A Bit about Dossiers: You’ve Been Eating this FUD for Years
NB: Note the byline — this is Rayne, with what might be another minority report.
Once upon a time in a nearby galaxy in the not-too-distant past, I worked in competitive intelligence. I gathered information about large technology companies’ competitors and summarized it into reports — dossiers, if you will. These firms made product decisions after reading these reports. Thanks to non-disclosure agreements I can’t tell you which companies or products, but know that if you are reading this you have been in contact with their goods and/or the long-term impact of their products and services.
The technology you’ve used or been in contact with has been shaped by these same dossiers.
My research was based on publicly available information. No sneaking around inside fence lines with false identification or hacking servers and networks to pry open locked-away goods. No flights overseas to slink through alleys into dark pubs with shady characters. I was armed with my native curiosity, a decent computer, both internet and library access, and a background in Fortune 500 report writing.
These companies took my work and used it in what is corporate warfare. It goes on around you every day, skirmishes and battles for your wallet and attention, volleys lobbed by hard and soft goods manufacturers and retailers, by firms selling services and intangibles. You think of this as marketing and often consciously blow it off.
Some of this corporate warfare is negative, openly bashing competitors based on comparative price and quality. But some of it is far more insidious; it attacks brands in a way designed to inspire long-term avoidance of entire product lines and brand names, and based on fairly flimsy information. Sometimes it’s just plain false — truly false misinformation and plausible disinformation.
But isn’t some of this fraud, you might ask? Hah-hah. Good luck proving it and making a case. Disinformation is particularly weaselly because it is plausibly true, plausibly deniable.
And I would bet dollars to donuts you’ve made tens and hundreds of purchasing decisions in your lifetime based on disinformation, perhaps even disinformation created from my dossiers. This is the point of corporate disinformation campaigns: to dissuade you from supporting their competition.
As a researcher I often ran into laundered information. For example, it might be disseminated as a small press release in another country in a language Americans don’t often bother to acquire any level of fluency. The press release may get picked up in another country, then by an English language media outlet which reports the content now two degrees from origin as news. Presto: what was once the direct output of a corporate entity is now news upon which buyers make decisions.
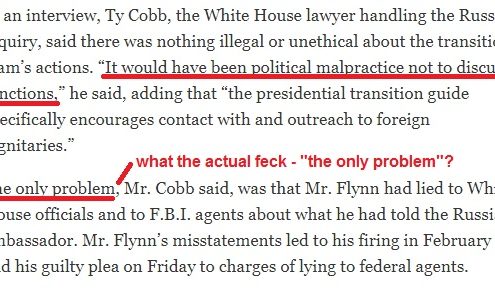
Is there media complicity here? Sure, to some degree; the point of origin may be lost and the first news outlets may not perceive the importance of information’s provenance because to them the origin is still visible; witness this week’s reporting by U.S. news outlets all ultimately relying on a single German business paper’s report. But the news media doesn’t bear all the culpability here. News consumers in the U.S. have been notoriously lax in validating content for decades.
It’s unsurprising given the antiquity of the admonishment, Caveat emptor. It has long been a problem that consumers of goods whether information or products and services must be more skeptical before committing their wallets and health, let alone their votes.
Social media has only made the job of laundering information even easier, between the number of washings platforms can offer and the automation of repetition, scale, and dispersion, all for a pittance. Over the last ten years the work I did as a researcher has become incredibly difficult; tracing the origin of a single piece of highly controversial or relatively arcane news originating overseas is like swimming against a mighty current.
And much of that current is deliberately crafted “alternative narrative” (pdf) — disinformation.
You may look askance at information laundering about products and services. Don’t. My own work was laundered not once but twice that I’m aware of. I wasn’t a marketing department employee at the firms which contracted competitive intel research. Nor was I an employ of the small firm contracted by these Fortune 100-1000 firms needing my services. That’s two removes and I am sure there was at least one more — the work I did was probably restated and re-presented internally, at a minimum.
Immaculate information conception — you were sold a bill of goods without knowing I was at the other end of the food chain. You never saw my fingerprints, heard my heels on the pavement, or caught a whiff of my perfume, even though in one way or another you have been touched in the last decade by decisions made based on my research.
~ | ~
You have been eating the FUD prepared for you — fear, uncertainty and doubt which gave you pause and made you choose something else. FUD has long been a tactic of technology companies; billions in sales have relied on its use. Entire industries have depended on it, created wholly from competitive intelligence dossiers like those I’ve prepared.
And yet concern trolls tell you Russia wasn’t a factor during the 2016 and that ‘fake news’ played no role whatsoever in Trump’s election? Bullshit. Russia’s culture and government make Silicon Valley look like pikers when it comes to the development and use of FUD. Social media and the decades-long reflexivity of right-wing media only served to weaponize Russia’s FUD against the U.S. We never saw it coming because we bought our own nonsense disinfo of American exceptionalism and western democracy’s inviolability.
