Three Months After Problematic John Sipher Post, Just Security Makes Clear It Let Known Errors Sit for Two Months
This post was first published on September 6, the same day John Sipher’s post was published. Because of something that happened today, December 10, I’m reposting it in its entirety, along with the two updates that make it clear when Just Security corrected one of the egregious errors I pointed out on September 6 two months later, around November 4, they didn’t credit me. In other words, they let a significant error sit for two months (and presumably haven’t even reviewed all the other problems I point out here, in spite of an extended conversation Ryan Goodman and I had about this post on September 6). Given the lefties are still making some of the same errors (notably, when Rachel Maddow hid how badly the Steele dossier was on the hack-and-leak by not mentioning the Guccifer 2.0 publications), the continued errors are telling.
If I were to write this post now, it’d show a bunch more problems. But I believe the analysis from September stands up.
I generally find former CIA officer John Sipher’s work rigorous and interesting, if not always persuasive. Which is why I find the shoddiness of this post — arguing, just as Republicans in Congress and litigious Russians start to uncover information about the Christopher Steele dossier, that the dossier is not garbage — so telling.
I don’t think the Steele dossier is garbage.
But neither do I think it supports the claim that it predicted a lot of information we’ve found since, something Sipher goes to great pains to argue. And there are far more problems with the dossier and its production than Sipher, who claims to be offering his wisdom about how to interpret raw intelligence, lets on. So the dossier isn’t garbage (though the story behind its production may well be). But Sipher’s post is. And given that it appears to be such a desperate — and frankly, unnecessary — attempt to reclaim the credibility of the dossier, it raises questions about why he feels the need.
Making and claiming accuracy for a narrative out of raw intelligence
Sipher’s project appears to be taking what he admits is raw intelligence and providing a narrative that he says we should continue to use to understand Trump’s Russian ties.
Close to the beginning of his piece, Sipher emphasizes that the dossier is not a finished intelligence report, but raw intelligence; he blames the media for not understanding the difference.
I spent almost thirty years producing what CIA calls “raw reporting” from human agents. At heart, this is what Orbis did. They were not producing finished analysis, but were passing on to a client distilled reporting that they had obtained in response to specific questions. The difference is crucial, for it is the one that American journalists routinely fail to understand.
[snip]
Mr. Steele’s product is not a report delivered with a bow at the end of an investigation. Instead, it is a series of contemporaneous raw reports that do not have the benefit of hindsight.
Sipher explains that you need analysts to make sense of these raw reports.
The onus for sorting out the veracity and for putting the reporting in context against other reporting – which may confirm or deny the new report – rests with the intelligence community’s professional analytic cadre.
He then steps into that role, an old clandestine services guy doing the work of the analysts. The result, he says, is a narrative he says we should still use — even in the wake of eight months of aggressive reporting since the dossier came out — in trying to understand what went on with the election.
As a result, they offer an overarching framework for what might have happened based on individuals on the Russian side who claimed to have insight into Moscow’s goals and operational tactics. Until we have another more credible narrative, we should do all we can to examine closely and confirm or dispute the reports.
[snip]
Looking at new information through the framework outlined in the Steele document is not a bad place to start.
How to read a dossier
One thing Sipher aspires to do — something that would have been enormously helpful back in January — is explain how an intelligence professional converts those raw intelligence reports into a coherent report. He describes the first thing you do is source validation.
In the intelligence world, we always begin with source validation, focusing on what intelligence professionals call “the chain of acquisition.” In this case we would look for detailed information on (in this order) Orbis, Steele, his means of collection (e.g., who was working for him in collecting information), his sources, their sub-sources (witting or unwitting), and the actual people, organizations and issues being reported on.
He goes to great lengths to explain how credible Steele is, noting even that he “was the President of the Cambridge Union at university.” I don’t dispute that Steele is, by all accounts, an accomplished intelligence pro.
But Sipher unwisely invests a great deal of weight into the fact that the FBI sought to work with Steele.
The fact that the FBI reportedly sought to work with him and to pay him to develop additional information on the sources suggest that at least some of them were worth taking seriously. At the very least, the FBI will be able to validate the credibility of the sources, and therefore better judge the information. As one recently retired senior intelligence officer with deep experience in espionage investigations quipped, “I assign more credence to the Steele report knowing that the FBI paid him for his research. From my experience, there is nobody more miserly than the FBI. If they were willing to pay Mr. Steele, they must have seen something of real value.”
This is flat-out dumb for two reasons. First, it is one of the things the GOP has used to discredit the dossier and prosecution — complaining (rightly) that the FBI was using a document designed as opposition research, possibly even to apply for a FISA warrant. If the FBI did that, I’m troubled by it.
