Fun with Dr. Corsi’s “Forensics”!
By far the most ridiculous part of Jerome Corsi’s book is where he spends an entire chapter pretending that he figured out on his own that WikiLeaks had John Podesta’s emails rather than being told that by someone whose identity he’s trying to avoid sharing with Mueller’s team.
The chapter is one of three in the book that he presents as having been written in real time, effectively as diary entries. Corsi presents it as the fevered narrative he writes on November 18, 2018, at a time when Mueller’s team was cracking down on him for his continued lies but before he refused the plea deal, after a night of nightmares.
Last night, I was plagued by nightmares that caused me to sleep very poorly.
His change in voice is followed with an even more direct address to readers, which he returns to as an interjection in the middle of his crazed explanation.
I am going to write this chapter to explain to you, the reader, how I used my basic intuitive skills as a reporter to figure out in August 2016 that Assange had Podesta’s emails, that Assange planned to start making the Podesta file public in October 2016, and that Assange would release the emails in a serial, day-by-day fashion, right up to election day.
[snip]
Now, I know this is tedious and will tax many readers, so I’ve decided here to take a break. You have to understand what I am going through is a roller-coaster. Sometimes I feel like everything is normal and that the federal government will understand that I am a reporter and should be protected by the First Amendment. Then, I realize that the next ring of the doorbell could be the FBI seeking to handcuff me and arrest me in full view of my family.
Resuming after a much-needed break, we need only a few more dates to complete the analysis.
The chapter consists of three things, none of which even remotely presents a case for how he could have concluded WikiLeaks was sitting on John Podesta’s emails:
- An argument that claims he simply reasoned it all out, without proof
- A chronology that makes no sense given the July and August 2016 emails he’s trying to explain away
- Other crap theories designed to undermine Mueller’s argument about Russian involvement, most of which post-date the date when Corsi claims to have figured out the Podesta emails were coming
Corsi’s “argument”
Corsi’s main argument is this:
Clearly, I reasoned there had to have been Podesta emails on that server that would have discussed the Clinton/DNC plot to deny Bernie Sanders the Democratic Party presidential nomination in 2016. Where were these Podesta emails, I wondered?
[snip]
I felt certain that if Assange had Podesta’s emails he would wait to drop them in October 2016, capturing the chance to stage the 2016 “October Surprise,” a term that had been in vogue in U.S. presidential politics since 1980 when Jimmy Carter lost re-election to Ronald Reagan, largely because the Reagan camp finessed Ayatollah Khomeini to postpone the release of the hostages from the American embassy in Tehran until after that year’s November election. I also figured that Assange would release the Podesta emails in drip-drip fashion, serially, over a number of days, stretching right up to the Election Day. In presidential politics, the news cycle speeds up, such that what might take a month or a week to play out in a normal news cycle might take only a day or two in the heightened intensity of a presidential news cycle—especially a presidential news cycle in October, right at Election Day is nearing.
In spite of his claims, elsewhere, to have done forensic analysis that told him John Podesta’s emails were coming, ultimately his argument boils down to this: he figured out that Podesta’s emails (which he purportedly hadn’t read) would be the most damning possible thing and therefore WikiLeaks must have and intend to release them in a serial release because it made sense.
Corsi’s chronology
From there, Corsi proceeds to spin out the following bullshit about how he came to that conclusion:
- Starting in February 2016, a woman named LH whose ex-husband was a former top NSA figure told him [why?] incorrect things about how the Democrats organize their servers. This information seems to be inflected by the flap over VAN space the previous December, but Corsi doesn’t mention that. This information is wrong in many of the ways later skeptics of the Russian hack would be wrong, but Corsi claims he had that wrong understanding well in advance of the crowd.
- When Assange announced on June 12 that he had upcoming Hillary leaks, Corsi was “alerted to the possibility Assange had obtained emails from the DNC email server,” which he took to mean VAN.
- When the WaPo reported on the DNC hack on June 14, 2016, Corsi took Democrats’ (false) reassurances about financial data to be true, matched it to his incorrect claimed understanding of how the Democrats organized their data, and assumed VAN had been hacked (this is the day before Guccifer 2.0 would claim he got in through VAN, remember). Corsi also claims to have noted from the WaPo story that Perkins Coie and Crowdstrike were involved, the latter of which he tied to Google’s Eric Schmidt (who was helping Dems on tech), which together he used to suggest that in real time he believed the Democrats had “manufactured” evidence to pin the hack on the Russians. Again, Corsi is suggesting he got to the conspiracy theories it took the rest of Republicans a year to get to, but in real time.
