I put together a very rough list of the interviews that John Durham included in his Report and a table showing the organization of his report.
I’d like to describe what appears to have happened with the investigation. Remember a few things about this list: It won’t include everything. Even just among witnesses who testified at trial, Durham was known to have done initial interviews, then threatened them with prosecution, in an often successful attempt to shade their testimony (see this post for an example). With others, Durham is being affirmatively misleading by stating that people who did appear before the grand jury were unwilling to be interviewed.
This list is just a list of interviews that actually support his narrative.
2019: Manufacturing a new origin story
As noted, most of the junkets that Durham and Barr did in the first year of the investigation don’t appear. The only overseas investigative steps noted in 2019 include the Legal Attaché personnel in London and the two Australian sources, Alexander Downer and Erika Thompson (described as Australian Diplomat-1), behind the original tip on George Papadopoulos. Durham did two separate interviews with the Australians, done on the same day, months before the DOJ IG Report determined the investigation was properly predicated.
Durham relies heavily on Downer, instead of Thompson, and claims to have discovered a conflict in their two accounts.
The Australian account reflects that two meetings of a casual nature took place with Papadopoulos. 215 These meetings were documented by Downer on May 11, 2016 and by Australian Diplomat-I later in the month. 216 Both diplomats advised that prior to the Spring of 2016, Papadopoulos was unknown to them. 217 Notably, the information in Paragraph Five does not include any mention of the hacking ofthe DNC, the Russians being in possession of emails, or the public release of any emails. In addition, when interviewed by the Office, Downer stated that he would have characterized the statements made by Papadopoulos differently than Australian Diplomat-1 did in Paragraph 5. According to Downer, Papadopoulos made no mention of Clinton emails, dirt or any specific approach by the Russian government to the Trump campaign team with an offer or suggestion of providing assistance. Rather, Downer’s recollection was that Papadopoulos simply stated “the Russians have information” and that was all. 218
As recounted to the FBI on August 2, 2016, by Australian Diplomat-1, the substance of Paragraph Five was written in a “purposely vague” way. 219 This was done because Papadopoulos left a number of things unexplained and “did not say he had direct contact with the Russians.” 220 The impression Papadopoulos made on the Australian diplomats was wide ranging. On the one hand, he “had an inflated sense of self,” was “insecure,” and was “trying to impress.” 221 On the other hand, he was “a nice guy,” was “not negative,” and “did not name drop.” 222
Downer noted that he
was impressed Papadopoulos acknowledged his lack of expertise and felt the response was uncommon for someone of Papadopoulos’ age, political experience and for someone thrust into the spotlight overnight. Many people in a similar position would represent themselves differently and [Downer] would have sniffed them out. If [Downer] believed Papadopoulos was a fraud [he] would not have recorded and reported on the meeting [he] had with Papadopoulos. 223
Downer also said that he “did not get the sense Papadopoulos was the middle-man to coordinate with the Russians.” 224 The Australian diplomats would later inform the FBI, and subsequently the Office, that the impetus for passing the Paragraph Five information in late-July was the public release by WikiLeaks ( on July 22, 2016) of email communications that had been hacked from the DNC servers. 225
215 We note there is an inconsistency in the statements given by Australian Diplomat-1 and former-High Commissioner Downer to the Crossfire Hurricane interviewers in August 2016 and what they told the Office when interviewed in October 2019. Australian Diplomat-1 and Downer were interviewed together in August 2016, and, according to the FD-302 prepared afterward by Supervisory Special Agent- 1, Papadopoulos made the statements about the Russians during the May 6, 2016 introductory meeting when he met only with Australian Diplomat-1. When the two diplomats were interviewed separately by the Office in October 2019, investigators were advised that Papadopoulos made the statements in front of both Australian Diplomat-1 and Downer during the second meeting on May 10, 2016.
216 The meetings with Papadopoulos took place on May 6 and 10, 2016. Australia 302 at 1- 2. The Australian diplomats documented the meetings in two cables dated May 11 and May 16, 2016; OSC Report of Interview ofAlexander Downer on Oct. 9, 2019 at 2; OSC Report of Interview ofAustralian Diplomat-1 on Oct. 9, 2019 at 3.
217 OSC Report of Interview of Alexander Downer on Oct. 09, 2019 at 1; OSC Report of Interview of Australian Diplomat-I on Oct. 09, 2019 at 1-2.
218 OSC Report of Interview of Alexander Downer on Oct. 09, 2019 at 2 (and related field notes); Downer also is reported to have stated in an interview that in talking with Papadopoulos there was “no suggestion that there was collusion between Donald Trump or Donald Trump’s campaign and the Russians.” Brooke Singman, Diplomat Who Helped Launch Russia Probe Speaks Out, Defends Role, Fox News (May 10, 2019), https://www.foxnews.com/politics/forrner-ausralian-diplomat-alexander-downer-defendswork-pushes-back-on-claim-he-tried-to-trap-papadopoulos. 219 Australia 302 at 2.
