How the FBI Missed Alleged January 6 Leader Joe Biggs
Let’s talk about how central Joe Biggs is to what we know of the implementation of January 6.
It explains a lot that — at least according to a claim Biggs himself made — two FBI agents were relying on him for information against Antifa in the lead-up to the terrorist attack.
By late 2018, Biggs also started to get “cautionary” phone calls from FBI agents located in Jacksonville and Daytona Beach inquiring about what Biggs meant by something politically or culturally provocative he had said on the air or on social media concerning a national issue, political parties, the Proud Boys, Antifa or other groups. Biggs regularly satisfied FBI personnel with his answers. He also stayed in touch with a number of FBI agents in and out of Florida. In late July 2020, an FBI Special Agent out of the Daytona Beach area telephoned Biggs and asked Biggs to meet with him and another FBI agent at a local restaurant. Biggs agreed. Biggs learned after he travelled to the restaurant that the purpose of the meeting was to determine if Biggs could share information about Antifa networks operating in Florida and elsewhere. They wanted to know what Biggs was “seeing on the ground.” Biggs did have information about Antifa in Florida and Antifa networks in other parts of the United States. He agreed to share the information. The three met for approximately two hours. After the meeting, Biggs stayed in touch with the agent who had called him originally to set up the meeting. He answered follow-up questions in a series of several phone calls over the next few weeks. They spoke often.
I don’t mean they were complicit. Rather, that they weren’t even aware that he was in the middle of plans to conduct a terrorist attack on the nation’s Capitol is a testament to and perhaps an explanation for how the FBI missed all this.
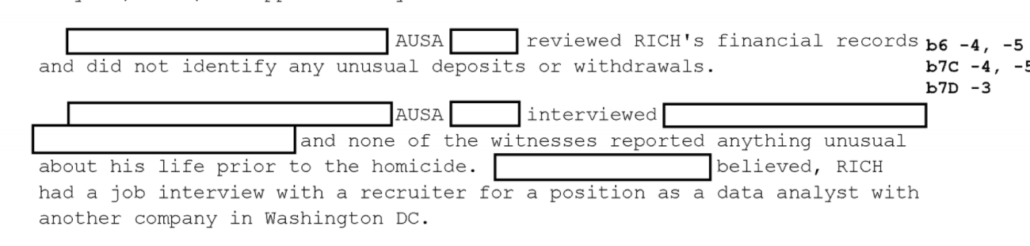
Joe Biggs is a former Army Staff Sergeant who did tours of duty in Iraq and Afghanistan before he left with a medical discharge and PTSD. After some troubled years, he started contributing to InfoWars, serving as a key proponent of the PizzaGate scandal that turned John Podesta emails stolen by Russia into an attack on a pizza restaurant in DC; he was formally ousted from InfoWars shortly after the Comet Ping Pong attack, but remained in the InfoWars orbit. Alex Jones claims he gave Biggs a big severance when he left. After that, Biggs was a key proponent of the Seth Rich conspiracy, posting the manufactured FBI Report that served as a basis for the Fox News story that had to be retracted.
According to one of Biggs’ own court filings, after he moved to Florida to take care of his mother in 2018, he contributed the same propaganda skills that fostered an attack on Comet Ping Pong and falsely impugned a murdered DNC staffer to the Proud Boys, ginning up events to sow violence in the name of Antifa.
The same year, 2018, after the move to Florida, Biggs became active as an organizer, event planner and thought leader in the Proud Boys. He used his platform as a radio and social media personality to promote Proud Boy events and ideas. In particular, he personally planned two major events: rallies in Portland, Oregon in both 2019 and 2020 designed as counterdemonstrations against Antifa, which had been active in and around Portland for over two decades.
His presence in Florida put him in close proximity to Enrique Tarrio and (as if his ties to InfoWars didn’t already do so) through him Roger Stone.
When Trump called out the Proud Boys in his first debate against Joe Biden, Biggs responded, “President Trump told the proud boys to stand by because someone needs to deal with ANTIFA . . . well sir! we’re ready!!” (Note, this hasn’t shown up in DOJ filings.)
Immediately after and in the weeks after the election, Biggs kept declaring war. “It’s time for fucking War if they steal this shit.” “No bitch. This is war.” ““This is a war on Americanism. This is only the beginning.”
