As you’ve no doubt heard, the House passed the bad reauthorization to Section 702 yesterday. The Senate will vote on cloture on Tuesday — though both Rand Paul and Ron Wyden have threatened to filibuster it — and will almost certainly be voted into law after that.
I’ll have comment later on the rising costs, for politicians, for mindlessly reauthorizing these bills in a follow-up post.
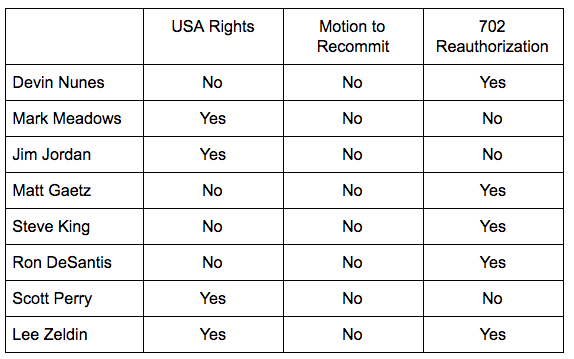
Paul Ryan told President Trump Section 702 hasn’t affected his people
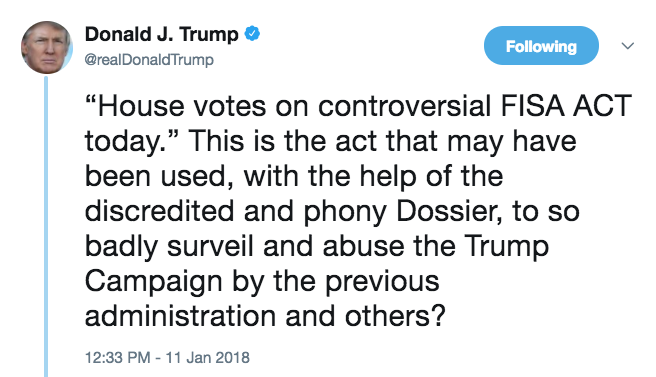
But for the moment, I want to comment on the debate that took place in response to Trump’s two tweets. The first tweet, which was clearly a response to a Judge Napolitano piece on Fox News yesterday morning, complaining about FISA.
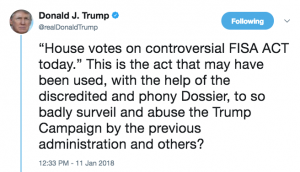
Then, after a half hour lesson from Paul Ryan on the different FISA regimes (note, for some reason Devin Nunes was conspicuously absent from much of this process yesterday, both the coddling of the President and managing debate on the bill), a follow-up tweet hailing Section 702’s utility for “foreign surveillance of foreign bad guys on foreign land.”
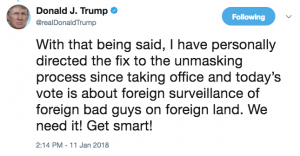
In response to those tweets, many commenters stated, as a matter of fact, that Trump hasn’t been impacted by Section 702, that only traditional FISA intercepts drove key developments in the Russian investigation.
That’s unlikely to be true, and I suspect we already have evidence that that’s not the case.
It is true that incidental collection on a Title I got Mike Flynn in trouble
To defend the case that incidental collection off a traditional FISA order has impacted Trump’s administration, people point to the December 29, 2016 intercepts of communications between Sergey Kislyak and Mike Flynn which were cited in Flynn’s guilty plea. It is true that those intercepts were done under a traditional FISA order. Admiral Mike Rogers as much as confirmed that last March in his efforts to explain basic FISA law to the House Intelligence Committee Republicans who are supposed to oversee it.
Rogers: FISA collection on targets in the United States has nothing to do with 702, I just want to make sure we’re not confusing the two things here. 702 is collection overseas against non US persons.
And Speaker Ryan, fresh off his efforts to teach the President basic surveillance law, yesterday clarified — inaccurately — that,
Title 1 of the FISA law is what you see in the news that applies to U.S. citizens. That’s not what we’re talking about here. This is Title 7, Section 702. This is about foreign terrorists on foreign soil.
Whatever the facts about FISA orders targeting Carter Page and Paul Manafort, the intercepts that have done the most known damage to the Trump Administration so far targeted a foreigner on US soil, Sergey Kislyak, and Flynn just got picked up incidentally.