There’s no conflict.
Papadopoulos appears to have told the story about advance notice of Russia’s help to Thompson twice, once on May 6 and again, with Downer present, on May 10. She explains that not everything Papadopoulos said made it into her report. It’s likely Papadopoulos said more at the first meeting (I believe the record reflects that he drank more at the first meeting).
But by relying on Downer instead of Thompson, Durham claims that there was less to the tip than Thompson appears to have taken from it.
Having manufactured an alternate story about the initial predication, it’s no wonder Durham pushed Michael Horowitz not to say the investigation was fully predicated.
Durham also appears to have investigated why it took so long for the Steele reports to make their way from New York to DC. This is a fairly remarkable and sustained part of his report, because Durham is basically complaining that the pee tape report wasn’t immediately taken seriously.
Finally, from the very first year, Durham started doing investigations into the treatment of the Clinton Foundation investigation. As I have noted, his report leaves out really important details of that investigation: that agents who exhibited every bit as much bias as Durham finds in Peter Strzok, Lisa Page, or Kevin Clinesmith were running a key informant on the investigation, something no one has alleged happened with investigations into Trump’s associates.
That silence is all the more important given how Durham compares the predication of the Crossfire Hurricane investigation with that of Clinton Foundation, which relied in significant part on the Steve Bannon-linked Clinton Cash book which was every bit as shoddy as the Christopher Steele dossier, with a much more aggressive bias.
Once again, the investigative actions taken by FBI Headquarters in the Foundation matters contrast with those taken in Crossfire Hurricane. As an initial matter, the NYFO and WFO investigations appear to have been opened as preliminary investigations due to the political sensitivity and their reliance on unvetted hearsay information (the Clinton Cash book) and CHS reporting. 388 By contrast, the Crossfire Hurricane investigation was immediately opened as a full investigation despite the fact that it was similarly predicated on unvetted hearsay information. Furthermore, while the Department appears to have had legitimate concerns about the Foundation investigation occurring so close to a presidential election, it does not appear that similar concerns were expressed by the Department or FBI regarding the Crossfire Hurricane investigation. Indeed, in short order after opening the Crossfire Hurricane file and its four subfiles, the FBI was having one of its long-time CHSs meet not with just one Trump campaign associate, but meet and record conversations with three such insiders. And a little more than a month after opening the Crossfire Hurricane file on Page, a “senior U.S. law enforcement official” was publicly reported as confirming for Michael Isikoff and Yahoo! News that the FBI had Page on its radar screen. 389
Durham says two Australians who had no stake in the election (and who likely didn’t want to create a row with a major political candidate) have the same credibility as a long term political hoaxster paid by Trump’s ultimate campaign manager.
And in making this comparison, Durham doesn’t consider the urgency of the ongoing Russian attack on democracy (something that he generally ignores throughout the report). The underlying crime behind the Papadopoulos tip was potential (and real, in the case of both Paul Manafort and Roger Stone) ongoing involvement in Russia’s efforts to interfere in the election.
2020: Laying the ground work for the Clinton conspiracy
Early in 2020, Barr made Durham a Special Counsel, giving him authority to use a grand jury.
The very next day, he met with Jim Baker.
In cross-examination at the Sussmann trial, Baker lawyer Sean Berkowitz situated this meeting and another, in June 2020, when Baker’s story about the Sussmann meeting was still radically different than the one he told at trial, in terms of a leak investigation into Baker that had just closed. Baker had recently been criminally investigated by Durham, he knew that Durham would come after him again on the Russian investigation, and that February 2020 meeting was the first after the close of the leak investigation.
Q. So you know what it’s like to be under criminal investigation. Right?
A. Yes.
Q. You know what it’s like to be under criminal investigation by this man?
A. Yes.
Q. That’s Mr. Durham?
A. Yes.
Q. In fact, sir, in March of 2017 Mr. Durham was appointed by the Department of Justice to conduct a criminal investigation of the unauthorized disclosure of classified information to a reporter. Correct?
A. I don’t remember exactly when he was appointed, but that’s roughly correct based on my recollection of the timeframe.
Q. And you were a subject of that investigation?
A. I was never told that I was a subject.
Q. Is it fair to say that your lawyer refused to let you answer questions before Congress because you were under investigation?
A. He did object to certain questions — certain questions — because I was under investigation. That’s correct.
Q. Under criminal investigation. Right?
A. It was a criminal investigation was my understanding, yes.
Q. And you refused to answer those questions on the gounds that it might incriminate you?
A. I refused to answer those questions on advice of counsel, and it was a voluntary interview so I could refuse to answer any questions that I didn’t want to answer.
Q. And the investigation took place between 2017 and 2018. correct:
A. Say that again.
Q. The investigation took place between 2017 and 2019. correct?
A. I think it was not closed until 2020 by the Department.
[snip]
Q. And you, sir, were aware that Mr. Baker was — I mean, Mr. Durham was reappointed as special counsel, correct, in or around 2019?
