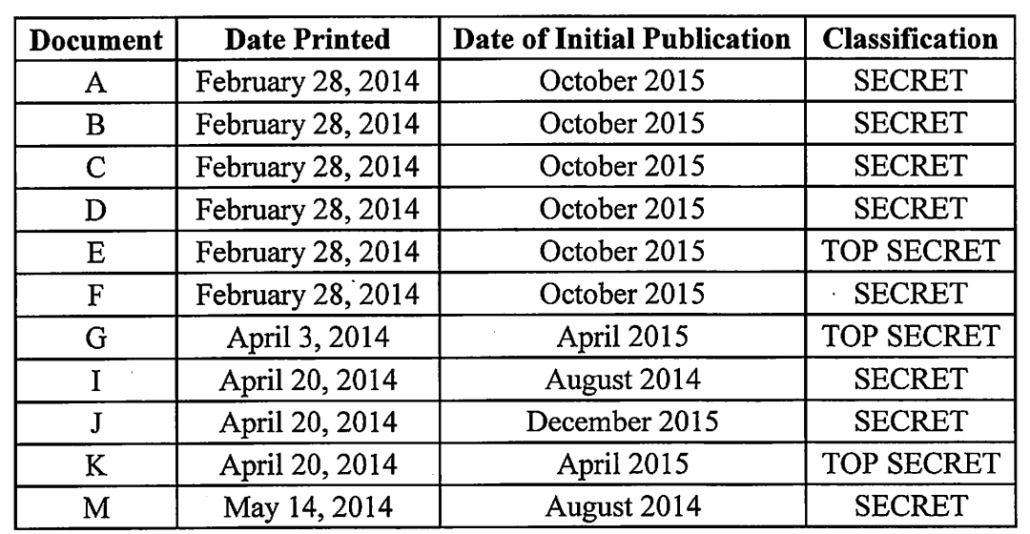
In his sentencing memorandum, Mike Flynn waved the following in front of Judge Emmet Sullivan, like a red cape before a bull.
There are, at the same time, some additional facts regarding the circumstances of the FBI interview of General Flynn on January 24, 2017, that are relevant to the Court’s consideration of a just punishment.
At 12:35 p.m. on January 24, 2017, the first Tuesday after the presidential inauguration, General Flynn received a phone call from then-Deputy Director of the FBI, Andrew McCabe, on a secure phone in his office in the West Wing.20 General Flynn had for many years been accustomed to working in cooperation with the FBI on matters of national security. He and Mr. McCabe briefly discussed a security training session the FBI had recently conducted at the White House before Mr. McCabe, by his own account, stated that he “felt that we needed to have two of our agents sit down” with General Flynn to talk about his communications with Russian representatives.21
Mr. McCabe’s account states: “I explained that I thought the quickest way to get this done was to have a conversation between [General Flynn] and the agents only. I further stated that if LTG Flynn wished to include anyone else in the meeting, like the White House Counsel for instance, that I would need to involve the Department of Justice. [General Flynn] stated that this would not be necessary and agreed to meet with the agents without any additional participants.”22
Less than two hours later, at 2:15 p.m., FBI Deputy Assistant Director Peter Strzok and a second FBI agent arrived at the White House to interview General Flynn.23 By the agents’ account, General Flynn was “relaxed and jocular” and offered to give the agents “a little tour” of the area around his West Wing office. 24 The agents did not provide General Flynn with a warning of the penalties for making a false statement under 18 U.S.C. § 1001 before, during, or after the interview. Prior to the FBI’s interview of General Flynn, Mr. McCabe and other FBI officials “decided the agents would not warn Flynn that it was a crime to lie during an FBI interview because they wanted Flynn to be relaxed, and they were concerned that giving the warnings might adversely affect the rapport,” one of the agents reported.25 Before the interview, FBI officials had also decided that, if “Flynn said he did not remember something they knew he said, they would use the exact words Flynn used, . . . to try to refresh his recollection. If Flynn still would not confirm what he said, . . . they would not confront him or talk him through it.”26 One of the agents reported that General Flynn was “unguarded” during the interview and “clearly saw the FBI agents as allies.”27
He cited a memo that fired FBI Deputy Director Andrew McCabe wrote the day of Flynn’s interview and the interview report (called a “302”) that fired FBI Special Agent Peter Strzok had a hand in writing up in August 2017, some seven months after the interview.