On December 11, the Proud Boys (at least Enrique Tarrio and Ethan Nordean) appeared prominently at a Stop the Steal event with InfoWars personality Owen Shroyer. There was coordination between the militias at a march the following day, after which Enrique Tarrio destroyed a Black Lives Matter banner from the Asbury United Methodist Church in DC.
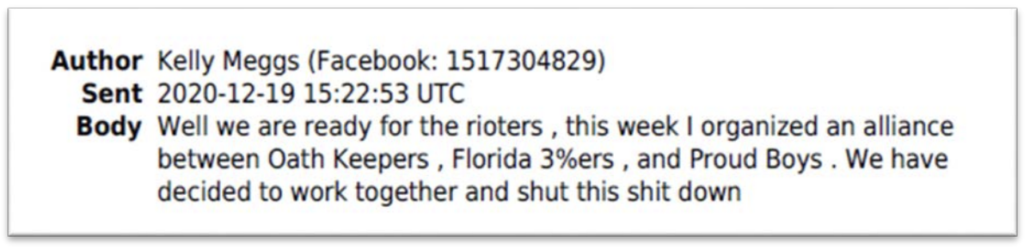
In the days after both the DC even and an event involving Stone in Florida, Oath Keeper Kelly Meggs claimed he organized a Florida-based “alliance” between the Oath Keepers, Proud Boys, and 3%ers.
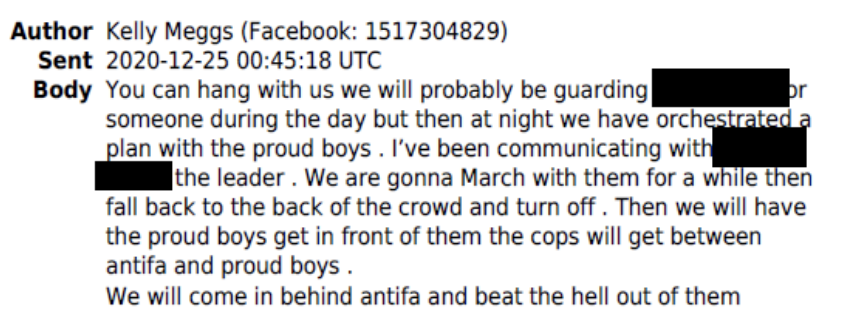
On Christmas Eve, Meggs specifically tied protection at the January rally, probably of Stone, and coordination with a Proud Boy, almost certainly Tarrio, in the same text.
In the days after, both Tarrio and Biggs posted plans to dress like Antifa rather than in their signature yellow and black.
9. For example, on December 29, 2020, Tarrio posted a message on the social media site Parler1 about the demonstration planned for January 6, 2021. Among other things, Tarrio announced that the Proud Boys would “turn out in record numbers on Jan 6th but this time with a twist… We will not be wearing our traditional Black and Yellow. We will be incognito and we will be spread across downtown DC in smaller teams. And who knows….we might dress in all BLACK for the occasion.” I believe the statement about dressing in “all BLACK” is a reference to dressing like the group known as “Antifa,” who the Proud Boys have identified as an enemy of their movement and are often depicted in the media wearing all black to demonstrations.
10. On or around the same day, BIGGS posted a similar message to his followers on Parler in which he stated, among other things, “we will not be attending DC in colors. We will be blending in as one of you. You won’t see us. You’ll even think we are you . . .We are going to smell like you, move like you, and look like you. The only thing we’ll do that’s us is think like us! Jan 6th is gonna be epic.” I understand that BIGGS was directing these statements at “Antifa.”
On December 30, Southern California 3%er Russell Taylor described a plan to meet at the Capitol and — in conjunction with Stop the Steal — surround the Capitol.
Spread the word to other CALIFORNIA Patriots to join us as we March into the Capitol Jan 6. The Plan right now is to meet up at two occasions and locations: 1. Jan 5th 2pm at the Supreme Court steps for a rally. (Myself, Alan, [and others] will be speaking) 2. Jan 6th early 7am meet in front of the Kimpton George Hotel…we will leave at 7:30am sharp and March (15 mins) to the Capital [sic] to meet up with the stop the steal organization and surround the capital. [sic] There will be speakers there and we will be part of the large effort for the “Wild Rally” that Trump has asked us all to be part of. [my emphasis]
This plan — surrounding the Capitol — was what Stop the Steal figures partially carried out on January 6.