A. For this matter?
Q. Yes.
A. Yes.
Q. And when that happened, you were concerned, were you not?
A. Concerned about what?
Q. That Mr. Durham might come and investigate you more?
A. I wasn’t concerned about it. I expected it.
[snip]
Q. It’s the first time you saw him after you were the subject of the criminal investigation by him?
A. Again, I was never told that I was a subject.
Q. Was that the first time?
A. Yeah, I think that was the first time.
In June 2020, Baker’s story started to evolve until ultimately, he testified, claiming 100% certainty about a story that had changed at least four times, to precisely the story Durham would want him to.
Most of the early 2020 interviews relied on by Durham in his report pertain to two topics: His reinvestigation of how the Clinton Foundation investigation proceeded, and his pursuit of a claim that Hillary framed Donald Trump (marked as “Russian intelligence” in the timeline).
Starting in June 2020, Durham appears to have started focusing on Igor Danchenko, burning him as a source, reviewing the long-dormant counterintelligence investigation into him, and focusing the same kind of pressure on Danchenko handler Kevin Helson (whom Durham seems to have referred for further investigation, on a date he doesn’t provide, for his handling of Danchenko). In July 2020, Barr provided Lindsey Graham the interview transcripts for Danchenko, which would lead to (or provide the excuse for) Danchenko’s exposure. In September 2020, the Senate Judiciary Committee would stage a FISA hearing to expose Danchenko’s past counterintelligence investigation.
None of these were effective investigative steps. Most witnesses didn’t testify at trial, and the one who did — Helson — was a devastating witness against Durham’s case (which may be why he was referred for further investigation). Those investigative steps did make Danchenko far more insecure, both legally and financially.
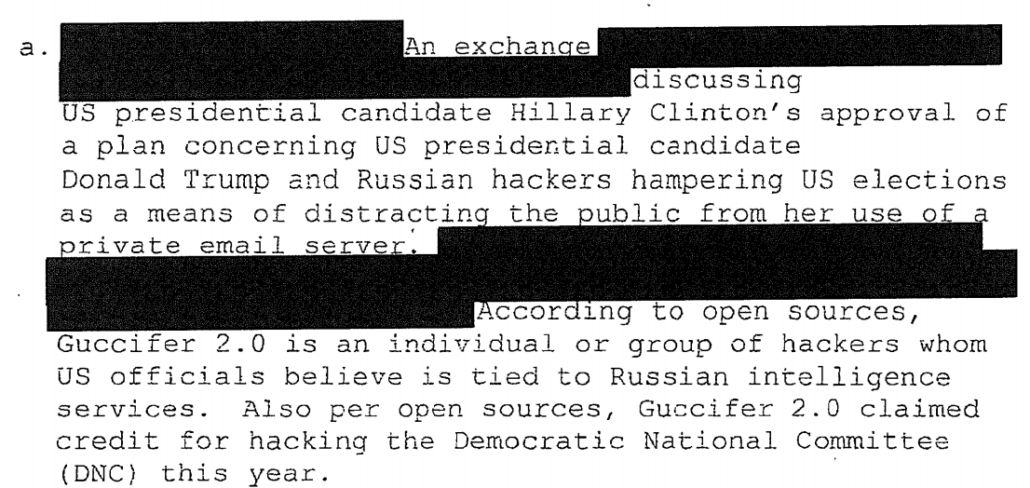
On September 29, John Ratcliffe would also share the report and, a week later, the underlying intelligence, around which Durham would build his Clinton conspiracy theory: A Russian intelligence Report that Hillary’s complaints about Trump’s pro-Russian bias stemmed from an attempt to cover up her email scandal and not from real concern about Russia or frustration with being victimized by a nation-state hack during an election.
On October 19, after Nora Dannehy disrupted Durham’s plan to release an initial report before the election, Barr made him Special Counsel so he could stick around for two more years to try to build the case he hadn’t done by 2020.
One of the most telling things about Durham’s actions in 2020 is that he didn’t do any of the ground work he needed to do to investigate the accusations he would make in late 2021. His primary work on the Alfa Bank case was making Danchenko far, far more vulnerable. He records virtually no obvious investigative work on the Alfa Bank allegations in 2020. He did little work on the dossier allegations. Some key investigative steps — getting a technical review of the Alfa Bank allegation and trying to secure Sergei Millian’s make-or-break testimony — waited until 2022, well after he had actually indicted these cases.
2021: Preparing actual indictments to hang failed conspiracy theories on
And it’s not just those two indictments Durham neglected in 2020. Here’s something Carter Page should think seriously about: John Durham did not do the investigation into the problems with his FISA application until the statutes of limitation started to expire in 2021. Given that investigative history, it’s fairly clear that Durham was never going to charge FBI agents in conjunction with those applications. Never. He had other priorities.
Instead, in 2021, he started making belated attempts to substantiate his Clinton conspiracy, with interviews to set up Charles Dolan as a witness.
Durham did no apparent interviews into Sergei Millian in 2021.
