In his latest effort to use the House Judiciary Committee as a goon squad to intimidate Donald Trump’s enemies, Jim Jordan actually developed proof that John Ratcliffe — and not the 51 former spooks he was after — inappropriately politicized intelligence to manufacture debate props.
And then Jordan did it himself.
I have the perfectly curated Xitter account to learn when Jim Jordan has released his latest installment of weaponization against democracy.
Last week, he issued his latest attempt to make a scandal out of the true free speech of the 51 former spooks who wrote a letter saying that the release of a Hunter Biden laptop days before the election “had all the classic earmarks of a Russian information operation.” My replies were overrun with trolls chanting incoherent claims.
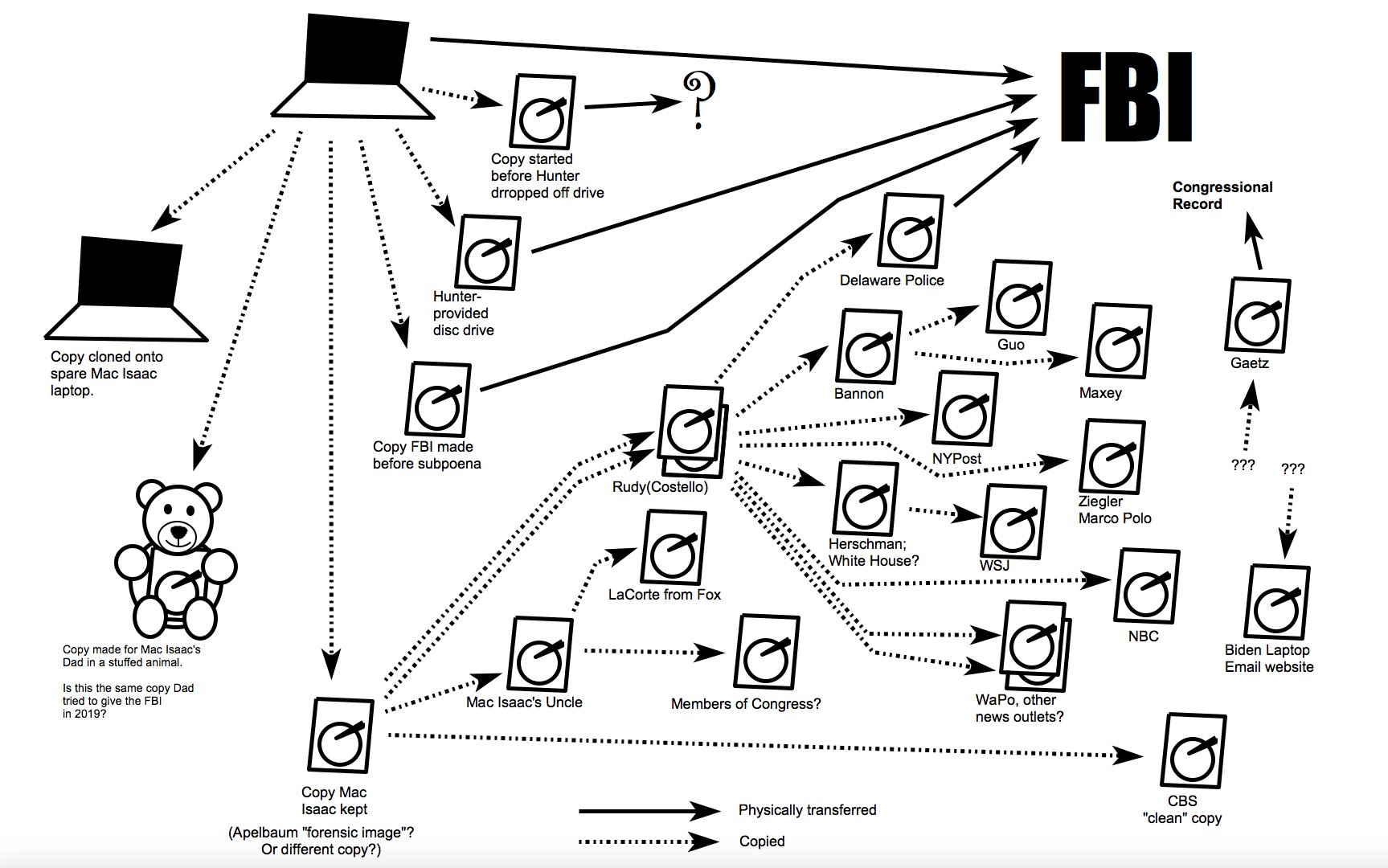
Of course the trolls in my Xitter feed didn’t know the most basic details of the letter or known facts about the copy of a hard drive referred to as a Hunter Biden laptop:
- The former spooks didn’t say this was disinformation, no matter how many times Jordan or Glenn Greenwald lie and say they did. In fact, they specifically caveated that they didn’t know if the emails were genuine and did not have evidence of Russian involvement.
