Glenn Greenwald Moves to Close the Deal on Trump’s Election Help Quid Pro Quo
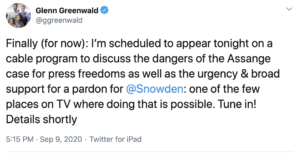
Two days ago, Glenn Greenwald started teasing a cable appearance where he was going to discuss — he claimed — the dangers an Assange extradition poses to press freedom. He was coy, however, about what outlet it was.
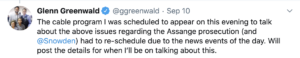
When he announced that his appearance had been postponed, he was again coy about what outlet this was.
The next day he described how “tyrannical” the hawkish civil servants who inhabit the Deep State are.
Last night, shortly before he went on, he revealed the cable outlet was Tucker Carlson’s show, which, he claimed, was “one of the few places on cable” where he could discuss the dangers of the prosecution of Julian Assange and the persecution of Edward Snowden. He excused his appearance on a white supremacist’s show by explaining that he cares more about having an opportunity to speak to “millions of Americans” about the “abuse of power by CIA/DOJ in persecuting those who expose the truth” than he does about the “sentiments of online liberals.”
Here’s the appearance, with my transcription to follow.
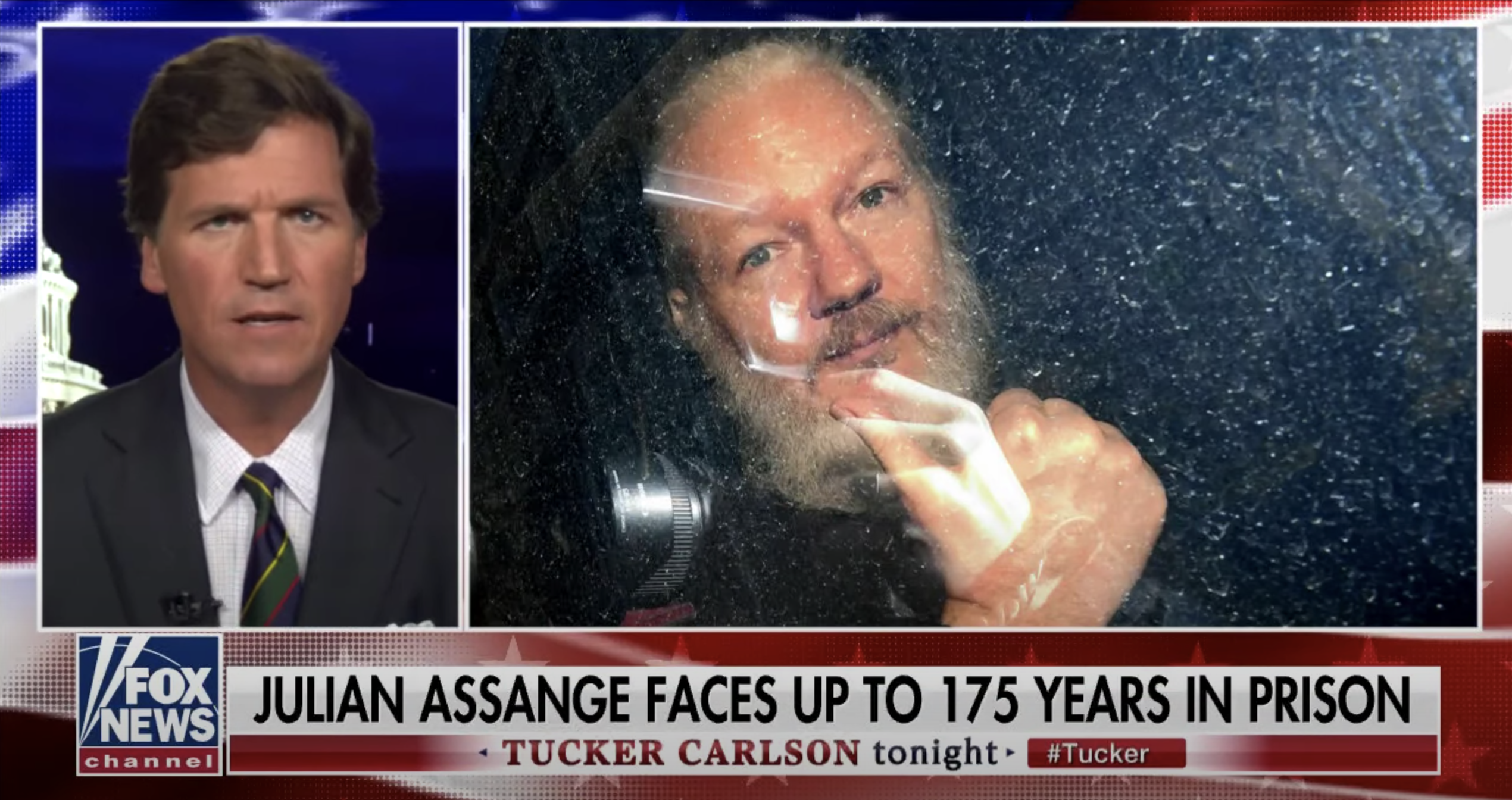
Tucker: WikiLeaks’ Julian Assange has been held in a high security prison since his arrest last spring in the Ecuadorian Embassy where he effectively was held for many years, in isolation. His extradition hearing is now finally under way. Assange’s lawyer estimates he could face 175 years in prison if he’s extradited to the United States. He faces Espionage charges here. WikiLeaks exposed all kinds of things, some of which it was good to know — including corruption by the Democratic National Committee in 2016. So what is the story on Julian Assange. Why is the DOJ pursuing this case so aggressively? Glenn Greenwald has followed this from the very beginning. He is of course a journalist, founded The Intercept. And we’re happy to have him tonight. So Glenn, thanks for coming on. I think a lot of people have heard for years that Julian Assange is a bad guy who hurt the United States, now the United States is going to bring justice in this case. What’s your view of this? Tell us what we should know, in 3 minutes, about Julian Assange.
Glenn: Let’s remember, Tucker, that the criminal investigation into Julian Assange began by the Obama Administration because in 2010 WikiLeaks published a slew of documents — none of which harmed anybody, not even the government claims that. That was very embarrassing to the Obama Administration. It revealed all kinds of abuses and lies that they were telling about these endless wars that the Pentagon and the CIA are determined to fight. They