On January 4, when Tarrio arrived in DC for the riot, he was arrested for his attack on the Black Church in December, whereupon he was found with weapons that are unlawful in DC. In the wake of Tarrio’s arrest, Ethan Nordean was supposed to be in charge of the operation. But around 9:08PM the day before the riot (these texts reflect Nordean’s Washington state time zone, so add three hours), someone said he had not heard from Nordean in hours.
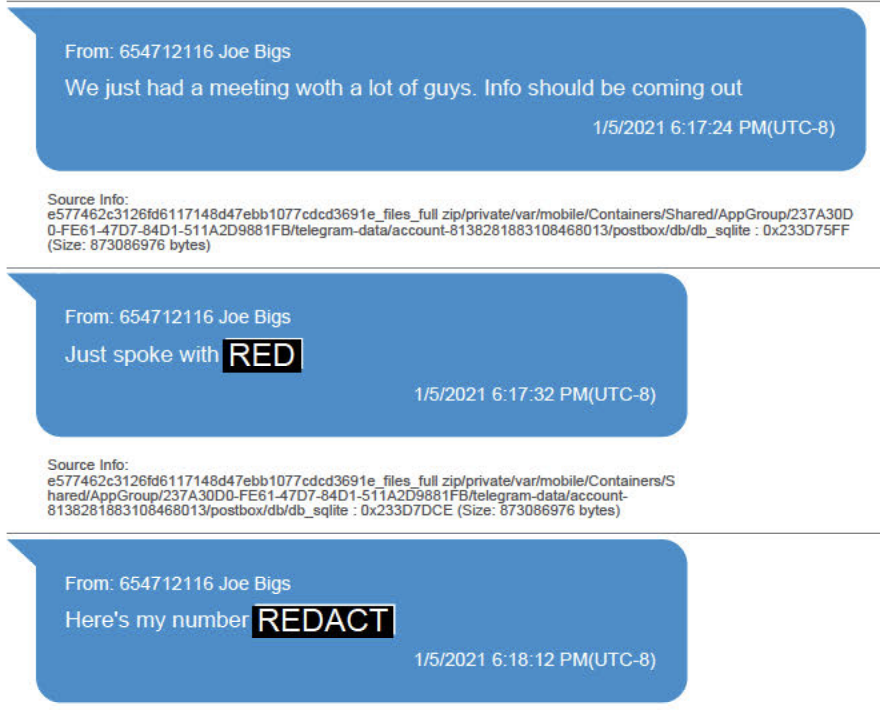
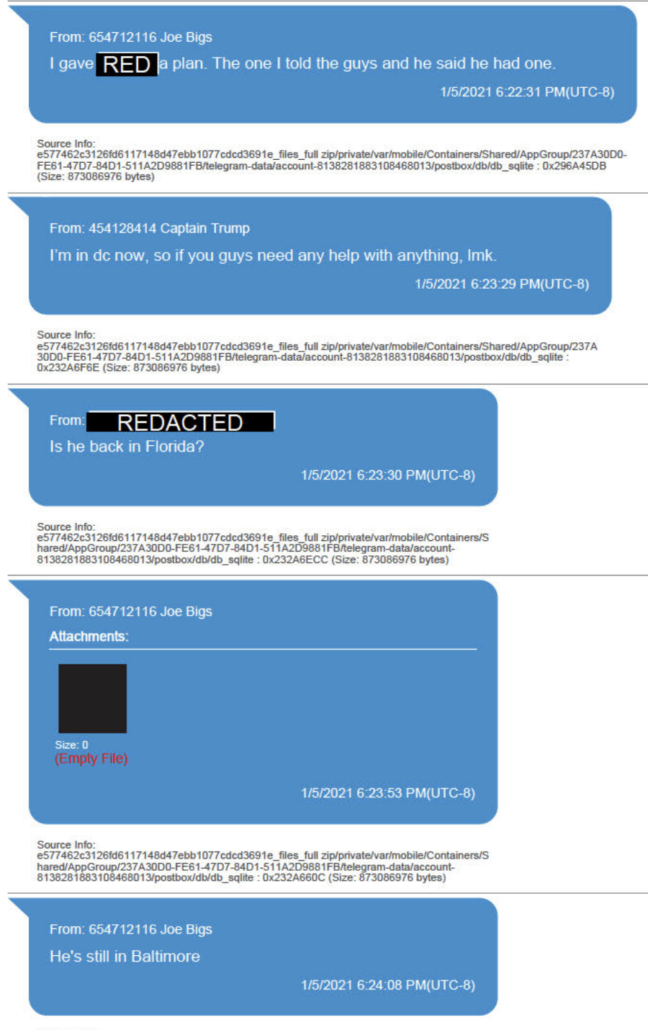
Minutes later, Biggs explained that “we just had a meeting w[i]th a lot of guys” and “info should be coming out.” While redacted in these texts, the superseding indictment describes that he also notes he had just spoken with Tarrio.