More importantly, the actual facts about whether FBI did pay Steele are very much in dispute, with three different versions in the public record and Chuck Grassley claiming the FBI has been giving conflicting details about what happened (it’s likely that FBI paid Steele’s travel to the US but not for the dossier itself).
WaPo reported that Steele had reached a verbal agreement that the FBI would pay him to continue his investigation of Russia’s involvement with Trump after still unnamed Democrats stopped paying him after the election. CNN then reported that FBI actually had paid Steele for his expenses. Finally, NBC reported Steele backed out of the deal before it was finalized.
If the FBI planned to pay Steele, but got cold feet after Steele briefed David Corn for a piece that made explicit reference to the dossier, it suggests FBI may have decided the dossier was too clearly partisan for its continued use. In any case, citing a “recently retired senior intelligence officer” claiming the FBI did pay Steele should either be accompanied by a “BREAKING, confirming the detail no one else has been able to!” tag, or should include a caveat that the record doesn’t affirmatively support that claim.
After vouching for Steele (again, I don’t dispute Steele’s credentials), Sipher lays out the other things that need to happen to properly vet raw intelligence, which he claims we can’t do.
The biggest problem with confirming the details of the Steele “dossier” is obvious: we do not know his sources, other than via the short descriptions in the reports. In CIA’s clandestine service, we spent by far the bulk of our work finding, recruiting and validating sources. Before we would ever consider disseminating an intelligence report, we would move heaven and earth to understand the access, reliability, trustworthiness, motivation and dependability of our source. We believe it is critical to validate the source before we can validate the reliability of the source’s information. How does the source know about what he/she is reporting? How did the source get the information? Who are his/her sub-sources? What do we know about the sub-sources? Why is the source sharing the information? Is the source a serious person who has taken appropriate measures to protect their efforts?
The thing is, we actually know answers to two of these questions. First, Steele’s sources shared the information (at least in part) because they were paid. [Update, 11/15: According to CNN, Glenn Simpson testified that Steele did not pay his sources. That somewhat conflicts with suggestions made by Mike Morell, who said Steele paid intermediaries who paid his sources, but Simpson’s testimony may simply be a cute legal parse.] That’s totally normal for spying, of course, but if Sipher aspires to explain to us how to assess the dossier, he needs to admit that money changes hands and that’s just the way things are done (again, that’s all the more important given that it’s one of the bases the GOP is using to discredit the report).
More importantly, Sipher should note that Steele worked one step removed — from London, rather than from Moscow — than an intelligence officer otherwise might. The reports may still be great, but that additional step introduces more uncertainty into the validation. It’s all the more important that Sipher address these two issues, because they’re the ones the GOP has been and will continue to use to discredit the dossier.
Ultimately, though, in his section on vetting the document, Sipher doesn’t deal with some key questions about the dossier. Way at the end of his piece, he questions whether we’re looking at the entire dossier.
We also don’t know if the 35 pages leaked by BuzzFeed is the entirety of the dossier. I suspect not.
He doesn’t raise two other key questions about the provenance of the dossier we’ve been given, some of which I laid out when the dossier came out when I also noted that the numbering of the dossier by itself makes it clear it’s not the complete dossier. Importantly: is the copy of the dossier leaked to BuzzFeed an unaltered copy of what Steele delivered to Fusion, in spite of the weird textual artifacts in it? And how and why did the dossier get leaked to BuzzFeed, which Steele has told us was not one of the six outlets that he briefed on its contents.
Finally, Sipher includes the obligation to “openly acknowledge the gaps in understanding” outside of the section on vetting, which is telling given that he notes only a few of the obvious gaps in this dossier.
Sipher claims the dossier predicted what wasn’t known
So there are a lot of aspects of vetting Sipher doesn’t do, whether or not he has the ability to. But having done the vetting of checking Steele’s college extracurricular record, he declares the dossier has proven to be “stunningly accurate.”
Did any of the activities reported happen as predicted?
To a large extent, yes.
The most obvious occurrence that could not have been known to Orbis in June 2016, but shines bright in retrospect is the fact that Russia undertook a coordinated and massive effort to disrupt the 2016 U.S. election to help Donald Trump, as the U.S. intelligence community itself later concluded. Well before any public knowledge of these events, the Orbis report identified multiple elements of the Russian operation including a cyber campaign, leaked documents related to Hillary Clinton, and meetings with Paul Manafort and other Trump affiliates to discuss the receipt of stolen documents. Mr. Steele could not have known that the Russians stole information on Hillary Clinton, or that they were considering means to weaponize them in the U.S. election, all of which turned out to be stunningly accurate.