- Corsi incorrectly read the Crowdstrike white paper (on which the WaPo story was obviously based and which Ellen Nakashima had had for about a week, and which includes an update written in response to the appearance of Guccifer 2.0) as a response to Guccifer 2.0’s post on June 15 and — in spite of the WaPo report that Cozy Bear had been “monitoring DNC’s email and chat communications” — concluded that the hackers had not taken email.
- After the DNC emails were released, Corsi had what he claims was his big insight: that these emails largely came from DNC’s Comms Director and their finance staffers, which meant Podesta’s (and DWS’, which he logically should but did not, pursue) had to be what was left. Mind you, the former point is something WikiLeaks made clear on its website:
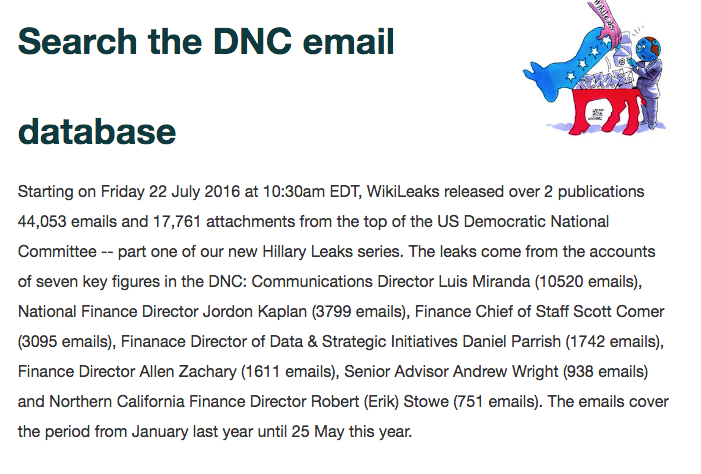
On July 22, 2016, Wikileaks began releasing over two days a total of 44,053 emails and17,761 email attachments from key figures in the DNC. What I noticed immediately was that the largest number of emails by far came from DNC Communications Director Luis Miranda (10,520 emails), who had approximately three-times the emails released for the next highest on the list, National Finance Director Jordon Kaplan (3,799 emails) and Finance Chief of Staff Scott Corner (3,095 emails). What I noticed immediately was that emails from Debbie Wasserman Schultz and John Podesta were missing. Yet, by analyzing the addresses in the emails, it was clear the “From,” “To,” and or “CC” listings indicate the email was sent by or to an addressee using the DNC email server, identified as @dnc.org.
- In his narrative of how he “figured out” there must be Podesta emails, he relies not on the July 25 NBC story he cites earlier in his book, quoting Assange saying there was “no proof” the emails came from Russia (and suggesting his set were a different one than the ones analyzed by cybersecurity experts), but a CNN story he dates to July 26 but which got updated early morning July 27, citing Assange saying, “Perhaps one day the source or sources will step forward and that might be an interesting moment some people may have egg on their faces. But to exclude certain actors is to make it easier to find out who our sources are;” Corsi also cites a July 27 NYMag story citing the CNN one. Corsi claims that as he was listening to this interview, he realized that Assange had Podesta emails “lifted from the DNC server,” which would be incorrect even if it were true, given that Podesta’s emails were from his Gmail account.
Listening to this interview on CNN, all the pieces fit in place for me. Assange had Podesta emails that were also lifted from the DNC server and these were the emails he was holding to drop later in the campaign.
- Corsi describes “the last piece of the puzzle” to be Seth Rich’s death on July 10, 2016, but which occurred before Assange’s post DNC release interviews, in one of which Assange suggested his sources were still alive to “step forward,” then points to Assange’s offer of a reward for information leading to a conviction on August 9. This happened after he had already suggested to Stone that Podesta’s emails were coming.
None of this explains how Corsi would not have decided that Clinton Foundation emails were what was missing, which is what Stone believed when he instructed Corsi to reach out to Ted Malloch on July 25, the day before the Assange interviews Corsi says led him to conclude WikiLeaks instead had Podesta’s emails. And much of it assumes that a unified hack occurred (otherwise it would be impossible to decide what was coming from what had already been released), an assumption he claims not to believe in much of the rest of his crap.
Corsi’s crap
In addition to that chronology, though, Corsi throws in a bunch of crap meant to discredit the evidence laid out in the Mueller GRU indictment. Much of this evidence post-dates the moment he claims he figured out that WikiLeaks had Podesta’s emails, which makes it irrelevant to his theory, nevertheless Corsi throws it out there.
- Corsi takes the Guccifer 2.0 leak of DCCC files to Aaron Nevins — which didn’t happen until over a month after he told Stone that WikiLeaks had Podesta emails — to be “proof” not just that Guccifer 2.0 only hacked DNC files, which he again asserts incorrectly came from VAN, but also that Guccifer 2.0 had not hacked emails.