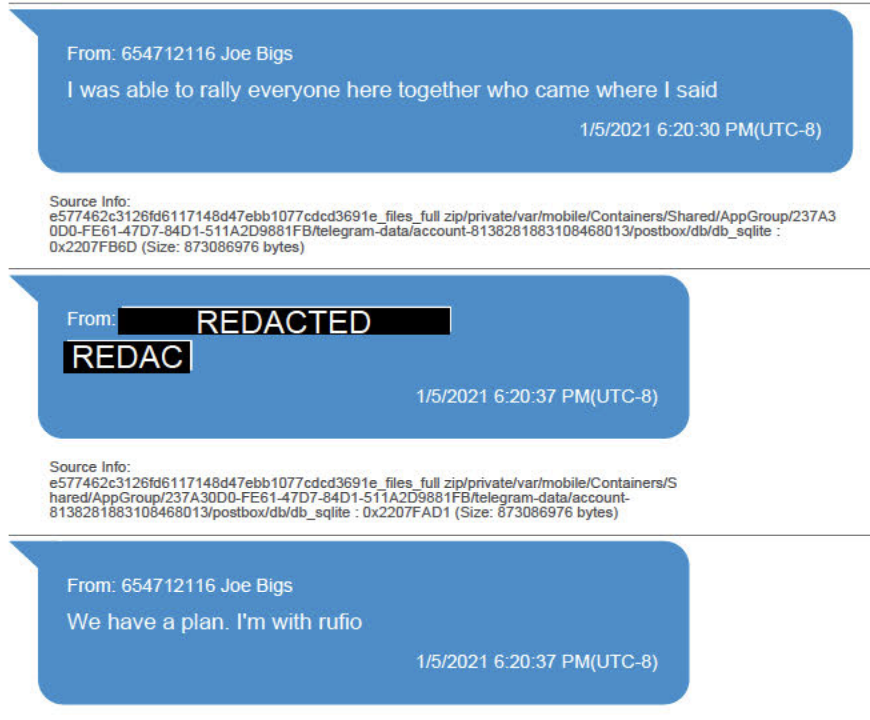
He further explained that he was with Nordean and “we have a plan.”
Biggs then says he gave Tarrio a plan.
Ethan Nordean may have been in charge on January 6. But Biggs seems to have been the one working most closely with Tarrio, through whom at least some of the inter-militia coordination worked.
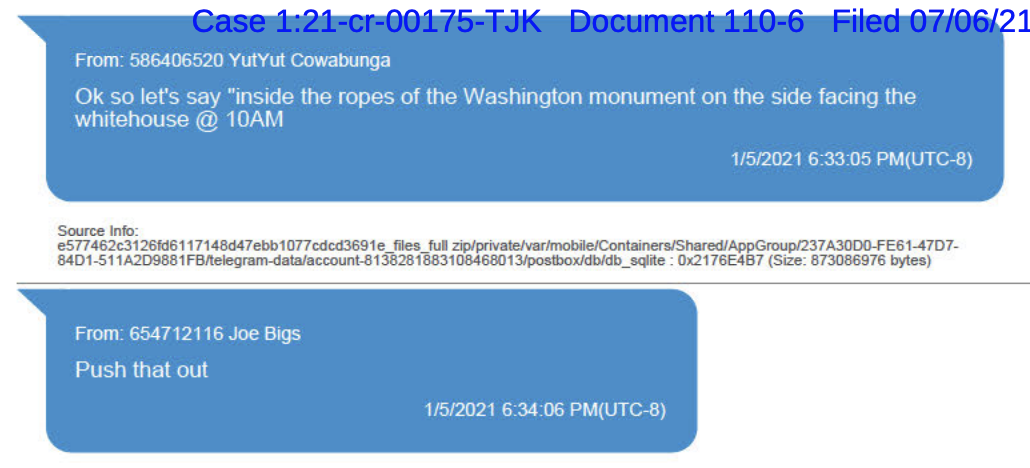
After all that, the Proud Boy leaders agree to meet at 10AM the next day.