He did begin the effort — one paralleled and assisted by Alfa Bank lawsuit against the researchers in question, which to a DC judge seemed,”almost like they were written by the same people in some way,” — to spin the research into DNS anomalies into a deliberate plan by Hillary’s team.
In Durham’s investigations, however, there were obvious basic investigative failures. Durham didn’t interview people from Cendyn and Listrak until after the Sussmann indictment (and in the latter case, it’s not clear whether Durham spoke to anyone authoritative or even got the name of all the people interviewed).
I’ve already laid out how Durham didn’t even ask Michael Horowitz for relevant evidence until after the indictment. It was several months later before he asked Jim Baker to check his iCloud for the exculpatory communications that Sussmann correctly predicted would be there.
Durham didn’t interview Sergei Millian — and even then, he only did so remotely, with no agreement he would testify at trial — until February 2022, three months after indicting Danchenko.
These indictments — both of which could only have worked if charged as conspiracy indictments for which Durham had no evidence — were always bound to fail. They were bound to fail because they weren’t the result of an investigation, the logical progression from a clear crime committed. They were instead legal clothes hangers on which he could try to hang a conspiracy theory. They might have worked if Sussmann or Rodney Joffe or Danchenko had caved to the economic and legal pressure Durham was applying (as he did with Danchenko, Durham also got Joffe discontinued as an FBI source, but that had no financial repercussions for Joffe). But the charges were so flimsy Sussmann and Danchenko mounted a fairly clearcut defense.
Late 2021 to 2022: Chasing Clinton conspiracies
There’s a detail, though, that is all the more revealing given Durham’s failure to conduct an adequate investigation into these charges before indicting. As I noted last year, even after Sussmann was indicted, Durham refused the former Clinton lawyer’s demand for a list of the people on the Clinton campaign with whom he had coordinated his Alfa Bank efforts. It wasn’t until months later that it became clear — as Sussmann laid out in a filing — that Durham hadn’t even interviewed any of the people Sussmann purportedly coordinated with until after the indictment.
[T]he Special Counsel has alleged that Mr. Sussmann met with the FBI on behalf of the Clinton Campaign, but it was not until November 2021—two months after Mr. Sussmann was indicted—that the Special Counsel bothered to interview any individual who worked full-time for that Campaign to determine if that allegation was true.
Here’s what those interviews look like, as laid out in the Durham Report:
11/10/21: Jennifer Palmieri
11/12/21: Jake Sullivan
1/19/22: John Podesta (Russian Intelligence)
5/11/22: Hillary Clinton (Russian Intelligence)
Those questions weren’t focused on Sussmann, though. They were focused on Durham’s Clinton conspiracy, the claim that she had made a plan to frame Donald Trump.
During an interview of former Secretary Clinton, the Office asked if she had reviewed the information declassified by DNI Ratcliffe regarding her alleged plan to stir up a scandal between Trump and the Russians. 44 ° Clinton stated it was “really sad,” but “I get it, you have to go down every rabbit hole.” She said that it “looked like Russian disinformation to me; they’re very good at it, you know.” Clinton advised that she had a lot of plans to win the campaign, and anything that came into the public domain was available to her.
In addition, the Office interviewed several other former members of the Clinton campaign using declassified materials441 regarding the purported “plan” approved by Clinton.
The campaign Chairperson, John Podesta, stated that he had not seen the declassified material before, characterized the information as “ridiculous,” and denied that the campaign was involved in any such “plan.”442 Jake Sullivan, the campaign Senior Policy Advisor, stated that he had not seen the intelligence reporting before and had no reaction to it other than to say, “that’s ridiculous.”443 Although the campaign was broadly focused on Trump and Russia, Sullivan could not recall anyone articulating a strategy or “plan” to distract negative attention away from Clinton by tying Trump to Russia, but could not conclusively rule out the possibility. 444 The campaign Communications Director, Jennifer Palmieri, who was shown the Referral Memo, 445 stated that she had never seen the memorandum before, found its contents to be “ridiculous,” and could not recall anything “like this” related to the campaign. 446 She stated that Podesta, Mook, Sullivan and herself were aware of a project involving ties between Trump and Russia being conducted by Perkins Coie, the campaign law firm, but she did not think Clinton was aware of it, nor did she receive any direction or instruction from Clinton about the project.447
Another foreign policy advisor (“Foreign Policy Advisor-2”) confirmed that the campaign was focused on Trump and Russia, but that focus was due to national security concerns and not designed to distract the public from Clinton’s server issue. 448
Every single one of them called Durham’s conspiracy theories “ridiculous.”
For good reason. As I’ve laid out, the timeline Durham obscures, in which Trump’s rat-fucker had contact with Russia weeks before Hillary purportedly ginned up this plan, disproves the conspiracy theory.