- Nothing revealed about the laptop or the hard drives purportedly based on the laptop rules out Russian involvement. That’s true, in part, because the FBI never bothered to test the laptop to see if anything had been added, never indexed it, and when introduced at trial, the summary witness specifically said she had not looked for signs of tampering. Plus, there were enough Russian drug and sex workers in close proximity to earlier Hunter Biden laptop compromises to allow for a role, particularly in packaging up the device.
- As the Democratic rebuttal notes, the 51 spook letter couldn’t have caused the social media companies to throttle the original New York Post story without a time machine, as Twitter and Facebook had stopped throttling the story several days before the letter was published. Linear time. It’s like magic to these trolls.
Even though Jordan’s latest report substantiates absolutely no misconduct, the trolls nevertheless yapped and yapped about it. Jordan showed:
- While Mike Morrell did target the letter to the last debate (the same one where Trump invited Tony Bobulinski to make claims that have not held up), the other participants were not doing this for the Biden campaign; they were doing it to speak out against Russian interference in the 2020 election
- The former spooks couldn’t have leaked classified information because none of them were read into pertinent information regarding the Russian spies cultivating Rudy Giuliani
- The former spooks got preclearance to publish the letter via the normal process
- After preclearance, the letter was forwarded for Gina Haspel’s attention, but neither she nor anyone else thought it was more important than vaccinating the CIA workforce
- Some of the people involved were private citizens with contracts that did not strip them of their free speech
In other words, the 51 spooks followed the rules, and Jordan was stuck trying to turn it into a scandal.
The Jordan report was only 31 pages and, like a college freshman composition paper, blew entire pages with big screen caps repeating the complaints of two random spooks complaining about “random signatures” on the letter and some discussion of Mark Polymeropoulos getting something excluded from a follow-up.

Polymeropoulos’ attorney, Mark Zaid, explained that CIA redacted two lines, which had nothing to do with Hunter Biden, from the Polymeropoulos follow-up — but that was precisely how preclearance is supposed to work.
Mr. Polymeropolous submitted to the PCRB a two page talking points memo about the subject matter. Obviously, he knew that there was going to be media attention concerning the issue and he wanted to be properly prepared to address the topic if asked. He followed the standard procedure for review of information intended to be made public. No different than any other individual who has a prepublication review requirement. As part of its review, which was handled in the normal timely fashion for such a short document, CIA redacted two lines of information as being classified. Those two lines had nothing to do with the Hunter Biden laptop specifically and concerned Mr. Polymeropolous’ background experience with Russia and a comment concerning that country’s activities generally. Of course, that information was properly protected by Mr. Polymeropolous and never used. To say that this constituted an attempt to use classified information is farcical and reflects a complete lack of understanding how the prepublication review process works. The system operated exactly how it was supposed to and is being distorted for political purposes.
That’s it. That’s the best Jordan could rush out to give Trump something to complain about in a presidential debate over and over.
To think that I would, in front of generals and others, say suckers and losers – we have 19 people that said it was never said by me. It was made up by him, just like Russia, Russia, Russia was made up, just like the 51 intelligence agents are made up, just like the new thing with the 16 economists are talking.
It’s the same thing. Fifty-one intelligence agents said that the laptop was Russia disinformation. It wasn’t. That came from his son Hunter. It wasn’t Russia disinformation. He made up the suckers and losers, so he should apologize to me right now.
[snip]
I’ve dealt with politicians all my life. I’ve been on this side of the equation for the last eight years. I’ve never seen anybody lie like this guy. He lies – I’ve never seen it. He could look you in the face. So – and about so many other things, too.
And we mentioned the laptop, We mentioned “Russia, Russia, Russia,” “Ukraine, Ukraine, Ukraine.” And everything he does is a lie. It’s misinformation and disinformation. The “losers and suckers” story that he made up is a total lie on the military. It’s a disgrace.
This was Trump’s prepackaged answer to attempt to projection his own lying onto Biden. It was barely more vigorous than Biden’s rebuttals.
As flimsy as it was, though, Trump’s use of the 51-spook letter was part of a larger effort, one designed to bully those who speak up against Russian disinformation, disinformation generally, or in favor of rule of law. As John Brennan described, it created a furor about the letter that distracted from Russian intervention, which in turn serves to divide the country.
I think the firestorm, the furor has been created responding to the letter as opposed to the letter itself, as I responded to one of the Congressmen earlier. So it’s unfortunate that this is taking up all your time, it’s taking up my time, and it is, again, further dividing the country.