In response, the judge in his case, Emmet Sullivan, issued an order asking not just for those two documents, but any documents related to the matters Flynn writes up, to be filed by tomorrow, along with the government’s reply to his memorandum.

And so it is that on the one year anniversary of the order Sullivan issued to ensure that Flynn got any exculpatory information relating to his plea, that the hopes among the frothy right that Flynn’s prosecution (including for lying about his sleazy influence peddling with Turkey) will be delegitimized and with it everything that happened subsequent to Flynn’s plea might be answered.
Or maybe not.
For those unfamiliar with his background, back in the waning years of the Bush Administration, Sullivan presided over the Ted Stevens’ prosecution. After Stevens was convicted, DOJ started ‘fessing up to a bunch of improprieties, which led Sullivan (on newly confirmed Eric Holder’s recommendation) to throw out the conviction. Sullivan demanded a report on the improprieties, which ended up being a scathing indictment of DOJ’s actions (that nevertheless didn’t lead to real consequences for those involved). Since that time, Sullivan has been wary of DOJ’s claims, which has led him to do things like routinely issue the order he did with Flynn’s case, making sure that defendants get any exculpatory evidence they should get.
Regardless of how this request works out, you should applaud Sullivan’s diligence. He’s one of just a few judges who approaches the government with the skepticism they deserve. And to the extent that problems with our criminal justice system only get noticed when famous people go through it, it’s important that this one be treated with such diligence.
Still, those problems include both abuse, like we saw in the Stevens case, and special treatment, like David Petraeus got, and it’s actually unclear whether Sullivan’s request will uncover one or the other (or neither). I say that for several reasons.
First, because the public evidence suggests that — if anything — Obama’s appointees demanded FBI proceed cautiously in their investigation of Trump’s people, delaying what in any other case would have been routine early collection. When FBI discovered Flynn making suspicious comments to Sergei Kislyak, concerns about how to proceed went all the way up to Obama.
Moreover, contrary to most reporting on this interview, the FBI’s suspicions about Flynn did not arise exclusively from his calls to Kislyak. The interview happened after a counterintelligence investigation into Flynn had been open for months, as laid out by the House Intelligence Committee Russia report.
Director Comey testified that he authorized the closure of the CI investigation into general Flynn by late December 2016; however, the investigation was kept open due to the public discrepancy surrounding General Flynn’s communications with Ambassador Kislyak. [redacted] Deputy Director McCabe stated that, “we really had not substantiated anything particularly significant against General Flynn,” but did not recall that a closure of the CI investigation was imminent.
If McCabe believed the CI investigation into Flynn had produced mostly fluff, it might explain why he would approach setting up an interview with him with less than the rigor that he might have (as arguably happened with Hillary in the analogous situation). He didn’t expect there to be a there there, but then there was (remember, Jim Comey has repeatedly said that the one thing that might have led the Hillary investigation to continue past her interview as if they caught her lying; the difference is that Flynn told obvious lies whereas Hillary did not).
Finally, there’s one other, major reason to think this ploy may not work out the way Flynn might like. That’s because the frothy right, its enablers in Congress, and the White House itself has pursued this line for most of a year. Particularly in the wake of Flynn’s cooperation agreement, claiming that Flynn was just confused or forgetful when he spoke to the FBI has been central to Trump’s serial cover stories for why he fired Flynn.
So Republicans hoping to find the smoking gun have looked and looked and looked and looked and looked at the circumstances of Mike Flynn’s interview. Already by March of last year, they had resorted only to misstating Comey’s testimony about what happened in the HPSCI report.