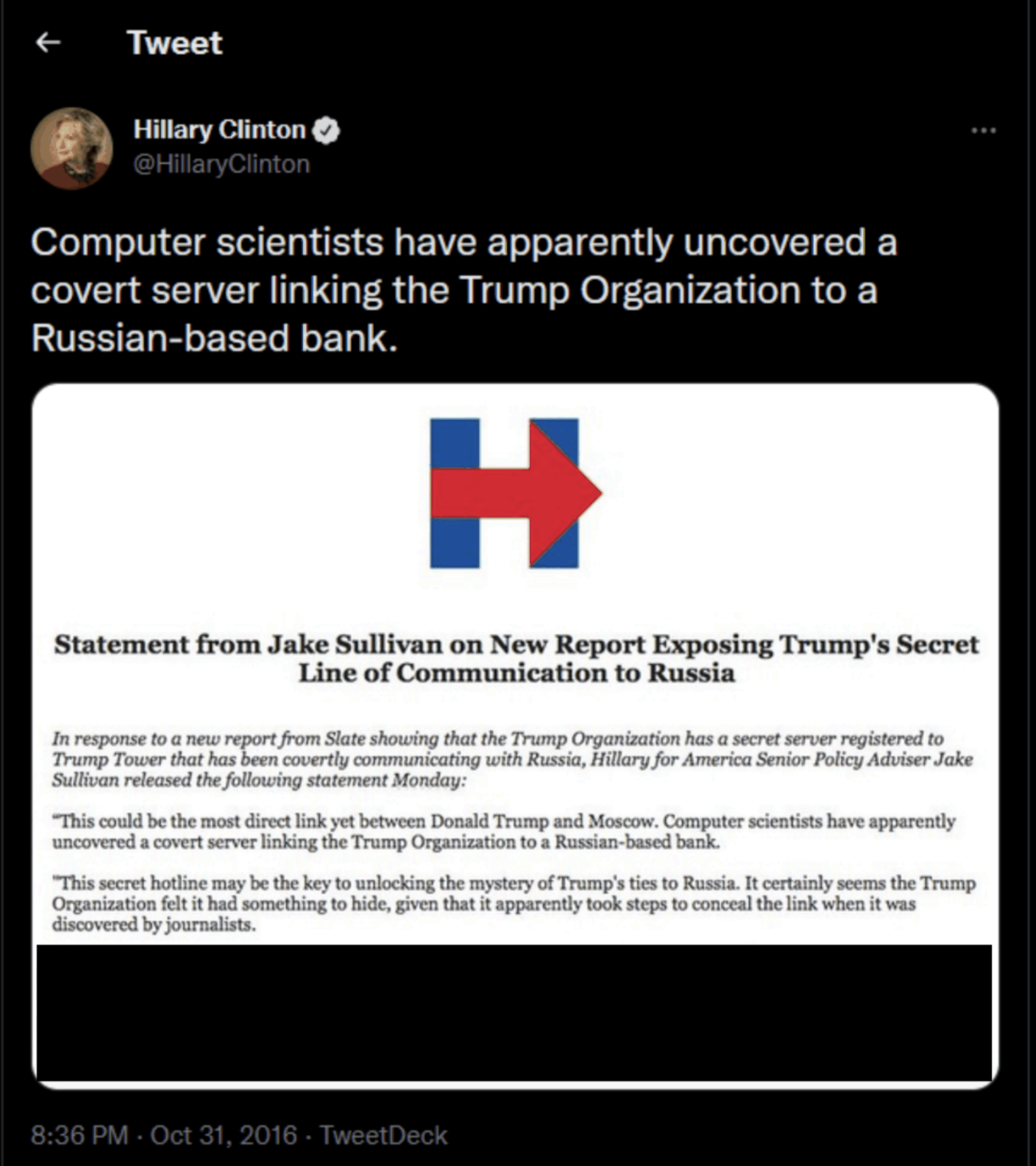
Which explains something about the Sussmann trial — led by Andrew DeFilippis, the same AUSA who had willingly attempted to trump up a crime against John Kerry. Over and over, Durham’s prosecutors willfully ignored Judge Christopher Cooper’s orders, thereby introducing evidence with no evidentiary basis. They did so most blatantly when, minutes after Cooper ordered DeFilippis not to read from a paragraph of a Hillary Tweet calling on FBI to investigate the Alfa Bank allegations, he did so anyway, predictably leading the same outlets that wrote supine reviews of the Durham report to focus exclusively on something not before the jury.
After Judge Cooper said he would reserve his decision, Berkowitz noted that in fact, DeFilippis planned to use the tweet to claim the campaign wanted to go to the FBI when the testimony at trial (from both Elias and Mook) would establish that going to the FBI conflicted with the campaign’s goals.
[T]hey are offering the tweet for the truth of the matter, that that’s what the campaign desired and wanted and that it was a accumulation of the efforts.
Number one, it’s not the truth; and in fact, it’s the opposite of the truth. We expect there to be testimony from the campaign that, while they were interested in an article on this coming out, going to the FBI is something that was inconsistent with what they would have wanted before there was any press. And in fact, going to the FBI killed the press story, which was inconsistent with what the campaign would have wanted.