- Corsi claims that Guccifer 2.0 “never bragged that he hacked the DNC email server that contained the Podesta emails,” even though Guccifer 2.0 did brag that WikiLeaks had published documents he gave them after the DNC leak.
- Corsi claims that Guccifer 2.0 published donor lists and voter analysis at DCLeaks, which is generally inaccurate (indeed, some Podesta files came out via DCLeaks!), but also admits a tie between Guccifer 2.0 and DCLeaks that would either rely on contemporary reporting that asserted a tie, the GRU indictment, or some personal knowledge not otherwise explained.
- Corsi claims that, unlike Marcel Lazar, “Guccifer 2.0 has never been positively identified let alone arrested,” without explaining how he’s sure that the 12 GRU officers Mueller indicted don’t amount to positively identifying the people running Guccifer 2.0. Indeed, rather than addressing that indictment, Corsi instead tries to rebut the Intelligence Community Assessment’s “high confidence” attribution of Guccifer 2.0 to GRU, which he claims relies on ‘tradecraft’ that relies on circumstantial evidence at best, presuming a hacker leaves a signature.” In the ICA, that discussion appears in a section that also notes that “Some analytic judgments are based directly on collected information,” as the Mueller indictment makes clear the GRU one was.
- Corsi claims the Vault 7 release suggesting the CIA has a tool to falsely attribute its own hacks “undermined” the IC’s attribution of Cozy Bear and Fancy Bear, without realizing that’s a different issue from whether the CIA, NSA, and FBI can correctly attribute the hack (though if the Russians obtained those files in the weeks after Joshua Schulte allegedly stole them in 2016, it would have made it harder for CIA to chase down the Russians).
- Corsi initially argues, providing no evidence except that he’s sure the DNC emails come from the DNC email server and not NGP-VAN or Hillary’s private server, that, “While the DNC email server could have been hacked by an outside agent, what is equally plausible is that the emails could have been stolen by someone on the inside of the DNC, perhaps an employee with their own @dnc.org email address.” He then feeds the Seth Rich conspiracy.
- Corsi uses what he claims to have learned about serialization in a college course covering Dickens (but details of which, regarding the history of Dickens’ serialization, he gets entirely wrong) to explain how he knew the Podesta emails would come out in a serialized release.
- Corsi dismisses the possibility the Russians used a cut-out with this garble:
The attempt to distinguish is disingenuous, suggesting the Russians may have been responsible for the hack, turning the information to a third party, not the Russians or a state actor, who handed WikiLeaks the emails and thus became “the source.”
- Corsi cites the Nation’s August 9, 2017 version of the Bill Binney theory purportedly proving that a set of files purporting to be from the DNC — which were never released by WikiLeaks — were copied inside the US and also noting that the Russian metadata in the first Guccifer 2.0 documents was placed there intentionally. As I noted at the time, the two theories actually don’t — at all — disprove the claim that Russia hacked the DNC. But they’re even worse for Corsi’s claims, because (even though the set of files were called NGP/VAN) they undermine his false claim about the Democrats’ servers and they acknowledge that the files he said disproved that Guccifer 2.0 had Podesta files actually were Podesta files.
These things are utterly irrelevant to the soundness of Corsi’s own claim to have been able to guess that the Podesta emails were coming and — as I note — a number of them sharply contradict what he claims to believe.
Corsi’s mistaken notion of his role in proving “collusion”
But the crap does serve Corsi’s larger point, which is to undermine what he imagines Mueller’s theory of “collusion” to be.
Mueller & Company had decided the Trump campaign somehow encouraged Russia to steal the DNC emails and give them to Assange, so WikiLeaks could publish them. Then to establish “Russian collusion” with the Trump campaign, Mueller was out to connect his own dots. The Mueller prosecutors had been charged with the mission to grill me until
I would “give up” my source to Assange. I was their critical “missing link.” If Rhee, Zelinsky, and Goldstein only got me to confess, Mueller figured he could connect the dots from Roger Stone to me to Assange, and from Assange back again to me, and from me to Roger Stone, who would feed the information to Steve Bannon, then chairing the Trump campaign.
The final dots, the Mueller prosecutors assumed, would connect Bannon to Trump and the “Russian collusion” chain of communication would be complete. The only problem was that I did not have a source connecting me to Assange, so Mueller’s chain-link narrative does not connect.
While I actually think it possible that Corsi’s shenanigans may have harmed the neatness of Mueller’s case against Stone, perhaps even leading Mueller to charge Stone only with the obstruction charges rather than in a larger conspiracy, it doesn’t affect the understanding with which Mueller seems to be approaching the Don Jr side of any conspiracy, in which Trump’s son accepted a meeting offering dirt, thinking the family might make $300 million off it, and promised policy considerations that — even before he was sworn into office — his father took steps to pay off.