Now as I said above, I don’t believe the dossier is junk. But this defense of the dossier, specifically as formulated here, is junk. Central to Sipher’s proof that Steele’s dossier bears out are these claims:
- Russia undertook a coordinated and massive effort to disrupt the 2016 U.S. election to help Donald Trump
- The Orbis report identified multiple elements of the Russian operation including
- A cyber campaign
- Leaked documents related to Hillary Clinton
- Meetings with Paul Manafort and other Trump affiliates to discuss the receipt of stolen documents
As I’ll show, these claims are, with limited exceptions, not actually what the dossier shows. Far later into the dossier, the reason Sipher frames it this way is clear. He’s taking validation from recent details about the June 9, 2016 meeting.
Of course, to determine if collusion occurred as alleged in the dossier, we would have to know if the Trump campaign continued to meet with Russian representatives subsequent to the June meeting.
The Steele dossier was way behind contemporary reporting on the hack-and-leak campaign
I consider the dossier strongest in its reports on early ties between Trump associates and Russians, as I’ll lay out below. But one area where it is — I believe this is the technical term — a shit-show is the section claiming the report predicted Russia’s hacking campaign.
Here’s how Sipher substantiates that claim.
By late fall 2016, the Orbis team reported that a Russian-supported company had been “using botnets and porn traffic to transmit viruses, plant bugs, steal data and conduct ‘altering operations’ against the Democratic Party leadership.” Hackers recruited by the FSB under duress were involved in the operations. According to the report, Carter Page insisted that payments be made quickly and discreetly, and that cyber operators should go to ground and cover their tracks.
[snip]
Consider, in addition, the Orbis report saying that Russia was utilizing hackers to influence voters and referring to payments to “hackers who had worked in Europe under Kremlin direction against the Clinton campaign.” A January 2017 Stanford study found that “fabricated stories favoring Donald Trump were shared a total of 30 million times, nearly quadruple the number of pro-Hillary Clinton shares leading up to the election.” Also, in November, researchers at Oxford University published a report based on analysis of 19.4 million Twitter posts from early November prior to the election. The report found that an “automated army of pro-Trump chatbots overwhelmed Clinton bots five to one in the days leading up to the presidential election.” In March 2017, former FBI agent Clint Watts told Congress about websites involved in the Russian disinformation campaign “some of which mysteriously operate from Eastern Europe and are curiously led by pro-Russian editors of unknown financing.”
The Orbis report also refers specifically to the aim of the Russian influence campaign “to swing supporters of Bernie Sanders away from Hillary Clinton and across to Trump,” based on information given to Steele in early August 2016. It was not until March 2017, however, that former director of the National Security Agency, retired Gen. Keith Alexander in Senate testimony said of the Russian influence campaign, “what they were trying to do is to drive a wedge within the Democratic Party between the Clinton group and the Sanders group.”
Here’s what the dossier actually shows about both kompromat on Hillary and hacking.
June 20: In the first report, issued 6 days after the DNC announced it had been hacked by Russia, and 5 days after Guccifer 2.0 said he had sent stolen documents to WikiLeaks, the dossier spoke of kompromat on Hillary, clearly described as years old wiretaps from when she was visiting Russia. While the report conflicts internally, one part of it said it had not been distributed abroad. As I note in this post, if true, that would mean the documents Natalia Veselnitsaka shared with Trump folks on June 9 was not the kompromat in question.
July 19: After Guccifer 2.0 had released 7 posts, most with documents, and after extended reporting concluding that he was a Russian front, the second report discussed kompromat — still seemingly meaning that dated FSB dossier — as if it were prospective.
July 26: Four days after WikiLeaks released DNC emails first promised in mid-June, Steele submitted a report claiming that Russian state hackers had had “only limited success in penetrating the ‘first tier’ of foreign targets. These comprised western (especially G7 and NATO) governments, security and intelligence services and central banks, and the IFIs.” There had been public reports of FSB-associated APT 29’s hacking of such targets since at least July 2015, and public reporting on their campaigns that should have been identified when DNC did a Google search in response to FBI’s warnings in September 2015. It’s stunning anyone involved in intelligence would claim Russia hadn’t had some success penetrating those first tier targets.
Report 095: An undated report, probably dating sometime between July 26 and July 30, did state that a Trump associate admitted Russia was behind WikiLeaks release of emails, something that had been widely understood for well over a month.
July 30: A few weeks before WikiLeaks reportedly got the second tranche of (Podesta) emails, a report states that Russia is worried that the email hacking operation is spiraling out of control so “it is unlikely that these [operations] would be ratcheted up.”
