There’s More to the SPCMA Document
Long time readers likely know I’ve been obsessed with the decision, which as far as we currently know started in 2007 after Alberto Gonzales and (since returned as FBI General Counsel) James Baker left DOJ, to let DOD chain through US person identifiers on metadata collected under EO 12333, what gets described as Special Procedures Governing Communications Metadata Analysis, or SPCMA. Here’s a post that describes it at more length.
We first learned about SPCMA in June 2013, when the Guardian published a 16-page document pertaining to the approval process that had been leaked by Edward Snowden. That document consisted of:
- A ten page memo dated November 20, 2007, from Assistant Attorney General for National Security Ken Wainstein and Acting OLC Head Steve Bradbury, analyzing the legality of SPCMA and recommending approval of the change.
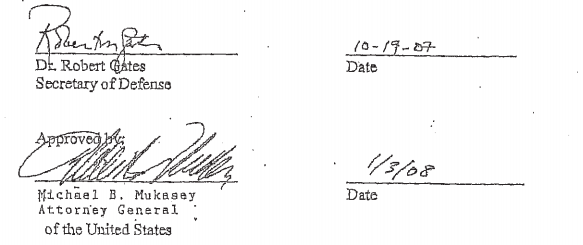
- Appendix A, consisting of a cover sheet and a two-page approval memo signed by Robert Gates on October 19, 2007 and Michael Mukasey on January 3, 2008. As I noted in this post, the signature line had to be altered after the fact to indicate Mukasey was signing it, suggesting that then Acting Attorney General Peter Keisler had refused.
- Appendix B, a September 28, 2006 memo written to Office of Intelligence and Policy head James Baker (this was the predecessor to the NSD at DOJ) by NSA’s General Counsel Vito Potenza requesting he approve what became SPCMA (Baker did not approve it).
Though it is not included in what Snowden leaked, the memo describes a third Appendix, Appendix C:
On July 20, 2004, the General Counsel of CIA wrote to the General Counsel of NSA and to the Counsel for Intelligence Policy asking that CIA receive from NSA United States communications metadata that NSA does not currently provide to CIA. The letter from CIA is attached at Tab C.
The government has not released an official version of the packet such as it got leaked by Snowden. However, it did release Appendix A, the approval memo, in Fall 2014 as part of the declassification of the Yahoo challenge to the Protect America Act. As I laid out in this post, the government not only got this document approved after the passage of PAA and while Yahoo was challenging orders received under it, but DOJ tried to hide it from FISC Judge Reggie Walton. They only handed it over — though without the context of the approval memo that made it clear it was about contact chaining including Americans — after he had scolded DOJ several times about not handing over all the documentation related to PAA.
DOJ did not submit the procedures to FISC in a February 20, 2008 collection of documents they submitted after being ordered to by Judge Walton after he caught them hiding other materials; they did not submit them until March 14, 2008.
So to sum up: We have 16 pages (the memo and two of three appendices) thanks to Edward Snowden, and we have an official copy of just the 2-page approval memo, released on the context of the Yahoo declassification.
I lay all this out because this entry, in the National Security Division Vaughn Index provided to ACLU last month, is undoubtedly this same memo.
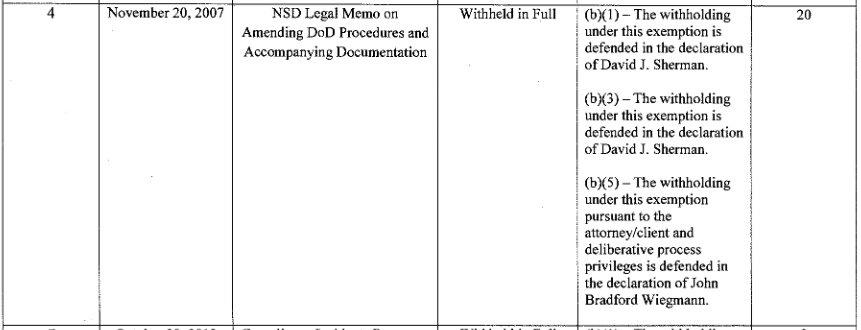
The date is the same, the description is almost the same. The only difference is that the withheld document has 20 pages, as compared to the 16 pages that Snowden gave us.
From that I conclude that the 2004 CIA memo is four pages long (three, plus a cover sheet). Note the date: squarely during the period when spooks were trying to put discontinued parts of Stellar Wind under some kind of legal authority.
Here’s how the NSA declared Exemptions 1 and 3 over this document.
