Notte reaches out to Grant Smith suggesting a resolution to all the back and forth on their joint venture, settling the past relationship in conjunction with a new paperback.
November 22, 2018: Corsi writes up collapse of his claim to cooperate.
November 23, 2018: Date Mueller offers Corsi a plea deal.
November 26, 2018: Jerome Corsi publicly rejects plea deal from Mueller and leaks the draft statement of offense providing new details on his communications with Stone.
November 26, 2019: Mueller deems Paul Manafort to be in breach of his plea agreement because he lied to the FBI and prosecutors while ostensibly cooperating.
November 27, 2018: Initial reports on contents of Jerome Corsi’s book, including allegations that Stone delayed release of John Podesta emails to blunt the impact of the Access Hollywood video.
November 29, 2018: Michael Cohen pleads guilty in Mueller related cooperation deal.
December 2, 2018: Roger Stone claims in ABC appearance he’d never testify against Trump and that he has not asked for a pardon.
December 3, 2018: Trump hails Stone’s promise not to cooperate against him.
December 9, 2018: Stone replies to Campbell saying that because he never made money on Making of the President, he has no interest.
December 13, 2018: Tony Lyons and Grant Smith negotiate a deal under which Sky Horse would buy Stone out of his hardcover deal with short turnaround, then expect to finalize a paperbook by mid January. This is how Stone gets removed from the joint venture — in an effort to minimize his risk.
December 14, 2018: Mueller formally requests Roger Stone’s transcript from House Intelligence Committee.
December 17, 2018: Smith, saying he and Stone have discussed the deal at length, sends back a proposal for how it could work. This is where he asks for payment the next day, to pay someone off for work on the original book.
For some reason, in the ensuing back-and-forth, Smith presses to delay decision on the title until January.
December 19, 2018: It takes two days to get an agreement signed and Stone’s payment wired.
December 20, 2018: HPSCI votes to release Stone’s transcript to Mueller.
January 8, 2019: Paul Manafort’s redaction fail alerts co-conspirators that Mueller knows he shared polling data with Konstantin Kilimnik.
January 13, 2019: Stone drafts new introduction, which he notes is “substantially longer and better than the draft sent to me by your folks.” He asks about the title again.
January 14, 2019: Stone sends the draft to Smith and Lyons. It is 3386 words long. Lyons responds, suggesting as title, “The Myth of Collusion; The Inside Story of How I REALLY Helped Trump Win.” Lyons also notes Stone can share the book with Senators.
Stone responds suggesting that he could live with, “The Myth of Collusion; The Inside Story of How Donald Trump really won,” noting, “I really can’t be seen taking credit for HIS victory.”
By end of day, Skyhorse’s Mike Campbell responds with his edits.
January 15, 2019: The next morning, Smith responds with his edits, reminding that Stone has to give final approval. Stone does so before lunch. Skyhorse moves to working on the cover. Late that day Campbell sends book jacket copy emphasizing Mueller’s “witch hunt.”
January 15, 2019: Mueller filing makes clear that not all Manafort’s interviews and grand jury appearances involve him lying.
January 16, 2019: Tony Lyons starts planning for the promotional tour, asking Stone whether he can be in NYC for a March 5 release. They email back and forth about which cover to use.
January 18, 2019: By end of day Friday, Skyhorse is wiring Stone payment for the new introduction.
January 24, 2019: Mike Campbell tells Stone the paperback “is printing soon,” and asks what address he should send Stone’s copies to. WaPo reports that Mueller is investigating whether Jerome Corsi’s “severance payments” from InfoWars were an effort to have him sustain Stone’s story. It also reports that Corsi’s stepson, Andrew Stettner, appeared before the grand jury. That same day, the grand jury indicts Stone, but not Corsi.
January 25, 2019, 6:00 AM: Arrest of Roger Stone.
January 25, 2019, 2:10 PM: Starting the afternoon after Stone got arrested, Tony Lyons starts working with Smith on some limited post-arrest publicity. He says Hannity is interested in having Stone Monday, January 28 “Will he do it?” Smith replies hours later on the same day his client was arrested warning, “I need to talk to them before.”
January 26, 2019: Lyons asks Smith if Stone is willing to do a CNN appearance Monday morning, teasing, “I guess he could put them on the spot about how they really go to this house with the FBI.”
January 27, 2019: Smith responds to the CNN invitation, “Roger is fully booked.” When Lyons asks for a list of those “fully booked” bookings, Smith only refers to the Hannity appearance on the 28th, and notes that Kristin Davis is handling the schedule. Davis notes he’s also doing Laura Ingraham.
January 28, 2019: The plans for Hannity continue on Monday, with Smith again asking for the Hannity folks to speak to him “to confirm the details.” In that thread, Davis and Lyons talk about how amazing it would be to support “another New York Times Bestseller” for Stone.
February 15, 2019: After two weeks — during which Stone was indicted, made several appearances before judges, and had his attorneys submit their first argument against a gag — Stone responded to Campbell’s January 24 email providing his address, and then asking “what is the plan for launch?” (a topic which had already been broached with Lyons on January 16). Campbell describes the 300-400 media outlets who got a review copy, then describes the 8 journalists who expressed an interest in it. Stone warns Campbell, “recognize that the judge may issue a gag order any day now” and admits “I also have to be wary of media outlets I want to interview me but don’t really want to talk about the book.”
February 18, 2019: Release of ebook version of Stone’s reissued book.
February 21, 2019: After Stone released an Instagram post implicitly threatening her, Amy Berman Jackson imposes a gag on Stone based on public safety considerations.
March 1, 2019: Ostensible official release date of paperback of Stone’s book. Stone submits “clarification” claiming that the book publication does not violate the gag.
March 12, 2019: Official release date of Corsi hard cover, which Mueller may need for indictment.
As I disclosed last July, I provided information to the FBI on issues related to the Mueller investigation, so I’m going to include disclosure statements on Mueller investigation posts from here on out. I will include the disclosure whether or not the stuff I shared with the FBI pertains to the subject of the post.