August 5: A report says Dmitry Peskov, who is reportedly in charge of the campaign, is “scared shitless” about being scapegoated for it.
August 10: Just days before WikiLeaks purportedly got the Podesta tranche of emails, a report says Sergei Ivanov said “Russians would not risk their position for the time being with new leaked material, even to a third party like WikiLeaks.”
August 10: Months after a contentious primary and over two weeks after Debbie Wasserman Schultz’s resignation during the convention (purportedly because of DNC’s preference for Hillary), a report cites an ethnic Russian associate of Russian US presidential candidate Donald TRUMP campaign insider, not a Russian, saying the email leaks were designed to “swing supporters of Bernie SANDERS and away from Hillary CLINTON and across to TRUMP.” It attributes that plan to Carter Page, but does not claim any Russian government involvement in that strategy. Nor would it take a genius for anyone involved in American politics to pursue such a strategy.
August 22: A report on Manafort’s “demise” doesn’t mention emails or any kompromat.
September 14: Three months after Guccifer 2.0 first appeared, the dossier for the first time treated the Russians’ kompromat as the emails, stating that more might be released in late September. That might coincide with Craig Murray’s reported contact with a go-between (Murray has been very clear he did not ferry the emails themselves though he did have some contact in late September).
October 12: A week after the Podesta emails first started appearing, a report states that “a stream of further hacked CLINTON materials already had been injected by the Kremlin into compliant media outlets like Wikileaks, which remained at least “plausibly deniable”, so the stream of these would continue through October and up to the election, something Julian Assange had made pretty clear. See this report for more.
October 18, 19, 19: Three reports produced in quick succession describe Michael Cohen’s role in covering up the Trump-Russia mess, without making any explicit (unredacted) mention of emails. See this post on that timing.
December 13: A virgin birth report produced as the US intelligence community scrambled to put together the case against Russia for the first time ties Cohen to the emails in unredacted form).
What the timeline of the hacking allegations in the Steele dossier (and therefore also “predictions” about leaked documents) reveal is not that his sources predicted the hack-and-leak campaign, but on the contrary, he and his sources were unbelievably behind in their understanding of Russian hacking and the campaign generally (or his Russian sources were planting outright disinformation). Someone wanting to learn about the campaign would be better off simply hanging out on Twitter or reading the many security reports issued on the hack in real time.
Perhaps Sipher wants to cover this over when he claims that, “The Russian effort was aggressive over the summer months, but seemed to back off and go into cover-up mode following the Access Hollywood revelations and the Obama Administration’s acknowledgement of Russian interference in the fall, realizing they might have gone too far and possibly benefitted Ms. Clinton.” Sure, that’s sort of (though not entirely) what the dossier described. But the reality is that WikiLeaks was dropping new Podesta emails every day, Guccifer 2.0 was parroting Russian (and Republican) themes about a rigged election, and Obama was making the first ever cyber “red phone” call to Moscow because of Russia’s continued probes of the election infrastructure (part of the Russian effort about which both the dossier and Sipher’s post are silent).
The quotes Sipher uses to defend his claim are even worse. The first passage includes two clear errors. The report in question was actually the December 13 one, not “late fall 2016” one. And the Trump associate who agreed (in the alleged August meeting in Prague, anticipating that Hillary might win) to making quick payments to hackers was Michael Cohen, not Carter Page. [Update, 12/10/17: Just Security has fixed this error.] Many things suggest this particular report should be read with great skepticism, not least that it post-dated both the disclosure of the existence of the dossier and the election, and that this intelligence was offered up to Steele, not solicited, and was offered for free.
Next, Sipher again cites the December 13 report to claim Steele predicted something reported in a November Oxford University report (and anyway widely reported by BuzzFeed for months), which seems to require either a time machine or an explanation for why Steele didn’t report that earlier. He attributes a quote sourced to a Trump insider as indicating Russian strategy, which that report doesn’t support. And if you need Keith Alexander to suss out the logic of Democratic infighting that had been clear for six months, then you’re in real trouble!
Sipher would have been better off citing the undated Report 095 (which is another report about which there should be provenance questions), which relies on the same ethnic Russian Trump insider as the August 10 report, which claims agents/facilitators within the Democratic Party and Russian émigré hackers working in the United States — a claim that is incendiary but (short of proof that the Al-Awan brothers or Seth Rich really were involved) — one that has not been substantiated.
In short, the evidence in the dossier simply doesn’t support the claim it predicted two of the three things Sipher claims it does, at least not yet.