56. NSD fully withheld Document 4 on its Vaughn index in part because the release of any portion of that document would disclose classified information about functions or activities of NSA. The document is a 20-page document dated 20 November 2007 and is described as NSD Legal Memo on Amending DoD Procedures and Accompanying Documentation.” This document. including its full title, was withheld in full under Exemption 1 and Exemption 3. I have reviewed the information withheld and determined that the information is currently and properly classified at the SECRET level in accordance with EO 13526 because the release of this information could reasonably be expected to cause serious damage to the national security. The information withheld pertains to intelligence activities, intelligence sources or methods, or cryptology. or the vulnerabilities or capabilities of systems or projects relating to the national security and therefore meets the criteria for classification set for in Sections 1.4(c) and 1.4(g) of EO 13526. The harm to national security of releasing any portion of this document and the reasons that no portion of this document can be released without disclosing classified information cannot be fully described on the public record. As a result my ex parte. in camera classified declaration more fully explains why this document was withheld in full.
57. The information withheld in N 0 Document 4 also relates to a “function of the National Security Agency” 50 U.S.C. § 3605. Indeed. this information relates to one of NSA’s primary functions, its SIGINT mission. Any disclosure of the withheld information would reveal NSA ·s capabilities and the tradecraft used to carry out this vital mission. Further. revealing these details would disclose “information with respect to lNSA ‘s] activities” in furtherance of its SIGINT mission. 50 U .. C. § 3605. Therefore. the information withheld is also protected from release by statute and is exempt from release based on FOIA Exemption 3. 5 U.S.C. § 552(b)(3).
The government asserted secrecy over the title of an already (and officially) released document in a recent EFF challenge, so this would not be the first time the government claimed the title of an already released document was secret to prevent nasty civil liberties groups from confirming that a FOIAed document was the same as a previously known one.
In NSD’s declaration, Bradley Weigmann indicated that “the vast majority” of the document pertained to attorney-client privilege.
NSD Document 17, the vast majority of a certain memorandum in NSD Document 4, and an email message in NSD Document 31 are protected by the attorney-client privilege. These documents discuss legal issues pertaining to an NSA program, set forth legal advice prepared by NSD lawyers for other attorneys to assist those other attorneys in representing the Government, and were sought by a decision-maker for the Government to obtain legal advice on questions of law and indeed reflect such advice. As such, NSD Document 17, the vast majority of a certain memorandum in NSD Document 4, and an email message in NSD Document 31 are protected from disclosure under the attorney-client privilege.
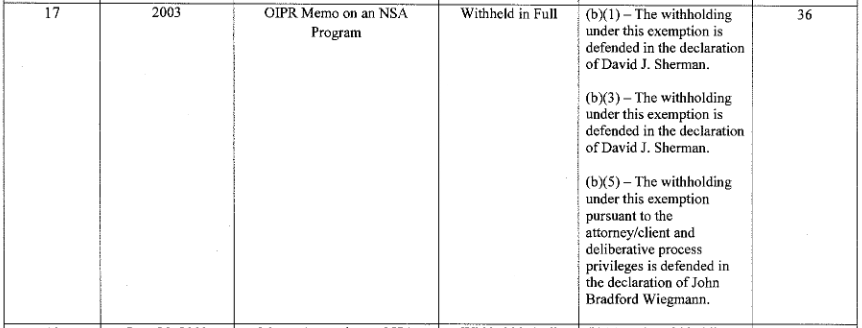
More interestingly, by referring to “an NSA program” it seemed to tie this document with this 2003 OIPR memo.
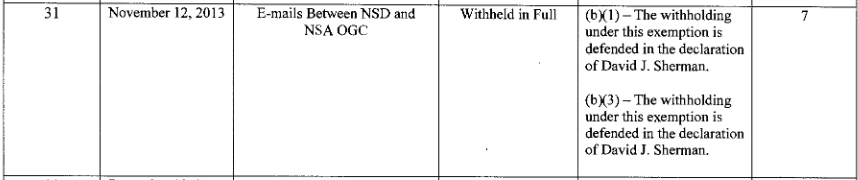
And this November 12, 2013 email (written during a period in the aftermath of the Snowden releases as the government was trying to decide how to respond to various FOIAs as well as Yahoo’s request to unseal its challenge, not to mention after ACLU submitted this FOIA, which was actually submitted before the first Snowden leaks).
Note, NSD won’t tell us what date in 2003 someone at OIPR (already headed by James Baker, one of the few people briefed on Stellar Wind) wrote about “an NSA program” that appears to be tied the chaining on US person metadata.
I have long believed one of the known but still as yet undescribed modifications to Stellar Wind (there is still at least one, though I believe there are two) enacted after the hospital confrontation in 2004 has to have been either at CIA or DOD, because it doesn’t appear in the unredacted NSA IG Report Snowden gave us. Here, we see CIA unsuccessfully asking for US person metadata at the time everyone was re-establishing Stellar Wind under more legal cover. Assuming NSA document 4 is this memo, the only thing the government is withholding that we haven’t seen yet is the CIA memo. I have a lot more suspicions about this program, too, that I still need to write up.
But I suspect they’re hiding these documents from us — and just as importantly, from the FISA Court — to prevent us from putting the various details of how US person metadata has been used over time. Or rather, to prevent us from laying out how the point of these foreign-targeted surveillance programs is to spy on Americans.
ACLU has already told the government they’re challenging the withholding of these documents.