Director Comey testified to the Committee that “the agents … discerned no physical indications of deception. They didn’t see any change in posture, in tone, in inflection, in eye contact. They saw nothing that indicated to them that he knew he was lying to them.”
Nothing in the report — which now includes a section substantially declassified to reveal more purportedly incriminating details about Flynn — suggests real impropriety with his interview.
Even in that very same paragraph, they quote McCabe (the guy who wrote up a memo that same day, which is probably what Sally Yates relied on when she suggested to the White House they needed to fire Flynn) stating very clearly that the FBI agents recognized that Flynn had lied.
McCabe confirmed the interviewing agent’s initial impression and stated that the “conundrum that we faced on their return from the interview is that although [the agents] didn’t detect deception in the statements that he made in the interview … the statements were inconsistent with our understanding of the conversation that he had actually had with the ambassador.”
The degree to which, after looking and looking and looking and looking for some smoking gun relating to the Flynn interview but finding very little is perhaps best indicated by where that search has gotten after looking and looking and looking and looking — as most recently exhibited in Jim Comey’s questioning from a week ago, by the Republicans’ best prosecutor, Trey Gowdy. After (apparently) hoping to catch Comey lying about what investigators thought when the lifetime intelligence officer managed to lie without any tells but instead leading him through a very cogent explanation of it, Gowdy then resorts to sophistry about what day of the week it is.
Mr. Gowdy. Who is Christopher Steele? Well, before I go to that, let me ask you this.
At any — who interviewed General Flynn, which FBI agents?
Mr. Comey. My recollection is two agents, one of whom was Pete Strzok and the other of whom is a career line agent, not a supervisor.
Mr. Gowdy. Did either of those agents, or both, ever tell you that they did not adduce an intent to deceive from their interview with General Flynn?
Mr. Comey. No.
Mr. Gowdy. Have you ever testified differently?
Mr. Comey. No.
Mr. Gowdy. Do you recall being asked that question in a HPSCI hearing?
Mr. Comey. No. I recall — I don’t remember what question I was asked. I recall saying the agents observed no indicia of deception, physical manifestations, shiftiness, that sort of thing.
Mr. Gowdy. Who would you have gotten that from if you were not present for the interview?
Mr. Comey. From someone at the FBI, who either spoke to — I don’t think I spoke to the interviewing agents but got the report from the interviewing agents.
Mr. Gowdy. All right. So you would have, what, read the 302 or had a conversation with someone who read the 302?
Mr. Comey. I don’t remember for sure. I think I may have done both, that is, read the 302 and then spoke to people who had spoken to the investigators themselves. It’s possible I spoke to the investigators directly. I just don’t remember that.
Mr. Gowdy. And, again, what was communicated on the issue of an intent to deceive? What’s your recollection on what those agents relayed back?
Mr. Comey. My recollection was he was — the conclusion of the investigators was he was obviously lying, but they saw none of the normal common indicia of deception: that is, hesitancy to answer, shifting in seat, sweating, all the things that you might associate with someone who is conscious and manifesting that they are being — they’re telling falsehoods. There’s no doubt he was lying, but that those indicators weren’t there.
Mr. Gowdy. When you say “lying,” I generally think of an intent to deceive as opposed to someone just uttering a false statement.
Mr. Comey. Sure.
Mr. Gowdy. Is it possible to utter a false statement without it being lying?
Mr. Comey. I can’t answer — that’s a philosophical question I can’t answer.
Mr. Gowdy. No, I mean, if I said, “Hey, look, I hope you had a great day yesterday on Tuesday,” that’s demonstrably false.
Mr. Comey. That’s an expression of opinion.
Mr. Gowdy. No, it’s a fact that yesterday was —
Mr. Comey. You hope I have a great day —
Mr. Gowdy. No, no, no, yesterday was not Tuesday.
Then Gowdy tries a new tack: suggesting that Flynn should have gotten the agents’ finding that he lied without any physical tells provided as some kind of Brady evidence.