The dossier is stronger in sketchy contacts with Russians
The dossier is stronger with respect to some, but not all Trump associates. But even there, Sipher’s defense demonstrates uneven analytic work.
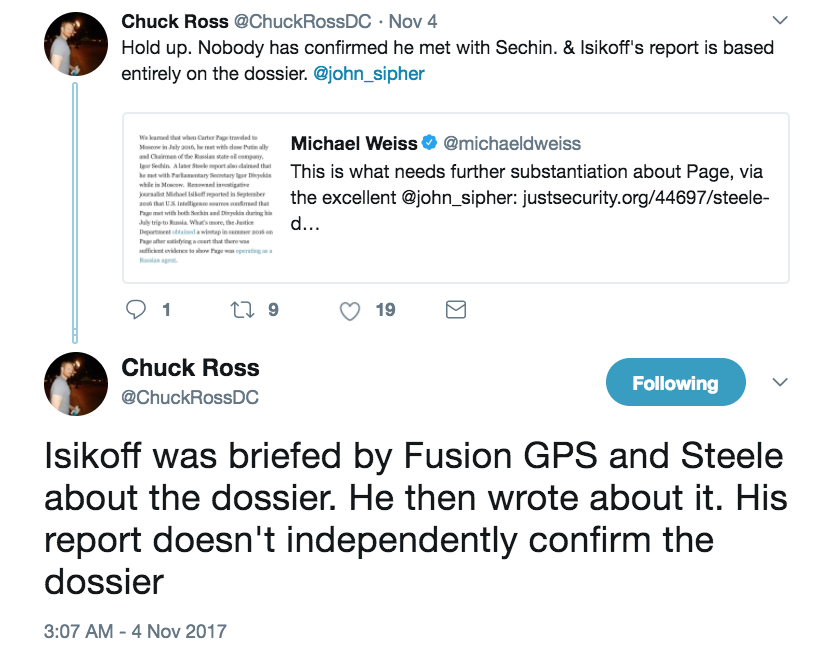
First, note that Sipher relies on “renowned investigative journalist” Michael Isikoff to validate some of these claims.
Renowned investigative journalist Michael Isikoff reported in September 2016 that U.S. intelligence sources confirmed that Page met with both Sechin and Divyekin during his July trip to Russia.
[snip]
A June 2017 Yahoo News article by Michael Isikoff described the Administration’s efforts to engage the State Department about lifting sanctions “almost as soon as they took office.”
Among the six journalists Steele admits he briefed on his dossier is someone from Yahoo.
The journalists initially briefed at the end of September 2016 by [Steele] and Fusion at Fusion’s instruction were from the New York Times, the Washington Post, Yahoo News, the New Yorker and CNN. [Steele] subsequently participated in further meetings at Fusion’s instruction with Fusion and the New York Times, the Washington Post and Yahoo News, which took place in mid-October 2016.
That the Yahoo journalist is Isikoff would be a cinch to guess. But we don’t have to guess, because Isikoff made it clear it was him in his first report after the dossier got leaked.
Another of Steele’s reports, first reported by Yahoo News last September, involved alleged meetings last July between then-Trump foreign policy adviser Carter Page and two high-level Russian operatives, including Igor Sechin — a longtime associate of Russian President Vladimir Putin who became the chief executive of Rosneft, the Russian energy giant.
In other words, Sipher is engaging in navel-gazing here, citing a report based on the Steele dossier, to say it confirms what was in the Steele dossier.
Sipher similarly cites a NYT article that was among the most criticized for the way it interprets “senior Russian intelligence officials” loosely to include anyone who might be suspect of being a spook.
We have also subsequently learned of Trump’s long-standing interest in, and experience with Russia and Russians. A February 2017 New York Times article reported that phone records and intercepted calls show that members of Trump’s campaign and other Trump associates had repeated contacts with senior Russian officials in the year before the election. The New York Times article was also corroborated by CNN and Reuters independent reports.
The two reports he claims corroborate the NYT one fall far short of the NYT claim about talks with Russian intelligence officials — a distinction that is critical given what Sipher claims about Sergey Kislyak, which I note below.
Carter Page
Sipher cites the Carter Page FISA order as proof that some of these claims have held up.
What’s more, the Justice Department obtained a wiretap in summer 2016 on Page after satisfying a court that there was sufficient evidence to show Page was operating as a Russian agent.
But more recent reporting, by journalists Sipher elsewhere cites approvingly, reveals that Page had actually been under a FISA order as early as 2014.
Page had been the subject of a secret intelligence surveillance warrant since 2014, earlier than had been previously reported, US officials briefed on the probe told CNN.
