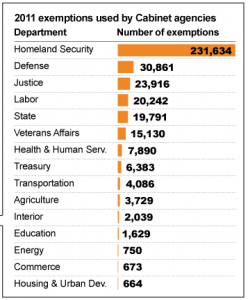
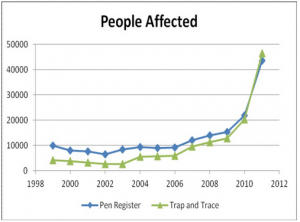
The Snarlin has ceased; via CBS News:
The Snarlin has ceased; via CBS News:
US Senator Arlen Specter, whose political career took him from Philadelphia City Hall to the US Congress, died Sunday morning at his home in Philadelphia at the age of 82 from complications of non-Hodgkins Lymphoma. He was born February 12, 1930.
His career was marked by what the pundits and Specter himself called “fierce independence.” But long before Specter ever stepped onto the Senate floor in Washington DC, he made it into national prominence by serving as assistant counsel for the Warren Commission, which investigated the 1963 assassination of Pres. John F. Kennedy.
Specter postulated the controversial “single-bullet theory” that was eventually embraced by the panel and still stands to this day, despite the cry of conspiracy theorists who say there was more than one gunman in Dallas that November day.
“Admittedly a strange path for a bullet to take, but sometimes truth is stranger than fiction,” Specter said.
We have had a complicated relationship with Arlen Specter here at Emptywheel, sometimes castigating him, sometimes praising him, sometimes laughing at him, sometimes laughing with him. Specter engendered all those things. But I always sensed a very decent heart beating underneath Specter’s surface, even if it was all too often masked by his votes for, and often vociferous support of, ever more destructive policies of the right.
For this, Specter earned the nickname “Scottish Haggis” here in the annals of Emptywheel. The term had its root in Mr. Specter’s predilection for Scottish Law, and goes all the way back to the original incarnation at The Next Hurrah. For a number of reasons, offal and otherwise, it was a nickname that stuck and seemed appropos and seemed to reflect the complicated nature of Senator Specter.
On a personal note, I did not have an abundance of interaction with Sen. Specter and his office, but in that which I did have, I found him and his office to be beyond both kind and professional. One instance stands head and shoulders above the others, and surrounded the Obama scuttled nomination of Dawn Johnsen to be head of the Office of Legal Counsel (OLC). It was my contention from the outset that the whip count votes were there to confirm Professor Johnsen for the job she was perfect for. And, in the roiling aftermath of the Bush/Cheney unitary executive excesses, the country desperately needed Johnsen’s intellectual sense of honesty and Constitutional integrity.
The only reason Dawn Johnsen did not get confirmed as OLC head was Barack Obama used her as false bait and cat nip for the more noisy progressive liberals. It was a glaring sign of depressing things to come from the not nearly as Constitution minded Barack Obama as had been pitched in his election run. Not only could Johnsen have been confirmed, as I pointed out before, she could also have been recess appointed by Obama. Despite all the ridicule I took at the time, that point has been proved conclusively by the later recess appointment of Richard Cordray to be head of the CFPB (another instance of Obama using a supremely qualified progressive, Elizabeth Warren, as bait and then hanging her out to dry).
The point was never that Dawn Johnsen couldn’t be confirmed, it was that Barack Obama and the insiders of his White House did not want her confirmed into leadership of the OLC. I knew that from talking to several inside the DOJ and Senate Judiciary Committee, but that was all off the record. When I found an obscure old comment from Arlen Specter indicating he was willing to support a cloture vote for Johnsen as far back as his second meeting with Dawn Johnsen on or about May 12, 2009, it was by then an old, and quite obscure comment. Specter could have walked it back or dissembled on the subject.
Arlen Specter didn’t walk it back or dissemble, instead he personally confirmed it to me. With the already in the bag vote of Sen. Richard Lugar, that was the 60 votes for Dawn Johnsen at OLC. Specter knew it would infuriate both the GOP and the Obama White House, and he knew exactly what story I was writing. He stood up. Oh, and, yes, he knew about “Scottish Haggis” too. The man had a sense of humor.
For the above vignette, and several others, I will always have a soft spot in my heart for Snarlin Arlen Specter. His life and work in government spanned over five decades, he has got my salute today.
Sen. Specter repeatedly had to fight off serious cancer, and he did so with aplomb, courage and his good humor. He also was a tireless champion for the NIH and funding of cancer and stem cell research. When confronted with the last battle, the one which finally took him, Specter was upbeat, defiant and determined to get back to his part time hobby of stand up comedy. May the Scottish Haggis have many laughs wherever he may travel.