Papadopoulos’ affidavit and statement of offense make different claims about his false claims and obstruction
But as I said, I suspect it is highly likely the Trump Administration has also been brought down by an American being caught up incidentally in a Section 702 tasking. That’s because of several details pertaining to the George Papadopoulos plea which I nodded to here; they strongly suggest that Papadopoulos’ Facebook communications with Joseph Mifsud were first obtained by the FBI via Section 702, and only subsequently parallel constructed using a warrant. It’s further likely that the FBI obtained a preservation order on Papadopoulos’ Facebook account before he deleted it because of what they saw via Section 702. [Update: KC has alerted me that they may not have gotten a preservation order, but instead were able to access the Facebook account because that content doesn’t all go away when you deactivate an account, which is what the October 5 document describes as happening.]
Compare the two descriptions of how Papadopoulos obstructed justice. The July 28, 2017 affidavit supporting Papadopoulos’ arrest describes Papadopoulos destroying his Facebook account to hide conversations he had with Timofeev.
The next day, on or about February 17, 2017, however, GEORGE PAPADOPOULOS, the defendant, shut down his Facebook account, which he had maintained since approximately August 2005. Shortly after he shut down his account, PAPADOPOULOS created a new Facebook account.
The Facebook account that PAPADOPOULOS shut down the day after his interview with the FBI contained information about communications he had with Russian nationals and other foreign contacts during the Campaign, including communications that contradicted his statements to the FBI. More specifically, the following communications, among others, were contained in that Facebook account, which the FBI obtained through a judicially authorized search warrant.
The affidavit makes it clear that Papadopoulos attempted to hide “his interactions during the Campaign with foreign contacts, including Russian nationals.” The descriptions of the communications that Papadopoulos attempted to hide are described as “a Facebook account identified with Foreign Contact 2,” Timofeev.
The FBI recorded both interviews, suggesting they already by January 27 they had reason to worry that Papadopoulos might not tell the truth.
The October 5 statement of the offense describes one of Papadopoulos’ false statements this way:
PAPADOPOULOS failed to inform investigators that the Professor had introduced him to the Russian MFA Connection [Timofeev], despite being asked if he had met with Russian nationals or “[a]nyone with a Russian accent” during the Campaign. Indeed, while defendant PAPADOPOULOS told the FBI that he was involved in meetings and did “shuttle diplomacy” with officials from several other countries during the Campaign, he omitted the entire course of conduct with the Professor and the Russian MFA Connection regarding his efforts to establish meetings between the Campaign and Russian government officials.
And it describes his obstruction this way:
The next day, on or about February 17, 2017, defendant PAPADOPOULOS deactivated his Facebook account, which he had maintained since approximately August 2005 and which contained information about communications he had with the Professor and the Russian MFA Connection. Shortly after he deactivated his account, PAPADOPOULOS created a new Facebook account that did not contain the communications with the Professor and the Russian MFA Connection.
On or about February 23, 2017, defendant PAPADOPOULOS ceased using his cell phone number and began using a new number.
In neither document does FBI mention having the content of Papadopoulos’ April 2016 Skype calls with Timofeev and neither one cites data — such as texts — that might have been on his cell phone.
What FBI (probably) learned when
While we can’t be sure — after all, the government may simply be withholding more information from other suspects — the differences between the two legal filings and other public information suggest the following evolution in what the government knew of Papadopoulous’ communications with his interlocutors when. Most importantly, the FBI had learned of Papadopoulos’ communications with Joseph Mifsud and Olga Vinogradova before his two interviews, but they had not learned of his communications with Ivan Timofeev.
Late July 2016
In a drunken conversation in May 2016, Papadopoulos told the Australian Ambassador Alexander Downer that he had been told (by Joseph Mifsud, but it’s not clear Papadopoulos would have revealed that) the Russians had dirt on Hillary in the form of emails.