And so we think that a tweet in October after there’s an article about it is being offered to prove something inconsistent with what actually happened.
Then, after both Elias and Mook had testified that they had not sanctioned Sussmann going to the FBI, DeFilippis renewed his assault on Cooper’s initial exclusion, asking to introduce it through Mook’s knowledge that the campaign had tried to capitalize on the Foer story.
Having ruled in the past that the tweet was cumulative and highly prejudicial, Cooper nevertheless permitted DeFilippis to introduce the tweet if he could establish that Mook knew that the campaign tried to capitalize on the Foer story.
But Cooper set two rules: The government could not read from the tweet and could not introduce the part of the tweet that referenced the FBI investigation. (I explained what DeFilippis did at more length in this post.)
THE COURT: All right. Mr. DeFilippis, if you can lay a foundation that he had knowledge that a story had come out and that the campaign decided to issue the release in response to the story, I’ll let you admit the Tweet. However, the last paragraph, I agree with the defense, is substantially more prejudicial than it is probative because he has testified that had neither — he nor anyone at the campaign knew that Mr. Sussmann went to the FBI, no one authorized him to go to the FBI, and there’s been no other evidence admitted in the case that would suggest that that took place. And so this last paragraph, I think, would unfairly suggest to the jury, without any evidentiary foundation, that that was the case. All right?
MR. DeFILIPPIS: Your Honor, just two brief questions on that.
THE COURT: Okay.
MR. DeFILIPPIS: Can we — so can we use — depending on what he says about whether he was aware of the Tweet or the public statement, may we use it to refresh him?
THE COURT: Sure. Sure.
MR. DeFILIPPIS: Okay. And then, as to the last paragraph, could it be used for impeachment or refreshing purposes as well in terms of any dealings with the FBI?
THE COURT: You can use anything to refresh.
MR. DeFILIPPIS: Okay.
THE COURT: But we’re not going to publish it to the jury. We’re not going to read from it. And let’s see what he says. [my emphasis]
Having just been told not to read the tweet, especially not the part about the FBI investigation, DeFilippis proceeded to have Mook do just that.
The exhibit of the tweet that got to the jury had that paragraph redacted and that part of the transcript was also redacted. But, predictably, the press focused on little but the tweet, including the part that Cooper had explicitly forbidden from coming into evidence.
In his report, Durham obscures the timeline of all this to falsely suggest that Hillary endorsed going to the FBI in September, before Sussmann met with the FBI, and not days before the election, when Franklin Foer reported the story.
On October 31, 2016 – about one week before the election – multiple media outlets reported that the FBI had received and was investigating the allegations concerning a purported secret channel between the Trump Organization and Alfa Bank. For example, Slate published an article that discussed at length the allegations that Sussmann provided to the FBI. 1530
Also on that day, the New York Times published an article titled Investigating Donald Trump, F.B.f Sees No Clear Link to Russia. 1531 The article discussed information in the possession of the FBI about ··what cyber experts said appeared to be a mysterious computer back channel between the Trump Organization and the Alfa Bank.” 1532 The article further reported that the FBI had “spent weeks examining computer data showing an odd stream of activity to a Trump Organization server,” and that the newspaper had been provided computer logs that evidenced this activity. The article also noted that at the time of the article, the FBI had not found “any conclusive or direct link” between Trump and the Russian government and that “Hillary Clinton’s supporters … pushed for these investigations.” 1533
As noted above, in the months prior to the publication of these articles, Sussmann had communicated with the media and provided them with the Alfa Bank data and allegations. 1534 Sussmann also kept Elias apprised of his efforts. 1535 Elias, in tum, communicated with the Clinton campaign’s leadership about potential media coverage of these issues. 1536
In addition, on September 15, 2016, Elias provided an update to the Clinton campaign regarding the Alfa Bank allegations and the not-yet-published New York Times article, sending an email to Jake Sullivan (HFA 154 ° Chief Policy Advisor), Robby Mook (HF A Campaign Manager), John Podesta (HF A Campaign Chairman), and Jennifer Palmieri (HFA Head of Communications), which he billed to the Clinton campaign as “email correspondence with J. Sullivan, R. Mook, J. Podesta, J. Palmieri re: Alfa Bank Article.” 1541
On the same day that these articles were published, the Clinton campaign posted a tweet through Hillary Clinton’s Twitter account which stated: “Computer scientists have apparently uncovered a covert server linking the Trump Organization to a Russian-based bank.” 1542 The tweet included a statement from Clinton campaign advisor Jake Sullivan which made reference to the media coverage article and stated, in relevant part, that the allegations in the article “could be the most direct link yet between Donald Trump and Moscow[,] that “[t]his secret hotline may be the key to unlocking the mystery ofTrump’s ties to Russia[,]” and that”[w ]e can only assume that federal authorities will now explore this direct connection between Trump and Russia as part oftheir existing probe into Russia’s meddling in our elections.”