Out there on the internet in either social media, public records, or leaked data is your voter records, disclosing your location, your state/congressional district/precinct, your voting habits; your vehicle records, your home address; your telephone number, your social media accounts and the network of family and friends and businesses with which you choose to associate. Add your purchasing habits from buyers’ loyalty cards and subscriptions, your fast food purchases when not made with cash. Your debts, whether your small business’ Dun & Bradstreet report, your mortgage, and now your personal credit record (thank you so much, Equifax). Your entire life can be digitally reconstructed to reveal your soft underbelly: what is it that makes you wake up at night in a cold sweat?
It takes little for corporations to identify and target you with an ad to make you doubt another company’s product. I don’t even have to weed through all sources I once mined and aggregated to tell them what you were thinking about Competitor X’s product Y. You’ve already told the world and the places you’ve connected to have shared it. There are simple algorithms to harvest what’s needed, quickly and cheaply.
You are not exceptional nor inviolable because you have been conditioned to exist in this information matrix. You have made little effort to pan golden fact from streams of manufactured information, too eager to swallow misinfo and disinfo because it’s easy — plausible, palatable, hits you right where you are most sensitive and vulnerable.
And yet concern trolls tell you a competing nation-state wouldn’t have used this against you, inserting FUD in a way that furthers their interests above our own, though trillions of dollars benefit at least one nation-state to do so? Though a competing nation-state’s disinformation campaign may have a very low benchmark of success, merely to dissuade you from wholeheartedly supporting restrictions against them?
Hah. Sucker. I have some technology to sell you.
~ | ~
Now here’s the part where I get annoyed with the friction over the Steele dossier. I have reasonable confidence in Steele’s findings. But this doesn’t put me in the same camp as folks who believe the dossier is gospel truth waiting to be decoded into trial-worthy evidence. My confidence separates me from those who pooh-pooh the dossier as ‘fake news’.
The fundamental problem with the public’s understanding of the dossier is the dossier’s utility. It is like the documents I prepared for technology companies — a competitive intelligence report, designed to inform its purchaser about the weaknesses and threats a competitor poses, or the most sensitive point where a competitor can be attacked. It’s not a full-blown SWOT analysis (strengths, weaknesses, opportunities, threats) as the dossier is an external view; it’s closer to an inverted SWOT looking at a competitor excluding any internal perception of the client and its place in the market. It also doesn’t have to be one hundred percent accurate — just reasonably close for the marketing equivalent of a grenade or a Daisy Cutter as the situation dictates.
The friction on the left exists because nearly everyone with a published opinion on the Steele dossier doesn’t see it as a marketing document which should have helped a purchaser develop the political equivalent of the Four Ps — product, placement, promotion (pricing doesn’t really work here, apart from ensuring messaging includes the opportunity costs of electing the right/wrong candidate).
The Clinton campaign nor the dossier-purchasing campaign before it would not necessarily take the Steele dossier as evidence in a legal sense, just as the marketing documents I prepared weren’t evidence. I didn’t get sworn statements and multiple corroborating witnesses to disclose what competing technology companies were doing; neither did Christopher Steele or his intermediary client(s) do this about candidate Trump. (It kind of runs up a flag to your targets when you ask a witness to swear out a statement in front of a notary — so much for gaining a competitive edge.) But just as the firms who bought my services trusted me to gather reasonably accurate information sufficient to make a marketing decision, so, too, did Steele’s clients trust him to do the same. (Just as an aside, it’s rather amusing so few ask how such trust is generated.)
In short, competitive intelligence dossiers are not evidentiary. They’re aggregations of reasonably accurate information for the purpose of making a marketing decision, whether the dossier’s user is a product, service, or a campaign. They help a client look forward. They aren’t designed to lock down and set in stone facts for retrospection. And in most cases, competitive intelligence dossiers try to capture a moving target; they work within a narrow time frame because the field can change rapidly.
Think about a technology company approaching someone like me today for competitive intelligence. What use would the dossiers I prepared years ago be today? They don’t capture the competitive environment in which products now go head to head. I can think of multiple competitors I followed and wrote about in my dossiers which no longer exist. In the technology sector, the landscape can change overnight. What in the Steele dossier has changed if a Trump competitor were to try and use it today?
Argue all you want about the Steele dossier. In the mean time, the competition has been drafting a more fluid dossier on us, shifting their information warfare, I mean, campaign to persuade us to their cause or to our detriment, serving up fresh, hot FUD you may all too willingly consume. For all you know, the friction itself is a direct result of disinfo-created FUD.



![[Photo: Emily Morter via Unsplash]](https://www.emptywheel.net/wp-content/uploads/2017/08/Question_EmilyMorter-Unsplash.jpg)