Before January 27, 2017
- Papadopoulos might lie and so should be recorded
- Papadopoulos had interesting communications with Joseph Mifsud and Olga Vinogradova
- Since Timofeev did not come up in the interview, FBI appears not to have learned of those conversations yet
Before February 16, 2017
- Papadopoulos’ Facebook was interesting enough to sustain a preservation request but (because FBI still didn’t know about Timofeev) FBI had not yet accessed its content via Papadopoulos [Though see update above]
- FBI had not yet accessed Skype, which would have shown call records between Timofeev and Papadopoulos
- FBI did not have a warrant on Papadopoulos’ phone and never obtained one before February 23
By July 28, 2017
- FBI had obtained a warrant for Papadopoulos’ email
- FBI had read the Facebook content Papadopoulos tried to delete, discovering the communications (and the relationship) with Timofeev
- FBI had identified the Skype conversations that had taken place, but not in time to collect them using 702
By October 5, 2017
- FBI had obtained far more email from the campaign side
- FBI had discovered that, in addition to destroying his Facebook account, Papadopoulos had also gotten a new phone number (and, I suspect, a new phone), thereby destroying any stored texts on the phone
FBI probably tracked Papadopoulos’ Facebook communications with Mifsud before February 16
Again, this is just a guess, but given the evolution of FBI’s understanding about Papadopoulos laid out above, it seems highly likely that FBI had obtained some (but not all) of Mifsud’s communications before February 16, had submitted preservation requests to Papadopoulos’ providers, but had not yet obtained any legal process for content via Papadopoulos. Given that Papadopoulos’ Facebook content was preserved even in spite of his effort to destroy it, it seems clear the government had reason to know its content was of interest, but it did not yet know about his Facebook communications with Timofeev. This is how FBI routinely launders Section 702 information through criminal process, by getting a warrant for the very same content available at PRISM providers that they already obtained via PRISM. They key detail is that they appear to have known about the content of some but not all of Papadopoulos’ Facebook messages in time to preserve the account before February 16.
This strongly suggests the FBI had obtained Mifsud’s Facebook content, but not Papadopoulos’.
Once FBI opened a full investigation into the Russian ties — which we know they did in late July, in part because of that Papadopoulos conversation about the Mifsud comments — it could task and obtain a raw feed of any known PRISM account for any foreigner overseas associated with that investigation. Once it identified Mifsud as Papadopoulos’ interlocutor — and they would have been able to identify their common relationship from their common front organization, the London Centre of International Law Practice — they would have tasked Mifsud on any identifier they could collect.
And collecting on Facebook would be child’s play — just ask nicely. So it would be shocking if they hadn’t done it as soon as they identified that Mifsud was Papadopoulos’ interlocutor and that he had a Facebook account.
Incidental collection under 702 may have led to the preservation of evidence about the Timofeev relationship Papadopoulos tried to destroy
If all this is right — and it is admittedly just a string of well-educated guesses — then it means FBI’s ability to incidentally collect on Papapdopoulos by targeting Mifsud may have been what led them to take action to preserve Papadopoulos’ Facebook content, and with it evidence of ongoing communications with Timofeev that he had tried to hide.
And the fact that he did try to hide it is what led to Mueller flipping his first cooperating witness.
So if all this is right, then incidental collection on Papadopoulos under Section 702 may be every bit as central to Trump’s legal jeopardy right now as the incidental collection on Flynn under Title I. They’re both critical pieces in proving any hypothetical case that Trump traded policy considerations for the release of Hillary emails.
This is how Section 702 is supposed to work, and could be done under USA Rights
Let me be clear: I’m not saying the discovery of Papadopoulos’ Facebook communications with Mifsud and through them his Facebook communications with Timofeev is an abuse. On the contrary, this is how 702 is supposed to work.
If we’re going to have this program, it should be used to target suspect agents of a foreign power located overseas, as Mifsud clearly was. If he was targeted under 702, he was targeted appropriately.
But there is no reason to believe doing so required any of the more abusive uses of 702 that USA Rights would limit. Unless Mifsud was already tasked at FBI when they opened the investigation in July 2016, there’s no reason to believe this account could have been found off of a back door search at FBI. Mifsud may have been tasked at NSA or even CIA, but if he was, searching on Papadopoulos because the government suspected he was being recruited by a foreign power would fall under known justifications for back door searches at those foreign intelligence agencies (especially at CIA).
USA Rights would permit the use of this 702 information to support the criminal case against Papadopoulos, because it’s clearly a case of foreign government spying.
And no use of the Tor exception would be implicated with this search.
In other words, Section 702 as Ron Wyden and Rand Paul and Justin Amash and Zoe Lofgren would have it would still permit the use of Section 702 as a tool to — ultimately — lead FBI to figure out that Papadopoulos was hiding his contacts with Ivan Timofeev.
As it turns out, the kinds of people Trump’s foreign policy advisor George Papadopoulos was chatting up on Facebook — Joseph Mifsud and Ivan Timofeev — are precisely the kind of people the FBI considers “foreign bad guys on foreign land” for the purposes of Section 702, meaning the Bureau could get their Facebook account quite easily.
And the incidental collection of Americans of such conversations can be — may well have been — as dangerous to Donald Trump as the incidental collection of Americans under Title I.












![[Photo: National Security Agency, Ft. Meade, MD via Wikimedia]](https://www.emptywheel.net/wp-content/uploads/2017/08/NationalSecurityAgency_HQ-FortMeadeMD_Wikimedia.jpg)