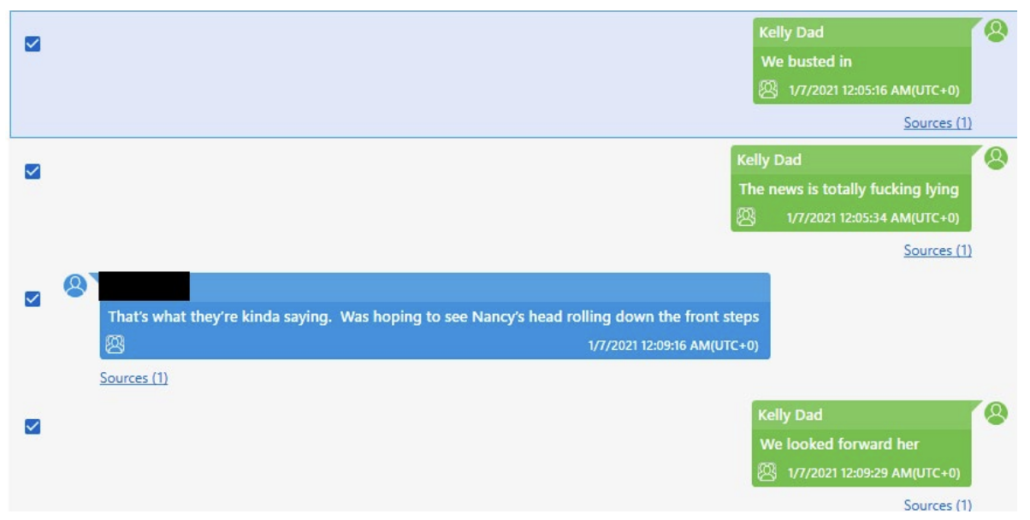
DNC Convention 2024: Day 3
[NB: check the byline, thanks. /~Rayne]
Welcome to Day 3 of Democratic National Committee Convention 2024.
The convention has an umbrella theme, “For the People, For Our Future,” with each successive day having a subset theme.
Day 1 — “For the People” — Joe Biden, keynote speaker
Day 2 — “A Bold Vision for America’s Future’ — Barack Obama, keynote speaker
Day 3 — “A Fight for Our Freedoms” — Tim Walz, keynote speaker <<– YOU ARE HERE
Day 4 — “For Our Future” — Kamala Harris, keynote speaker
Philip Elliot at TIME suggests tonight’s programming will be white man dense because white men were a key voting block which helped Biden win over Trump in 2020 and are still a critical variable in 2024.
Given how often minority groups and women have historically been given short shrift, this approach feels uncomfortable. But if the Democratic Party is to crush Trump and the GOP, no voting bloc should go without outreach, including the Never-Trumpers.
DAY 3 CONVENTION SCHEDULE
Here’s today’s convention schedule (times shown are Central Time):
• 7 a.m.-9:30 a.m.: Delegation breakfasts
• 9 a.m.-10a.m.: Morning press briefing
• 9:30 a.m.-11:30 a.m.: Black Caucus meeting
• 9:30 a.m.-11:30 a.m.: Hispanic Caucus meeting
• 9:30 a.m.-11:30 a.m.: AAPI Caucus meeting
• 9:30 a.m.-11:30 a.m.: Native American Caucus meeting
• 9:30 a.m.-11:30 a.m.: Ethnic Council meeting
• 12 p.m.-1:30 p.m.: Labor Council meeting
• 12 p.m.-1:30 p.m.: LGBTQ+ Caucus meeting
• 12 p.m.-1:30 p.m.: Small Business Council meeting
• 1:45 p.m.-3:15 p.m.: Environmental & Climate Crisis Council meeting
• 1:45 p.m.-3:15 p.m.: Seniors Council meeting
• 6 p.m.-10 p.m.: Main programming
MAIN PROGRAMMING
Main programming has already begun as this post publishes at 7:30 PM ET/6:30 PM CT
Tonight’s schedule (times shown are Central Time):
5:30 PM
Call to Order
• Alex Hornbrook, Executive Director of the 2024 Democratic National Convention CommitteeGavel In
• Sen. Cory Booker (D-NJ)Invocation
• Sri Rakesh Bhatt
• Sri Siva Vishnu Temple
• Bishop Leah D. Daughtry, The House of the Lord ChurchesPledge of Allegiance
• Students from Moreland Arts & Health Sciences Magnet School from St. Paul, MNNational Anthem
• Jess DavisPresentation of Honorary Resolutions
• Jaime Harrison, Chairman of the Democratic National CommitteeJoined by Vice Chairs
• Keisha Lance Bottoms
• Ken Martin
• Henry R. Muñoz III, Treasurer
• Virginia McGregor
• Chris Korge, Finance ChairRemarks
• Mini Timmaraju, President and CEO of Reproductive Freedom for All
• Alexis McGill Johnson, President and CEO of Planned Parenthood Action Fund
• Cecile Richards, Reproductive Rights Champion
• Kelley Robinson, President of the Human Rights Campaign
• Jessica Mackler, President of EMILYs List
• María Teresa Kumar, Founding President and CEO of Voto Latino
• Rep. Tom Suozzi (NY-03)6:00 PM