were embarrassing to Hillary Clinton, and so they conducted, they initiated a grand jury investigation to try and prosecute him for reporting to the public. He worked with the New York Times, the Guardian, to publish very embarrassing information about the endless war machine, about the Neocons who were working in the Obama Administration. To understand what’s happening here, we can look at a very similar case which is one that President Trump recently raised is the prosecution by the Obama Administration, as well, of Edward Snowden for the same reason — that he exposed the lies that James Clapper told, he exposed how there’s this massive spying system that the NSA and the CIA control, that they can use against American citizens. Obviously this isn’t coming from President Trump! He praised WikiLeaks in 2016 for informing the public. He knows, firsthand, how these spying systems that Edward Snowden exposed can be abused and were abused in 2016. This is coming from people who work in the CIA, who work in the Pentagon, who insist on endless war, and who believe that they’re a government unto themselves, more powerful than the President. I posted this weekend that there’s a speech from Dwight Eisenhower warning that this military industrial complex — what we now call the Deep State — is becoming more powerful than the President. Chuck Schumer warned right before President Obama — President Trump — took office that President Trump challenging the CIA was foolish because they have many ways to get back at anybody who impedes them. That’s what these cases are about Tucker, they’re punishing Julian Assange and trying to punish Edward Snowden for informing the public about things that they have the right to know about the Obama Administration. They’re basically saying to President Trump, “You don’t run the country even though you were elected. We do!” And they’re daring him to use his pardon power to put an end to these very abusive prosecutions. One which resulted in eight years of punishment for Julian Assange for telling the truth, the other which resulted in seven years of exile for Edward Snowden of being in Russia simply for informing the public and embarrassing political officials who are very powerful.
Tucker: So, in thirty seconds, the President could pardon Julian Assange right now, and end this. Is that correct?
Glenn: He could pardon him and Edward Snowden and there’s widespread support across the political spectrum on both the right and the left for doing both. It would be politically advantageous for the President. The only people who would be angry would be Susan Rice, John Brennan, Jim Comey, and James Clapper because they’re the ones who both of them exposed.