In context, Durham falsely leaves the impression that Hillary supported going to the FBI in advance, even though both Robby Mook and Marc Elias testified that the last thing Hillary wanted to do was let the FBI get more involved in her campaign. In context, Durham falsely leaves the impression that Sussmann had sustained contacts with the NYT starting in September and never stopping, when the evidence he cites pertains exclusively to early September communications, after which Sussmann worked with the FBI to kill the story.
In a follow-up post, I will lay out just how grotesque Durham’s conspiracy theory is — the digital equivalent of slut-shaming a rape victim.
But for now, consider the abundant evidence that Durham didn’t investigate the charges he ultimately charged. He was far too busy, instead, pursuing this Clinton conspiracy theory he started chasing at least as early as February 2020.
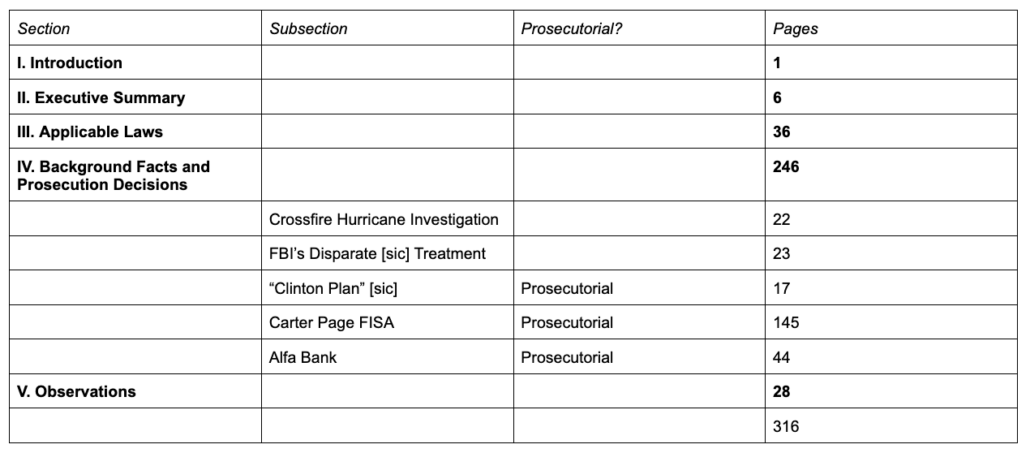
Update: Added table showing the organization of Durham’s Report.
Dates
5/13/19: Preliminary review
5/28/19: UK Legat-1
6/4/19: UK ALAT-1
6/17/19: SSA-1 (Steele Reports, Papadopoulos)
6/17/19: CIA Employee-1 (Page FISA)
6/18/19: SSA-1 (bias)
6/19/19: Case Agent-1 (defensive briefing, Steele Reports, Papadopoulos)
7/2/19: Handling Agent-1 (Page FISA)
7/2/19: NYFO ASAC-1 (Page FISA)
7/3/19: Michael Harpster (Steele Reports)
8/1/19: Mike Rogers
8/6/19: NYFO ADC-1
8/12/19: Randall Coleman (Clinton Foundation, Steele Reports)
8/12/19: Diego Rodriquez (Clinton Foundation)
8/14/19: HQ Analyst-3
9/16/19: Cyber Agent-2 (Alfa)
10/17/19: SSA-2 (Clinesmith, Papadopoulos)
8/21/19: Case Agent-1
8/29/19: OGC Unit Chief-1 (bias, Australia referral, Page FISA)
9/5/19: NYFO Case Agent-1 (Page FISA)
10/9/19: Erika Thompson; Alexander Downer
12/9/19: DOJ IG Report
12/10/19: HQ Analyst-3
1/6/20: David Johnson (Steele Reports)
1/15/20: NYFO Case Agent-1 (Clinton Foundation)
1/16/20: Diego Rodriquez (Clinton Foundation)
1/28/20: HQ Unit Chief-3 (Clinton Foundation)
2/6/20: Special Attorney to Attorney General (may reflect grand jury)
2/7/20: Jim Baker (defensive briefing)
2/13/20: Cyber Agent-3 (Alfa)
2/19/20: HQ Analyst-3 (Page FISA)
2/25/20: HQ Analyst-2 (Russian Intelligence, Clinesmith)
2/28/20: Jonathan Moffa (Russian Intelligence)
3/18/20: Paul Abbate (Clinton Foundation)
4/14/20: Field Office-1 Handling Agent-3
4/23/20 Field Office-1 Handling Agent (Clinton Foundation)
4/23/20: Michael Harpster (Steele Reports)
5/1/20: Mueller SSA-1
5/5/20 Field Office-1 Handling Agent (Clinton Foundation)
5/6/20: Steele Reports
5/28/20: HQ SSA-4 (Clinton Foundation)
6/11/20: Jim Baker (Russian Intelligence)
6/18/20: Jim Baker (Russian Intelligence)
6/25/20: SA-2 (Steele Reports)
6/29/20: Michael Steinbach (initial EC)
6/30/20: Referral regarding existing counterintelligence investigation
7/1/20: OI Attorney (Page FISA)
7/8/20: Ray Hülser (Clinton Foundation)
7/14/20: Kevin Helson (Page FISA)
7/22/20: SSA-1 (Russian intelligence, Steele Report)
7/23/20: OGC Unit Chief-1 (Page FISA)
7/28/20: Baltimore Special Agent-2 (Danchenko)
8/13/20: Baltimore Case Agent-1 (Danchenko)
