BREAKING! Romney Surrogate Points to Effects of Republican Budget Cutting as Factor in Benghazi Attack!!
Eli Lake continues to serve as the mouthpiece for a political attack explicitly crafted by close Rove associates. In today’s installment, he repeats Mitt Romney campaign surrogate, UT Congressman Jason Chaffetz’ latest attack: that the State Department cut security after the hot war in Libya ended.
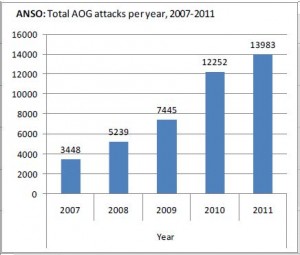
In the six months leading up to the assault on the United States consulate in Benghazi, the State Department reduced the number of trained Americans guarding U.S. facilities in Libya, according to a leading House Republican investigating the Sept. 11 anniversary attacks. The reduction in U.S. security personnel increased America’s reliance on local Libyan guards for the protection of its diplomats.
[snip]
Chaffetz went further Wednesday, saying in an interview that the number of American diplomatic security officers serving in Libya had been reduced in the six months prior to the attacks. “The fully trained Americans who can deal with a volatile situation were reduced in the six months leading up to the attacks,” he said. “When you combine that with the lack of commitment to fortifying the physical facilities, you see a pattern.”
I suppose it would be too much for Lake to acknowledge that Chaffetz is a Romney surrogate and note the repeated admissions that Romney’s team intends to turn the Benghazi attack into Obama’s Jimmy Carter. Doing so might reveal that this outrage is, to some extent, manufactured.
With the help of Eli Lake.
Perhaps he could at least read this article.
Not only does it support the argument that Mike Rogers, the House Intelligence Chair, should be the one to conduct Congress’ investigation, not a Romney surrogate on a committee without the clearances to do so.
Rep. Michael Rogers, chairman of the House Intelligence Committee, made clear Wednesday that congressional staff will be looking into the attack, in addition to a probe by the State Department’s inspector general and another State Department investigation required by federal law.
But it explains why the surrogate for a candidate running with the House Budget Chair really shouldn’t be squawking about the State Department cutting security after a hot war ends.
Since 2010, Congress cut $296 million from the State Department’s spending request for embassy security and construction, with additional cuts in other State Department security accounts, according to an analysis by a former appropriations committee staffer.