Paul Manafort
I have no complaint with Sipher’s claims about Manafort — except to the extent he suggests Manafort’s Ukrainian corruption wasn’t know long before the election. Sipher does, however, repeat a common myth about Manafort’s influence on the GOP platform.
The quid pro quo as alleged in the dossier was for the Trump team to “sideline” the Ukrainian issue in the campaign. We learned subsequently the Trump platform committee changed only a single plank in the 60-page Republican platform prior to the Republican convention. Of the hundreds of Republican positions and proposals, they altered only the single sentence that called for maintaining or increasing sanctions against Russia, increasing aid for Ukraine and “providing lethal defensive weapons” to the Ukrainian military. The Trump team changed the wording to the more benign, “appropriate assistance.”
Republicans have credibly challenged this claim about the platform. Bob Dole is credited with making the platform far harsher on China in the service of his Taiwanese clients. And Trump’s team also put in language endorsing the revival of Glass-Steagall, with support from Manafort and/or Carl Icahn.
Michael Cohen
Sipher’s discussion of Trump lawyer Michael Cohen is the weirdest of all, not least because the Cohen reports are the most incendiary but also because they were written at a time when Steele had already pitched the dossier to the media (making it far more likely the ensuing reports were the result of disinformation). Here’s how Sipher claims the Steele dossier reports have been validated.
We do not have any reporting that implicates Michael Cohen in meetings with Russians as outlined in the dossier. However, recent revelations indicate his long-standing relationships with key Russian and Ukrainian interlocutors, and highlight his role in a previously hidden effort to build a Trump tower in Moscow. During the campaign, those efforts included email exchanges with Trump associate Felix Sater explicitly referring to getting Putin’s circle involved and helping Trump get elected.
Go look at that “recent revelations” link. It goes to this Josh Marshall post which describes its own sourcing this way:
TPM Reader BR flagged my attention to this 2007 article in The New York Post.
[snip]
Because two years ago, in February 2015, New York real estate trade sheet The Real Deal reported that Cohen purchased a $58 million rental building on the Upper East Side.
This is not recent reporting!! Again, this is stuff that was publicly known before the election.
More importantly, given Cohen’s rebuttal to the dossier, Marshall supports a claim that Cohen has ties to Ukraine, not Russia. The dossier, however, claims Cohen has ties to the latter, as Cohen mockingly notes.
Felix Sater
Then there are the Trump associates who are now known to have been central to any ties between Trump and the Russians that the Steele dossier didn’t cite — as least not as subjects (all could well be sources, which raises other questions). The first is Felix Sater, whom Sipher discusses three times in suggesting that the dossier accurately predicts Cohen’s involvement in the Russian negotiations.
To take one example, the first report says that Kremlin spokesman Dmitry Peskov was responsible for Russia’s compromising materials on Hillary Clinton, and now we have reports that Michael Cohen had contacted Peskov directly in January 2016 seeking help with a Trump business deal in Moscow (after Cohen received the email from Trump business associate Felix Sater saying “Our boy can become president of the USA and we can engineer it. I will get all of Putins team to buy in on this.”).
[snip]
Following the inauguration, Cohen was involved, again with Felix Sater, to engage in back-channel negotiations seeking a means to lift sanctions via a semi-developed Russian-Ukrainian plan (which also included the hand delivery of derogatory information on Ukrainian leaders) also fits with Orbis reporting related to Cohen.
Given that Sater’s publicly known links between mobbed up Russians and Trump go back a decade, why isn’t he mentioned in the dossier? And why does the dossier seemingly contradict these claims about an active Trump Tower deal?
Aras Agalarov and Rinat Akhmetshin
There are far more significant silences about two other Trump associates, Aras Agalarov and Rinat Akhmetshin.
To be fair, the dossier isn’t entirely silent about the former, noting in at one place that Agalarov would be the guy to go to to learn about dirt on Trump in Petersburg (elsewhere he could be a source).
Far, far more damning is the dossier’s silence (again, at least as a subject rather than source) about Akhmetshin. That’s long been one of the GOP complaints about the dossier — that Akhmetshin was closely involved with Fusion GPS on Magnitsky work in parallel with the Trump dossier, which (if Akhmetshin really is still tied to Russian intelligence) would provide an easy feedback loop to the Russians. The dossier’s silence on someone well known to Fusion GPS is all the more damning given the way that Sipher points to the June 9 meeting (which the dossier didn’t report, either) as proof that the dossier has been vindicated.