And, by design, it has chilled speech that talks about Russian interference.
One after another of the spooks interviewed confessed they or others would be chilled by the precedent of Jordan investigating private citizens for their free speech. Kristin Wood described how Mike Flynn put out all their names on a Telegram chat, leading to stalking and death threats.
Several ways. First of all, I’ve received death threats. I’ve received vicious calls, texts, emails from all sorts of random people. Mike Flynn — General Flynn posted on Telegram all of our names and said, you know, let them know how we feel. It unleashed this viciousness that had several other folks calling the police, calling the Threat Management Unit at CIA, to let them know what was happening.
And so for the first time ever, I looked at getting a gun and getting a concealed carry permit because it’s not just that people have been mean or say horrific things, but we’ve seen them take action. And so that feeling of vulnerability for speaking, exercising a First Amendment right, and for saying what I thought was as obvious as there’s air in — there’s air. Let’s just let the FBI do their work.
It has a profound effect on health as well. I’ve been to the emergency room for stress because of all of this. And so when you ask would I do this again, I would insist on a little more precision of language. But it has the effect of censoring people who have more than a thousand years of experience in this topic. And I would think the focus would be on stopping Russia and not on what feels like persecution.
Several of the spooks admitted the mob treatment would lead them to decline further involvement in anything political. Most described that it would chill others.
At that level, the spooks are just like the disinformation experts Jordan also targeted, those who tracked efforts to muddy reason and truth. Their lives have been upended because they attempted to track Russian disinformation that served Republican interests, and the personal and financial cost is shutting down those efforts during an election year.
But then something funny happened.
House Republicans kept pushing the spooks, arguing — notwithstanding the public reporting on Rudy Giuliani’s efforts to solicit dirt from known Russian agent Andrii Derkach — that the spooks should have known, somehow, that the hard drive called a Hunter Biden laptop wasn’t Russian disinformation (which, as noted, the spooks didn’t claim).
Republicans — often Jordan himself — kept asking whether the spooks knew that John Ratcliffe had claimed the laptop was not disinformation (which, again, was not what the letter claimed).
Chairman Jordan. Were you aware of Mr. Ratcliffe’s statement on the morning of the 19th, prior to the letter being sent, where he said in an interview on FOX News that morning that this is not part of the Russian disinformation campaign?
And that led multiple witnesses to explain why Ratcliffe simply wasn’t credible. Wood described that a proper counterintelligence investigation takes longer than would have transpired (no one knew how long the FBI had had the laptop).
Ms. Wood. So, I think what I would say in response to that is that the letter — the purpose of the letter was to say, Let’s not rush to judgment. Everyone, regardless of who they are as Americans, deserves due process. Let’s let the FBI do their work. And when DNI Ratcliffe said that — so as you have seen from all of these investigations, right, they take a very long time to do, to do the considered judgment of 17 or 18 intelligence agencies, and to come up with that to do the exhaustive search of asking new sources, of pulling in every bit of signals intelligence, there’s just no way that’s possible to have been done in the timeframe in which that statement was made. So our whole point was to say, Be careful here. Let us — we don’t know if this is all real. We don’t know if all the emails are real, and we don’t know if this is tied to the Russians. Let’s let the process work
James Clapper described that, not only didn’t he consider Ratcliffe a reliable source, but that he made the statement before any investigation of the laptop.
Mr. Clapper. Well, if the Department of Justice or the FBI or some other legitimate credible source of — who had done a credible forensic analysis — certainly I would accept that. That’s why I suggested that would be a good — would have been a good fix — a good addition to the letter had we said that.
Mr. Gaetz. Are you aware of Director Ratcliffe, the DNI at the time, contradicting the thrust of this letter you signed?
Mr. Clapper. Well, okay. He said that statement before, I think, an investigation had begun of the laptop. So I don’t know where he’s coming from making a statement like that.
In response to a follow-up question from the Minority, Clapper also agreed that Ratcliffe himself was making public statements in anticipation of the debate.
Q It’s an article reporting on Ratcliffe’s remarks, and it’s dated October 19th, 2020, 1:49 p.m. And we’re just introducing it for the fact of the date. The New York Post story in question was released on October 14th, correct?
A Yes.
Q So that would have been 5 days before Ratcliffe made his remarks?
A Right.
Q And I think you said earlier he couldn’t have even begun an investigation in that time period. Is that correct?
A Correct.
Q And can you explain what you mean by that?
A Well, I don’t know how — what his basis for making that statement is when the laptop itself hasn’t been investigated. The DNI, Office of the Director National Intelligence, has no organic forensic analysis capability at all. So they’re dependent on other components of the intelligence community, in this case the FBI, to render such a judgment, which hadn’t been rendered. So I don’t know how he could make that statement.