As has become the new norm for Glenn, there’s a lot that is exaggerated or simply made up in this rant (I’ve bolded the four main claims above):
- It is not the case that the government claims no one was harmed by Assange’s releases (even assuming we’re limiting the discussion to those already charged, and ignoring Vault 7, where the government presented hours and hours of testimony on the subject). The government has repeatedly claimed they caused a great deal of harm, even if they have not released their damage assessments publicly.
- The files that Assange has been charged for do include the first (in the case of the Afghan and Iraq War Logs) and the first two years of Obama’s term (in the case of Cablegate). They also include details about Guantanamo that were helpful to Obama’s failed efforts to shut down the gulag set up by Bush. The files did cause grave embarrassment to the Obama Administration, both for some policy stances (Yemen remains, to my mind, one of the most important disclosures), and because the Obama Administration had to explain how candid conversations could leak. But to the extent one wants to (as Glenn appears to) make this about tribalism, they exposed far more about the Bush Administration, and many of the policies exposed (like support for torture and Saudi Arabia) are policies Trump is more supportive of than Obama was.
- Glenn insinuates that the spying systems revealed by Edward Snowden were abused in 2016. He suggests that Trump was targeted by them. Glenn has made this error before, in his invention-filled defense of Mike Flynn. But there is no relationship between Snowden’s disclosures of NSA programs and the FBI surveillance that caught Flynn incidentally or FBI’s FISA targeting of Carter Page. And the worst abuses on the Page targeting happened in 2017, under Trump. Crazier still, Trump himself is worse on surveillance issues than Obama was! He has had enemies targeted by contract spies to thwart a peace deal. His DOJ got a Title III warrant on a suspected leaker to capture evidence implicating the journalists he was leaking to. Various of his agencies have been purchasing location data to bypass a Supreme Court prohibition on warrantless surveillance of location. ICE and other agencies have ratcheted up earlier spying on immigrants and those who advocate for them. And Trump’s Attorney General — the guy who unilaterally approved the predecessor of the spying systems Snowden exposed — has said the government doesn’t need Section 215 (one authority Snowden exposed) to conduct the surveillance it had been using it for until March 15, 2020; the suspicion is Barr has resumed reliance on legal claims rejected in 2010. It is, frankly, insane for Glenn to suggest that Trump is better on surveillance than his predecessors.
And while WikiLeaks releases have been embarrassing in certain ways to John Brennan, Jim Comey, and (especially) James Clapper, I’m particularly astounded that Glenn claims that Susan Rice was “exposed” by the releases.
I checked. I found just three Cablegate releases involving Susan Rice. One discusses efforts to remain engaged in the Democratic Republic of Congo. One discusses a meeting between Rice, Dennis Ross, and Ban Ki-moon where Obama’s officials described wanting to establish a bilateral channel with Iran in pursuit of peace.
Ambassador Rice and Special Advisor for the Gulf and Southwest Asia Ambassador Dennis Ross on June 9 met with UN Secretary-General Ban Ki-moon to explain key elements of U.S. diplomatic outreach to Iran and to hear Ban’s assessment. Ambassador Ross explained that President Obama in various fora and particularly from Cairo has made it clear that the USG will engage Iran without any preconditions.
[snip]
Ambassador Ross said the USG values the P5 1 structure for dealing with Iran because it is a statement of the international community’s resolve to deal with the nuclear issue in a coordinated fashion, and he said the USG will be a full participant in the P5 1 structure. Despite its importance, Ambassador Ross said the USG aims to engage Iran bilaterally, because that would allow for a broader treatment of the issues, which is more difficult to achieve in a multilateral context.
And one describes Rice engaging with UN Relief and Works Agency (UNRWA) Director for Gaza John Ging to learn how supporting infrastructure projects in Gaza would counter the growth of Hamas.