That conspiracy remains, even if Mueller can’t show that at the same time, Trump was maximizing the advantage of the WikiLeaks releases via his old political advisor Roger Stone.
But who knows? Perhaps Mueller may one day prove that, too?
One other thing that’s worth noting, however: As I laid out above, Corsi doesn’t just attempt to explain how he came to guess that WikiLeaks would release John Podesta’s emails. In the guise of doing that, he lays out what amounts to the Greatest Hits of the Denialist Conspiracies, throwing every possible claim mobilized to undermine the conclusion that Russia hacked the Democrats out there, even the ones that undermine Corsi’s own claimed beliefs.
And, as Corsi himself notes, Mueller has Corsi’s Google searches.
Truthfully, I was astounded because it seemed as if the FBI had studied me down to knowing the key strokes that I had used on my computer to do Google searches for articles. I realized my Google file would have much information about my locations and my Internet searches, but the way Zelinsky drilled down on how I wrote this article was shocking.
Repeatedly Zelinsky had warned me that I had no idea how truly extensive the Special Counselor’s investigation had been. Now, I imagined an army of FBI computer specialists at Quantico mapping out my every electronic communication in 2016, including my emails, my cellphone calls, and my use of the laptop and the Internet to conduct my research and write my various articles and memos.
They actually know whether he read this stuff (notably, the NBC, CNN, and NYMag articles he cites from late July 2016) in real time or only after the fact. They know when Corsi downloaded a bunch of other things (including the Guccifer 2.0 releases), and they know whether he read the GRU indictment. The FBI has also likely obtained what he was doing in November, 2018, as he was writing this stuff.
So it may be that when Corsi’s book comes out in hard cover on March 12, Mueller’s team will already have put together the forensic evidence to prove that Corsi’s claims about how he came by his own forensic analysis — and the rest of these conspiracies — are absolute bullshit. It is, admittedly, frightening how much the government can obtain about our contemporaneous thinking.
But it would be an ironic and just outcome for Corsi if Mueller’s best demonstration about the power of FBI’s forensic analysis comes not in the GRU indictment Corsi so studiously avoided mentioning in the entire book attempting to discredit it, but in proving Corsi’s own claims about forensics to be utterly false.
Corsi’s Timeline
March 16, 2016: WikiLeaks indexes FOIAed Hillary emails
June 12, 2016: Assange announces he has more information on Hillary
In that interview, Assange disclosed that WikiLeaks has “upcoming leaks in relation to Hillary Clinton,” though Assange distinguished the Hillary Clinton emails WikiLeaks possessed pending publication came from a different source than the emails from Hillary’s private email server. This alerted me to the possibility Assange had obtained emails from the DNC email server.
June 14, 2016: WaPo announces the DNC hack
June 15, 2016: Crowdstrike publicly releases white paper on DNC hack and Guccifer 2.0 first posts
July 10, 2016: Seth Rich’s murder
July 22, 2016: WikiLeaks releases the DNC emails
July 25, 2016: Stone emails Corsi asking him to Get to Assange to “get the pending WikiLeaks emails;” Corsi forwards the email to Ted Malloch
July 26, 2016: Assange tells CNN a lot more material is coming and refuses to exclude Russia as a source because “to exclude certain actors is to make it easier to find out who our sources are”
July 28, 2016: Corsi and his wife leave for Italy
July 31, 2016: Stone emails Corsi to “call me MON” instructing him to get Malloch to see Assange
August 2, 2016: Corsi emails Stone,
Word is friend in embassy plans 2 more dumps. One shortly after I’m back. 2nd in Oct. Impact planned to be very damaging.… Time to let more than Podesta to be exposed as in bed w enemy if they are not ready to drop HRC. That appears to be the game hackers are now about. Would not hurt to start suggesting HRC old, memory bad, has stroke — neither he nor she well. I expect that much of next dump focus, setting stage for Foundation debacle.
August 9, 2016: WikiLeaks offers $20,000 reward for information leading to conviction for murder of Seth Rich
August 12, 2016: Corsi returns from Italy
March 7, 2017: WikiLeaks starts to release Vault 7 documents, including an Umbrage file showing that CIA uses disinformation to hide which attacks it launches
May 25, 2017: WSJ reports on Aaron Nevins files that Guccifer 2.0 noted in real time; Corsi deems this (in a Murdoch paper) to be part of the anti-Stone narrative
As I disclosed last July, I provided information to the FBI on issues related to the Mueller investigation, so I’m going to include disclosure statements on Mueller investigation posts from here on out. I will include the disclosure whether or not the stuff I shared with the FBI pertains to the subject of the post.