NSA and Compromised Encryption: The Sword Cuts Both Ways
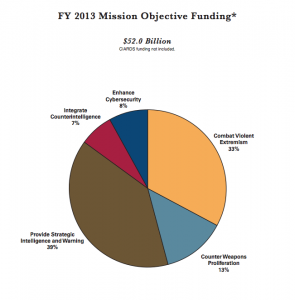
![[Snapshot, Ralph Langner presentation re: Stuxnet, outlining payload extraction (c. 2012 via YouTube)]](http://www.emptywheel.net/wp-content/uploads/2013/09/RalphLangner_StuxnetPresentation_snapshot_275pxw.jpg)
[Snapshot, Ralph Langner presentation re: Stuxnet, outlining payload extraction (c. 2012 via YouTube)]
A friendly handshake is offered;
Names are swapped after entry;
The entrant delivers a present;
The present is unboxed with a secret key…
And * BOOM *
Payload delivered.
This is cyber weapon Stuxnet‘s operations sequence. At two points in the sequence its identity is masked — at the initial step, when identity is faked by a certificate, and at the third step, when the contents are revealed as something other than expected.
The toxic payload is encrypted and cannot be read until after the handshake, the name swap, and then decrypted when already deep inside the computer.
In the wake of the co-reported story on the National Security Agency’s efforts to crack computer and network encryption systems, the NSA claims they are only doing what they must to protect the country from terrorists, criminals, and cyber attacks generated by individuals, groups, and nation-state actors.
Defense, though, is but one side of the NSA’s sword; it has two lethal edges.
While use of encryption tools may prevent unauthorized access to communications, or allow malicious code to be blocked, the same tools can be used to obstruct legitimate users or shut down entire communications systems.
Encryption APIs (ex: Microsoft CryptoAPI embedded in Windows operating systems) are often used by higher level applications — for example, a random number generator within the API used to create unique keys for access can also be used to create random names or select random event outcomes like a roll of the dice.
In Stuxnet alone we have evidence of encryption-decryption used as cyber warfare, the application planned/written/supported in some way by our own government. This use was Pandora’s Box opened without real forethought to the long-term repercussions, including unintended consequences.
We know with certainty that the repercussions weren’t fully considered, given the idiocy with which members of Congress have bewailed leaks about Stuxnet, in spite of the fact the weapon uncloaked itself and pointed fingers in doing so.
One of the unconsidered/ignored/unintended consequences of using weaponry requiring encryption-decryption is that the blade can cut in the other direction.
Imagine someone within the intelligence community “detonating” a cyber weapon built in the very same fashion as Stuxnet.
A knock at the door with a handshake;
Door open, package shoved in, treated as expected goods;
Encrypted content decrypted.
And then every single desktop computer, laptop, netbook, tablet, and smartphone relying on the same standardized, industry-wide encryption tools “detonates,” obstructing all useful information activities from personal and business work to telecommunications. Read more →