It was also apparently news to investigators when the New York Times in July 2017 published Don Jr’s emails arranging for the receipt of information held by the Russians about Hillary Clinton. How could Steele and Orbis know in June 2016 that the Russians were working actively to elect Donald Trump and damage Hillary Clinton?
[snip]
To take another example, the third Orbis report says that Trump campaign manager Paul Manafort was managing the connection with the Kremlin, and we now know that he was present at the June 9 2016 meeting with Donald Trump, Jr., Russian lawyer Natalia Veselnitskaya and Rinat Akhmetshin, who has reportedly boasted of his ties to ties and experience in Soviet intelligence and counterintelligence. According to a recent New York Times story, “Akhmetshin told journalists that he was a longtime acquaintance of Paul J. Manafort.”
There’s no allegation that investigations didn’t know about June 2016 plan to hurt Hillary (indeed, the Guccifer 2.0 stuff that Sipher ignores was public to all). Rather they didn’t know — but neither did Fusion, who has an established relationship with Akhmetshin — about the meeting involving Akhmetshin. If you’re going to claim the June 9 meeting proves anything, it’s that the dossier as currently known has a big hole right in Fusion’s client/researcher list.
Sergey Kislyak
Which brings me — finally! — to Sipher’s weird treatment of Sergey Kislyak. Sipher argues (correctly) that Trump associates’ failure to report details of their contacts with Russians may support a conspiracy claim.
Of course, the failure of the Trump team to report details that later leaked out and fit the narrative may make the Steele allegations appear more prescient than they otherwise might. At the same time, the hesitancy to be honest about contacts with Russia is consistent with allegations of a conspiracy.
Of course, Trump’s folks have failed to report details of that June 9 meeting as well as meetings with Sergey Kislyak. Having now invested his vindication story on that June 9 meeting, he argues that reports about Kislyak (on which the NYT article he cites approvingly probably rely) are misguided; we need to look to that June 9 meeting intead.
It should be noted in this context, that the much-reported meetings with Ambassador Kislyak do not seem to be tied to the conspiracy. He is not an intelligence officer, and would be in the position to offer advice on politics, personalities and political culture in the United States, but would not be asked to engage in espionage activity. It is likewise notable that Ambassador Kislyak receives only a passing reference in the Steele dossier and only having to do with his internal advice on the political fallout in the U.S. in reaction to the Russian campaign.
Of course, to determine if collusion occurred as alleged in the dossier, we would have to know if the Trump campaign continued to meet with Russian representatives subsequent to the June meeting.
This seems utterly bizarre. We know what happened after June 9, in part: Per Jared Kushner (who also is not mentioned in the dossier or Sipher’s column), immediately after the election Kislyak started moving towards meeting about Syria (not Ukraine). But in the process, Kushner may have asked for a back channel and at Kislyak’s urging, Kushner took a meeting with the head of a sanctioned bank potentially to talk about investments in his family’s debt-ridden empire. And all that is the lead-up to the Mike Flynn calls with Kislyak about sanctions relief which provide some of the proof that Trump was willing to deliver the quo that the dossier claims got offered for quids.
That latter story — of the meetings Kushner and Flynn did in the wake of the election and events that may have taken place since — is every bit as coherent a narrative as the Steele dossier or the entirely new narratives tied to the June 9 meeting (which Sipher claims are actually the Steele narrative).
Of course, neither is yet evidence of collusion. And that’s, frankly, what we as citizens should be after.
A narrative offered up by an intelligence contractor who was always trying to catch up to the central part of the story — the hack-and-leak — is not what we should be striving for. That’s why this dossier is probably mostly irrelevant to the Mueller probe, no matter how the GOP would like to insinuate the opposite. If there was collusion (or rather, coordination on all this stuff between the campaign and Russia), we should expect evidence of it. The Steele dossier, as I have noted, left out one of the key potential proofs of that, in spite of having ties with someone who attended the meeting.
All that said, it would be useful for someone responsible to respond to GOP criticisms and, where invented (such as with the claim that Steele paying sources diminishes its value), demonstrate that. It would be useful for someone to explain what we should take from the dossier.
Sipher didn’t do that, though. Indeed, his post largely suffers from the same bad analysis he accuses the media of.
Update: In the original I got the date of the final report incorrect. That has been corrected.
Update, 12/10/17: I didn’t realize it, but Just Security updated Sipher’s post to include this language, which it explains with an editor’s note saying “Editor’s note: This article was update to provide additional analysis on Carter Page.” Compare this with this. Here’s the language.