Q Okay. And even assuming that Ratcliffe — sorry. Withdraw that. And he made these remarks on October 19th, which was the day before the second debate, correct? The second Presidential debate was the 20th.
A Uh-huh.
Q So isn’t it possible that Ratcliffe also made his remarks in the hope that they would impact the debate?
A Well, one could conclude that, yes.
John Brennan was even more disdainful of Ratcliffe’s actions. He described that Ratcliffe’s release of his briefing notes, for the first 2020 debate, made it clear that Ratcliffe was involved in politics.
Chairman Jordan. Director, were you aware of what Director of National Intelligence John Ratcliffe said on the morning of October 19th regarding this Biden laptop story, where he said that it wasn’t a Russian disinformation operation?
Mr. Brennan. I don’t know if I was aware of it at the time, but I would have dismissed it anyway.
Chairman Jordan. Why would you have dismissed it?
Mr. Brennan. Because I don’t think John Ratcliffe was an independent, objective leader of the intelligence community at the time.
Chairman Jordan. So you would dismiss the statement from the Director of National Intelligence — the Acting — the Director of National Intelligence at the time, in the administration, getting intelligence in real-time, you would just dismiss that out of hand?
Mr. Brennan. Not out of hand, but I think it was — a week or two prior to that, there was a selective release of information that included my briefing notes to President Obama in the White House Situation Room that was misrepresenting, in fact, the facts, where it was pushed out in redacted version. And I did think that was a very, very unfortunate, unprofessional, unethical engagement on the part of the Director of National Intelligence in a Presidential election.
Mr. Gaetz. So your dismissing Mr. Ratcliffe was somehow payback for the fact that you thought that your briefing to President Obama had been mischaracterized?
Mr. Brennan. No, that’s not what I said.
Mr. Gaetz. Okay. Well, I’m trying to understand how this event that seems to have aggrieved you regarding the briefing to President Obama impacted your view of the Ratcliffe assessment.
Mr. Brennan. It didn’t aggrieve me. It just indicated to me that John Ratcliffe was not going to be an independent, nonpartisan, apolitical actor.
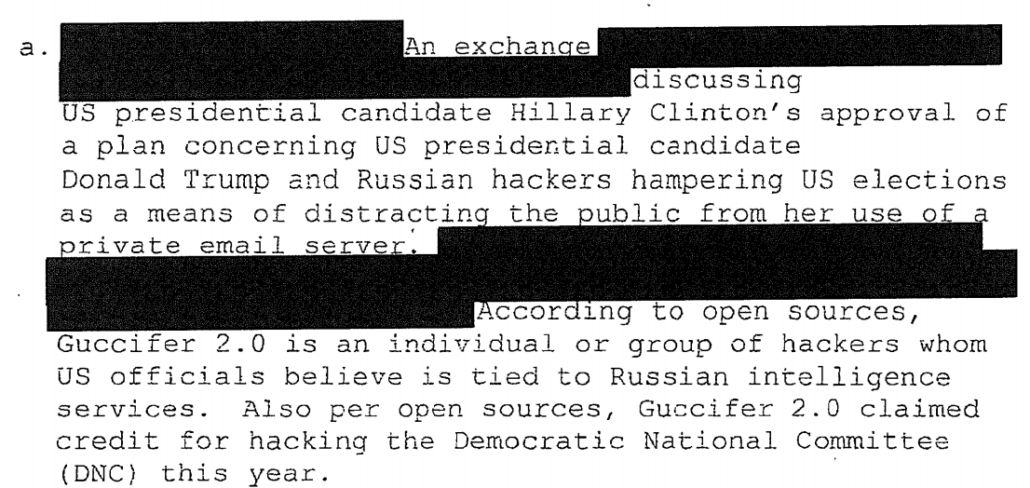
Brennan is referring to the notes he got about materials found among hacked documents in Russia, which Republicans and John Durham spun up, first of all, as true (rather than suspected Russian disinformation), and then misrepresented to claim that Hillary had a plan to frame Donald Trump.
Not only did Brennan see this as an election season stunt (which I observed at the time), but he described that Ratcliffe “misrepresent[ed] the facts” about the materials.
Jim Jordan has been searching for a former spook to accuse of politicizing intelligence in 2020 for years, and he finally found one! Trump’s hand-picked Director of National Intelligence, John Ratcliffe, who was doing precisely what Jordan falsely accused the former spooks of doing, but did so while still an employee of the Intelligence Community.
Update: Corrected that the “laptop” was not just a “hard drive,” but in fact a copy of another hard drive.