8/13/20: CIA Employee-2 (Alfa)
8/19/20: IC Officer #6 (Russian Intelligence)
8/20/20: WFO Clinton Foundation Case Agent-1
8/21/20: John Brennan (Russian Intelligence)
9/9/20: Acting OGC Section Chief-1 (Clinton Foundation)
9/10/20: Field Office-1 SAC
9/22/20: Field Office-1 Handling Agent-3
9/29/20: Patrick Fallon (Clinton Foundation)
9/29/20: John Ratcliffe shares Russian Intelligence with Lindsey Graham
10/19/20: Special Counsel appointment
10/27/20: OI Unit Chief-1 (Page FISA)
11/24/20: Kevin Helson (Danchenko)
12/8/20: HQ Supervisory Analyst-1 (Danchenko)
12/15/20: HQ SSA-3 (Alfa)
12/18/20: Baltimore Special Agent-1 (Danchenko)
12/21/20: Designation to use classified information
12/23/20: IC Officer#12 (Russian Intelligence)
12/20: Referral regarding accuracy of info in non-Page FISA (possibly Millian?)
2/2/21: Tech Company-1 Employee 1 (Alfa)
2/11/21: DARPA Program Manager-1 (Alfa)
2/25/21: Tech Company-1 Employee 1 (Alfa)
3/3/21: SSA-1 signed statement on Steele Reports
3/18/21: SSA-3 (Page FISA)
3/21/21: SA-1 (Page FISA)
4/8/21: Field Office-1 SSA-1
4/13/21: US Person-1 (Dolan Associate) (Danchenko)
4/14/21: Research Exec-1 (Alfa)
4/22/21: HQ Unit Chief-2
5/5/21: SSA-2 (bias, Page FISA, Danchenko, Clinesmith, Papadopoulos)
5/5/21: Field Office-1 Handling Agent-2 (second CI investigation)
6/21/21: David Archey (Defensive briefings)
6/29/21: CIA Employee-3 (Alfa)
6/30/21: OGC Attorney-1 (Page FISA)
6/30/21: Danchenko Employer-1 Exec-1
7/7/21: Field Office-1 ASAC-1
7/9/21: Jennifer Boone
7/9/21: Tech Company-1 Employee 1 (Alfa)
7/21/21: Foreign Policy Advisor-1 (Russian Intelligence)
7/21/21: SSA-1 (Page FISA)
7/22/21: University-1 Researcher-1 (Alfa)
7/26/21: Brian Auten (bias, Russian Intelligence, Steele Reports)
7/27/21: Kevin Helson (Danchenko)
8/21: University-1 Researcher-2 (Alfa) [appears to be one 302 on more than one conversation]
8/9/21: NJ-Based Company Exec (Danchenko)
8/10/21: University-1 Researcher-3
8/11/21: Handling Agent-1 (Page FISA)
8/16/21: Mueller Analyst-1 (Danchenko)
8/12/21: Tech Company-3 Exec-1 (Alfa)
8/31/21: Charles Dolan (Danchenko)
8/31/21: Mueller SSA-1 (Danchenko)
9/7/21: Charles Dolan (Danchenko)
9/16/21: Michael Sussmann indictment
9/17/21: Brookings Fellow-1 (Danchenko)
10/21/21: UCE-1 (Papadopoulos)
10/27/21: Listrak Employee-1 and personnel (Alfa)
10/29/21: Mueller Analyst-1 (Danchenko)
11/1/21: Charles Dolan (Danchenko)
11/3/21: Danchenko indictment
11/17/21: Cendyn CEO and CTO (Alfa)
11/9/21: Jonathan Winer (Steele Reports)
11/10/21: Jennifer Palmieri
11/12/21: Jake Sullivan
11/16/21: Brookings Fellow-2 (Danchenko)
11/17/21: Cendyn CEO and CTO (Alfa)
12/2/21: HQ Analyst-3 (Steele)
11/20/21: Victoria Nuland
11/30/21: Victoria Nuland (Steele Reports)
12/13/21: James Clapper
1/19/22: John Podesta (Russian Intelligence, Alfa)
2/2/22: David Cohen
2/5/22: Sergei Millian (Danchenko)
3/1/22: Handling Agent-1 (Page FISA)
3/28/22: Foreign Policy Advisor-2
5/11/22: Hillary Clinton (Russian Intelligence)
6/22/22: SSA-1 (Russian Intelligence)
8/9/22: Ritz GM (Danchenko)
12/14/22: Referral to DOD IG on DARPA