Admittedly, Isikoff’s reporting may have relied on Steele himself for that information. Isikoff, however, also reported that U.S. intelligence officials were confident enough in the information received about Page’s meeting Russian officials to brief senior members of Congress on it. There are also other indicia that are also consistent with the Orbis report but only developed or discovered later. In early December 2016, Page returned to Moscow where he said he had “the opportunity to meet with an executive from” Sechin’s state oil company. In April 2017, Page confirmed that he met with and passed documents to a Russian intelligence officer in 2013. Court documents include an intercept in April 2013 of conversations between the Russians discussing their effort to recruit Page as “as an intelligence source.” A Russian intelligence officer said of Page: “He got hooked on Gazprom … I don’t know, but it’s obvious that he wants to earn lots of money … For now his enthusiasm works for me. I also promised him a lot … You promise a favor for a favor. You get the documents from him and tell him to go fuck himself.” In late December 2016, Sechin’s chief of staff, Oleg Erovinkin “who may have been a source for ex-British spy Christopher Steele’s Trump dossier,” according to multiple reports, was found dead in the back of his car in Moscow.
But this passage introduces new errors for Sipher’s post!
First, here’s the language (in an article Just Security never links) Sipher relies on to justify using Isikoff’s Steele-based reporting to claim Steele had been proven correct.
After one of those briefings, Senate minority leader Harry Reid wrote FBI Director James Comey, citing reports of meetings between a Trump adviser (a reference to Page) and “high ranking sanctioned individuals” in Moscow over the summer as evidence of “significant and disturbing ties” between the Trump campaign and the Kremlin that needed to be investigated by the bureau.
Some of those briefed were “taken aback” when they learned about Page’s contacts in Moscow, viewing them as a possible back channel to the Russians that could undercut U.S. foreign policy, said a congressional source familiar with the briefings but who asked for anonymity due to the sensitivity of the subject. The source added that U.S. officials in the briefings indicated that intelligence reports about the adviser’s talks with senior Russian officials close to President Vladimir Putin were being “actively monitored and investigated.”
A senior U.S. law enforcement official did not dispute that characterization when asked for comment by Yahoo News. “It’s on our radar screen,” said the official about Page’s contacts with Russian officials. “It’s being looked at.”
It is true that “U.S. intelligence officials were confident enough in the information received about Page’s meeting Russian officials to brief senior members of Congress on it,” and that Harry Reid was leaking from the Steele dossier just like Isikoff was. But the “senior US law enforcement officer” does not back the identities of those Page met with, just that “it’s being looked at.”
That’s important for the way that Page’s meetings with people other than Igor Sechin have been used to claim the dossier has borne out. Not-A = A. Which is what Sipher does here, by pointing to Page saying he met with Rosneft but not Sechin. “Page says he was not referring to Sechin in his remarks,” the linked AP story says (as does Page’s congressional testimony).
Then Sipher points to language unsealed in a court filing in January 2015 that Page admitted — after reporting on it — was him. That Page was wrapped up in an earlier Russian spy prosecution is another of those things one might ask why Steele didn’t know, particularly given that the filing and the case was already public.
But the citation also exacerbates the problems with Sipher’s reliance on Page’s FISA wiretap as proof the Steele dossier proved out. As I noted above, later reports stated Page had been under FISA wiretap “since 2014, earlier than had been previously reported, US officials briefed on the probe told CNN.” That means it wasn’t the meetings in Russia, per se, that elicited the interest, but (at least) the earlier interactions with Russian spies.
Finally, Sipher points to the death of Oleg Erovinkin, something I’ve pointed to myself (and which would only be “Carter Page” analysis if Page actually had met with Sechin). Since Sipher updated this post, however, Luke Harding wrote (on page 101),
Steele was adamant that Erovinkin wasn’t his source and “not one of ours.”
As a person close to Steele put it to me: “Sometimes people just die.”
I’m not sure I find Harding entirely reliable elsewhere, and I can see why Steele would deny working with Erovinkin if the leak of his work had gotten the man killed. But if you buy Harding, then Erovinkin no longer proves the value of the Steele dossier either.
Update, 12/10: According to the Wayback Machine this change was made between October 25 and November 6. Ryan Goodman explained that he didn’t give me a hat-tip for this correction because he’s not sure whether he corrected because of me because a Daily Caller reporter also weighed in.
It is true that Chuck Ross (with whom I discuss the dossier regularly) tweeted that Sipher’s Isikoff reference was self-confirming on November 4, shortly before the change was made.
Ryan and I had a conversation about the errors in this piece on September 6, when the post first came out, both on Twitter then–late that evening–on DM. I included a link to my post and he said he was going to read it.
I guess Ryan is now confessing he never read this post, and let notice of egregious errors sit unreviewed for two months, because he didn’t like my tone.