Welcome Remarks
• Sen. Cory Booker (D-NJ)Joint Remarks
• Aftab Pureval, Mayor of Cincinnati OH
• Cavalier Johnson, Mayor of Milwaukee WI
• Deanna Branch, mother and lead pipe removal advocate
• Rashawn Spivey, plumbing business owner and lead pipe removal advocateRemarks
• Rep. Lisa Blunt Rochester (D-DE At-large District)
• Rep. Grace Meng (NY-Remarks: “Project 2025—Chapter Three: Freedoms”
• Gov. Jared Polis, ColoradoRemarks
• Rep. Debbie Wasserman Schultz (FL-)
• Suzan DelBene, Chair of the Democratic Congressional Campaign Committee
• Keith Ellison, Attorney General of Minnesota
• Dana Nessel, Attorney General of Michigan
• Jon Polin and Rachel Goldberg, Parents of Hersh Goldberg-PolinPerformance
• Maren Morris, American singer-songwriter7:00 PM
Remarks
• Rep. Veronica Escobar (TX-16)
• Sen. Chris Murphy (D-CT)
• Javier Salazar, Sheriff of Bexar County, Texas
• Pete Aguilar, Chair of the House Democratic CaucusInfluencer Remarks
• Carlos Eduardo Espina, Content creatorRemarks
• Olivia Troye, former Trump administration national security official
• Geoff Duncan, former Lt. Governor of Georgia
• Rep. Bennie G. Thompson (MS-02)
• Sergeant Aquilino Gonell, Retired United States Capitol Police Officer
• Rep. Andy Kim, (NJ-03)Influencer Remarks
• Olivia Julianna, Content creatorPerformance
• Stevie Wonder, American singer-songwriter and musicianRemarks
• Kenan Thompson, American comedian and actor and Guests on Project 20258:00 PM
Host Introduction
• Mindy KalingRemarks
• Rep. Hakeem Jeffries, Democratic Leader
• Bill Clinton, 42nd President of the United States
• Rep. Nancy Pelosi, Speaker Emerita (CA-)
• Gov. Josh Shapiro, Pennsylvania
• Alexander Hudlin
• Jasper Emhoff
• Arden Emhoff
• Sen. Catherine Cortez Masto (D-NV)9:00 PM
Performance
• Amanda Gorman, National Youth Poet LaureateRemarks
• Gov. Wes Moore, Maryland
• Pete Buttigieg, Secretary of TransportationPerformance
• John Legend, American singer-songwriter
• Sheila E., American singer and drummerRemarks
• Sen. Amy Klobuchar (D-MN)
• Benjamin C. Ingman, Former student of Governor WalzRemarks
• Gov. Tim Walz, Minnesota, Democratic Party vice presidential nominee and keynote speakerBenediction
• William Emmanuel Hall
• Lead Pastor of St. James Church in Chicago
HOW TO WATCH
See Monday’s Day 1 post for the best channels on which to catch the majority of this evening’s programming.
DNC at United Center-Chicago will stream a live feed from its own website between 7:00 PM to 11:00 PM ET (6:00 PM to 10:00 PM CT) Tuesday through Thursday.
https://demconvention.com/
USA Today will also live stream Tuesday through Thursday.
https://www.youtube.com/@USATODAY/streams – main page
https://www.youtube.com/watch?v=LxBzoWNCWHo – tonight’s feed
The DNC’s convention feeds are:
https://www.youtube.com/@DemConvention – main page
https://www.youtube.com/watch?v=hIoAq_BHNLU – tonight’s feed