In an October 22 meeting with USUN Ambassador Susan Rice, UN Special Coordinator for the Middle East Peace Process (UNSCO) Robert Serry and UN Relief and Works Agency (UNRWA) Director for Gaza John Ging emphasized the need to restart essential infrastructure projects in Gaza, including shelters and schools. As a result of the Israeli “blockade,” both Serry and Ging noted that Hamas now controls Gaza’s tunnel-driven economy, increasing people’s dependency on Hamas. Ging described a population in Gaza suffering from massive physical devastation. He pointed out that while Hamas has all the cement it needs to build a new checkpoint near Erez, the UN cannot get the cement it needs to build a single school. Serry stressed the need for a new strategy on Gaza, suggesting that the current policy has only strengthened Hamas’ position.
In short, purported anti-imperialist Glenn Greenwald claims that Susan Rice was “exposed” because Cablegate revealed her involvement in efforts to make peace in Iran and Gaza.
But Glenn’s lies and exaggerations aren’t the craziest thing about this appearance.
The craziest thing about the appearance is that Glenn doesn’t talk about the danger to journalism of an Assange extradition.
What Glenn does instead of discussing the very real dangers that the Assange extradition poses to journalism is instead push Trump’s buttons — the very same buttons that Sergei Kislyak first started pushing on December 31, 2016, when he called Flynn to tell him that Putin had not retaliated against Obama’s sanctions because, in part, the sanctions were “targeted not only against Russia, but also the president elect.”
KISLYAK: I, I just wanted to tell you that our conversation was also taken into account in Moscow and …
FLYNN: Good
KISLYAK: Your proposal that we need to act with cold heads, uh, is exactly what is uh, invested in the decision.
FLYNN: Good
KISLYAK: And I just wanted to tel I you that we found that these actions have targeted not only against Russia, but also against the president elect.
FLYNN: yeah, yeah
KISLYAK: and and with all our rights to responds we have decided not to act now because, its because people are dissatisfied with the lost of elections and, and its very deplorable. So, so I just wanted to let you know that our conversation was taken with weight.
Glenn’s case — made in an appearance that was transparently an attempt to lobby the President directly — wasn’t about journalism. It was about sticking it to the “tyrannical” civil servants in the Deep State™ who had the audacity to try to protect the country from Russian interference. Glenn pitched this as one more way for Trump to damage Obama (which is presumably why Glenn falsely claimed that Obama was the most embarrassed by the disclosures), spitting out the names — Jim Comey, James Clapper, and Susan Rice’s tyrannical consideration of how to improve life in Gaza — that serve as triggers to the President.
And, remarkably, at a time when all the messaging of WikiLeaks supporters is focused on claiming that Trump has targeted Assange as part of his larger war on the press (a bullshit claim, but politically useful in an effort to mobilize press advocates in support of Assange), Glenn does the opposite, suggesting that Trump wants to pardon Assange (and Snowden), but the Deep State that Trump has been in charge of for 45 months, that Trump has purged of any disloyalty and much competence, is preventing him.
Of course, Tucker knows his audience of one, and so tees this up perfectly, reminding Trump of the only information Assange exposed that Trump cares about: Democratic emails that Russia released to help Trump get elected.
Seven days after the election, Trump’s rat-fucker, Roger Stone, started pursuing a pardon for Julian Assange. I’m increasingly convinced that effort started earlier, as part of Stone’s efforts to optimize the release of the emails in August 2016. Up until now, the overt signs of the effort to pay off Trump’s debt to Assange (and Russia) for help getting elected seemed to cease in 2018, after the nihilistic damage of the Vault 7 releases made such an effort increasingly toxic (and perhaps because the Mueller investigation made it legally dangerous).
But last night, Glenn Greenwald joined Tucker Carlson to renew the effort explicitly, claiming to defend press freedoms but instead pitching it as an opportunity to stick to to a Deep State™ that both Glenn and Trump have inflated so ridiculously that they prefer real tyranny to civil servants pursuing draconian measures within the dregs of law that Trump hasn’t already blown away.
For four years, this campaign debt has been hanging over Trump’s head. And Glenn Greenwald, pushing all the same buttons Russia did starting in 2016, last night moved to close the deal.





![[Photo: National Security Agency, Ft. Meade, MD via Wikimedia]](https://www.emptywheel.net/wp-content/uploads/2017/08/NationalSecurityAgency_HQ-FortMeadeMD_Wikimedia.jpg)