Mr. Gowdy. And, again — because I’m afraid I may have interrupted you, which I didn’t mean to do — your agents, it was relayed to you that your agents’ perspective on that interview with General Flynn was what? Because where I stopped you was, you said: He was lying. They knew he was lying, but he didn’t have the indicia of lying.
Mr. Comey. Correct. All I was doing was answering your question, which I understood to be your question, about whether I had previously testified that he — the agents did not believe he was lying. I was trying to clarify. I think that reporting that you’ve seen is the product of a garble. What I recall telling the House Intelligence Committee is that the agents observed none of the common indicia of lying — physical manifestations, changes in tone, changes in pace — that would indicate the person I’m interviewing knows they’re telling me stuff that ain’t true. They didn’t see that here. It was a natural conversation, answered fully their questions, didn’t avoid. That notwithstanding, they concluded he was lying.
Mr. Gowdy. Would that be considered Brady material and hypothetically a subsequent prosecution for false statement?
Mr. Comey. That’s too hypothetical for me. I mean, interesting law school question: Is the absence of incriminating evidence exculpatory evidence? But I can’t answer that question.
I mean, maybe there are some irregularities explaining why it took seven months to write up Flynn’s 302 and how information about the interview was shared within DOJ in the interim; if there is I’d like to know what those are. But what everyone seems to agree is that there was no dispute, from the very beginning, that Flynn lied.
And Flynn’s statement actually makes things worse for himself (and, importantly, for one of the White House cover stories that his firing was immediately precipitated by Don McGahn confronting him with the transcript of his conversation with Kislyak). Flynn’s own sentencing memo makes it clear the FBI Agents were quoting directly from the transcript about what he said.
FBI officials had also decided that, if “Flynn said he did not remember something they knew he said, they would use the exact words Flynn used, . . . to try to refresh his recollection. If Flynn still would not confirm what he said, . . . they would not confront him or talk him through it.”
So Flynn would have known, way back when the White House was trying to find excuses to keep him on, precisely what he had been caught saying.
Finally, remember two more details. While we can’t read it, Sullivan (and Flynn’s team) know what’s behind this redaction:

That means Sullivan knows, even if we don’t, why Mueller thinks it so important that Flynn lied, and so may have a very different understanding about the import of those lies.
Finally, note that along with requiring the government to turn over all the filings relating to his interview (not just the two Flynn selectively quoted from), Sullivan also instructed the government to file their reply to Flynn’s sentencing memo by the same time.
DOJ has never had the opportunity to write its own explanation for what happened with Flynn’s interview. By inviting a reply specifically in the context of this Flynn claim, Sullivan has given DOJ the opportunity to do just that, finally.
DOJ may have a very interesting explanation for why they approached a counterintelligence interview with a guy they might have considered one of them with jocularity.
Sure, there may yet be damning details. As I’ve said, I really look forward to learning why it took seven months to formally memorialize this interview.
But the GOP has been looking for a smoking gun for a year and have not apparently found one. It’s quite possible we’ll learn something else tomorrow, that Mike Flynn actually got special treatment that none of us would get if we were suspected of being recruited by Russian intelligence.
At the very least, Sullivan’s order may result in documentation that reveals just how shoddy all the claims irregularity surrounding Flynn’s interview have been all this time.
Update: Elevating this from pinc’s comment. If DOJ chooses to tell a story that at all resembles Greg Miller’s account of the meeting (including that Flynn specifically said he didn’t want to have a lawyer of any type present), then this could spectacularly backfire.
As I disclosed in July, I provided information to the FBI on issues related to the Mueller investigation, so I’m going to include disclosure statements on Mueller investigation posts from here on out. I will include the disclosure whether or not the stuff I shared with the FBI pertains to the subject of the post.


![[Photo: National Security Agency, Ft. Meade, MD via Wikimedia]](https://www.emptywheel.net/wp-content/uploads/2017/08/NationalSecurityAgency_HQ-FortMeadeMD_Wikimedia.jpg)