As captured by the WSJ, the next day, after the Proud Boys met at the Washington Monument, they then marched the East side of the Capitol first, but then later approach it from the Northwest. Just before Trump started speaking and before a broader call to assembly tied to 1PM, at 12:52 Biggs said something to Ryan Samsel, who then kicked off the assault on a series of barricades, giving a police officer a brain injury in the process.
Proud Boys Dominic Pezzola and Billy Chrestman were among the leaders of the next confrontation. After a series of fights, at 2:13, Dominic Pezzola broke through a window in the Capitol. Biggs followed him, with some other Proud Boys (in this picture, Paul Rae) in tow, a minute later.
Meanwhile, even as Biggs was leading a mob of people in a violent attack on the Capitol, Alex Jones — Biggs’ former employer — was leading a larger mob of people from the Ellipse, where they had just been instructed by their President that “we’re going to the Capitol, and we’re going to try and give…we’re going to try and give our Republicans, the weak ones because the strong ones don’t need any of our help. We’re going to try and give them the kind of pride and boldness that they need to take back our country.” Jones stopped when he got to the Capitol and gave a speech.
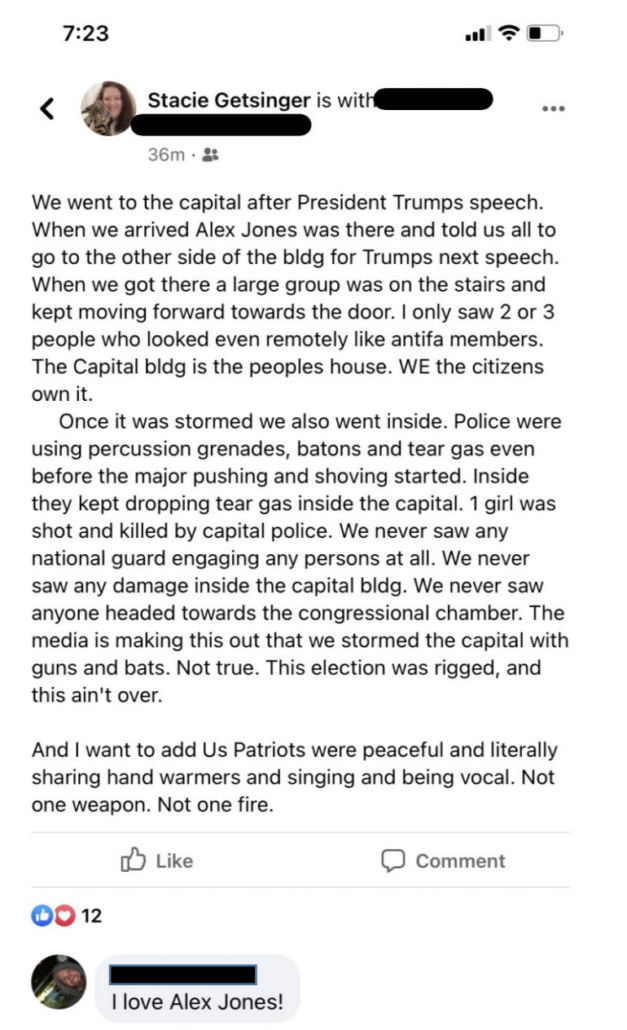
According to Stacie Getsinger, a woman from South Carolina who was arrested for trespassing in June who was listening to Jones at that first speech, Jones told his audience to go to the other side of the building (which would be the East side), because that’s where Trump’s next speech would be.
She and her husband did. Trump gave no speech, but they were among the first wave of people to breach the East entrance.
Alex Jones went to the other side of the Capitol, too. Even before he did, though, Oath Keeper Jason Dolan was on the stairs, waiting.
As Dolan waited, Jones and his entourage (including Ali Alexander and the recently arrested Owen Shroyer) pushed up the stairs stack-style.
Meanwhile, at some point, former InfoWars employee and Florida militia member reportedly joined in an alliance with the Oath Keepers by fellow Floridian Meggs, Biggs left the Capitol from one of the West entrances, walked around it, and assembled on the East Steps with Arthur Jackman, Rae, and two others (probably Kevin and Nathan Tuck, and possibly Edward George; the Tucks are both — now former — cops, and Jackman’s and one of the Tucks’ spouses still are cops).
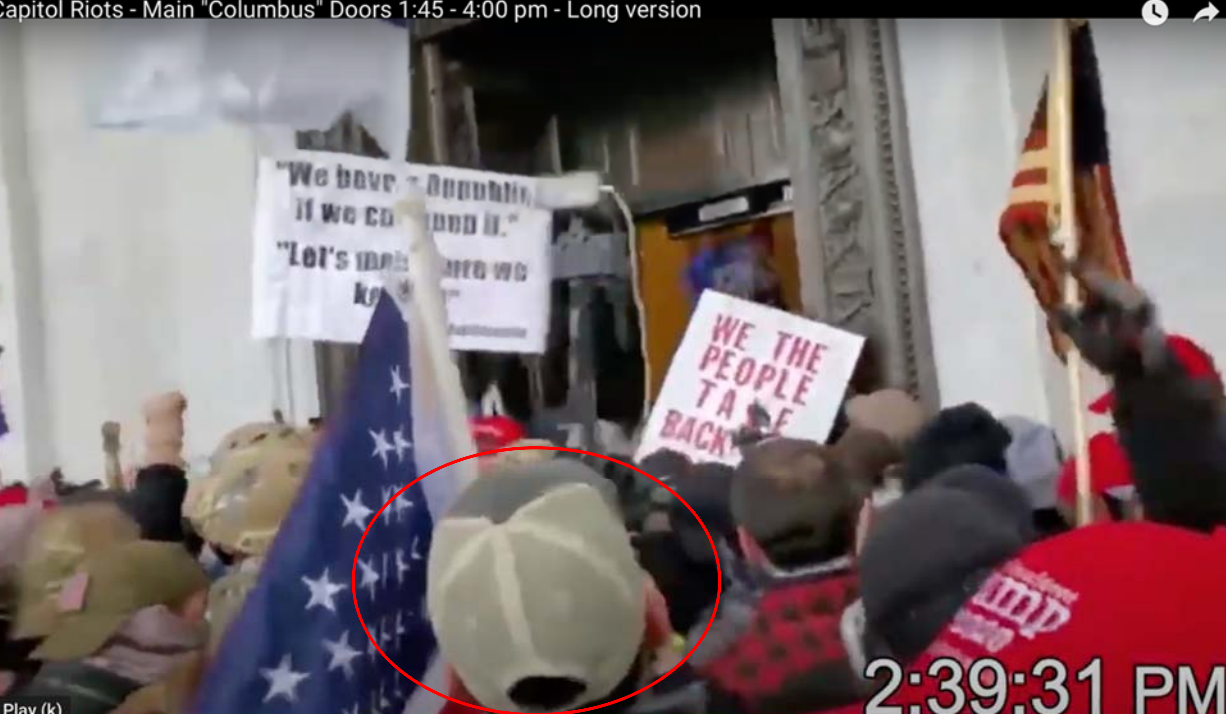
At 2:39, Rae and Jackman can be seen approaching the East Door with Biggs.
At around 2:40, they entered the East door.
At almost exactly the same time, Jason Dolan and Kenneth Harrelson entered the door along with the Oath Keeper stack led by Kelly Meggs (this is believed to be a picture Harrelson took of Dolan filming the entry; if you watch the video you can see both signs visible in the Biggs photo, making it clear that the people kitted out with helmets in that picture are the Stack).
People like the Getsingers — who were brought there by Alex Jones — pushed through around the same time.
Something brought Joe Biggs, Florida Oath Keepers Kenneth Harrelson and Jason Dolan, along with former Biggs employer Alex Jones to the top of the East steps, along with the mob that Jones brought on false pretenses. Shortly thereafter, Florida Oath Keeper head Kelly Meggs would bring a stack of Oath Keepers through the same door and — evidence suggests — in search of Nancy Pelosi, whom Meggs had talked about killing on election day.
Joe Biggs kicked off the riot on the West side of the building.
Then he went over to the East side to join his former employer Alex Jones and a bunch of Oath Keepers, led by fellow Floridians, to lead a mob back into the Capitol.
West side. Joe Biggs. East side. Joe Biggs.
This is the guy a couple of FBI Agents in Daytona believed was a credible informant against Antifa.
[Thanks to Benny Bryant for continuing to help me sort through the Oath Keeper side of this, and thanks to gal_suburban for sharing the video of Jones on the East side.]